Harvard Architecture
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Early Stored Program Computers
Stored Program Computers Thomas J. Bergin Computing History Museum American University 7/9/2012 1 Early Thoughts about Stored Programming • January 1944 Moore School team thinks of better ways to do things; leverages delay line memories from War research • September 1944 John von Neumann visits project – Goldstine’s meeting at Aberdeen Train Station • October 1944 Army extends the ENIAC contract research on EDVAC stored-program concept • Spring 1945 ENIAC working well • June 1945 First Draft of a Report on the EDVAC 7/9/2012 2 First Draft Report (June 1945) • John von Neumann prepares (?) a report on the EDVAC which identifies how the machine could be programmed (unfinished very rough draft) – academic: publish for the good of science – engineers: patents, patents, patents • von Neumann never repudiates the myth that he wrote it; most members of the ENIAC team contribute ideas; Goldstine note about “bashing” summer7/9/2012 letters together 3 • 1.0 Definitions – The considerations which follow deal with the structure of a very high speed automatic digital computing system, and in particular with its logical control…. – The instructions which govern this operation must be given to the device in absolutely exhaustive detail. They include all numerical information which is required to solve the problem…. – Once these instructions are given to the device, it must be be able to carry them out completely and without any need for further intelligent human intervention…. • 2.0 Main Subdivision of the System – First: since the device is a computor, it will have to perform the elementary operations of arithmetics…. – Second: the logical control of the device is the proper sequencing of its operations (by…a control organ. -

Computer Organization and Architecture Designing for Performance Ninth Edition
COMPUTER ORGANIZATION AND ARCHITECTURE DESIGNING FOR PERFORMANCE NINTH EDITION William Stallings Boston Columbus Indianapolis New York San Francisco Upper Saddle River Amsterdam Cape Town Dubai London Madrid Milan Munich Paris Montréal Toronto Delhi Mexico City São Paulo Sydney Hong Kong Seoul Singapore Taipei Tokyo Editorial Director: Marcia Horton Designer: Bruce Kenselaar Executive Editor: Tracy Dunkelberger Manager, Visual Research: Karen Sanatar Associate Editor: Carole Snyder Manager, Rights and Permissions: Mike Joyce Director of Marketing: Patrice Jones Text Permission Coordinator: Jen Roach Marketing Manager: Yez Alayan Cover Art: Charles Bowman/Robert Harding Marketing Coordinator: Kathryn Ferranti Lead Media Project Manager: Daniel Sandin Marketing Assistant: Emma Snider Full-Service Project Management: Shiny Rajesh/ Director of Production: Vince O’Brien Integra Software Services Pvt. Ltd. Managing Editor: Jeff Holcomb Composition: Integra Software Services Pvt. Ltd. Production Project Manager: Kayla Smith-Tarbox Printer/Binder: Edward Brothers Production Editor: Pat Brown Cover Printer: Lehigh-Phoenix Color/Hagerstown Manufacturing Buyer: Pat Brown Text Font: Times Ten-Roman Creative Director: Jayne Conte Credits: Figure 2.14: reprinted with permission from The Computer Language Company, Inc. Figure 17.10: Buyya, Rajkumar, High-Performance Cluster Computing: Architectures and Systems, Vol I, 1st edition, ©1999. Reprinted and Electronically reproduced by permission of Pearson Education, Inc. Upper Saddle River, New Jersey, Figure 17.11: Reprinted with permission from Ethernet Alliance. Credits and acknowledgments borrowed from other sources and reproduced, with permission, in this textbook appear on the appropriate page within text. Copyright © 2013, 2010, 2006 by Pearson Education, Inc., publishing as Prentice Hall. All rights reserved. Manufactured in the United States of America. -
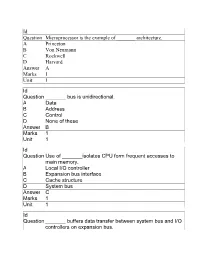
Id Question Microprocessor Is the Example of ___Architecture. A
Id Question Microprocessor is the example of _______ architecture. A Princeton B Von Neumann C Rockwell D Harvard Answer A Marks 1 Unit 1 Id Question _______ bus is unidirectional. A Data B Address C Control D None of these Answer B Marks 1 Unit 1 Id Question Use of _______isolates CPU form frequent accesses to main memory. A Local I/O controller B Expansion bus interface C Cache structure D System bus Answer C Marks 1 Unit 1 Id Question _______ buffers data transfer between system bus and I/O controllers on expansion bus. A Local I/O controller B Expansion bus interface C Cache structure D None of these Answer B Marks 1 Unit 1 Id Question ______ Timing involves a clock line. A Synchronous B Asynchronous C Asymmetric D None of these Answer A Marks 1 Unit 1 Id Question -----timing takes advantage of mixture of slow and fast devices, sharing the same bus A Synchronous B asynchronous C Asymmetric D None of these Answer B Marks 1 Unit 1 Id st Question In 1 generation _____language was used to prepare programs. A Machine B Assembly C High level programming D Pseudo code Answer B Marks 1 Unit 1 Id Question The transistor was invented at ________ laboratories. A AT &T B AT &Y C AM &T D AT &M Answer A Marks 1 Unit 1 Id Question ______is used to control various modules in the system A Control Bus B Data Bus C Address Bus D All of these Answer A Marks 1 Unit 1 Id Question The disadvantage of single bus structure over multi bus structure is _____ A Propagation delay B Bottle neck because of bus capacity C Both A and B D Neither A nor B Answer C Marks 1 Unit 1 Id Question _____ provide path for moving data among system modules A Control Bus B Data Bus C Address Bus D All of these Answer B Marks 1 Unit 1 Id Question Microcontroller is the example of _____ architecture. -

Parallel Computing
Lecture 1: Computer Organization 1 Outline • Overview of parallel computing • Overview of computer organization – Intel 8086 architecture • Implicit parallelism • von Neumann bottleneck • Cache memory – Writing cache-friendly code 2 Why parallel computing • Solving an × linear system Ax=b by using Gaussian elimination takes ≈ flops. 1 • On Core i7 975 @ 4.0 GHz,3 which is capable of about 3 60-70 Gigaflops flops time 1000 3.3×108 0.006 seconds 1000000 3.3×1017 57.9 days 3 What is parallel computing? • Serial computing • Parallel computing https://computing.llnl.gov/tutorials/parallel_comp 4 Milestones in Computer Architecture • Analytic engine (mechanical device), 1833 – Forerunner of modern digital computer, Charles Babbage (1792-1871) at University of Cambridge • Electronic Numerical Integrator and Computer (ENIAC), 1946 – Presper Eckert and John Mauchly at the University of Pennsylvania – The first, completely electronic, operational, general-purpose analytical calculator. 30 tons, 72 square meters, 200KW. – Read in 120 cards per minute, Addition took 200µs, Division took 6 ms. • IAS machine, 1952 – John von Neumann at Princeton’s Institute of Advanced Studies (IAS) – Program could be represented in digit form in the computer memory, along with data. Arithmetic could be implemented using binary numbers – Most current machines use this design • Transistors was invented at Bell Labs in 1948 by J. Bardeen, W. Brattain and W. Shockley. • PDP-1, 1960, DEC – First minicomputer (transistorized computer) • PDP-8, 1965, DEC – A single bus -

P the Pioneers and Their Computers
The Videotape Sources: The Pioneers and their Computers • Lectures at The Compp,uter Museum, Marlboro, MA, September 1979-1983 • Goal: Capture data at the source • The first 4: Atanasoff (ABC), Zuse, Hopper (IBM/Harvard), Grosch (IBM), Stibitz (BTL) • Flowers (Colossus) • ENIAC: Eckert, Mauchley, Burks • Wilkes (EDSAC … LEO), Edwards (Manchester), Wilkinson (NPL ACE), Huskey (SWAC), Rajchman (IAS), Forrester (MIT) What did it feel like then? • What were th e comput ers? • Why did their inventors build them? • What materials (technology) did they build from? • What were their speed and memory size specs? • How did they work? • How were they used or programmed? • What were they used for? • What did each contribute to future computing? • What were the by-products? and alumni/ae? The “classic” five boxes of a stored ppgrogram dig ital comp uter Memory M Central Input Output Control I O CC Central Arithmetic CA How was programming done before programming languages and O/Ss? • ENIAC was programmed by routing control pulse cables f ormi ng th e “ program count er” • Clippinger and von Neumann made “function codes” for the tables of ENIAC • Kilburn at Manchester ran the first 17 word program • Wilkes, Wheeler, and Gill wrote the first book on programmiidbBbbIiSiing, reprinted by Babbage Institute Series • Parallel versus Serial • Pre-programming languages and operating systems • Big idea: compatibility for program investment – EDSAC was transferred to Leo – The IAS Computers built at Universities Time Line of First Computers Year 1935 1940 1945 1950 1955 ••••• BTL ---------o o o o Zuse ----------------o Atanasoff ------------------o IBM ASCC,SSEC ------------o-----------o >CPC ENIAC ?--------------o EDVAC s------------------o UNIVAC I IAS --?s------------o Colossus -------?---?----o Manchester ?--------o ?>Ferranti EDSAC ?-----------o ?>Leo ACE ?--------------o ?>DEUCE Whirl wi nd SEAC & SWAC ENIAC Project Time Line & Descendants IBM 701, Philco S2000, ERA.. -

Oral History Interview with David J. Wheeler
An Interview with DAVID J. WHEELER OH 132 Conducted by William Aspray on 14 May 1987 Princeton, NJ Charles Babbage Institute The Center for the History of Information Processing University of Minnesota, Minneapolis Copyright, Charles Babbage Institute 1 David J. Wheeler Interview 14 May 1987 Abstract Wheeler, who was a research student at the University Mathematical Laboratory at Cambridge from 1948-51, begins with a discussion of the EDSAC project during his tenure. He compares the research orientation and the programming methods at Cambridge with those at the Institute for Advanced Study. He points out that, while the Cambridge group was motivated to process many smaller projects from the larger university community, the Institute was involved with a smaller number of larger projects. Wheeler mentions some of the projects that were run on the EDSAC, the user-oriented programming methods that developed at the laboratory, and the influence of the EDSAC model on the ILLIAC, the ORDVAC, and the IBM 701. He also discusses the weekly meetings held in conjunction with the National Physical Laboratory, the University of Birmingham, and the Telecommunications Research Establishment. These were attended by visitors from other British institutions as well as from the continent and the United States. Wheeler notes visits by Douglas Hartree (of Cavendish Laboratory), Nelson Blackman (of ONR), Peter Naur, Aad van Wijngarden, Arthur van der Poel, Friedrich L. Bauer, and Louis Couffignal. In the final part of the interview Wheeler discusses his visit to Illinois where he worked on the ILLIAC and taught from September 1951 to September 1953. 2 DAVID J. -

Parallel Computing
Lecture 1: Single processor performance Why parallel computing • Solving an 푛 × 푛 linear system Ax=b by using Gaussian 1 elimination takes ≈ 푛3 flops. 3 • On Core i7 975 @ 4.0 GHz, which is capable of about 60-70 Gigaflops 푛 flops time 1000 3.3×108 0.006 seconds 1000000 3.3×1017 57.9 days Milestones in Computer Architecture • Analytic engine (mechanical device), 1833 – Forerunner of modern digital computer, Charles Babbage (1792-1871) at University of Cambridge • Electronic Numerical Integrator and Computer (ENIAC), 1946 – Presper Eckert and John Mauchly at the University of Pennsylvania – The first, completely electronic, operational, general-purpose analytical calculator. 30 tons, 72 square meters, 200KW. – Read in 120 cards per minute, Addition took 200µs, Division took 6 ms. • IAS machine, 1952 – John von Neumann at Princeton’s Institute of Advanced Studies (IAS) – Program could be represented in digit form in the computer memory, along with data. Arithmetic could be implemented using binary numbers – Most current machines use this design • Transistors was invented at Bell Labs in 1948 by J. Bardeen, W. Brattain and W. Shockley. • PDP-1, 1960, DEC – First minicomputer (transistorized computer) • PDP-8, 1965, DEC – A single bus (omnibus) connecting CPU, Memory, Terminal, Paper tape I/O and Other I/O. • 7094, 1962, IBM – Scientific computing machine in early 1960s. • 8080, 1974, Intel – First general-purpose 8-bit computer on a chip • IBM PC, 1981 – Started modern personal computer era Remark: see also http://www.computerhistory.org/timeline/?year=1946 -

Building Computers in 1953: JOHNNIAC"
The Computer Museum History Center presents "Building Computers in 1953: JOHNNIAC" Willis Ware Bill Gunning JOHNNIAC Designer JOHNNIAC Project Engineer Paul Armer Mort Bernstein RAND Department Head JOHNNIAC Software Developer 5:30 PM, Tuesday, Sept. 15, 1998 Computer Museum History Center Building 126 Moffett Field Mt. View JOHNNIAC was one of an illustrious group of computers built in the early 1950's, all inspired by the IAS computer designed by John von Neumann at the Institute for Advanced Study in Princeton. Some of these machines were MANIAC (Los Alamos) and ILLIAC (Univ. of Illinois), as well as WEIZAC, AVIDAC, and ORDVAC. JOHNNIAC was built at RAND Corporation in Santa Monica, and named after John von Neumann himself (he "disapproved", but didn't complain too much). This talk will be given in front of JOHNNIAC itself, the actual machine, since it is now part of the Computer Museum History Center at Moffett Field, the world's largest collection of historical computer hardware. JOHNNIAC ran for the first time in March, 1954. It pioneered the development of time shared operating systems with JOSS (the JOHNNIAC Open Shop System). JOSS could support several dozen users with drum swapping -- there were no disk drives then, so no disk swapping, but instead large rotating drums for magnetic storage. JOHNNIAC also inaugurated the commercial use of magnetic core memory, iron doughnuts on wires, which dominated computer memories for the next decade. Among other tasks, JOHNNIAC was also used to develop digitizing tablets for computer input. Our speakers were all working on JOHNNIAC over 40 years ago. -

The Baleful Effect of Computer Languages and Benchmarks Upon Applied Mathematics, Physics and Chemistry
SIAMjvnl July 16, 1997 The John von Neumann Lecture on The Baleful Effect of Computer Languages and Benchmarks upon Applied Mathematics, Physics and Chemistry presented by Prof. W. Kahan Mathematics Dept., and Elect. Eng. & Computer Sci. Dept. University of California Berkeley CA 94720-1776 (510) 642-5638 at the 45th Annual Meeting of S.I.A.M. Stanford University 15 July 1997 PostScript file: http://http.cs.berkeley.edu/~wkahan/SIAMjvnl.ps For more details see also …/Triangle.ps and …/Cantilever.ps Slide 1 SIAMjvnl July 16, 1997 The Baleful Effect of Computer Languages and Benchmarks upon Applied Mathematics, Physics and Chemistry Abstract: An unhealthy preoccupation with floating–point arithmetic’s Speed, as if it were the same as Throughput, has distracted the computing industry and its marketplace from other important qualities that computers’ arithmetic hardware and software should possess too, qualities like Accuracy, Reliability, Ease of Use, Adaptability, ··· These qualities, especially the ones that arise out of Intellectual Economy, tend to be given little weight partly because they are so hard to quantify and to compare meaningfully. Worse, technical and political limitations built into current benchmarking practices discourage innovations and accommodations of features necessary as well as desirable for robust and reliable technical computation. Most exasperating are computer languages like Java that lack locutions to access advantageous features in hardware that we consequently cannot use though we have paid for them. That lack prevents benchmarks from demonstrating the features' benefits, thus denying language implementors any incentive to accommodate those features in their compilers. It is a vicious circle that the communities concerned with scientific and engineering computation must help the computing industry break. -

E.\.!T' ."Ee ,-, ."!T ,,.,,,,Se"I) E."
• • e.\.!t' ."ee ,-, ."!t ,,.,,,,se"I) e." • •••• II •• -.• DEPARTMENT OF COMPUTER SCIENCE UNIVERSITY OF ILLINOIS URBANA, ILLINOIS The Department of Computer Science is a department of the Graduate. College of the University of Illinois. Activities include: research on the design of computers, their components and application; teaching in related subjects, and operation of computer facilities for instruction and research by all parts of the University. Though a graduate department, the Department of Computer Science has major responsibilities in the undergraduate teaching of computer-related topics, as well as providing scientific computing service to the entire University. The Department, formerly known as the Digital Computer Laboratory, is internationally known for its contribution to computer development. Com puters built under its auspices include ORDVAC, ILLIAC, ILLIAC II, and ILLIAC III, a pattern recognition processor now under construction. Its computer.ser vice facilities presently include five computers: an IBM 7094 with two IBM 1401's located in the Engineering Research Laboratory building and ILLIACII with one IBM 1401 located in the Digital Computer Laboratory buildi~g. A very recent acquisition is a Digital Equipment Corporation com puter, PDP-7, being used on-line to ILLIAC II as a communications processor. -1- ILLIAC II ILLIAC II is a general-purpose scientific digital computing machine. Planning for it began in mid-1957 and construction in 1958 when the Digital Computer Laboratory was completed. The machine ran its first major problem in the Fall of 1962. ILLIAC II is the successor to the famous ILLIAC, built at the University of Illinois over a decade ago and then one of the fastest computers in existence. -

Computer Architecture ELE 475 / COS 475 Slide Deck 1
Computer Architecture ELE 475 / COS 475 Slide Deck 1: Introduction and Instruction Set Architectures David Wentzlaff Department of Electrical Engineering Princeton University 1 What is Computer Architecture? Application 2 What is Computer Architecture? Application Physics 3 What is Computer Architecture? Application Gap too large to bridge in one step Physics 4 What is Computer Architecture? Application In its broadest definition, Gap too large to computer architecture is the design of the abstraction/ bridge in one step implementation layers that allow us to execute information processing applications efficiently using manufacturing technologies Physics 5 What is Computer Architecture? Application In its broadest definition, Gap too large to computer architecture is the design of the abstraction/ bridge in one step implementation layers that allow us to execute information processing applications efficiently using manufacturing technologies Physics 6 Abstractions in Modern Computing Systems Application Algorithm Programming Language Operating System/Virtual Machines Instruction Set Architecture Microarchitecture Register-Transfer Level Gates Circuits Devices Physics 7 Abstractions in Modern Computing Systems Application Algorithm Programming Language Operating System/Virtual Machines Instruction Set Architecture Computer Architecture Microarchitecture (ELE 475) Register-Transfer Level Gates Circuits Devices Physics 8 Computer Architecture is Constantly Changing Application Application Requirements: Algorithm • Suggest how to improve -

1.12 Historical Perspective and Further Reading 54.E1
1.12 Historical Perspective and Further Reading 54.e1 An active fi eld of science is like an 1.12 Historical Perspective and Further immense anthill; the Reading individual almost vanishes into the mass of minds tumbling over For each chapter in the text, a section devoted to a historical perspective can each other, carrying be found online. We may trace the development of an idea through a series of information from place machines or describe some important projects, and we provide references in case to place, passing it you are interested in probing further. around at the speed of Th e historical perspective for this chapter provides a background for some of the light. key ideas presented therein. Its purpose is to give you the human story behind the Lewis Th omas, “Natural technological advances and to place achievements in their historical context. By Science,” in Th e Lives of learning the past, you may be better able to understand the forces that will shape a Cell , 1974 computing in the future. Each historical perspective section ends with suggestions for additional reading, which are also collected separately in the online section “Further Reading.” The First Electronic Computers J. Presper Eckert and John Mauchly at the Moore School of the University of Pennsylvania built what is widely accepted to be the world’s fi rst operational electronic, general-purpose computer. Th is machine, called ENIAC ( Electronic Numerical Integrator and Calculator), was funded by the United States Army and started working during World War II but was not publicly disclosed until 1946.