Suspicious Sweeps the General Intelligence Department and Jordan’S Rule of Law Problem
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

2017 National History Bowl National Championships Playoff Round 7
2017 National History Bowl National Championships Playoff Round 7 Round: Playoffs 7 Supergroup Group Room: Reader: Scorekeep: Team Names, including letter designation if needed, go in the large boxes to the right. TU# Bonus Bonus Points Cumulative Score Bonus Points Cumulative Score 1 Quarter 1 2 Tossups Only 3 4 Put a "10" in the 5 column of the team 6 that answers correctly. 7 Otherwise leave box 8 blank. 9 10 1 Quarter 2 2 Tossups and bonuses 3 Put "10" in the team's 4 column. Otherwise, 5 leave box blank. 6 For bonuses, put "0" or 7 Substitutions allowed between Qtrs all "10" in the bonus 8 column. 9 10 Quarter 3 points points 60 sec. rds - trailing team Lightning Lightning goes first. 10 pts each. Bounceback Bounceback 20 pt bonus for sweep! Total Total 1 Quarter 4 2 Tossups worth 30, 20, or 3 10 points each 4 Put the appropriate 5 number in the column of 6 the team that answers 7 correctly. Otherwise leave 8 box blank. 9 10 Tiebreakers 1 Tiebreak questions Tie Breaker (Sudden are only used 2 have no point value Victory) to determine winner! 3 at all! Final Score NHBB Nationals Bowl 2016-2017 Bowl Playoff Packet 7 Bowl Playoff Packet 7 First Quarter (1) Description acceptable. This event was thought to have occurred in retaliation for the bombing of the perpetrator's Tunisian headquarters in Operation Wooden Leg. Muhammad Zaidan organized this event, which involved the redirection of a vessel to Tartus, Syria. A John Adams opera focusing on this event opens with two choruses of exiles and is named after its only casualty, the 69-year old Leon Klinghoffer. -

Unholy Alliance. the Connection Between the East German Stasi and the Right-Wing Terrorist Odfried Hepp
Unholy Alliance. The Connection between the East German Stasi and the Right-Wing Terrorist Odfried Hepp Bernhard Blumenau Introduction On 18 February 1983, a young man, aged 23, suspected that the police were keeping his apartment under surveillance and took his rucksack, climbed onto an adjacent balcony to hide there until the police were gone. In the depth of night, he left the building and ran ceaselessly through the streets of West Berlin. Finally, to confuse his pursuers, he took several taxis, as well as the U-Bahn, to the Friedrichstraße checkpoint between West Berlin and the German Democratic Republic (GDR), where he arrived just before 6 am. Announcing himself to the East German border guards, he waited in a backroom until he was finally picked up by an officer of the East German State Security, the Stasi.1 This man, Odfried Hepp (aka ‘Friedrich’ in the Stasi files), was one of the most wanted right-wing terrorists2 in the Federal Republic of Germany (FRG) in the 1980s. What sounds like an extract from a spy novel is only one of the highlights of a story that has all the basic ingredients of a thriller: murders and bank robberies, a young man driven by – however abhorrent – political and idealistic beliefs, Cold War politics, Palestinian ‘freedom fighters’, boot camps in the Middle East, spies, and fake identities. Yet this story, which is at the centre of this article, is not fiction – it is the very real account of the life of Odfried Hepp as well as a glimpse at radicalisation and political extremism as well as right-wing terrorism in West Germany, the dimensions of the German- German Cold War struggle and the GDR’s relationship with terrorism. -
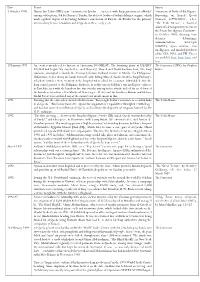
Date Event Source 1 October 1990 Usama Bin Ladin (UBL) Sent
Date Event Source 1 October 1990 Usama bin Ladin (UBL) sent “emissaries to Jordan … to meet with Iraqi government officials” ‘Summary of Body of Intelligence among a delegation, led by Hassan al-Turabi, the de facto leader of Sudan’s Islamist regime, which Reporting on Iraq-al Qaeda made a public display of defending Saddam’s annexation of Kuwait. Al-Turabi was the primary Contacts (1990-2003)’, a.k.a. intermediary between Saddam and al-Qaeda in these early years. “The Feith Memo”, a classified annex of a Pentagon report sent to the Senate Intelligence Committee in October 2003, drawing from detainee debriefings, communications intercepts (SIGINT), open sources, raw intelligence, and finished products of the CIA, NSA, and FBI. Pieces are available here, here, here, and here. 19 January 1991 An event remembered to history as Operation DOGMEAT: The bombing phase of DESERT The Connection (2004), by Stephen STORM had begun two days before, and Ahmed J. Ahmed and Abdul Kadham Saad, two Iraqi Hayes students, attempted to bomb the Thomas Jefferson Cultural Center in Manila, the Philippines. Unfortunately (for them) the bomb went off early, killing Ahmed. Saad recited the Iraqi Embassy’s telephone number from memory at the hospital when asked for a contact. Muwafak al-Ani, the Iraqi consul general at the Philippine Embassy, in reality one of Saddam’s top intelligence officers in East Asia, met with the bombers five times in the run-up to the attack; indeed his car delivered the bombers to within a few blocks of their target. Al-Ani and the brothers Husam and Hisham Abdul Sattar were ordered out of the country for involvement in this. -

Suspicious Sweeps RIGHTS the General Intelligence Department and Jordan’S Rule of Law Problem WATCH September 2006 Volume 18, No
Jordan HUMAN Suspicious Sweeps RIGHTS The General Intelligence Department and Jordan’s Rule of Law Problem WATCH September 2006 Volume 18, No. 6(E) Suspicious Sweeps The General Intelligence Department and Jordan’s Rule of Law Problem I. Summary............................................................................................................... 1 II. Recommendations ...............................................................................................5 To the Government of Jordan...............................................................................5 To the Jordanian parliament ............................................................................... 6 III. Background: The General Intelligence Department and Rule of Law ....................7 Powers and duties of the GID ............................................................................ 11 Powers of arrest under Jordanian law and the GID ........................................ 11 Compliance with International Human Rights Law........................................16 The State Security Court and SSC prosecutors ................................................... 17 Lack of oversight............................................................................................... 21 Who does the General Intelligence Department arrest?......................................22 IV. Arbitrary Detention ...........................................................................................27 Legal standards ................................................................................................30 -

Iraq, Reconsidered Joshua J
Claremont Colleges Scholarship @ Claremont Pitzer Senior Theses Pitzer Student Scholarship 2012 Iraq, Reconsidered Joshua J. Brewer Pitzer College Recommended Citation Brewer, Joshua J., "Iraq, Reconsidered" (2012). Pitzer Senior Theses. Paper 27. http://scholarship.claremont.edu/pitzer_theses/27 This Open Access Senior Thesis is brought to you for free and open access by the Pitzer Student Scholarship at Scholarship @ Claremont. It has been accepted for inclusion in Pitzer Senior Theses by an authorized administrator of Scholarship @ Claremont. For more information, please contact [email protected]. Iraq, Reconsidered By Josh Brewer 4/20/2012 1 Table of Contents Acknowledgments………………..……………………….……………pg(6) Chapter 1: Introduction…………………………..………………...pg(7-12) . What will not be Discussed…………………….………pg(8-9) . The Purpose of this work…………………………........pg(9-10) . Chapter Outline…………………………………… pg(10-12) Chapter 2: Historical Background……………………………… pg(13-16) Chapter 3: The Security Argument……………………………… pg(17-69) o Information Available before Intervention…………...……pg(17-41) . Defection of Hussein Kamel…………………………pg(18-21) . UNSCOM Technical Evaluation Meeting….………pg(21-23) . Testimony of Rolf Ekeus………………………… pg(23-26) . Graham Pearson (a Timeline of Non- Compliance)…………………………………….. pg(26-29) . Conclusions and Further Questions……………… pg(29-30) . Scott Ritter and the Iraq Liberation Act of 1998…………………………………………..…..pg(30-33) . Operation Desert Fox of 1998……………………pg(33-34) . 1998-2002 the Dark Years: Bombs and UN Rearrangements…………………………………..pg(34-37) . The Iraq Resolution: October of 2002……………pg(37-40) 2 . Resolution 1441: November of 2002…………… pg(40-41) o Information Available after the Intervention……………… pg(41-) . The Nuclear Question……………………………… pg(41-44) . North Korean Missile Dealings…………………… pg(44-45) . Russian, Polish, and Indian Missile Dealings……… pg(45-47) . -

Economic and Social Council
UNITED NATIONS E Distr. Economic and Social GENERAL Council E/CN.4/1997/111 4 February 1997 Original: ENGLISH COMMISSION ON HUMAN RIGHTS Fiftythird session Item 4 of the provisional agenda QUESTION OF THE VIOLATION OF HUMAN RIGHTS IN THE OCCUPIED ARAB TERRITORIES, INCLUDING PALESTINE Notes verbale dated 18 June, 8 August and 22 October 1996 from the Permanent Mission of the League of Arab States to the United Nations Office at Geneva addressed to the High Commissioner for Human Rights/ Centre for Human Rights The Permanent Mission of the League of Arab States to the United Nations Office at Geneva presents its compliments to the High Commissioner for Human Rights/Centre for Human Rights and has the honour to transmit herewith the monthly reports on Israeli practices in the Palestinian and occupied Arab territories for April, May and August 1996.* The Permanent Mission of the League of Arab States wishes to express its deep concern at the aggravation of the situation of Arab civilians in the territories occupied by Israel, as described in the attached reports. It requests the High Commissioner for Human Rights/Centre for Human Rights to consider these reports as official documents and to circulate them to the members of the Commission on Human Rights at its fiftythird session. * The annexed reports are reproduced as received in the language of submission and English only. GE.9710398 (E) E/CN.4/1997/111 page 2 Annex [Original: Arabic] Monthly report on the latest developments on the question of Palestine during the month of April 1996 1. -

Re-Assessment of Acts of Piracy Under Contemporary International
Golden Gate University School of Law GGU Law Digital Commons Theses and Dissertations Student Scholarship 11-30-2017 Re-assessment of Acts of Piracy Under Contemporary International Law With Particular Reference to Activities of Somali Pirates Nutcha Sukhawattanakun Golden Gate University School of Law, [email protected] Follow this and additional works at: https://digitalcommons.law.ggu.edu/theses Part of the International Law Commons, and the Law of the Sea Commons Recommended Citation Sukhawattanakun, Nutcha, "Re-assessment of Acts of Piracy Under Contemporary International Law With Particular Reference to Activities of Somali Pirates" (2017). Theses and Dissertations. 79. https://digitalcommons.law.ggu.edu/theses/79 This Dissertation is brought to you for free and open access by the Student Scholarship at GGU Law Digital Commons. It has been accepted for inclusion in Theses and Dissertations by an authorized administrator of GGU Law Digital Commons. For more information, please contact [email protected]. Re-assessment ofActs ofPiracy Under Contemporary International Law with Particular Reference to Activities ofSomali Pirates A Dissertation Submitted To The Committee of International Legal Studies In Candidacy for the Degree Of Scientiae Juridicae Doctor Department oflnternational Legal Studies GOLDEN GATE UNIVERSITY By Nutcha Sukhawattanakun San Francisco, California November 30, 2017 Copyright by Nutcha Sukhawattanakun 2017 i Golden Gate University The Dissertation Committee for Ms. Nutcha Sukhawattanakun Certifies that this -

Tactical and Technological Innovation in Terrorist Campaigns
This document is downloaded from DR‑NTU (https://dr.ntu.edu.sg) Nanyang Technological University, Singapore. Tactical and technological innovation in terrorist campaigns Dolnik, Adam 2006 Dolnik, A. (2006). Tactical and technological innovation in terrorist campaigns. Doctoral thesis, Nanyang Technological University, Singapore. https://hdl.handle.net/10356/14420 https://doi.org/10.32657/10356/14420 Nanyang Technological University Downloaded on 01 Oct 2021 10:16:09 SGT ATTENTION: The Singapore Copyright Act applies to the use of this document. Nanyang Technological University Library Tactical and Technological Innovation in Terrorist Campaigns Adam Dolnik Institute of Defence and Strategic Studies Thesis submitted to the Nanyang Technological University in fulfilment of the requirement for the degree of Doctor of Philosophy (Strategic Studies) 2006 1 ATTENTION: The Singapore Copyright Act applies to the use of this document. Nanyang Technological University Library ACKNOWLEDGEMENTS First and foremost, my thanks go to Dr. Rohan Gunaratna, who has guided me through this effort and who stood up for me when I needed it most. I would also like to thank all of my mentors of past and present: Jason Pate, Dr. Alex Schmid, Dr. Bruce Hoffman, Dr. Amin Tarzi, Dr. Amy Sands, Dr. Stephen Garrett, Dr. Gerard Chaliand, William Monning J.D., Dr. James Wirtz, Dr. Kumar Ramakrishna, Dr. Richard Pilch, Dr. Gavin Cameron, Dr. Jonathan Tucker, Doug MacKinnon, Eric Croddy, Kimberly McCloud, Dr. Raymond Zilinskas, Dr. William Potter, Dr. Anna Vassilieva, Dr. Ibrahim al Marashi, Sundeep Nayak, Dr. Hamidullah Tarzi and others. Special thanks to Chong Yee Ming, hands down the world’s best librarian. I would also like to thank all researchers who have contributed to the terrorism field – without your work there would be no accumulation of knowledge, and nothing for me to build on. -

FOIA CASE LOGS for the Central Intelligence Agency (CIA)
Description of document: FOIA CASE LOGS for: The Central Intelligence Agency (CIA) for FY 2005 – FY 2007 Requested date: 21-October-2007 Released date: 19-February-2008 Posted date: 29-April-2008 Title of Document FY 2005, FY 2006, FY 2007 Case Log Date/date range of document: 01-October-2004 – 21-November-2007 Source of document: Information and Privacy Coordinator Central Intelligence Agency Washington, DC 20505 Fax: (703) 613-3007 The governmentattic.org web site (“the site”) is noncommercial and free to the public. The site and materials made available on the site, such as this file, are for reference only. The governmentattic.org web site and its principals have made every effort to make this information as complete and as accurate as possible, however, there may be mistakes and omissions, both typographical and in content. The governmentattic.org web site and its principals shall have neither liability nor responsibility to any person or entity with respect to any loss or damage caused, or alleged to have been caused, directly or indirectly, by the information provided on the governmentattic.org web site or in this file Central Intelligence Agency Washington, o.c. 20505 • FEB 19 lOW Reference: F-2008-00211 This is a final response to your 21 October 2007 Freedom ofInformation Act (FOIA) request for "FOIA Case Logs for CIA for the time period FY2005 and FY2006 and FY2007-to-date." We processed your request in accordance with the FOIA, 5 U.S.C. § 552, as amended, and the CIA Information Act, 50 U.S.c. § 431, as amended. -

Fråga-Svar Palestinska Områdena. Palestine Liberation Front
2012-01-19 Landinformationsenheten Fråga-svar Palestinska områdena. Palestine Liberation Front (PLF) Fråga Information efterfrågas om gruppen Palestine Liberation Front (PLF) (Jabhat at-tahrir al-filastiniyya). PLF har tidigare funnits med på EU:s terrorlista, men försvann därifrån 2010. Svar Migrationsverket (2009) uppger att PLF är politiskt engagerat, bl.a. på Västbanken. PLF bildades redan 1959, huvudsakligen som en underrättelseorganisation i tjänst för den dåvarande syriska regimen. Har en lång historia av samgående med och splittring från olika andra organisationer, spektakulära terrorattentat mm, bl.a. kapningen av passagerarfärjan Achille Lauro 1985[…] En av PLF- fraktionerna (”Abu Abbas”) finns representerad i PLO och tillhör en av de organisationer som erkänt staten Israel i och med DOP 1993 och officiellt lagt ned terrorism som metod. PLF har begränsat inflytande på de palestinska områdena, men verkar idag politiskt vid al-Fatahs sida och har representation i bl.a. Betlehem, Gaza, Hebron, Jenin, Jeriko och Tulkarm. (Generalsekreterare, Dr Wasel Abu Yousef). (s. 86) Landinfo (2008) rapporterar om att PLF 1983 splittrades i tre olika fraktioner. 5.1.6 PLF – ”Abu al-Abbas fraksjonen” 2 PLF (Palestinian Liberation Front), Jabhat at-tahrir al-filastiniyya, splittet fra PFLP-GC (se under) i 1976. Da det oppsto kamper mellom ulike palestinske fraksjoner i Libanon i 1983 ble PLF splittet i tre. En del under ledelse av Abu al-Abbas støttet Yasser Arafat og Al-Fatah. En annen gren under ledelse av Abdalfatah Ghanim støttet Fatah al-Intifada (se under) som var i opposisjon til Arafat. En tredje gren under ledelse av Talat Yaqub, og senere Abu Nidal al-Ashqar forsøkte å forholde seg nøytral. -

The Decline of the Popular Front for the Liberation of Palestine: A
The Decline of the Popular Front for the Liberation of Palestine: A Historical Analysis Terry James Buck Poster reads: “The Path of Armed Struggle - The Path of Liberated Palestine”. By Ghassan Kanafani, 1969. Accessed on the Palestine Poster Project website. ii Table of Contents Table of Contents iii Acknowledgements iv Preface vi Introduction 1 I. The Popular Front in Jordan: Liberation, Confrontation, and Dispersal 5 The Arab Nationalist Movement: Unity, Liberation, and Vengeance 7 The Palestinian Liberation Movement: Resistance until Victory 12 Unity of the Palestinian and Jordanian Masses: Down with the King 20 II. The Popular Front in Lebanon: Revolution, Cooperation, and the Sectarian Divide 31 The Arab Nationalist Movement in Lebanon 32 After the War: The Palestinian Presence in Lebanon 38 The Lebanese Civil War 46 III. The Popular Front in the Territories: Resistance, Autonomy, and Collaboration 56 The Gaza Strip under Occupation 58 The West Bank under Occupation 67 The Prisons of the Occupation 76 Rising up and Throwing off: al-Intifada 83 Conclusion 90 Appendix One: Glossary of Acronyms and Organizations 94 Appendix Two: Glossary of Terms 96 Appendix Three: Glossary of Names 97 Appendix Four: The Palestinian Student Left: A Diagnosis of the Fall 100 Bibliography 106 iii Acknowledgments To start, my committee transformed a mess of facts and opinions into an essay with, at maximum, a half dozen theses. Aaron Berman, as a historian, an advisor, a supporter, and a friend, shaped this project with hundreds of useful edits and suggestions and much needed encouragement. Hiba Bou Akar challenged me to think outside the narrow terms of a historian, adding layers of meaning to this essay, while also bringing humor to every meeting. -

F-14 Tomcat Tales | David Cenciotti
F-14 TOMCAT TALES | DAVID CENCIOTTI The aviationist presents F-14 Tomcat tales The most interesting stories of the F-14 in U.S. Navy service David Cenciotti HTTP://THEAVIATIONIST.COM PAGE 1/80 F-14 TOMCAT TALES | DAVID CENCIOTTI Introduction The Grumman F-14 Tomcat is, by far, the most iconic fighter in the world. Made famous by the 1986 blockbuster about elite U.S. Navy fighter pilots, the Tomcat has long been considered the symbol of Naval Aviation. Developed at the end of the 1960s, to protect the U.S. Navy Carrier Battle Groups from the Soviet long-range bombers, the F-14 replaced the F-4 Phantom and deployed aboard U.S. aircraft carriers from 1974 to 2006, when it was retired from active service. Throughout its about 30-year long career, the F-14 has served as the U.S. Navy's primary maritime air superiority fighter, tactical photo reconnaissance platform (using the Tactical Airborne Reconnaissance Pod System – TARPS – fielded on the Tomcat in 1981) and, beginning in 1990s, as a fighter bomber (a variant dubbed “Bombcat”) capable of performing air-to-surface missions carrying PGMs (Precision Guided Munitions). From the Gulf of Sidra incidents, which saw USN F-14s kill Libyan Mig-23 and Su-22 jets, to the Achille Lauro operation; from Top Gun to the participation in Desert Storm and Iraqi Freedom, this ebook contains a series of articles that will provide a rare insight into the operational history of the legendary Tomcat. David Cenciotti Founder & Editor HTTP://THEAVIATIONIST.COM PAGE 2/80 F-14 TOMCAT TALES | DAVID CENCIOTTI TABLE OF CONTENTS CHAPTER 1 .................................................................................................................................................................