Network Coded Wireless Architecture
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Extreme Networks EXOS V12.3.6.2 EAL3+ ST
Extreme Networks, Inc. ExtremeXOS Network Operating System v12.3.6.2 Security Target Evaluation Assurance Level: EAL3+ Document Version: 0.9 Prepared for: Prepared by: Extreme Networks, Inc. Corsec Security, Inc. 3585 Monroe Street 13135 Lee Jackson Memorial Hwy., Suite 220 Santa Clara, CA 95051 Fairfax, VA 22033 Phone: +1 408 579 2800 Phone: +1 703 267 6050 http://www.extremenetworks.com http://www.corsec.c om Security Target , Version 0.9 March 12, 2012 Table of Contents 1 INTRODUCTION ................................................................................................................... 4 1.1 PURPOSE ................................................................................................................................................................ 4 1.2 SECURITY TARGET AND TOE REFERENCES ...................................................................................................... 4 1.3 TOE OVERVIEW ................................................................................................................................................... 5 1.3.1 TOE Environment ................................................................................................................................................... 5 1.4 TOE DESCRIPTION .............................................................................................................................................. 6 1.4.1 Architecture ............................................................................................................................................................. -

Game Developers Agree: Lag Kills Online Multiplayer, Especially When You’Re Trying to Make Products That Rely on Timing-Based CO Skill, Such As Fighting Games
THE LEADING GAME INDUSTRY MAGAZINE VOL19 NO9 SEPTEMBER 2012 INSIDE: SCALE YOUR SOCIAL GAMES postmortem BER 9 m 24 PIXELJUNK 4AM How do you invent a new musical instrument? PIXELJUNK 4AM turned PS3s everywhere into music-making machines and let players stream E 19 NU their performances worldwide. In this postmortem, lead designer Rowan m Parker walks us through the ups (Move controls, online streaming), the LU o downs (lack of early direction, game/instrument duality), and why you V need to have guts when you’re reinventing interactive music. By Rowan Parker features NTENTS.0912 7 FIGHT THE LAG! Nine out of ten game developers agree: Lag kills online multiplayer, especially when you’re trying to make products that rely on timing-based co skill, such as fighting games. Fighting game community organizer Tony Cannon explains how he built his GGPO netcode to “hide” network latency and make online multiplayer appetizing for even the most picky players. By Tony Cannon 15 SCALE YOUR ONLINE GAME Mobile and social games typically rely on a robust server-side backend—and when your game goes viral, a properly-architected backend is the difference between scaling gracefully and being DDOSed by your own players. Here’s how to avoid being a victim of your own success without blowing up your server bill. By Joel Poloney 20 LEVEL UP YOUR STUDIO Fix your studio’s weakest facet, and it will contribute more to your studio’s overall success than its strongest facet. Production consultant Keith Fuller explains why it’s so important to find and address your studio’s weaknesses in the results of his latest game production survey. -

Network Devices Configuration Guide for Packetfence Version 6.5.0 Network Devices Configuration Guide by Inverse Inc
Network Devices Configuration Guide for PacketFence version 6.5.0 Network Devices Configuration Guide by Inverse Inc. Version 6.5.0 - Jan 2017 Copyright © 2017 Inverse inc. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or any later version published by the Free Software Foundation; with no Invariant Sections, no Front-Cover Texts, and no Back-Cover Texts. A copy of the license is included in the section entitled "GNU Free Documentation License". The fonts used in this guide are licensed under the SIL Open Font License, Version 1.1. This license is available with a FAQ at: http:// scripts.sil.org/OFL Copyright © Łukasz Dziedzic, http://www.latofonts.com, with Reserved Font Name: "Lato". Copyright © Raph Levien, http://levien.com/, with Reserved Font Name: "Inconsolata". Table of Contents About this Guide ............................................................................................................... 1 Other sources of information ..................................................................................... 1 Note on Inline enforcement support ................................................................................... 2 List of supported Network Devices ..................................................................................... 3 Switch configuration .......................................................................................................... 4 Assumptions ............................................................................................................ -

Glossaire Des Protocoles Réseau
Glossaire des protocoles réseau - EDITION LIVRES POUR TOUS - http://www.livrespourtous.com/ Mai 2009 A ALOHAnet ALOHAnet, également connu sous le nom ALOHA, est le premier réseau de transmission de données faisant appel à un média unique. Il a été développé par l'université d'Hawaii. Il a été mis en service en 1970 pour permettre les transmissions de données par radio entre les îles. Bien que ce réseau ne soit plus utilisé, ses concepts ont été repris par l'Ethernet. Histoire C'est Norman Abramson qui est à l'origine du projet. L'un des buts était de créer un réseau à faible coût d'exploitation pour permettre la réservation des chambres d'hôtels dispersés dans l'archipel d'Hawaï. Pour pallier l'absence de lignes de transmissions, l'idée fut d'utiliser les ondes radiofréquences. Au lieu d'attribuer une fréquence à chaque transmission comme on le faisait avec les technologies de l'époque, tout le monde utiliserait la même fréquence. Un seul support (l'éther) et une seule fréquence allaient donner des collisions entre paquets de données. Le but était de mettre au point des protocoles permettant de résoudre les collisions qui se comportent comme des perturbations analogues à des parasites. Les techniques de réémission permettent ainsi d'obtenir un réseau fiable sur un support qui ne l'est pas. APIPA APIPA (Automatic Private Internet Protocol Addressing) ou IPv4LL est un processus qui permet à un système d'exploitation de s'attribuer automatiquement une adresse IP, lorsque le serveur DHCP est hors service. APIPA utilise la plage d'adresses IP 169.254.0.0/16 (qu'on peut également noter 169.254.0.0/255.255.0.0), c'est-à-dire la plage dont les adresses vont de 169.254.0.0 à 169.254.255.255. -

Sintesi Catalogo Competenze 2
Internet of Things Competenze Campi di applicazione • Progettazione e sviluppo di firmware su micro • Monitoraggio ambientale meteorologico di para- controllori a basso e bassissimo consumo quali ad metri climatici e parametri della qualità dell’aria, esempio Arduino, Microchip, NXP, Texas Instru- anche in mobilità ments e Freescale • Monitoraggio ambientale distribuito per l’agricol- • Sviluppo su PC embedded basati su processori tura di precisione ARM e sistema operativo Linux quali ad esempio • Monitoraggio della qualità dell’acqua e dei parame- Portux, Odroid, RaspberryPI ed Nvidia Jetson tri di rischio ambientale (alluvioni, frane, ecc.) • Progettazione e sviluppo di Wired e Wireless Sen- • Monitoraggio di ambienti indoor (scuole, bibliote- sor Networks basate su standard quali ZigBee, che, uffici pubblici, ecc) SimpliciTI, 6LoWPAN, 802.15.4 e Modbus • Smart building: efficienza energetica, comfort am- • Progettazione e sviluppo di sistemi ad alimentazio- bientale e sicurezza ne autonoma e soluzioni di Energy harvesting • Utilizzo di piattaforme microUAV per misure distri- • Ottimizzazione di software e protocolli wireless buite, per applicazioni di fotogrammetria, teleme- per l’uso efficiente dell’energia all’interno di nodi tria e cartografia, per sistemi di navigazione auto- ad alimentazione autonoma matica basata su sensoristica e image processing, • Design e prototipazione (con strumenti CAD, pianificazione e gestione delle missioni stampante 3D, ecc) di circuiti elettronici per l’inte- • Smart Grid locale per l’ottimizzazione -

Network Devices Configuration Guide
Network Devices Configuration Guide PacketFence v11.0.0 Version 11.0.0 - September 2021 Table of Contents 1. About this Guide . 2 1.1. Other sources of information . 2 2. Note on Inline enforcement support. 3 3. Note on RADIUS accounting . 4 4. List of supported Network Devices. 5 5. Switch configuration . 6 5.1. Assumptions . 6 5.2. 3COM . 6 5.3. Alcatel . 12 5.4. AlliedTelesis . 16 5.5. Amer . 21 5.6. Aruba. 22 5.7. Avaya. 24 5.8. Brocade. 25 5.9. Cisco . 28 5.10. Cisco Small Business (SMB) . 61 5.11. D-Link. 63 5.12. Dell . 65 5.13. Edge core . 70 5.14. Enterasys . 71 5.15. Extreme Networks. 74 5.16. Foundry . 78 5.17. H3C . 80 5.18. HP . 83 5.19. HP ProCurve . 84 5.20. Huawei . 94 5.21. IBM . 97 5.22. Intel. 98 5.23. Juniper . 98 5.24. LG-Ericsson . 104 5.25. Linksys . 105 5.26. Netgear . 106 5.27. Nortel . 108 5.28. Pica8. 110 5.29. SMC . 111 5.30. Ubiquiti. 112 6. Wireless Controllers and Access Point Configuration . 116 6.1. Assumptions. 116 6.2. Unsupported Equipment . 116 6.3. Aerohive Networks . 117 6.4. Anyfi Networks . 135 6.5. Avaya . 138 6.6. Aruba . 138 6.7. Belair Networks (now Ericsson) . 158 6.8. Bluesocket . 158 6.9. Brocade . 159 6.10. Cambium . 159 6.11. Cisco. 163 6.12. CoovaChilli. 204 6.13. D-Link. 206 6.14. Extricom . 206 6.15. Fortinet FortiGate . 207 6.16. Hostapd . -

Red Hat Openstack Platform 12 Networking Guide
Red Hat OpenStack Platform 12 Networking Guide An Advanced Guide to OpenStack Networking Last Updated: 2019-12-04 Red Hat OpenStack Platform 12 Networking Guide An Advanced Guide to OpenStack Networking OpenStack Team [email protected] Legal Notice Copyright © 2019 Red Hat, Inc. The text of and illustrations in this document are licensed by Red Hat under a Creative Commons Attribution–Share Alike 3.0 Unported license ("CC-BY-SA"). An explanation of CC-BY-SA is available at http://creativecommons.org/licenses/by-sa/3.0/ . In accordance with CC-BY-SA, if you distribute this document or an adaptation of it, you must provide the URL for the original version. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, the Red Hat logo, JBoss, OpenShift, Fedora, the Infinity logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. Linux ® is the registered trademark of Linus Torvalds in the United States and other countries. Java ® is a registered trademark of Oracle and/or its affiliates. XFS ® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. MySQL ® is a registered trademark of MySQL AB in the United States, the European Union and other countries. Node.js ® is an official trademark of Joyent. Red Hat is not formally related to or endorsed by the official Joyent Node.js open source or commercial project. -

Improving Input Prediction in Online Fighting Games
DEGREE PROJECT IN TECHNOLOGY, FIRST CYCLE, 15 CREDITS STOCKHOLM, SWEDEN 2021 Improving Input Prediction in Online Fighting Games Anton Ehlert KTH ROYAL INSTITUTE OF TECHNOLOGY ELECTRICAL ENGINEERING AND COMPUTER SCIENCE Authors Anton Ehlert <[email protected]> Electrical Engineering and Computer Science KTH Royal Institute of Technology Place for Project Stockholm, Sweden Examiner Fredrik Lundevall KTH Royal Institute of Technology Supervisor Fadil Galjic KTH Royal Institute of Technology Abstract Many online fighting games use rollback netcode in order to compensate for network delay. Rollback netcode allows players to experience the game as having reduced delay. A drawback of this is that players will sometimes see the game quickly ”jump” to a different state to adjust for the the remote player’s actions. Rollback netcode implementations require a method for predicting the remote player’s next button inputs. Current implementations use a naive repeatlast frame policy for such prediction. There is a possibility that alternative methods may lead to improved user experience. This project examines the problem of improving input prediction in fighting games. It details the development of a new prediction model based on recurrent neural networks. The model was trained and evaluated using a dataset of several thousand recorded player input sequences. The results show that the new model slightly outperforms the naive method in prediction accuracy, with the difference being greater for longer predictions. However, it has far higher requirements both in terms of memory and computation cost. It seems unlikely that the model would significantly improve on current rollback netcode implementations. However, there may be ways to improve predictions further, and the effects on user experience remains unknown. -

Counter Strike:Source)
Institut für Technische Informatik und Kommunikationsnetze Lorenz Breu Online-Games: Traffic Analysis of Popular Game Servers (Counter Strike:Source) Semester Thesis SA-2007-42 February 2007 to September 2007 Tutor: Dr. Martin May Supervisor: Prof. B. Plattner 2 Abstract As the amount of traffic generated by online games is increasing, models used to simulate network traffic and design or optimize network hardware and protocols as well as implementa- tions of QoS may have to be adapted to consider such traffic. This study examined the network characteristics of three Counter-Strike: Source gameservers running on a single PC in the ETH network yet publicly accessible across the internet, both in terms of technical issues such as packet size as well as in terms of player load and its effects on the traffic footprint. The results agree with previous studies based on other FPS games including Counter-Strike, the predeces- sor of the game used in this study. It shows that traffic generated by the client is different to that generated by the server, yet both show similar patterns of short packets sent in bursts. Player behaviour plays a major role in shaping game traffic as was to be expected. Several patterns for online game traffic detection are discussed, specifically the use of unique patterns of status request and status information exchanges. In addition some netflow data from the DDosVax project was analysed to confirm that the patterns seen in the trace data are also visible in the netflow data. Contents 1 Introduction 9 1.1 Motivation . 11 1.2 The Task . -
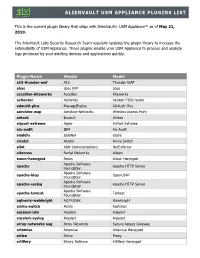
Alienvault Usm Appliance Plugins List
ALIENVAULT USM APPLIANCE PLUGINS LIST This is the current plugin library that ships with AlienVault USM Appliance as of May 21, 2019. The AlienVault Labs Security Research Team regularly updates the plugin library to increase the extensibility of USM Appliance. These plugins enable your USM Appliance to process and analyze logs produced by your existing devices and applications quickly. Plugin Name Vendor Model a10-thunder-waf A10 Thunder WAF abas abas ERP abas accellion-kiteworks Accellion Kiteworks actiontec Actiontec Verizon FIOS router adaudit-plus ManageEngine ADAudit Plus aerohive-wap Aerohive Networks Wireless Access Point airlock Envault Airlock airport-extreme Apple AirPort Extreme aix-audit IBM Aix Audit aladdin SafeNet eSafe alcatel Alcatel Arista Switch allot Allot Communications NetEnforcer alteonos Nortel Networks Alteon amun-honeypot Amun Amun Honeypot Apache Software apache Apache HTTP Server Foundation Apache Software apache-ldap OpenLDAP Foundation Apache Software apache-syslog Apache HTTP Server Foundation Apache Software apache-tomcat Tomcat Foundation aqtronix-webknight AQTRONiX WebKnight arista-switch Arista Switches arpalert-idm Arpalert Arpalert arpalert-syslog Arpalert Arpalert array-networks-sag Array Networks Secure Access Gateway artemisa Artemisa Artemisa Honeypot artica Artica Proxy artillery Binary Defense Artillery Honeypot ALIENVAULT USM APPLIANCE PLUGINS LIST aruba Aruba Networks Mobility Access Switches aruba-6 Aruba Networks Wireless aruba-airwave Aruba Networks Airwave aruba-clearpass Aruba Networks -

The ECI Exam Study Materials
Sold to [email protected] Study Guide Disclaimer The Esports Certification Institute (“ECI”) does not make any guarantee, warranty or representation that any examinee will pass any exam as a result of studying and reviewing the information presented in the Official ECI Exam Study Guide (the “Study Guide”) or in any other publications or study materials created, endorsed, or recommended by ECI. Further, no guarantee is given that all information tested on a particular exam appears in the Study Guide or that all information appearing in the Study Guide is up-to-date and free from unintentional errors or omissions. Your use of the Study Guide constitutes your review, approval and acceptance of this disclaimer provision. Nonetheless, ECI believes the Study Guide to be the best and most complete set of information available for examinees to study and, therefore, recommends it to all exam takers. If you believe that any of the information contained in the Study Guide is inaccurate or requires updating, please feel free to contact ECI at [email protected]. ECI values your feedback and will investigate all such assertions. 2 TO THE FUTURE ECI EXAM SUCCESS STORY First, thank you very much for purchasing the ECI Exam study materials. Congratulations, as well, for taking an important step toward preparing for the ECI exam. The Official ECI Exam Guide is the best tool available to you to prepare you for the ECI exam. By investing in an ECI Exam study guide, you are taking the first step towards employment in the esports industry. We created this guide with the goal of teaching you the exam materials in a way that is easy to use and understand. -

Smash Ultimate Online Lag Fix
Smash Ultimate Online Lag Fix Ultimate: 5 things Nintendo needs to fix. Reduce graphic lags in Realm of the Mad God. Ultimate, replacing Plasma Wire from Super Smash Bros. The upgrade menu for spirits is fine. gg has been acquired by Microsoft! Since we started in 2015, our goal has been to build active esports scenes around the games people love to play. The Ultimate GTA 5 Guide to Boosting Your Graphics & FPS. since we are aiming at non-interpolated. This was the tenth iteration of the tournament series. You have successfully removed some lag from your gmod! Thanks for reading this guide. Wi-Fi lag, which is very often confused with frame delay, is a drop in the frames per second of a game due to a slow or inconsistent connection while playing a game online. 2 - Disable wxWidgets asserts, fix H264DECCheckDecunitLength not working properly when H264 AUD are present in stream 0. Super Smash bros ultimate's online is seeming to be quite a disaster But im hopeful that it will be fixed! Subscribe for more Super Smash Bros Ultimate LAG Gameplay & some Online Matches. Super Smash Bros. Lag problem Then i go outside, my fps go down in 30. Do NOT join the VC if you ain't joining the arena, if you are in one without the other and after I warned you, don't be surprised if your temporarily kicked. The game is the sixth entry in the Super Smash Bros. From matchmaking to performance to. Yuzu is an experimental open-source emulator for the Nintendo Switch from the creators of Citra.