Nebraska Incident-Based Reporting System (NIBRS)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Crimes Act 2016
REPUBLIC OF NAURU Crimes Act 2016 ______________________________ Act No. 18 of 2016 ______________________________ TABLE OF PROVISIONS PART 1 – PRELIMINARY ....................................................................................................... 1 1 Short title .................................................................................................... 1 2 Commencement ......................................................................................... 1 3 Application ................................................................................................. 1 4 Codification ................................................................................................ 1 5 Standard geographical jurisdiction ............................................................. 2 6 Extraterritorial jurisdiction—ship or aircraft outside Nauru ......................... 2 7 Extraterritorial jurisdiction—transnational crime ......................................... 4 PART 2 – INTERPRETATION ................................................................................................ 6 8 Definitions .................................................................................................. 6 9 Definition of consent ................................................................................ 13 PART 3 – PRINCIPLES OF CRIMINAL RESPONSIBILITY ................................................. 14 DIVISION 3.1 – PURPOSE AND APPLICATION ................................................................. 14 10 Purpose -

Competing Theories of Blackmail: an Empirical Research Critique of Criminal Law Theory
Competing Theories of Blackmail: An Empirical Research Critique of Criminal Law Theory Paul H. Robinson,* Michael T. Cahill** & Daniel M. Bartels*** The crime of blackmail has risen to national media attention because of the David Letterman case, but this wonderfully curious offense has long been the favorite of clever criminal law theorists. It criminalizes the threat to do something that would not be criminal if one did it. There exists a rich liter- ature on the issue, with many prominent legal scholars offering their accounts. Each theorist has his own explanation as to why the blackmail offense exists. Most theories seek to justify the position that blackmail is a moral wrong and claim to offer an account that reflects widely shared moral intuitions. But the theories make widely varying assertions about what those shared intuitions are, while also lacking any evidence to support the assertions. This Article summarizes the results of an empirical study designed to test the competing theories of blackmail to see which best accords with pre- vailing sentiment. Using a variety of scenarios designed to isolate and test the various criteria different theorists have put forth as “the” key to blackmail, this study reveals which (if any) of the various theories of blackmail proposed to date truly reflects laypeople’s moral judgment. Blackmail is not only a common subject of scholarly theorizing but also a common object of criminal prohibition. Every American jurisdiction criminalizes blackmail, although there is considerable variation in its formulation. The Article reviews the American statutes and describes the three general approaches these provisions reflect. -

Incest Statutes
Statutory Compilation Regarding Incest Statutes March 2013 Scope This document is a comprehensive compilation of incest statutes from U.S. state, territorial, and the federal jurisdictions. It is up-to-date as of March 2013. For further assistance, consult the National District Attorneys Association’s National Center for Prosecution of Child Abuse at 703.549.9222, or via the free online prosecution assistance service http://www.ndaa.org/ta_form.php. *The statutes in this compilation are current as of March 2013. Please be advised that these statutes are subject to change in forthcoming legislation and Shepardizing is recommended. 1 National Center for Prosecution of Child Abuse National District Attorneys Association Table of Contents ALABAMA .................................................................................................................................................................. 8 ALA. CODE § 13A-13-3 (2013). INCEST .................................................................................................................... 8 ALA. CODE § 30-1-3 (2013). LEGITIMACY OF ISSUE OF INCESTUOUS MARRIAGES ...................................................... 8 ALASKA ...................................................................................................................................................................... 8 ALASKA STAT. § 11.41.450 (2013). INCEST .............................................................................................................. 8 ALASKA R. EVID. RULE 505 (2013) -

Conflict of the Criminal Statute of Limitations with Lesser Offenses at Trial
William & Mary Law Review Volume 37 (1995-1996) Issue 1 Article 10 October 1995 Conflict of the Criminal Statute of Limitations with Lesser Offenses at Trial Alan L. Adlestein Follow this and additional works at: https://scholarship.law.wm.edu/wmlr Part of the Criminal Law Commons Repository Citation Alan L. Adlestein, Conflict of the Criminal Statute of Limitations with Lesser Offenses at Trial, 37 Wm. & Mary L. Rev. 199 (1995), https://scholarship.law.wm.edu/wmlr/vol37/iss1/10 Copyright c 1995 by the authors. This article is brought to you by the William & Mary Law School Scholarship Repository. https://scholarship.law.wm.edu/wmlr CONFLICT OF THE CRIMINAL STATUTE OF LIMITATIONS WITH LESSER OFFENSES AT TRIAL ALAN L. ADLESTEIN I. INTRODUCTION ............................... 200 II. THE CRIMINAL STATUTE OF LIMITATIONS AND LESSER OFFENSES-DEVELOPMENT OF THE CONFLICT ........ 206 A. Prelude: The Problem of JurisdictionalLabels ..... 206 B. The JurisdictionalLabel and the CriminalStatute of Limitations ................ 207 C. The JurisdictionalLabel and the Lesser Offense .... 209 D. Challenges to the Jurisdictional Label-In re Winship, Keeble v. United States, and United States v. Wild ..................... 211 E. Lesser Offenses and the Supreme Court's Capital Cases- Beck v. Alabama, Spaziano v. Florida, and Schad v. Arizona ........................... 217 1. Beck v. Alabama-LegislativePreclusion of Lesser Offenses ................................ 217 2. Spaziano v. Florida-Does the Due Process Clause Require Waivability? ....................... 222 3. Schad v. Arizona-The Single Non-Capital Option ....................... 228 F. The Conflict Illustrated in the Federal Circuits and the States ....................... 230 1. The Conflict in the Federal Circuits ........... 232 2. The Conflict in the States .................. 234 III. -

PDF-Download
Order of the 1st Chamber of the Second Senate of 1 March 2004 – 2 BvR 1570/03 – in the proceedings on the constitutional complaint of the Turkish national A. ... against a) the order of the Higher Administrative Court (Oberverwaltungsgericht) for the Land North Rhine-Westphalia of 19 August 2003 – 18 B 1503/03 –, b) the order of Düsseldorf Administrative Court (Verwaltungsgericht) of 15 July 2003 – 24 L 1977/03 – and application to issue an injunction ... RULING: The constitutional complaint is not admitted for decision. The application to issue an injunction is therewith concluded. GROUNDS: I. 1. a) The applicant objects to his expulsion to Turkey. 1 He was born in Germany in 1983 and grew up here, where his parents and siblings 2 also live. He has had a permanent residence permit since December 1999. The applicant has come to the notice of the police several times since 2000. He was 3 sentenced most recently on 22 July 2002 in respect of joint robbery by blackmail in concurrence of offences with threat, robbery by blackmail in concurrence of offences with bodily harm, threat in concurrence of offences with deprivation of liberty and co- ercion, coercion in concurrence of offences with threat, threat in two cases in concur- rence of offences with theft resembling robbery, coercion and theft, as well as in re- spect of blackmail relating to the two latter convictions, to combined youth custody of three years and six months. In consequence of the latter conviction, the immigration authority expelled him by or- 4 der of 9 May 2003, ordered the immediate enforcement of this expulsion and an- nounced to him that he would be expelled from custody to Turkey. -

Digital Blackmail As an Emerging Tactic 2016
September 9 DIGITAL BLACKMAIL AS AN EMERGING TACTIC 2016 Digital Blackmail (DB) represents a severe and growing threat to individuals, small businesses, corporations, and government Examining entities. The rapid increase in the use of DB such as Strategies ransomware; the proliferation of variants and growth in their ease of use and acquisition by cybercriminals; weak defenses; Public and and the anonymous nature of the money trail will only increase Private Entities the scale of future attacks. Private sector, non-governmental organization (NGO), and government cybersecurity experts Can Pursue to were brought together by the Office of the Director of National Contain Such Intelligence and the Department of Homeland Security to determine emerging tactics and countermeasures associated Attacks with the threat of DB. In this paper, DB is defined as illicitly acquiring or denying access to sensitive data for the purpose of affecting victims’ behaviors. Threats may be made of lost revenue, the release of intellectual property or sensitive personnel/client information, the destruction of critical data, or reputational damage. For clarity, this paper maps DB activities to traditional blackmail behaviors and explores methods and tools, exploits, protection measures, whether to pay or not pay the ransom, and law enforcement (LE) and government points of contact for incident response. The paper also examines the future of the DB threat. Digital Blackmail as an Emerging Tactic Team Members Name Organization Caitlin Bataillon FBI Lynn Choi-Brewer -

Misprison of Felony
South Carolina Law Review Volume 6 Issue 1 Article 8 Fall 9-1-1953 Misprison of Felony E. L. Morgan Follow this and additional works at: https://scholarcommons.sc.edu/sclr Part of the Law Commons Recommended Citation E. Lee Morgan, Misprison of Felony, 6 S.C.L.R. 87. (1953). This Note is brought to you by the Law Reviews and Journals at Scholar Commons. It has been accepted for inclusion in South Carolina Law Review by an authorized editor of Scholar Commons. For more information, please contact [email protected]. Morgan: Misprison of Felony MISPRISION OF FELONY Misprision1 of felony has been defined in various ways, but per- haps its best definition is as follows: "Misprision of felony at common law is a criminal neglect either to prevent a felony from being committed or to bring the offender to justice after its com- mission, but without such previous concert with or subsequent assis- tance of him as will make the concealer an accessory before or after 12 the fact." In the modern use of the term, misprision of felony has been said to be almost, if not identically, the same offense as that of an acces- sory after the fact.3 It has also been stated that misprision is nothing more than a word used to describe a misdemeanor which does not possess a specific name.4 It is that offense of concealing a felony committed by another, but without such previous concert with or subsequent assistance to the felon as would make the concealing party an accessory before or after the fact.5 Misprision is distinguished from compounding an offense on the basis of consideration or amends; misprision is a bare concealment of crime, while compounding is a concealment for a reward by one 6 directly injured by the crime. -

Texas Law Review See Also
Texas Law Review See Also Response Taking It to the Streets Stuart P. Green* For more than fifty years, some of the best minds in criminal law theory have applied some of the most sophisticated tools of analysis in an effort to solve the seemingly insolvable blackmail paradox.1 Whether any of these theorists has been successful is debatable. In Competing Theories of Blackmail: An Empirical Research Critique of Criminal Law Theory, Paul Robinson, Michael Cahill, and Daniel Bartels advance the novel—dare I say, paradoxical—notion that one way to solve the problem is to ask a collection of laypersons, untutored in law or philosophy, what they think should count as blackmail.2 There is much about the article that is admirable: The way the authors derive concrete scenarios from abstract theories is ingenious; their summary of the various blackmail theories is a model of conciseness; the methodological techniques they use are exemplary. As is the norm for brief responses of this sort, however, I shall focus on what I perceive as the article’s shortcomings rather than its strengths. In so doing, I do not mean to minimize the authors’ achievement. * Professor of Law and Justice Nathan L. Jacobs Scholar, Rutgers School of Law–Newark. 1. The seminal piece is Glanville Williams, Blackmail, CRIM. L. REV. 79 (1954). See also, e.g., JOEL FEINBERG, HARMLESS WRONGDOING (1988); Mitchell N. Berman, The Evidentiary Theory of Blackmail: Taking Motives Seriously, 65 U. CHI. L. REV. 795 (1998); George P. Fletcher, Blackmail: The Paradigmatic Crime, 141 U. PA. L. REV. 1617 (1993); Leo Katz, Blackmail and Other Forms of Arm-Twisting, 141 U. -

602KB***Composition – Legal and Theoretical Foundations
462 Singapore Academy of Law Journal (2015) 27 SAcLJ COMPOSITION Legal and Theoretical Foundations The composition of offences has been an integral part of the Singapore criminal justice system from its inception. This article sets out the legal and theoretical foundations for composition, as well as its historical genesis within our Criminal Procedure Code – from its roots in English law to its statutory entrenchment in India and the Straits Settlements. The recent amendments to the Criminal Procedure Code and its effect on composition in our penal system will also be examined. Ryan David LIM LLB (Hons) (Nott); Deputy Public Prosecutor, Attorney-General’s Chambers, Singapore. Selene YAP BA (Hons) (National University of Singapore), JD (Melb); Deputy Public Prosecutor, Attorney-General’s Chambers, Singapore. I. Historical genesis of composition A. English common law1 1 At first blush, composition appears to be an aberration in criminal law. As K S Rajah observes in his article “Composition and Due Process”:2 A crime is regarded as a wrong done to society. The offender and the victim are not normally allowed to come to an agreement to absolve the offender from criminal responsibility. 2 Indeed, the compounding of a felony – a prosecutor or a victim accepting consideration in return for not prosecuting a felony – was an offence under English common law.3 The compounding of theft 1 For a comprehensive history of the composition of offences in English law, see Percy Henry Winfield, The Present Law of Abuse of Legal Procedure (Cambridge University Press, 2013) at p 117. 2 K S Rajah, “Composition and Due Process” (2004) Law Gazette <http://www.lawgazette.com.sg/2004-1/Jan04-col.htm> (accessed 3 June 2014). -

Copyright, Spleens, Blackmail, and Insider Trading
California Law Review VOL. 80 DECEMBER 1992 No.6 Copyright © 1992 by California Law Review, Inc. A Theory of Law and Information: Copyright, Spleens, Blackmail, and Insider Trading James Boyle TABLE OF CONTENTS Introduction ................................................... 1416 I. Four Puzzles ............................................ 1426 A. Copyright .......................................... 1426 B. Blackmail .......................................... 1428 C. Insider Trading ..................................... 1429 D. Spleens ............................................. 1429 II. Public and Private in the Liberal State ................... 1433 III. Information in the Liberal State ......................... 1437 IV. The Economics of Information .......................... 1443 V. Property in the Liberal State ............................ 1458 VI. Copyright .............................................. , 1461 VII. Blackmail ............................................... 1470 A. Economic Theories ................................. 1471 B. Libertarian Theories ................................ 1477 C. Third Party Theories ............................... 1481 D. Shared Problems ................................... 1483 VIII. Insider Trading ....................................' ..... 1488 A. Economic Analysis of Information Disparities ....... 1494 1. Baseline Errors. .. 1494 2. Ad Hoc Claims About Behavior ................. 1498 3. Ignoring Contradictions in the Theory ........... 1499 B. Insider Trading Law as a Puzzle ................... -

1 PUBLIC JUSTICE OFFENCES Hindering Investigations
PUBLIC JUSTICE OFFENCES Hindering investigations; concealing offences and attempting to pervert the course of justice Reasonable Cause Criminal Law CLE Conference 28 March 2015 Part 7 of the Crimes Act 1900 was introduced as a package of Public Justice Offences inserted into the Crimes Act in 1990.1 The purpose of the package was to create a comprehensive statement of the law relating to public justice offences which, until the enactment of the amendments, was described by the then Attorney General Mr John Dowd as “fragmented and confusing, consisting of various common law and statutory provisions, with many gaps, anomalies and uncertainties”.2 Part 7 Division 2 deals broadly with offences concerning the interference in the administration of justice. This paper does not aim to cover every aspect of the package of public justice offences but focuses on the principal offences incorporated within Division 2, being Ss. 315, 316 and 319 offences, and their common law equivalents. Background Up until 25 November 1990, the various common law offences including misprision of felony, hindering an investigation, compounding a felony and perverting the course of justice, to name a few, operated, until abolished by the Crimes (Public Justice) Amendment Act 19903. From 25 November 1990, Part 7 of the Crimes Act 1900 provided for ‘public justice offences’ broadly described as offences targeting interference with the administration 1 Inserted by the Crimes (Public Justice) Amendment Act 1990 (NSW) s 3, Sch 1. 2 New South Wales, Parliamentary Debates (Hansard) Legislative Assembly, 17 May 1990, the Hon JRA Dowd, Attorney General, Second Reading Speech at 3692. -
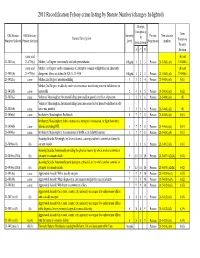
2011 Recodification Felony Crime Listing by Statute Number (Changes Hi-Lighted)
2011 Recodification Felony crime listing by Statute Number (changes hi-lighted) Attempt, Conspiracy, Old Statute Old Statutory Severity Person New statute New Statute Description & Number Violated Penalty Section Level Nonperson number Statutory Solicitation Penalty A C S Section same and (b) and 21-3401(a) 21-4706(c) Murder; 1st Degree; intentionally and with premeditation Off-grid 1 2 3 Person 21-5402(a)(1) 21-6806(c) same and Murder; 1st Degree; in the commission of, attempt to commit, or flight from an inherently (b) and 21-3401(b) 21-4706(c) dangerous felony as defined in K.S.A. 21-3436 Off-grid 1 2 3 Person 21-5402(a)(2) 21-6806(c) 21-3402(a) same Murder; 2nd Degree; intentional killing 1 3 3 4 Person 21-5403(a)(1) (b)(1) Murder; 2nd Degree; recklessly, under circumstances manifesting extreme indifference to 21-3402(b) same human life 2 4 4 5 Person 21-5403(a)(2) (b)(2) 21-3403(a) same Voluntary Manslaughter; Intentional killing upon sudden quarrel or in heat of passion 3 5 5 6 Person 21-5404(a)(1) (b) Voluntary Manslaughter; Intentional killing upon unreasonable but honest belief that deadly 21-3403(b) same force was justified 3 5 5 6 Person 21-5404(a)(2) (b) 21-3404(a) same Involuntary Manslaughter; Recklessly 5 7 7 8 Person 21-5405(a)(1) (b)(1) Involuntary Manslaughter; In the commission, attempted commission, or flight from other 21-3404(b) same felonies excluding DUI 5 7 7 8 Person 21-5405(a)(2) (b)(1) 21-3404(c) same Involuntary Manslaughter; In commission of lawful act in unlawful manner 5 7 7 8 Person 21-5405(a)(4) (b)(1)