Intelligence-Driven Computer Network Defense Informed by Analysis of Adversary Campaigns and Intrusion Kill Chains
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

FAQ About Recycling Cartons
FREQUENTLY ASKED QUESTIONS ABOUT CARTONS WHAT IS A CARTON? » Cartons are a type of packaging for food and beverage products you can purchase at the store. They are easy to recognize and are available in two types—shelf-stable and refrigerated. Shelf-stable cartons (types of products) Refrigerated (types of products) » Juice » Milk » Milk » Juice » Soy Milk » Cream » Soup and broth » Egg substitutes » Wine You will find these You will find these products in the chilled products on the shelves sections of grocery stores. in grocery stores. WHAT ARE CARTONS MADE FROM? » Cartons are mainly made from paper in the form of paperboard, as well as thin layers of polyethylene (plastic) and/or aluminum. Shelf-stable cartons contain on average 74% paper, 22% polyethylene and 4% aluminum. Refrigerated cartons contain about 80% paper and 20% polyethylene. ARE CARTONS RECYCLABLE? » Yes! Cartons are recyclable. In fact, the paper fiber contained in cartons is extremely valuable and useful to make new products. WHERE CAN I RECYCLE CARTONS? » To learn if your community accepts cartons for recycling, please visit RecycleCartons.com or check with your local recycling program. HOW DO I RECYCLE CARTONS? » Simply place the cartons in your recycle bin. If your recycling program collects materials as “single- stream,” you may place your cartons in your bin with all the other recyclables. If your recycling program collects materials as “dual-stream” (paper items together and plastic, metal and glass together), please place cartons with your plastic, metal and glass containers. WAIT, YOU JUST SAID CARTONS ARE MADE MAINLY FROM PAPER. Don’t I WANT TO PUT THEM WITH OTHER PAPER RECYCLABLES? » Good question. -

Automated Malware Analysis Report for Shellcode.Exe
ID: 205432 Sample Name: shellcode.exe Cookbook: default.jbs Time: 00:40:30 Date: 04/02/2020 Version: 28.0.0 Lapis Lazuli Table of Contents Table of Contents 2 Analysis Report shellcode.exe 3 Overview 3 General Information 3 Detection 3 Confidence 3 Classification 4 Analysis Advice 4 Mitre Att&ck Matrix 5 Signature Overview 5 AV Detection: 5 System Summary: 5 Data Obfuscation: 5 Malware Configuration 5 Behavior Graph 5 Simulations 6 Behavior and APIs 6 Antivirus, Machine Learning and Genetic Malware Detection 6 Initial Sample 6 Dropped Files 6 Unpacked PE Files 6 Domains 6 URLs 6 Yara Overview 7 Initial Sample 7 PCAP (Network Traffic) 7 Dropped Files 7 Memory Dumps 7 Unpacked PEs 7 Sigma Overview 7 Joe Sandbox View / Context 7 IPs 7 Domains 7 ASN 7 JA3 Fingerprints 7 Dropped Files 7 Created / dropped Files 8 Domains and IPs 8 Contacted Domains 8 Contacted IPs 8 Static File Info 8 General 8 File Icon 8 Static PE Info 8 General 8 Entrypoint Preview 9 Data Directories 10 Sections 10 Imports 11 Network Behavior 11 Code Manipulations 11 Statistics 11 System Behavior 11 Disassembly 11 Copyright Joe Security LLC 2020 Page 2 of 11 Analysis Report shellcode.exe Overview General Information Joe Sandbox Version: 28.0.0 Lapis Lazuli Analysis ID: 205432 Start date: 04.02.2020 Start time: 00:40:30 Joe Sandbox Product: CloudBasic Overall analysis duration: 0h 2m 15s Hypervisor based Inspection enabled: false Report type: light Sample file name: shellcode.exe Cookbook file name: default.jbs Analysis system description: Windows 10 64 bit (version 1803) -

Smashing the Stack for Fun and Profit
Introduction Since the famous article "Smashing the Stack for fun and profit" by aleph1 there have been countless papers about buffer overflows, why then should there be another one? Because I have read most of them and they lack the specifics of the technique, why everything happens and how to react in case of a change and why you have to react. Most of the papers out there are really notes. I can say that this has been explicitly written as a formal paper. Examples are made and also live examples are done of the different techniques and they all should work, if they don't drop me an email, although they have been tested on Slackware 7.0, 7.1 and RedHat 6.0, 6.2 and 7.0, all examples have been revisited on Slackware 9.0, RedHat 8.0 and Mandrake 9.0, Windows 2000 and Solaris on SPARC architecture. During this chapter we will have some standards, I'll use and example to illustrate them: nahual@fscking$ ./exploit1 [ + ] Example 1 for The Tao of Buffer Overflows [ + ] [ + ] Coded by Enrique A. Sanchez Montellano [ + ] Using address 0xbffff9c0 [ + ] Starting exploitation... bash# id As you can see now we've exploited the program uid=0(root) gid=0(root) bash# So as you can see user input will have this type of font, the computer will have normal and comments will have this type of font. And the Tao was born. Functions like strcpy(), strcat(), gets(), sprintf() and all its derivates can be dangerous if not used with care. Why are they not used with care?, Books and classes are not taught with security in mind, the concept of buffer overflows is a concept that is solely for security consultants and hackers, being the first a ramification of the later as far as a lot of people are concerned, so you need special skills to find them and exploit them. -

Different Perspectives for Assigning Weights to Determinants of Health
COUNTY HEALTH RANKINGS WORKING PAPER DIFFERENT PERSPECTIVES FOR ASSIGNING WEIGHTS TO DETERMINANTS OF HEALTH Bridget C. Booske Jessica K. Athens David A. Kindig Hyojun Park Patrick L. Remington FEBRUARY 2010 Table of Contents Summary .............................................................................................................................................................. 1 Historical Perspective ........................................................................................................................................ 2 Review of the Literature ................................................................................................................................... 4 Weighting Schemes Used by Other Rankings ............................................................................................... 5 Analytic Approach ............................................................................................................................................. 6 Pragmatic Approach .......................................................................................................................................... 8 References ........................................................................................................................................................... 9 Appendix 1: Weighting in Other Rankings .................................................................................................. 11 Appendix 2: Analysis of 2010 County Health Rankings Dataset ............................................................ -

Corrugated Board Structure: a Review M.C
ISSN: 2395-3594 IJAET International Journal of Application of Engineering and Technology Vol-2 No.-3 Corrugated Board Structure: A Review M.C. Kaushal1, V.K.Sirohiya2 and R.K.Rathore3 1 2 Assistant Prof. Mechanical Engineering Department, Gwalior Institute of Information Technology,Gwalior, Assistant Prof. Mechanical Engineering 3 Departments, Gwalior Engineering College, Gwalior, M. Tech students Maharanapratap College of Technology, Gwalior, [email protected] [email protected] [email protected] ABSTRACT Corrugated board is widely used in the packing industry. The main advantages are lightness, recyclability and low cost. This makes the material the best choice to produce containers devoted to the shipping of goods. Furthermore examples of structure design based on corrugated boards can be found in different fields. Structural analysis of paperboard components is a crucial topic in the design of containers. It is required to investigate their strength properties because they have to protect the goods contained from lateral crushing and compression loads due to stacking. However in this paper complete and detailed information are presented. Keywords: - corrugated boards, recyclability, compression loads. Smaller flutes offer printability advantages as well as I. INTRODUCTION structural advantages for retail packaging. Corrugated board is essentially a paper sandwich consisting of corrugated medium layered between inside II. HISTORY and outside linerboard. On the production side, corrugated In 1856 the first known corrugated material was patented is a sub-category of the paperboard industry, which is a for sweatband lining in top hats. During the following four sub-category of the paper industry, which is a sub-category decades other forms of corrugated material were used as of the forest products industry. -
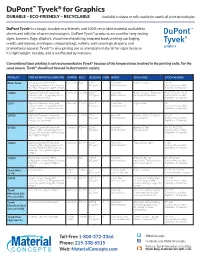
Tyvek Graphics Technical Data Sheet
DuPont ™ Tyvek ® for Graphics DURABLE – ECO-FRIENDLY – RECYCLABLE Available in sheets or rolls; usable for nearly all print technolo gies DuPont Tyvek a is a tough, durable, eco-friendly and 100% recyclable material available in sheets and rolls for all print technologies. DuPont Tyvek ® products are used for long-lasting signs, banners, flags, displays, visual merchandising, map and book printing, packaging, credit card sleeves, envelopes, shopping bags, wallets, wall coverings, drapery, and promotional apparel. Tyvek ® is also gaining use as a template material for signs because it is lightweight, durable, and is unaffected by moisture. Conventional laser printing is not recommended on Tyvek ® because of the temperatures involved in the printing units. For the same reason, Tyvek ® should not be used in electrostatic copiers. PRODUCT TYPE OF PRINTING USED FOR COATED MILS OZ. [GSM] CORE NOTES IDEAL USES STOCK WIDTHS Black Tyvek Flexography, Gravure, Offset Uncoated 5 mil 1.25 oz 2” Paper-like. Banners & Signs 36", 45" Lithography, Screen Process, UV-cure [42 gsm] Hard Structure Custom sizes available Inkjet (w/ testing due to lighter weight) Available in 10-yard rolls 1085D Digital on Demand, Flexography, Uncoated 10.3 mil 3.2 oz 3” Paper-like. Banners & Signs. Extra body 48.25", 57.125", 114.25" Gravure, Offset Lithography, Screen [109 gsm] Hard Structure for shape development. Custom sizes available Process, UV-cure Inkjet Available in 10-yard rolls 1079 Digital on Demand, Flexography, Uncoated 7.9 mil 2.85 oz 3” Paper-like. Tags & Labels 48" Gravure, Offset Lithography, Screen [97 gsm] Hard Structure Custom sizes available Process, Thermal Transfer, UV-cure Available in 10-yard rolls Inkjet 1073D Digital on Demand, Flexography, Uncoated 7.5 mil 2.2 oz 3” Paper-like. -

Label Liners: Meeting the Sustainability Challenge
Label liners: meeting the sustainability challenge By Mariya Nedelcheva, Product Manager Film & With ever-greater emphasis placed on packaging and waste reduction, Jenny Wassenaar, Compliance & Sustainability brand owners are looking for solutions that secure their sustainability Director, Avery Dennison credentials. Consumers pay particularly close attention to packaging, where there are significant environmental gains to be made. For example, waste from labelling can create useful by-products and circular economies. Waste is not always visible on the final packaging, but its impact on brand reputation is no less real. Consumers’ perceptions of a brand can be enhanced when sustainability is improved. label.averydennison.com Matrix Liner Final White paper waste waste label 16% 35% 37% Start-up waste plus Challenge printed End-user The challenge of recycling waste from the labelling process in error scrap - and ideally creating useful by-products - is complex. Many 10% 1% different elements must be addressed in order to move towards the ultimate goal of zero waste. For example, the word ‘recyclable’ can mean many things, and should not be viewed in isolation. Today there is a chance that recyclable products will still end up in landfill, so what matters is establishing genuinely viable end-to-end recycling solutions. That means considering every component within packaging, including where it comes from, how much material has been used, and what happens at every stage of the package’s journey through the value chain. This paper discusses how the sustainability of labelling laminates can be improved, with a particular focus on the label release liners that are left behind once labels have been dispensed. -

C-130J Super Hercules Program Status and Fast Facts Program Status
January 2020 C-130J Super Hercules Program Status and Fast Facts Program Status 24 Super Hercules Advantages The C-130J Super Hercules provides significant performance improvements and added operational capabilities that translate directly into increased ground and air combat effectiveness. Some of these attributes include the ability to: • Operate out of 2,000 ft. long dirt strips in high mountain ranges. • Carry tons of supplies more than 3,000 miles and deliver “the last mile” to remote operating bases, keeping trucks off dangerous highways. • Perform in-flight refueling, ground fueling, weather reconnaissance, electronic warfare, medical evacuation, search and rescue, paradrop, maritime mission, special operations and many other missions. • Generate much greater operational efficiencies. The C-130J outperforms older C-130s in combat operations by at least a 2:1 margin. • Operate with only two pilots and one loadmaster for most missions, exposing fewer flight crew members to potential combat threats. • Demonstrate reliability that far exceeds most other military aircraft with average mission capable rates routinely in the 80-to-90% range. One Aircraft, Many Capabilities Electronic Air Drop Intelligence, Humanitarian Combat Aeromedical Aerial Search Commercial Surveillance Surveillance & Delivery Refueling & Rescue Freighter Reconnaissance Communication Aerial Personnel Recovery Weather Gunship Maritime Special Passenger Special Ops Personnel Ground Firefighting Reconnaissance Surveillance Accommodations Transport Refueling Super Hercules -

Network Security Project Buffer Overflow Exploitation
Network Security Project Buffer Overflow Exploitation Samuele Andreoli Nicol`oFornari Giuseppe Vitto Abstract In computer security a buffer overflow is an anomaly where a program, while writing data to a buffer, overruns the buffer’s boundary and overwrites adjacent memory locations. This is a special case of the violation of memory safety. Buffer overflows can alter the way the program operates. This may result in erratic program be- havior, including memory access errors, incorrect results, crashes or a breach in system security. Thus, they are the basis of many software vulnerabilities and can be maliciously exploited. [1] Buffer overflow is a complex and broad topic which requires a solid background in memory man- agement and code execution to be understood (i.e. registers, jumps, interrupts, stack frames). In this project we try to give a taste of stack-based buffer overflow putting our efforts into achieving a linear and relatively simple explanation of the topic. Report layout In Section 1 we describe all the technical details of our working environment. In Section 2 we recall some theoretical background about pointers, registers, etc. With Section 3 the lab starts: we briefly explain how the memory works by introducing gdb, which will be fundamental for the rest of the exercises 1. In Section 4 we present a first buffer overflow that allows the user to access a function which is not intended to be invoked. This is done by overwriting the value of a function pointer. In Section 5 we exploit a buffer overflow in order to execute a shellcode. The main reference for this part is the ground-breaking article Smashing The Stack For Fun And Profit by Aleph One [2]. -

C-130J-Sof International Special Operations Forces Configurations
C-130J-SOF INTERNATIONAL SPECIAL OPERATIONS FORCES CONFIGURATIONS Lockheed Martin Aeronautics Company 86 South Cobb Drive Marietta, Georgia 30063 www.lockheedmartin.com MG170335-003 © 2017 Lockheed Martin Corporation. All rights reserved. PIRA# AER201706008 When the need for security cannot be compromised, a PROVEN solution must be selected. With increasing and evolving global threats, precise use of POWER provides security. In a confusing and rapidly-changing environment, PRECISION and SKILL are force multipliers for peace. These are the moments and missions where failure is not an option. Now is when special operations forces (SOF) are called upon toPROTECT your today and your tomorrows. There is one solution that fully supports all special missions needs, fferingo versatility, endurance, command and control, surveillance and protection. Feared by enemies. Guardian of friendly forces. A global force multiplier. It is the world’s ultimate special missions asset. INTRODUCING THE C-130J-SOF. THE NEWEST MEMBER OF THE SUPER HERCULES FAMILY. SPECIAL OPERATIONS AIRCRAFT FOR THE 21ST CENTURY The C-130J-SOF provides specialized intelligence, surveillance, and reconnaissance (ISR) support, along with infiltration, C-130J-SOF exfiltration, and re-supply of special operations forces (SOF) and equipment in hostile or denied territory. With added special mission equipment options, the C-130J-SOF may be configured to execute armed overwatch, precision strike, helicopter and vertical lift aerial refueling, psychological operations, high-speed/low-signature -

U.S. Postal Service Mail Addressing Guidelines
U.S. Postal Service Mail Addressing Guidelines Address Placement Placement of the address on the face of an envelope should conform to the following U. S. Postal Service specifications. • The address should be in an area, one inch from each side of the envelope. • The top of the address should be no more than 2 3/4 inches from the bottom of the envelope and the bottom no more than 5/8's of an inch from the bottom of the envelope. • The area 4 1/2 inches by 5/8 's of an inch in the lower right hand corner of the envelope MUST remain empty for bar code placement for any maul that is processed by the Mail Center. Enclosures Correspondence Mail of any kind for transport by the U. S. Postal Service must be enclosed in an appropriate envelope or parcel and sealed. The type of enclosures determine the mailing classification. Non-mailables Several items are listed by the U. S. Postal Service as non-mailable in envelopes: • paper clips • metal pieces • glass, chips • sand. These can jam or damage the mailing machines and can cause serious injury to Mail Center and Postal employees. The following are also classified as non-mailables and subject to return to sender: envelopes and cards less than 3 1/2 inches in height or 5 inches in length. It is recommended that when mailing questionable items to U. S. or foreign destinations, the mailer should contact the Mail Center for assistance. All foreign countries also impose various restrictions. Brochures, letters and newsletters being mailed without an envelope must be folded consistently and must be tabbed with the recommended number of tabs. -

The HP Molded Fiber Advanced Tooling Solution White Paper | the HP Molded Fiber Advanced Tooling Solution
White paper The HP Molded Fiber Advanced Tooling Solution White paper | The HP Molded Fiber Advanced Tooling Solution Macrotrends driving the packaging market The packaging market is transitioning from foam/plastic to molded fiber (also known as molded pulp) packaging for sustainability reasons, with environmental packaging (i.e., replacing foam with paper) favoring the growth of this segment. The molded fiber packaging market is a worldwide industry, valued at $8 billion, and is the fastest-growing segment in the packaging market, with growth being fueled by growing consumer demand for sustainable and environmentally friendly packaging solutions, as well as the increase in take-out food and e-commerce.1 Asia-Pacific countries (APAC) are the biggest geographical market, especially China, Hong Kong, and Taiwan. The region is experiencing the highest growth and is expected to be the largest market by 2024. This growth can be attributed to the rising importance of disposable packaging,2 as well as the lower cost of tooling production in these areas, which presents a significant price advantage over other regions. The primary segments currently are food and beverage and electronics, which are estimated to have the highest growth. The increasing use of molded pulp products for the packaging of various electronic products (including mobile phones and accessories, computers, printers, modems, trimmers, and projectors, among others) due to its convenience, improved sustainability, and low cost are some of the factors contributing to the growth of this segment.2 Molded fiber manufacturing The thermoformed tooling segment is expected to outgrow other segments, propelled by increased consumer demand for high-quality molded fiber packaging and ongoing innovation driving down thermoforming-packaging manufacturing costs.