Security in Computing
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

CHERI Concentrate: Practical Compressed Capabilities
1 CHERI Concentrate: Practical Compressed Capabilities Jonathan Woodruff, Alexandre Joannou, Hongyan Xia, Anthony Fox, Robert Norton, Thomas Bauereiss, David Chisnall, Brooks Davis, Khilan Gudka, Nathaniel W. Filardo, A. Theodore Markettos, Michael Roe, Peter G. Neumann, Robert N. M. Watson, Simon W. Moore Abstract—We present CHERI Concentrate, a new fat-pointer compression scheme applied to CHERI, the most developed capability-pointer system at present. Capability fat pointers are a primary candidate to enforce fine-grained and non-bypassable security properties in future computer systems, although increased pointer size can severely affect performance. Thus, several proposals for capability compression have been suggested elsewhere that do not support legacy instruction sets, ignore features critical to the existing software base, and also introduce design inefficiencies to RISC-style processor pipelines. CHERI Concentrate improves on the state-of-the-art region-encoding efficiency, solves important pipeline problems, and eases semantic restrictions of compressed encoding, allowing it to protect a full legacy software stack. We present the first quantitative analysis of compiled capability code, which we use to guide the design of the encoding format. We analyze and extend logic from the open-source CHERI prototype processor design on FPGA to demonstrate encoding efficiency, minimize delay of pointer arithmetic, and eliminate additional load-to-use delay. To verify correctness of our proposed high-performance logic, we present a HOL4 machine-checked proof of the decode and pointer-modify operations. Finally, we measure a 50% to 75% reduction in L2 misses for many compiled C-language benchmarks running under a commodity operating system using compressed 128-bit and 64-bit formats, demonstrating both compatibility with and increased performance over the uncompressed, 256-bit format. -

R00456--FM Getting up to Speed
GETTING UP TO SPEED THE FUTURE OF SUPERCOMPUTING Susan L. Graham, Marc Snir, and Cynthia A. Patterson, Editors Committee on the Future of Supercomputing Computer Science and Telecommunications Board Division on Engineering and Physical Sciences THE NATIONAL ACADEMIES PRESS Washington, D.C. www.nap.edu THE NATIONAL ACADEMIES PRESS 500 Fifth Street, N.W. Washington, DC 20001 NOTICE: The project that is the subject of this report was approved by the Gov- erning Board of the National Research Council, whose members are drawn from the councils of the National Academy of Sciences, the National Academy of Engi- neering, and the Institute of Medicine. The members of the committee responsible for the report were chosen for their special competences and with regard for ap- propriate balance. Support for this project was provided by the Department of Energy under Spon- sor Award No. DE-AT01-03NA00106. Any opinions, findings, conclusions, or recommendations expressed in this publication are those of the authors and do not necessarily reflect the views of the organizations that provided support for the project. International Standard Book Number 0-309-09502-6 (Book) International Standard Book Number 0-309-54679-6 (PDF) Library of Congress Catalog Card Number 2004118086 Cover designed by Jennifer Bishop. Cover images (clockwise from top right, front to back) 1. Exploding star. Scientific Discovery through Advanced Computing (SciDAC) Center for Supernova Research, U.S. Department of Energy, Office of Science. 2. Hurricane Frances, September 5, 2004, taken by GOES-12 satellite, 1 km visible imagery. U.S. National Oceanographic and Atmospheric Administration. 3. Large-eddy simulation of a Rayleigh-Taylor instability run on the Lawrence Livermore National Laboratory MCR Linux cluster in July 2003. -

Antikernel: a Decentralized Secure Hardware-Software Operating System Architecture
Antikernel: A Decentralized Secure Hardware-Software Operating System Architecture Andrew Zonenberg1 and B¨ulent Yener2 1 IOActive Inc., Seattle WA 98105, USA, [email protected] 2 Rensselaer Polytechnic Institute, Troy NY 12180, USA, [email protected] Abstract. The \kernel" model has been part of operating system ar- chitecture for decades, but upon closer inspection it clearly violates the principle of least required privilege. The kernel is a single entity which provides many services (memory management, interfacing to drivers, context switching, IPC) having no real relation to each other, and has the ability to observe or tamper with all state of the system. This work presents Antikernel, a novel operating system architecture consisting of both hardware and software components and designed to be fundamen- tally more secure than the state of the art. To make formal verification easier, and improve parallelism, the Antikernel system is highly modular and consists of many independent hardware state machines (one or more of which may be a general-purpose CPU running application or systems software) connected by a packet-switched network-on-chip (NoC). We create and verify an FPGA-based prototype of the system. Keywords: network on chip · system on chip · security · operating sys- tems · hardware accelerators 1 Introduction The Antikernel architecture is intended to be more, yet less, than simply a \ker- nel in hardware". By breaking up functionality and decentralizing as much as possible we aim to create a platform that allows applications to pick and choose the OS features they wish to use, thus reducing their attack surface dramati- cally compared to a conventional OS (and potentially experiencing significant performance gains, as in an exokernel).3 Antikernel is a decentralized architecture with no system calls; all OS func- tionality is accessed through message passing directly to the relevant service. -
Silicon Forest Universe
15239 Poster 9/16/02 1:03 PM Page 1 AB CDE FGH I JKL M N O P Q R S Pearlsoft COMSAT General Integrated Systems Ashwood Group '85 Qualis Design fka CPU International Nel-Tech Development '98 Qsent '01 Briefsmart.com '00 Relyent TrueDisk Trivium Systems '80 '74 '99 '90 Gearbeat '81 Relational Systems Galois 3DLand Teradyne in 2001 '85 '00 '98 Solution Logic SwiftView Imagenation '89 Metro One IronSpire '84 Smart Mediary Systems Connections 13 Telecommunications WireX GenRad in 1996 '00 CyberOptics E-Core Salu Logiplex '79 MyHealthBank Semiconductor Cotelligent Technologies Fujitsu America Barco Metheus '77 '99 Group Knowledge fka United Data Biotronik Timlick & Associates in 1999 Gadget Labs Adaptive Solutions Wave International Processing Cascade Laser '98 Webridge Axis Clinical Software Mitron Basicon '91 GemStone fka Servio Logic Source Services '83 Integra Telecom Accredo FaxBack Polyserve Metheus Intersolv Babcock & Jenkins Electro '79 Informedics Scientific Sliceware Graphic Software Systems Industries IBM 12 in 1999 Atlas Telecom 1944 Sequent Computer ProSight Credence in 2001 19 ADC Kentrox '78 Oracle '69 Merant Datricon 60s Informix Systems FEI Sage Software fka Polytron MKTX 197 Mikros Nike 0s Etec Systems '63 19 Sentrol in 1995 Intel 80s SEH America Teseda Oregon Graduate Institute Flight Dynamics 1976 '97 1990 Purchasing Solutions Fluence ~ Relcom Vidco Mushroom Resources Cunningham & Cunningham '99 Myteam.com Praegitzer Industries Integrated Measurement Systems Zicon Digital World Lucy.Com Nonbox in 2001 ATEQ 11 Software Access -

Targeting AVX-Enabled Processors Using PGI Compilers and Tools
Targeting AVX-Enabled Processors Using PGI Compilers and Tools Brent Leback, John Merlin, and Steven Nakamoto, The Portland Group (PGI) ABSTRACT: AMD and Intel are releasing new microprocessors in 2011 with extended AVX support. In this paper we show examples of compiler code generation and new library and tools capabilities which support these new processors. We also discuss performance issues, comparing the new platforms versus previous generations. KEYWORDS: Compiler, Optimization, Micro-architecture The next year, at CUG 2008, we presented a paper 1. Introduction that studied the ratio of data bandwidth to peak floating point performance on x64 processors [3]. That year, the At CUG 2007 co-authors of this paper presented the first quad-core chips were beginning to show up from characteristics and performance of the first and second AMD and Intel. Most importantly, we showed that the generation x64 processors from AMD and Intel [1]. In peak transfer rate to and from memory divided by the particular, these second generation micro-architectures, peak floating point performance had trended dramatically the AMD “Barcelona” and the Intel “Woodcrest”, were downward over the generations of x64 processors, the first to use 128-bit wide data paths and floating point beginning in 2003. Also in 2008, both Intel and AMD units. For the first time on the x86 architecture, announced future chips, and it was feared that the trend vectorization of double-precision codes could enable a 2x would continue. In May of 2008, we expected these new speedup over non-vectorized, a.k.a. scalar, codes. chips to show up in roughly 12 to 18 months, before the Vectorization [2] for x64 processors is used to end of 2009. -

Steve Tolopka – the Beat Goes
Steve Tolopka – The Beat Goes On! Editor’s Note: Steve told and wrote his own story showing not only a great transition from engineering to retirement, but a great talent as a writer! Former Senior Principal Engineer Steve Tolopka retired from Intel Labs at the end of 2010 after nearly three decades with the company. He can’t figure out why on earth people ask him “Are you enjoying retirement?” Steve joined Intel in 1981 as a systems software engineer with a Ph.D. in Computer Science from Purdue University, becoming chief architect of the Intel 80960XA processor’s capability-oriented, fault- tolerant, distributed operating system and earning an individual Intel Achievement Award. In 1988 he became part of the team that formed BiiN, Intel’s joint venture with Siemens AG, to further develop and market 80960XA-based systems. Steve’s first lesson that “great technology isn’t enough for great products” hit home when BiiN was dissolved just fifteen months later. After rejoining the “Intel mothership” as part of the group that over time became Intel Labs, Steve worked as a manager and individual contributor at various points of his career. His professional Ready to take the field at the Northwest background at Intel Labs includes Computer Association for the Performing Arts Supported Collaboration, videoconferencing Marching Band Championship technology, networking technologies including the WinSock 2 specification, usage models and technology enablers for the Digital Home, and improved PC manageability, where he landed a second Intel Achievement Award as part of the team that created the Wired for Management Baseline Specification. -

A Brief History of Intel CPU Microarchitectures
All the contents in this presentation come from the public Internet, belong to their respective owners. This work is licensed under the Creative Commons Attribution-ShareAlike 3.0 Unported License. A Brief History of Intel CPU Microarchitectures Xiao-Feng Li [email protected] 2013-02-10 Notes • The materials are only for my personal use. – Not representing Intel opinions – Not a complete list of Intel microprocessors – Not specifications of Intel microprocessors Brief history of Intel CPU uArch - 2013/02/10 2 [email protected] Intel Pre-Processor Devices • Intel founded in 1968 • Intel 3101, 1969 – Intel first product – World first solid state memory device – 16 x 4-bit SRAM • Intel 1103, 1970 – World first DRAM product, 1K-bit PMOS – Used in HP 9800 series computers – By 1972, world bestselling memory chip, defeating magnetic memory Brief history of Intel CPU uArch - 2013/02/10 3 [email protected] Moore’s Law • Moore, Gordon E. (1965). "Cramming more components onto integrated circuits" (PDF). Electronics Magazine. pp. 4. – “The complexity for minimum component costs has increased at a rate of roughly a factor of two per year.” – Moore refined it to “every two years” in 1975 – Also quoted as “every 18 months” by David House, (referring to performance) – Most popular formulation: #transistors/IC • Carver Mead coined it as Moore's law around 1970 – “Tall & Thin engineers” • Ultimate limit of Moore’s Law – No one knows – How to use the capability? Resource limit? Brief history of Intel CPU uArch - 2013/02/10 4 [email protected] -
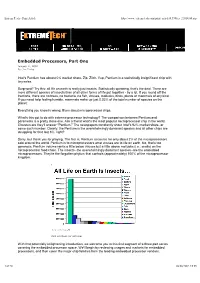
Embedded Processors, Part One January 11, 2002 By: Jim Turley
ExtremeTech - Print Article http://www.extremetech.com/print_article/0,3998,a=21014,00.asp Embedded Processors, Part One January 11, 2002 By: Jim Turley Intel's Pentium has almost 0% market share. Zip. Zilch. Yup, Pentium is a statistically insignificant chip with tiny sales. Surprised? Try this: all life on earth is really just insects. Statistically speaking, that's the deal. There are more different species of insects than of all other forms of life put together - by a lot. If you round off the fractions, there are no trees, no bacteria, no fish, viruses, mollusks, birds, plants or mammals of any kind. If you need help feeling humble, mammals make up just 0.03% of the total number of species on the planet. Everything you know is wrong. Even about microprocessor chips. What's this got to do with extreme processor technology? The comparison between Pentium and paramecia is a pretty close one. Ask a friend what's the most popular microprocessor chip in the world. Chances are they'll answer "Pentium." The newspapers constantly shout Intel's 92% market share, or some such number. Clearly, the Pentium is the overwhelmingly dominant species and all other chips are struggling for that last 8%, right? Sorry, but thank you for playing. The fact is, Pentium accounts for only about 2% of the microprocessors sold around the world. Pentium is to microprocessors what viruses are to life on earth. No, that's too generous. Pentium volume ranks a little below viruses but a little above mollusks (i.e., snails) on the microprocessor food chain. -

Portland Daily Press: November 16,1888
ESTABLISHED JUNE 23, 1862--V0L. 27. PORTLAND, MAINE, FRIDAY MORNING, NOVEMBER 16, 1888. PRICE THREE CENTS. DPECIU, NOTICES. WmCilitAKKIHig. MR. BLAINE IN THE NEXT CABINET. Interests combined is about 47 per cent.; OUR NEW REPRESENTATIVE IN ENGLAND hundred is ridiculous. There can be no more POWDERLY LOOKS FORWARD WITH HOPE very unceremonious and ungraceful appear- CHARGEO UPON BY MOUNTED POLICE that the manufacturing interests alone are recounts by ballot In New York city. Under ance through the parlor ceiling. She was in protected to the amount of 55 per cent., the law, the ballots there are already de- the attic, which Is unfinished, and stumbling, while the average on agricultural products Plush Garments Steamed Milliken Tells He The Marriage of Miss Endicott to stroyed. All that remains of the official After the Most Discouraging Year In one foot went down between the floor beams, Str.klng Brooklyn Horae Car Men Whole.'! Congressman Why is only about 20 per cent. This NO RIPPING inequality count is the the canvassers breaking down the celling. Four la- REQUIRED. Should Be has existed altogether too and al- Mr. Joseph Chamberlain. compilation by His Experience. young Resist the Officers. There, long, at next Tuesday. That consists dies were in the parlor below. They were our instructors inform us Albany though political of a verification of the tables returned somewhat surprised by the breaking of the that the "home market” which manufac- simply to the canvassers irom their districts. These of laths, the falling of plastering, and the intro- FOSTER’S FOREST CITY DYE HOUSE, And the New York Press that turing industries give to agriculture should A Ceremeny Witnessed The Annual Report of the Leader Volleys of Stones Thrown Against Reports Quiet by canvassers have no ballots to count; their duction of a woman's limb, which protruded atone in a great measure for this No. -

Cisco IOS Bridging Command Reference November 2011
Cisco IOS Bridging Command Reference November 2011 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387) Fax: 408 527-0883 THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL STATEMENTS, INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL ARE BELIEVED TO BE ACCURATE BUT ARE PRESENTED WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED. USERS MUST TAKE FULL RESPONSIBILITY FOR THEIR APPLICATION OF ANY PRODUCTS. THE SOFTWARE LICENSE AND LIMITED WARRANTY FOR THE ACCOMPANYING PRODUCT ARE SET FORTH IN THE INFORMATION PACKET THAT SHIPPED WITH THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO LOCATE THE SOFTWARE LICENSE OR LIMITED WARRANTY, CONTACT YOUR CISCO REPRESENTATIVE FOR A COPY. The Cisco implementation of TCP header compression is an adaptation of a program developed by the University of California, Berkeley (UCB) as part of UCB’s public domain version of the UNIX operating system. All rights reserved. Copyright © 1981, Regents of the University of California. NOTWITHSTANDING ANY OTHER WARRANTY HEREIN, ALL DOCUMENT FILES AND SOFTWARE OF THESE SUPPLIERS ARE PROVIDED “AS IS” WITH ALL FAULTS. CISCO AND THE ABOVE-NAMED SUPPLIERS DISCLAIM ALL WARRANTIES, EXPRESSED OR IMPLIED, INCLUDING, WITHOUT LIMITATION, THOSE OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OR ARISING FROM A COURSE OF DEALING, USAGE, OR TRADE PRACTICE. IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL DAMAGES, INCLUDING, WITHOUT LIMITATION, LOST PROFITS OR LOSS OR DAMAGE TO DATA ARISING OUT OF THE USE OR INABILITY TO USE THIS MANUAL, EVEN IF CISCO OR ITS SUPPLIERS HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. -

Biintm SYSTEMS OVERVIEW TM
BiiNTM SYSTEMS OVERVIEW TM BiiNTM SYSTEMS OVERVIEW Order Code: 6AN9000-1AJOO-OBA2 LIMITED DISTRIBUTION MANUAL This manual Is for customers who receive preliminary ver sions of this product. It may contain material subject to change. BIINTM 2111 NE 25th Ave. Hillsboro, OR 97124 © 1988, BiiNTM PRELIMINARY REV. REVISION HISTORY DATE -001 Preliminary Edition 7/88 BiiNTM MAKES NO WARRANTY OF ANY KIND WITH REGARD TO THIS MANUAL, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF :MERCHANTABll..ITY AND FITNESS FOR A PARTICULAR PURPOSE. BiiNN assumes no responsibility for any errors that may appear in this documenL B~ makes no commitment to update nor to keep current the infonnation contained in this documenL No part of this document may be copied or reproduced in any fonn or by any means without written consent of BiiNN. BiiNN retains the right to make changes to these specifications at any time, without notice. The following are trademarks of BiiNTlI: BiiN, BiiN/OS, BiiN/UX, BiiN Series 20, BiiN Series 40. BiiN Series 60, BiiN Series SO. Apple and MacTenninal are trademarks of Apple Computer. Inc. UNIX is a trademark of AT&T Bell Laboratories. Torx is a trademark of Camcar Screw and Mfg. Ada is a certification mark of the Department of Defense, Ada Joint Program Office. DEC, VT100, and VAX are trademarks of Digital Equipment Corporation. Smartmodem is a trademark of Hayes Corporation. mM is a trademark of Intemational Business Machines, Inc. MULTm US is a registered trademark of Intel Corporation. Macintosh is a trademark of McIntosh Laboratory, Inc. Microsoft is a registered trademark of Microsoft Corporation. -

Analyzing Computer Security
Analyzing Computer Security This page intentionally left blank AnAlyzing Computer SeCurity A ThreAT / VulnerAbiliTy / CounTermeAsure Approach Charles P. Pfleeger Shari Lawrence Pfleeger Pfleeger Consulting Group Dartmouth College Upper Saddle River, NJ • Boston • Indianapolis • San Francisco New York • Toronto • Montreal • London • Munich • Paris • Madrid Capetown • Sydney • Tokyo • Singapore • Mexico City Many of the designations used by manufacturers and sellers to distinguish their products are Publisher claimed as trademarks. Where those designations appear in this book, and the publisher was Paul Boger aware of a trademark claim, the designations have been printed with initial capital letters or Acquisitions Editor in all capitals. Bernard Goodwin The authors and publisher have taken care in the preparation of this book, but make no Managing Editor expressed or implied warranty of any kind and assume no responsibility for errors or John Fuller omissions. No liability is assumed for incidental or consequential damages in connection Full-Service Production with or arising out of the use of the information or programs contained herein. Manager The publisher offers excellent discounts on this book when ordered in quantity for bulk Julie B. Nahil purchases or special sales, which may include electronic versions and/or custom covers and Project Manager content particular to your business, training goals, marketing focus, and branding interests. LaurelTech For more information, please contact: Copy Editor U.S. Corporate and Government Sales Mary Lou Nohr (800) 382-3419 Proofreader [email protected] LaurelTech For sales outside the United States, please contact: Editorial Assistant Michelle Housley International Sales [email protected] Cover Designer Chuti Prasertsith Visit us on the Web: informit.com Compositor Library of Congress Cataloging-in-Publication Data LaurelTech Pfleeger, Charles P., 1948– Analyzing computer security : a threat/vulnerability/countermeasure approach / Charles P.