Efficient Authentication and Key Agreement Procedure in Ip Multimedia Subsystem for Umts
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Durastrip Select Ip20
PRODUCT DATASHEET Cod. 05U402424IN DURASTRIP SELECT IP20 * Ra> 90 * Excellent luminous efficiency and an emission able to replace fluorescence in most applications, with the additional benefit of versatility. * Extreme long life and absence of maintenance. * Absence of UV emission. * Ease of application: it can be fixed with the 3M® double-sided tape, the strip is provided with. * Cutting distance: 10 cm on 25W and 60W and 5cm on 96W. * 5 meters package for 25W and 60W wattages; 4 meters on the 96W reel. * Wattage below indicated is intended for the whole reel. * IP20: suitable for dry locations. INSTRUCTION FOR USE * Max current for single power supply: 4A. * Do not use this item with electronic transformers for halogen lamps: it is recommended the use of the drivers indicated. ACCESSORIES Additional connect and junction kit, please chose according to wattage: * KT05IN-CON ; SELECT IP20 Connector (5 pcs) for 25W strip * KT05IN-CON-HP ; SELECT IP20 Connector (5 pcs) for 60W strip * KT05IN-JUN ; SELECT IP20 Junction between 2 strips (5 pcs) for 25W strip * KT05IN-JUN-HP ; SELECT IP20 Junction between 2 strips (5 pcs) for 60W strip . Item Characteristics Code 05U402424IN Lamp Voltage 24V DC V Nominal Power 96 W Base Cavi liberi / Loose wire Flux 9000 LUMEN Input voltage 24V DC Light Tonality Natural white Colour temperature 4000 K Opening beam 120° Lenght 4000 mm Lenght 1 8 mm Lenght 2 3 mm Weight 75 g LED Number 480 All parts of this document are Duralamp ownership. All rights reserved. This document and the included information are provided without any responsibility deriving from mistakes or omissions. -

A Fuzzy Traffic Assignment Algorithm Based on Driver Perceived Travel Time of Network Links
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Elsevier - Publisher Connector Scientia Iranica A (2011) 18 (2), 190–197 Sharif University of Technology Scientia Iranica Transactions A: Civil Engineering www.sciencedirect.com A fuzzy traffic assignment algorithm based on driver perceived travel time of network links H. Ramazani a, Y. Shafahi b, S.E. Seyedabrishami b,∗ a Department of Civil and Environmental Engineering, B106 Newmark Civil Engineering Laboratory, University of Illinois at Urbana-Champaign, Urbana, IL 61801, USA b Department of Civil Engineering, Sharif University of Technology, Tehran, P.O. Box 11155-9313, Iran KEYWORDS Abstract Traffic assignment is a step of travel demand estimation. Given a trip origin–destination demand Assignment; matrix, this step determines traffic flow in each link, according to assumptions based on the behavior Fuzzy set; of drivers. Conventional assignment algorithms, which are mostly based on the Wardrop first principle Perceived travel time; of user equilibrium, assume that all drivers choose the shortest path to the destination, based on the Route choice; same travel time computed by travel time functions. However, in reality, driver perception of travel time Uncertainty. varies for a specific route. This paper presents a traffic assignment algorithm which assumes that driver perception of travel time affects route choices. Fuzzy set theory is used to define travel time perceived by drivers. A fuzzy equilibrium is suggested for the prediction of network flows. Next, a Fuzzy Incremental Traffic Assignment algorithm (FITA) is developed to utilize route Perceived Travel Time (PTT) for reaching the suggested fuzzy equilibrium. -

Technical Reference Manual for the Standardization of Geographical Names United Nations Group of Experts on Geographical Names
ST/ESA/STAT/SER.M/87 Department of Economic and Social Affairs Statistics Division Technical reference manual for the standardization of geographical names United Nations Group of Experts on Geographical Names United Nations New York, 2007 The Department of Economic and Social Affairs of the United Nations Secretariat is a vital interface between global policies in the economic, social and environmental spheres and national action. The Department works in three main interlinked areas: (i) it compiles, generates and analyses a wide range of economic, social and environmental data and information on which Member States of the United Nations draw to review common problems and to take stock of policy options; (ii) it facilitates the negotiations of Member States in many intergovernmental bodies on joint courses of action to address ongoing or emerging global challenges; and (iii) it advises interested Governments on the ways and means of translating policy frameworks developed in United Nations conferences and summits into programmes at the country level and, through technical assistance, helps build national capacities. NOTE The designations employed and the presentation of material in the present publication do not imply the expression of any opinion whatsoever on the part of the Secretariat of the United Nations concerning the legal status of any country, territory, city or area or of its authorities, or concerning the delimitation of its frontiers or boundaries. The term “country” as used in the text of this publication also refers, as appropriate, to territories or areas. Symbols of United Nations documents are composed of capital letters combined with figures. ST/ESA/STAT/SER.M/87 UNITED NATIONS PUBLICATION Sales No. -

001148/EU XXVII. GP Eingelangt Am 31/10/19
001148/EU XXVII. GP Eingelangt am 31/10/19 Council of the European Union Brussels, 31 October 2019 (OR. en) 6365/14 ADD 1 DCL 1 DATAPROTECT 25 JAI 80 MI 145 FREMP 24 RELEX 114 DECLASSIFICATION of document: 6365/14 ADD 1 RESTREINT UE/EU RESTRICTED dated: 14 February 2014 new status: Public Subject: Negotiations on the modernisation of the Council of Europe Convention for the Protection of Individuals with regard to Automatic Processing of personal data (EST 108) - Follow-up of the CAHDATA meeting on 12-14 November 2013 and - preparation of CAHDATA meeting on 28-30 April 2014 Delegations will find attached the declassified version of the above document. The text of this document is identical to the previous version. 6365/14 ADD 1 DCL 1 ni SMART.2.C.S1 EN www.parlament.gv.at RESTREINT UE/EU RESTRICTED COUNCIL OF Brussels, 14 February 2014 THE EUROPEAN UNION 6365/14 ADD 1 RESTREINT UE/EU RESTRICTEDR DATAPROTECTDATAPRROTTECCT 2525 JAIJAI 800 MI 1451445 FREMPFRREME P 2424 RELEXREELELEX 114111 4 NOTE from: Commissionission ServicesServices to: Delegationstions Subject: Negotiationsations on the modernisation of ththee CouncilCoounccilil ofof EuropeEurope Convention for the Protectionion of Individuals with regarregardd tto AutomaticAutomo aatiic Processing of personalpersona data (EST 108)08) - Follow-upw-up of the CCAHDATAAHDATA meetingmeeetinng ono 12-1412-14 NovemberNovember 2013 andand - preparationration of CAHDATACAHDATA memeetingeete ining on 28-3028-330 April 20120144 The delegations wwillill find in the AAnnexnnnexe a tatableabble ffofollowingllowing ththee CCAHDATAAHDATA mmeetingeeting oon 12-14 November 2013 aandnd in view off tthehe CCAHDATAAHHDAATA mmeetingeeting on 2828-30-30 April 20142014. -
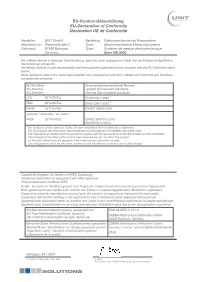
EU-Konformitätserklärung EU-Declaration of Conformity Déclaration UE De Conformité
EU-Konformitätserklärung EU-Declaration of Conformity Déclaration UE de Conformité Hersteller: UWT GmbH Gerätetyp: Elektromechanisches Messsystem Manufacturer: Westendstraße 5 Type: Electromechanical Measuring system Fabricant: 87488 Betzigau Type: Système de mesure électromécanique Germany Serie NB 3000 Wir erklären hiermit in alleiniger Verantwortung, dass das oben angegebene Gerät den nachfolgend aufgeführten EU-Richtlinien entspricht: We hereby declare in sole responsibility that the equipment specified above complies with the EU Directives listed below: Nous déclarons sous notre seule responsabilité que l'équipement spécifié ci-dessus est conforme aux directives européennes suivantes: EU-Richtlinie Angewandte (harmonisierte) Normen EU Directive Applied (harmonized) standards EU Directive Normes (harmonisées) appliqués LVD 2014/35/EU EN 61010-1:2010 1 EMC 2014/30/EU EN 61326-1:2013 1 RoHS 2011/65/EU EN IEC 63000:2018 optional / optionally / en option ATEX 2014/34/EU EN IEC 60079-0:2018 EN 60079-31:2014 1 Der Hersteller erklärt, dass die Geräte mit dem aktuellsten Normenstand übereinstimmen. Die Änderungen des aktuellsten Normenstandes wurden geprüft und betreffen das Gerät nicht. The manufacturer declares that this product complies with the requirements of the latest editions of the standards. The changes of the latest editions have been checked and do not affect this product. Le fabricant déclare que les appareils sont conformes aux dernières normes. Les changements de la les dernières normes ont été vérifiées et n’affectent pas le périphérique. Zusätzliche Angaben für Geräte mit ATEX-Zulassung: Additional information for equipment with ATEX Approval: Pour produits avec certificat ATEX: Geräte, die nach der Richtlinie gebaut sind, tragen die entsprechende Kennzeichnung auf dem Typenschild. -

Is ...^Ig^Igi; *Cwi£»-.Ar ,Aicfl Uacuihuffi Ob L'^Ue
AAA H*U 694 IS ... .^IG^IGI; *CWI£»-.AR ,AICFL UACUIHUFFI OB L'^UE 6, 1919. On k&roh 6, l&lfc, thore was a roar-end oafLi^en-between two freight trains on the Pennsylvania hailroad at Heaton, Pa*t which resulted in the death of 4 employeec and the injury of 2 omployaen, one of wr>oro afterwarde died* nXter investigation of this accident, the Chief of the Bureau ol Safety submits the following report* 2h& tart oi the Ihlladelphia Division upon ^hioh this accident occurred Is known as the !Drenfcoa Qut-Off, extending from Glen Looh to .eot Korrisville, and le used exclusively for freight movements. It is a d out le-t reel- line, and train movements ere handled under time tab!e rulea and train orders, protected by a manual block signal system under vthich permissive movements are allowed• Approaching the point of accident from tie west, the track ia straight y.lt. a slight descending grade for about 1*1/2 miles* Uhe weather was clear. iiaatbound extra 3275 consisted of 65 care and a cabooset hauled by engines 3276 and SS02, on route to .est tforrievillt* and was in charge of Conductor Jury and ^ngineraen Hogenioyler and Cork. It raseed SB Bloc1 station, which le about 17 miles from c laorrisvllle, at 5.11 a»n*, stopping for water with the rear end about 3,000 feet beyone Lhe tower. It yes while standing at this point that it van struct" by eaatbound extra 1666 at £.28 a.m. J.aetbound extra 1566 consisted of 78 cars and a caboose, hauled by engine 1566, and w in charge of Conductor Killer and •2- tingineman (iaecfcler. -

Helping You to Focus Better
#1 BOOK ONE word search Helping you to focus better Crystalens® vision workbook “your road to visual rejuvenation” DUNKIN DONUTS F J N H I A F L R W X D D T Z K T P E K Y W X C S T V B Q L O D V H O O R F Y X S O T E O M G M Q R D I Q K L T H I Z B J Y T T Y H G M V C Y Y T F L E L L E H J J P L I Y C H U J Y W N C E R K F O A R I T C R O I S S A N T W F R P C N F Z I X Y N Y E Y J X L N Y F R P A I L N E O L S W Z T E F K D U O C X D C J B Y L K G N Q E T T A L V C R W D C K D Q N N S A G R U B W F N U W R H U X O M D D U Q C L K W P B R P B W B P T U M J D R T F W S L T E I M A Y Y P X G E J X C V V S C L K I L P D V M A V H S Y V Q Y W N N A T W O N I J D C U N R Y Z F I J Q O A K D K N E A D T M U A J F P V D R O U E L E G A B E V Y T E J K V G P S H D E B M M H T C R Q T G K U W V F Z W R U K P T R O I J U B Y U H J E L E E X W Q V Q F B N M G J A W M U F F I N Z E G X K A S N B P A S V P Q X A L K O D U D A Q Bagel Drive Thru Beans Hazelnut Cappuccino Iced Coffee Latte Croissant Muffin Doughnut Vanilla #1 CANDY BARS W G I X B R B U Q I U C V Q S V K O O I H Y V S W Q Q U O R C N D C T Y Z K F B O O WH M M Y A W C E J T V Y I R R P S W O U U R K A L N O O E R N X J B X M G G J O O G C U Q W C Z Q T D H V M O W O W R E Q O C M V F U I L Y E D O R A O W R D M E O S L G Q M C S A I K E K E E K A J U L D E S E E R M B W Z S S O N Y K R L J Q B Y T A S H U H Y Q S M U V A U A I M P A A U R B T M N K E H E B M C O B R E O R T M S T V T I L H E R S H E Y Y V K L N N B E K I K H I U T M J T T V K B B A B D R W K C A K M E F K A T Q B S A -

Utility and Usage of Descender Devices in the Red Snapper Recreational Fishery in the South Atlantic
Utility and Usage of Descender Devices in the Red Snapper Recreational Fishery in the South Atlantic Julie Vecchio, Dominique Lazarre, Beverly Sauls SEDAR 73-WP15 Received: 11/16/2020 Revised: 12/4/2020 This information is distributed solely for the purpose of pre-dissemination peer review. It does not represent and should not be construed to represent any agency determination or policy. Please cite this document as: Vecchio, Julie, Dominique Lazarre, Beverly Sauls. 2020. Utility and Usage of Descender Devices in the Red Snapper Recreational Fishery in the South Atlantic. SEDAR73-WP15. SEDAR, North Charleston, SC. 16 pp. Utility and Usage of Descender Devices in the Red Snapper Recreational Fishery in the South Atlantic Prepared by: Julie Vecchio, Dominique Lazarre, Beverly Sauls Florida Fish and Wildlife Conservation Commission Fish and Wildlife Research Institute Saint Petersburg, Florida For: SEDAR 73 South Atlantic Red Snapper Data Workshop, 2020 The proportion of regulatory discards in American Red Snapper (Lutjanus campechanus: hereafter Red Snapper) fisheries has increased tremendously over the past several decades, sparking concern over the fate of discarded fish within both commercial and recreational fisheries. Several recent studies have assessed Red Snapper barotrauma and release condition with specific topics including immediate release mortality (Rummer 2007, Pulver 2017), the relationship between capture depth and discard mortality (Campbell et al. 2010b, Campbell et al. 2014), and the impact of barotrauma mitigation measures such as venting or recompression devices (Drumhiller et al. 2014, Sauls et al. 2016, Tomkins 2017, Ayala 2020, Bohaboy et al. 2020). The probability of anglers employing best release practices can also influence the overall survival within the fishery. -

Unicode Alphabets for L ATEX
Unicode Alphabets for LATEX Specimen Mikkel Eide Eriksen March 11, 2020 2 Contents MUFI 5 SIL 21 TITUS 29 UNZ 117 3 4 CONTENTS MUFI Using the font PalemonasMUFI(0) from http://mufi.info/. Code MUFI Point Glyph Entity Name Unicode Name E262 � OEligogon LATIN CAPITAL LIGATURE OE WITH OGONEK E268 � Pdblac LATIN CAPITAL LETTER P WITH DOUBLE ACUTE E34E � Vvertline LATIN CAPITAL LETTER V WITH VERTICAL LINE ABOVE E662 � oeligogon LATIN SMALL LIGATURE OE WITH OGONEK E668 � pdblac LATIN SMALL LETTER P WITH DOUBLE ACUTE E74F � vvertline LATIN SMALL LETTER V WITH VERTICAL LINE ABOVE E8A1 � idblstrok LATIN SMALL LETTER I WITH TWO STROKES E8A2 � jdblstrok LATIN SMALL LETTER J WITH TWO STROKES E8A3 � autem LATIN ABBREVIATION SIGN AUTEM E8BB � vslashura LATIN SMALL LETTER V WITH SHORT SLASH ABOVE RIGHT E8BC � vslashuradbl LATIN SMALL LETTER V WITH TWO SHORT SLASHES ABOVE RIGHT E8C1 � thornrarmlig LATIN SMALL LETTER THORN LIGATED WITH ARM OF LATIN SMALL LETTER R E8C2 � Hrarmlig LATIN CAPITAL LETTER H LIGATED WITH ARM OF LATIN SMALL LETTER R E8C3 � hrarmlig LATIN SMALL LETTER H LIGATED WITH ARM OF LATIN SMALL LETTER R E8C5 � krarmlig LATIN SMALL LETTER K LIGATED WITH ARM OF LATIN SMALL LETTER R E8C6 UU UUlig LATIN CAPITAL LIGATURE UU E8C7 uu uulig LATIN SMALL LIGATURE UU E8C8 UE UElig LATIN CAPITAL LIGATURE UE E8C9 ue uelig LATIN SMALL LIGATURE UE E8CE � xslashlradbl LATIN SMALL LETTER X WITH TWO SHORT SLASHES BELOW RIGHT E8D1 æ̊ aeligring LATIN SMALL LETTER AE WITH RING ABOVE E8D3 ǽ̨ aeligogonacute LATIN SMALL LETTER AE WITH OGONEK AND ACUTE 5 6 CONTENTS -

Edgerouter Lite Quick Start Guide
3-Port Router Model: ERLite-3 Introduction Thank you for purchasing the Ubiquiti Networks® EdgeRouter™ Lite. This Quick Start Guide is designed to guide you through installation and also includes warranty terms. Package Contents eth0 eth1 eth2 EdgeRouter Lite Screws Screw Anchors (Qty. 2) (Qty. 2) Power Adapter Power Cord (12V, 1A) TERMS OF USE: All Ethernet cabling runs must use CAT5 (or above). It is the professional installer’s responsibility to follow local country regulations, including operation within legal frequency channels, output power, indoor cabling requirements, and Dynamic Frequency Selection (DFS) requirements. Hardware Overview Front Panel Ports Console Ethernet (eth0-eth2) Reset eth0 eth1 eth2 Interface Description RJ45 serial console port for Command Line Interface (CLI) management. Use a RJ45‑to‑DB9, serial console cable, also known as a rollover cable, to connect the Console port to your computer. (If your computer does not have a DB9 port, then you will also need a DB9 adapter.) Then Console configure the following settings as needed: • Baud rate 115200 • Data bits 8 • Parity NONE • Stop bits 1 • Flow control NONE Ethernet 10/100/1000 Mbps Ethernet ports. (eth0‑eth2) Interface Description There are two methods to reset the EdgeRouter Lite to factory defaults: • Runtime reset (recommended) The EdgeRouter Lite should be running after bootup is complete. Press and hold the Reset button for about 10 seconds until the right LED on port eth2 starts flashing and then becomes solidly lit. After a few seconds, the LED will turn off, and Reset the EdgeRouter Lite will automatically reboot. • Power-on reset Disconnect the Power Cord from the Power Adapter. -

EU Declaration of Conformity
EU declaration of conformity Manufacturer: Petzl Distribution Zone Industrielle de Crolles 38920 Crolles FRANCE Declares, under its sole responsibility, that the following product: GRILLON Reference: L052XYXX - Rope: Polyester / Nylon - Highly abrasion-resistant rope Meets the following European regulations: Regulation (EU) 2016/425 on personal protective equipment The notified body DOLOMITICERT SCARL Zona Industriale Villanova, 7/A 32013 LONGARONE (BL) ITALY performed the EU type examination (module B) and issued the EU type-examination certificate Applicable standards: GRILLON EN 358 : 1999 EN 795 : 2012 N° 18-0014 + EN 12841 : 2006 Rope: Polyester / Nylon GRILLON EN 358 : 1999 EN 795 : 2012 N° 18-0016 + EN 12841 : 2006 Highly abrasion-resistant rope The notified body APAVE Sudeurope 17,bd Paul Langevin 38600 FONTAINE FRANCE performed the EU type examination (module B) and issued the EU type-examination certificate Lanyard end connector Applicable standards: HOOK EN362 : 2004 0082/047/160/07/18/0515 HOOK U EN362 : 2004 0082/047/160/10/17/0584 MGO 60S EN362 : 2004 0082/047/160/02/16/0082 MGO 60 EN362 : 2004 0082/047/160/07/18/0496 EASHOOK OPEN EN362 : 2004 0082/047/160/06/18/0440 MGO OPEN EN362 : 2004 0082/047/160/02/16/0081 Rope adjuster connector OK TL/TLN EN362 : 2004 0082/047/160/07/18/0514 OXAN TL EN362 : 2004 0082/047/160/11/16/0384 OXAN TLN EN362 : 2004 0082/047/160/11/16/0385 The product is subject to the type conformity assessment procedure on the basis of the quality assurance of the production process (module D) under the supervision of the notified body APAVE Sudeurope (0082). -

Writing As Language Technology
HG2052 Language, Technology and the Internet Writing as Language Technology Francis Bond Division of Linguistics and Multilingual Studies http://www3.ntu.edu.sg/home/fcbond/ [email protected] Lecture 2 HG2052 (2021); CC BY 4.0 Overview ã The origins of writing ã Different writing systems ã Representing writing on computers ã Writing versus talking Writing as Language Technology 1 The Origins of Writing ã Writing was invented independently in at least three places: Mesopotamia China Mesoamerica Possibly also Egypt (Earliest Egyptian Glyphs) and the Indus valley. ã The written records are incomplete ã Gradual development from pictures/tallies Writing as Language Technology 2 Follow the money ã Before 2700, writing is only accounting. Temple and palace accounts Gold, Wheat, Sheep ã How it developed One token per thing (in a clay envelope) One token per thing in the envelope and marked on the outside One mark per thing One mark and a symbol for the number Finally symbols for names Denise Schmandt-Besserat (1997) How writing came about. University of Texas Press Writing as Language Technology 3 Clay Tokens and Envelope Clay Tablet Writing as Language Technology 4 Writing systems used for human languages ã What is writing? A system of more or less permanent marks used to represent an utterance in such a way that it can be recovered more or less exactly without the intervention of the utterer. Peter T. Daniels, The World’s Writing Systems ã Different types of writing systems are used: Alphabetic Syllabic Logographic Writing