Interim Guidelines for Owners, Operators and Masters for Protection Against Piracy in the Gulf of Guinea Region
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
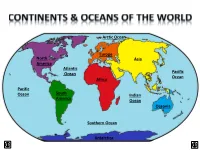
North America Other Continents
Arctic Ocean Europe North Asia America Atlantic Ocean Pacific Ocean Africa Pacific Ocean South Indian America Ocean Oceania Southern Ocean Antarctica LAND & WATER • The surface of the Earth is covered by approximately 71% water and 29% land. • It contains 7 continents and 5 oceans. Land Water EARTH’S HEMISPHERES • The planet Earth can be divided into four different sections or hemispheres. The Equator is an imaginary horizontal line (latitude) that divides the earth into the Northern and Southern hemispheres, while the Prime Meridian is the imaginary vertical line (longitude) that divides the earth into the Eastern and Western hemispheres. • North America, Earth’s 3rd largest continent, includes 23 countries. It contains Bermuda, Canada, Mexico, the United States of America, all Caribbean and Central America countries, as well as Greenland, which is the world’s largest island. North West East LOCATION South • The continent of North America is located in both the Northern and Western hemispheres. It is surrounded by the Arctic Ocean in the north, by the Atlantic Ocean in the east, and by the Pacific Ocean in the west. • It measures 24,256,000 sq. km and takes up a little more than 16% of the land on Earth. North America 16% Other Continents 84% • North America has an approximate population of almost 529 million people, which is about 8% of the World’s total population. 92% 8% North America Other Continents • The Atlantic Ocean is the second largest of Earth’s Oceans. It covers about 15% of the Earth’s total surface area and approximately 21% of its water surface area. -
From Operation Serval to Barkhane
same year, Hollande sent French troops to From Operation Serval the Central African Republic (CAR) to curb ethno-religious warfare. During a visit to to Barkhane three African nations in the summer of 2014, the French president announced Understanding France’s Operation Barkhane, a reorganization of Increased Involvement in troops in the region into a counter-terrorism Africa in the Context of force of 3,000 soldiers. In light of this, what is one to make Françafrique and Post- of Hollande’s promise to break with colonialism tradition concerning France’s African policy? To what extent has he actively Carmen Cuesta Roca pursued the fulfillment of this promise, and does continued French involvement in Africa constitute success or failure in this rançois Hollande did not enter office regard? France has a complex relationship amid expectations that he would with Africa, and these ties cannot be easily become a foreign policy president. F cut. This paper does not seek to provide a His 2012 presidential campaign carefully critique of President Hollande’s policy focused on domestic issues. Much like toward France’s former African colonies. Nicolas Sarkozy and many of his Rather, it uses the current president’s predecessors, Hollande had declared, “I will decisions and behavior to explain why break away from Françafrique by proposing a France will not be able to distance itself relationship based on equality, trust, and 1 from its former colonies anytime soon. solidarity.” After his election on May 6, It is first necessary to outline a brief 2012, Hollande took steps to fulfill this history of France’s involvement in Africa, promise. -

The North Caucasus: the Challenges of Integration (III), Governance, Elections, Rule of Law
The North Caucasus: The Challenges of Integration (III), Governance, Elections, Rule of Law Europe Report N°226 | 6 September 2013 International Crisis Group Headquarters Avenue Louise 149 1050 Brussels, Belgium Tel: +32 2 502 90 38 Fax: +32 2 502 50 38 [email protected] Table of Contents Executive Summary ................................................................................................................... i Recommendations..................................................................................................................... iii I. Introduction ..................................................................................................................... 1 II. Russia between Decentralisation and the “Vertical of Power” ....................................... 3 A. Federative Relations Today ....................................................................................... 4 B. Local Government ...................................................................................................... 6 C. Funding and budgets ................................................................................................. 6 III. Elections ........................................................................................................................... 9 A. State Duma Elections 2011 ........................................................................................ 9 B. Presidential Elections 2012 ...................................................................................... -

Country by Country Reporting
COUNTRY BY COUNTRY REPORTING PUBLICATION REPORT 2018 (REVISED) Anglo American is a leading global mining company We take a responsible approach to the management of taxes, As we strive to deliver attractive and sustainable returns to our with a world class portfolio of mining and processing supporting active and constructive engagement with our stakeholders shareholders, we are acutely aware of the potential value creation we operations and undeveloped resources. We provide to deliver long-term sustainable value. Our approach to tax is based can offer to our diverse range of stakeholders. Through our business on three key pillars: responsibility, compliance and transparency. activities – employing people, paying taxes to, and collecting taxes the metals and minerals to meet the growing consumer We are proud of our open and transparent approach to tax reporting. on behalf of, governments, and procuring from host communities – driven demands of the world’s developed and maturing In addition to our mandatory disclosure obligations, we are committed we make a significant and positive contribution to the jurisdictions in economies. And we do so in a way that not only to furthering our involvement in voluntary compliance initiatives, such which we operate. Beyond our direct mining activities, we create and generates sustainable returns for our shareholders, as the Tax Transparency Code (developed by the Board of Taxation in sustain jobs, build infrastructure, support education and help improve but also strives to make a real and lasting positive Australia), the Responsible Tax Principles (developed by the B Team), healthcare for employees and local communities. By re-imagining contribution to society. -

Chirac and ‘La Franc¸Afrique’: No Longer a Family Affair Tony Chafer
Modern & Contemporary France Vol. 13, No. 1, February 2005, pp. 7–23 Chirac and ‘la Franc¸afrique’: No Longer a Family Affair Tony Chafer Since political independence, France has maintained a privileged sphere of influence—the so-called ‘pre´ carre´’—in sub-Saharan Africa, based on a series of family-like ties with its former colonies. The cold war provided a favourable environment for the development of this special relationship, as the USA saw the French presence in this part of the world as useful for the containment of Communism. However, following the end of the cold war, France has had to adapt to a new international policy environment that is more competitive and less conducive to the maintenance of such family-like ties. This article charts the evolution of Franco-African relations in an era of globalisation, as French governments have undertaken a hesitant process of policy adaptation since the mid-1990s. Unlike decolonisation in Indochina and Algeria, the transfer of power in Black Africa was largely peaceful; as a result, there was no rupture of relations with the former colonial power. On the contrary, the years after independence were marked by an intensification of the links with France. Official rhetoric often referred to the great Franco-African family and the term ‘la Franc¸afrique’ testified to a symbiotic relationship in which ‘Africa is experienced in French representations as a natural extension where the Francophone world and Francophilia merge’ (Bourmaud, 2000). In fact, a wide variety of terms have been coined to describe -

THE LIMITS of SELF-DETERMINATION in OCEANIA Author(S): Terence Wesley-Smith Source: Social and Economic Studies, Vol
THE LIMITS OF SELF-DETERMINATION IN OCEANIA Author(s): Terence Wesley-Smith Source: Social and Economic Studies, Vol. 56, No. 1/2, The Caribbean and Pacific in a New World Order (March/June 2007), pp. 182-208 Published by: Sir Arthur Lewis Institute of Social and Economic Studies, University of the West Indies Stable URL: http://www.jstor.org/stable/27866500 . Accessed: 11/10/2013 20:07 Your use of the JSTOR archive indicates your acceptance of the Terms & Conditions of Use, available at . http://www.jstor.org/page/info/about/policies/terms.jsp . JSTOR is a not-for-profit service that helps scholars, researchers, and students discover, use, and build upon a wide range of content in a trusted digital archive. We use information technology and tools to increase productivity and facilitate new forms of scholarship. For more information about JSTOR, please contact [email protected]. University of the West Indies and Sir Arthur Lewis Institute of Social and Economic Studies are collaborating with JSTOR to digitize, preserve and extend access to Social and Economic Studies. http://www.jstor.org This content downloaded from 133.30.14.128 on Fri, 11 Oct 2013 20:07:57 PM All use subject to JSTOR Terms and Conditions Social and Economic Studies 56:1&2 (2007): 182-208 ISSN:0037-7651 THE LIMITS OF SELF-DETERMINATION IN OCEANIA Terence Wesley-Smith* ABSTRACT This article surveys processes of decolonization and political development inOceania in recent decades and examines why the optimism of the early a years of self government has given way to persistent discourse of crisis, state failure and collapse in some parts of the region. -

Traditional Cartography in Papua New Guinea
12 · Traditional Cartography in Papua New Guinea ERIC KLINE SILVERMAN SOCIAL LIFE, COSMOLOGY, AND rather of social conventions such as gift exchanges that POLITICS IN MELANESIA enable people to continually forge and negotiate rela tionships and alliances. Gift exchange, first studied by The cultural diversity of Melanesia in the southwestern Marcel Mauss, is the basis for the constitution of tradi Pacific Ocean is astounding. Regional generalizations are tional or prestate societies in particular. 1 Guided by the bound to falter: some sociocultural exception to any principle of reciprocity, gift exchange refers to the moral posited rule will almost assuredly exist. Nevertheless, it is obligation to give, to receive, and to give back various ob possible at least to sketch some common, nearly pan jects such as food, tobacco, and valuables as well as labor Melanesian social and cultural parameters. Since all in and services. As a result, people are enmeshed in a web of digenous representations of space in Melanesia are the obligations whereby they are constantly giving and re product or the reflection of social life, this brief discus ceiving, thus holding the society together. All societies in sion will provide a necessary context for understanding Melanesia are at some level a group of people who speak the social generation of local modes of cartography. a common language, share the same culture, and form a The peoples of the first migration from Southeast Asia moral community united by gift exchange. spread into New Guinea, the larger islands off New However, there are other foundations of societies in Guinea, and Australia, which at that time were connected Melanesia, and although these vary greatly, they can be by a land bridge (fig. -

Female Genital Mutilation in Africa: an Analysis of Current Abandonment Approaches
Female genital mutilation in Africa An analysis of current abandonment approaches December 2005 A.C.S. Plaza, 4th Floor, Lenana Road P.O. Box 76634, Nairobi, 00508 Tel: 254.20.3877177 Fax: 254.20.3877172 email: [email protected] www.path.org Suggested citation: Muteshi J, Sass J. Female Genital Mutilation in Africa: An Analysis of Current Abandonment Approaches. Nairobi: PATH; 2005. Copyright © 2006, Program for Appropriate Technology in Health (PATH). All rights reserved. The material in this document may be freely used for education or noncommercial purposes, provided the material is accompanied by an acknowledgement line. Table of contents Acronyms ............................................................................................................................ 3 Executive summary ............................................................................................................ 4 1 Introduction ................................................................................................................ 6 2 FGM prevalence.......................................................................................................... 7 FGM prevalence by residence ..................................................................................... 8 FGM prevalence by ethnicity ...................................................................................... 9 FGM prevalence by education..................................................................................... 9 FGM prevalence by religion.......................................................................................10 -

WEST AFRICA LIBYA 25° ALGERIA 25° WEST Western AFRICA Sahara Tamanrasset Fdérik
20° 15° 10° 5° 0° 5° 10° 15° WEST AFRICA LIBYA 25° ALGERIA 25° WEST Western AFRICA Sahara Tamanrasset Fdérik Nouâdhibou Atâr 20° Akjoujt MAURITANIA 20° Tidjikja Kidal Nouakchott MALI A NIGER T Aleg Tombouctou Agadez Rosso Sene Kiffa 'Ayoûn el 'Atroûs gal L Gao Kaédi Saint-Louis A Louga Matam Sélibabi Tahoua 15° N Dakar Lake 15° Kayes Chad Kaolack SENEGAL Tillabéri T Mopti mbia Tambacounda Zinder CHAD Ga er Niamey Maradi I ig Diffa GAMBIA N Ségou BURKINA Dosso Sokoto C Banjul Kolda Koulikoro FASO Dédougou Katsina Ziguinchor Bamako Ouagadougou Kano Bissau Birnin Kebbi Gusau Maiduguri Koudougou Fada Dutse GUINEA-BISSAU Bobo- N'Gourma Niger Labé Sikasso Dioulasso Boké Léo Kandi O Mamou Kankan Banfora Kaduna Maroua GUINEA Bolgatanga Bauchi C Kindia BENIN Gombe Wa Jos 10° Faranah Odienné Kara Djougou NIGERIA 10° E Conakry Tamale e Kissidougou Lake Abuja nu Yola A Forécariah SIERRA Korhogo e Makeni Volta B Garoua Guéckédou Ilorin Lafia N Freetown Macenta Touba CÔTE Jalingo LEONE Bo Voinjama Nzérékoré D'IVOIRE Lac de GHANA Ado-Ekiti Makurdi Kenema ManKossou Bouaké TOGO Ibadan Ngaoundéré 25° 24° Sunyani Abomey Yamoussoukro Abeokuta CABO VERDE Dimbokro Santo Antão Robertsport LIBERIA Kumasi Cotonou Ikeja Daloa Lagos Benin City Enugu 17° 17° Monrovia Kakata Ho Santa Luzia Zwedru Guiglo Divo Koforidua Porto- Bamenda São Sal Gagnoa Buchanan Lomé Novo Owerri Bafoussam Vicente Fish Town Accra São Nicolau Cestos City Bight of Benin Calabar 5° Port 5° Greenville Abidjan Cape Harcourt CAMEROON Boa Vista Sekondi- Coast 16° 16° Barclayville San-Pédro Buea ATLANTIC Harper Takoradi Douala Yaoundé OCEAN Malabo São 0 100 200 300 400 500 km 0 50 km The boundaries and names shown and the designations used Tiago EQUATORIAL GUINEA Ébolowa 0 25 mi Maio on this map do not imply official endorsement or acceptance Fogo by the United Nations. -

Traditional Male Circumcision Among Young People
November 2009 TRADITIONAL MALE CIRCUMCISION AMONG YOUNG PEOPLE A public health perspective in the context of HIV prevention WHO Library Cataloguing-in-Publication Data Traditional male circumcision among young people : a public health perspective in the context of HIV prevention. 1.Circumcision, Male -utilization. 2.Circumcision, Male - psychology. 3.HIV infection - prevention and control. 4.Ceremonial behaviour. 5.Cross-cultural comparison. 6.Decision-making. 7.Medicine, Traditional. 8.Delivery of health care. 9.Adolescent. I.World Health Organization. ISBN 978 92 4 159891 0 (NLM classification: WC 503.6) © World Health Organization 2009 All rights reserved. Publications of the World Health Organization can be obtained from WHO Press, World Health Organization, 20 Avenue Appia, 1211 Geneva 27, Switzerland (tel: +41 22 791 2476; fax: +41 22 791 4857; e-mail: [email protected]). Requests for permission to reproduce or translate WHO publications - whether for sale or for noncommercial distribution - should be addressed to WHO Press, at the above address (fax: +41 22 791 4806; e-mail: [email protected]). The designations employed and the presentation of the material in this publication do not imply the expression of any opinion whatsoever on the part of the World Health Organization concerning the legal status of any country, territory, city or area or of its authorities, or concerning the delimitation of its frontiers or boundaries. Dotted lines on maps represent approximate border lines for which there may not yet be full agreement. The mention of specific companies or of certain manufacturers’ products does not imply that they are endorsed or recommended by the World Health Organization in preference to others of a similar nature that are not mentioned. -

Piracy in the Gulf of Guinea: EU and International Action
BRIEFING Piracy in the Gulf of Guinea EU and international action SUMMARY The Gulf of Guinea is framed by 6 000 km of west African coastline, from Senegal to Angola. Its sea basin is an important resource for fisheries and is part of a key sea route for the transport of goods between central and southern Africa and the rest of the world. Its geo-political and geo-economic importance has grown since it has become a strategic hub in global and regional energy trade. Every day, nearly 1 500 fishing vessels, cargo ships and tankers navigate its waters. The security of this maritime area is threatened by the rise of piracy, illegal fishing, and other maritime crimes. Regional actors have committed to cooperate on tackling the issue through the 'Yaoundé Code of Conduct' and the related cooperation mechanism and bodies. The international community has also pledged to track and condemn acts of piracy at sea. The European Union (EU), which has a strong interest in safeguarding its maritime trade and in addressing piracy's root causes, supports regional and international initiatives. The EU is also implementing its own maritime security strategy, which includes, among other features, a regional component for the Gulf of Guinea; this entails EU bodies' and Member States' cooperation in countering acts of piracy, as well as capacity-building projects. This briefing draws from and updates the sections on the Gulf of Guinea in 'Piracy and armed robbery off the coast of Africa', EPRS, March 2019. In this Briefing Background Regional cooperation International action EU strategies Map of the Gulf of Guinea and ECOWAS and ECCAS member states. -

French Relations with Sub-Saharan Africa Under President Sarkozy
OCCASIONAL PAPER NO 1 0 7 South African Foreign Policy and African Drivers Programme January 2012 French Relations with Sub-Saharan Africa Under President Sarkozy R i c h a r d M o n c r i e f f s ir a f f A l a n o ti a rn e nt f I o te tu sti n In rica . th Af hts Sou sig al in Glob African perspectives. About SAIIA The South African Institute of International Affairs (SAIIA) has a long and proud record as South Africa’s premier research institute on international issues. It is an independent, non-government think-tank whose key strategic objectives are to make effective input into public policy, and to encourage wider and more informed debate on international affairs with particular emphasis on African issues and concerns. It is both a centre for research excellence and a home for stimulating public engagement. SAIIA’s occasional papers present topical, incisive analyses, offering a variety of perspectives on key policy issues in Africa and beyond. Core public policy research themes covered by SAIIA include good governance and democracy; economic policymaking; international security and peace; and new global challenges such as food security, global governance reform and the environment. Please consult our website www.saiia.org.za for further information about SAIIA’s work. A b o u t t h e S o u t h A f r I c A n f o r e I g n p o l I c y A n d A f r I c A n d r I v e r S p r o g r A m m e Since the fall of Apartheid in 1994, South Africa’s foreign policy has prioritised the development of Africa.