Practical Verifiable In-Network Filtering for Ddos Defense
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Tate Report 08-09
Tate Report 08–09 Report Tate Tate Report 08–09 It is the Itexceptional is the exceptional generosity generosity and and If you wouldIf you like would to find like toout find more out about more about PublishedPublished 2009 by 2009 by vision ofvision individuals, of individuals, corporations, corporations, how youhow can youbecome can becomeinvolved involved and help and help order of orderthe Tate of the Trustees Tate Trustees by Tate by Tate numerousnumerous private foundationsprivate foundations support supportTate, please Tate, contact please contactus at: us at: Publishing,Publishing, a division a divisionof Tate Enterprisesof Tate Enterprises and public-sectorand public-sector bodies that bodies has that has Ltd, Millbank,Ltd, Millbank, London LondonSW1P 4RG SW1P 4RG helped Tatehelped to becomeTate to becomewhat it iswhat it is DevelopmentDevelopment Office Office www.tate.org.uk/publishingwww.tate.org.uk/publishing today andtoday enabled and enabled us to: us to: Tate Tate MillbankMillbank © Tate 2009© Tate 2009 Offer innovative,Offer innovative, landmark landmark exhibitions exhibitions London LondonSW1P 4RG SW1P 4RG ISBN 978ISBN 1 85437 978 1916 85437 0 916 0 and Collectionand Collection displays displays Tel 020 7887Tel 020 4900 7887 4900 A catalogue record for this book is Fax 020 Fax7887 020 8738 7887 8738 A catalogue record for this book is available from the British Library. DevelopDevelop imaginative imaginative education education and and available from the British Library. interpretationinterpretation programmes programmes AmericanAmerican Patrons Patronsof Tate of Tate Every effortEvery has effort been has made been to made locate to the locate the 520 West520 27 West Street 27 Unit Street 404 Unit 404 copyrightcopyright owners ownersof images of includedimages included in in StrengthenStrengthen and extend and theextend range the of range our of our New York,New NY York, 10001 NY 10001 this reportthis and report to meet and totheir meet requirements. -
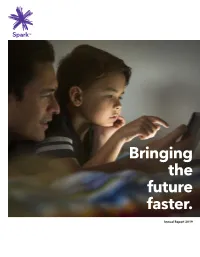
Bringing the Future Faster
6mm hinge Bringing the future faster. Annual Report 2019 WorldReginfo - 7329578e-d26a-4187-bd38-e4ce747199c1 Bringing the future faster Spark New Zealand Annual Report 2019 Bringing the future faster Contents Build customer intimacy We need to understand BRINGING THE FUTURE FASTER and anticipate the needs of New Zealanders, and Spark performance snapshot 4 technology enables us Chair and CEO review 6 to apply these insights Our purpose and strategy 10 to every interaction, Our performance 12 helping us serve our Our customers 14 customers better. Our products and technology 18 Read more pages 7 and 14. Our people 20 Our environmental impact 22 Our community involvement 24 Our Board 26 Our Leadership Squad 30 Our governance and risk management 32 Our suppliers 33 Leadership and Board remuneration 34 FINANCIAL STATEMENTS Financial statements 38 Notes to the financial statements 44 Independent auditor’s report 90 OTHER INFORMATION Corporate governance disclosures 95 Managing risk framework roles and 106 responsibilities Materiality assessment 107 Stakeholder engagement 108 Global Reporting Initiative (GRI) content 109 index Glossary 112 Contact details 113 This report is dated 21 August 2019 and is signed on behalf of the Board of Spark New Zealand Limited by Justine Smyth, Chair and Charles Sitch, Chair, Audit and Risk Management Committee. Justine Smyth Key Dates Annual Meeting 7 November 2019 Chair FY20 half-year results announcement 19 February 2020 FY20 year-end results announcement 26 August 2020 Charles Sitch Chair Audit and Risk Management Committee WorldReginfo - 7329578e-d26a-4187-bd38-e4ce747199c1 Create New Zealand’s premier sports streaming business Spark Sport is revolutionising how New Zealanders watch their favourite sports events. -

Thinktv FACT PACK NEW ZEALAND
ThinkTV FACT PACK JAN TO DEC 2017 NEW ZEALAND TV Has Changed NEW ZEALAND Today’s TV is a sensory experience enjoyed by over 3 million viewers every week. Powered by new technologies to make TV available to New Zealanders anywhere, any time on any screen. To help advertisers and agencies understand how TV evolved over the last year, ThinkTV has created a Fact Pack with all the stats for New Zealand TV. ThinkTV’s Fact Pack summarises the New Zealand TV marketplace, in-home TV viewing, timeshifted viewing and online video consumption. And, because we know today’s TV is powered by amazing content, we’ve included information on some top shows, top advertisers and top adverts to provide you with an insight into what was watched by New Zealanders in 2017. 2017 THE NEW ZEALAND TV MARKETPLACE BIG, SMALL, MOBILE, SMART, CONNECTED, 1. HD-capable TV sets are now in CURVED, VIRTUAL, 3D, virtually every home in New Zealand DELAYED, HD, 4K, 2. Each home now has on average ON-DEMAND, CAST, 7.6 screens capable of viewing video STREAM… 3. Almost 1 in every 3 homes has a internet-connected smart TV THE TV IS AS CENTRAL TO OUR ENTERTAINMENT AS IT’S EVER BEEN. BUT FIRST, A QUICK PEAK INSIDE NEW ZEALAND’S LIVING ROOMS • In 2015 New Zealand TV celebrated 55 years of broadcast with the first transmission on 1 June, 1960 • Today’s TV experience includes Four HD Free-to-air channels Two Commercial Free-to-Air broadcasters One Subscription TV provider • Today’s TV is DIGITAL in fact, Digital TV debuted in 2006 followed by multi-channels in 2007 • In its 58th year, New Zealand TV continues to change and evolve. -

Bryan Donnell • Director of Photography [email protected] • Website Bryandonnell.Com • 213.321.3909 M
Bryan Donnell • Director of Photography [email protected] • website bryandonnell.com • 213.321.3909 m DOCUMENTARY TELEVISION E.P./PRODUCER/DIRECTOR NETWORK/CO. Untitled doc feature Chai Vasarhelyi/Jimmy Chin HBO/Little Monsters Untitled doc feature Erin Lee Carr Netflix/Story Syndicate This Is Life w/ Lisa Ling (multiple eps) Lisa Ling/multiple CNN/Part2 We’re Here Peter Logreco HBO/IPC • nominee best doc series Emmy, IDA, Independent Spirit Untitled doc series Nikki Calabrese HBO/WoW Rick James biopic Steve Rivo/Sacha Jenkins Showtime/Mass Appeal The Con Star Price ABC/IPC Empires of New York (add’l) Matthew Galkin CNBC/IPC The Witnesses Matt Testa Oxygen/Herzog Broken Steve Rivo Netflix/ZeroPointZero The Redemption Project w/ Van Jones Jason Cohen CNN/Citizen Jones Murder Mountain Jon Chinn/Matt Testa/Joshua Zeman Netflix/Lightbox QB1 Peter Berg/Rachel Libert Netflix/Film45 Kids Behind Bars Peter Logreco A&E/IPC Afflicted Peter Logreco Netflix/Doc Shop Criminal Confessions Dick Wolf/Adam Kassen Oxygen/Shed Media Religion of Sports Tom Brady/Sam French Dish/Dirty Robber Invisible Killers Steve Rivo/BJ Perlmutt Discovery/Doc Group Hot Girls Wanted: Turned On Peter Logreco Netflix/Herzog Truth and Power Brian Knappenberger Pivot/Luminant Media DB Cooper: Case Closed? Ted Skillman History Channel truInside: Iconic Comedies Lisa Kalikow, Meri Haitkin, et al. truTV/left/right Morgan Spurlock: Inside Man Morgan Spurlock/Matt Galkin CNN/Warrior Poets • IDA AWARD, best doc series Living in Secret Sarah Skibitzke LMN/Brownstone Years of Living Dangerously (add’l) James Cameron/Joel Bach Showtime/Years Project • EMMY AWARD, best doc series Summer Dreams Jonathan Chinn/Ted Skillman CBS/Mandalay Sport in America (add’l) Adam del Deo/James Stern HBO/Endgame 30 for 30: The Dotted Line Morgan Spurlock/Matt Galkin ESPN/Warrior Poets Intervention Dan Partland A&E/GRB • EMMY AWARD, best reality series • EMMY NOM, best cinematography (for me) 30 Days: Animal Rights Morgan Spurlock/Jonathan Chinn FX/Actual Reality DOCUMENTARY FILMS PRODUCER/DIRECTOR DISTRIBUTOR/PROD. -

The Export of European Films on SVOD Outside Europe
The export of European films on SVOD services outside Europe Christian Grece September 2019 A publication of the European Audiovisual Observatory Table of Contents Overview of 79 SVOD services in 21 countries worldwide Analysis by region and country ▪ North America – Canada and USA ▪ Latin America – Argentina, Brazil and Mexico ▪ South East Asia – Indonesia, Malaysia, Philippines, Singapore and Thailand ▪ East Asia – China and Japan ▪ India ▪ Oceania –Australia and New Zealand ▪ Middle East – The United Arab Emirates, Egypt and Saudi Arabia ▪ Individual countries - Russian Federation, South Africa and Turkey Introduction The aim of this report is to give a picture on the export of EU films on SVOD services outside of the European Union. 79 SVOD services in 21 countries worldwide are part of the sample. The report looks at the circulation of unique film titles and the volume/occurrences of films available on these services, on a regional and service basis. The first part gives a snapshot of the availability of EU films around the globe after which a overview for each region is provided. Methodology The analysis has been carried out based on data provided by Ampere Analysis and comprehends SVOD catalogue data collected in June 2019. A film is defined as a feature film, fiction film, documentary or other film content available in the “Film” / “Movie” section of the SVOD catalogues part of the sample. For the origin of a film, only the first country of production is taken into account. The production countries are based on data collected from the Observatory’s LUMIERE database on admissions to films in Europe, IMDb and the Movie database. -

A Guide to Smartphone Astrophotography National Aeronautics and Space Administration
National Aeronautics and Space Administration A Guide to Smartphone Astrophotography National Aeronautics and Space Administration A Guide to Smartphone Astrophotography A Guide to Smartphone Astrophotography Dr. Sten Odenwald NASA Space Science Education Consortium Goddard Space Flight Center Greenbelt, Maryland Cover designs and editing by Abbey Interrante Cover illustrations Front: Aurora (Elizabeth Macdonald), moon (Spencer Collins), star trails (Donald Noor), Orion nebula (Christian Harris), solar eclipse (Christopher Jones), Milky Way (Shun-Chia Yang), satellite streaks (Stanislav Kaniansky),sunspot (Michael Seeboerger-Weichselbaum),sun dogs (Billy Heather). Back: Milky Way (Gabriel Clark) Two front cover designs are provided with this book. To conserve toner, begin document printing with the second cover. This product is supported by NASA under cooperative agreement number NNH15ZDA004C. [1] Table of Contents Introduction.................................................................................................................................................... 5 How to use this book ..................................................................................................................................... 9 1.0 Light Pollution ....................................................................................................................................... 12 2.0 Cameras ................................................................................................................................................ -

Study of Mobile Telecommunications Markets in NZ Submission
Study of mobile telecommunications markets in NZ Submission | Commerce Commission 26 October 2018 Public Version Contents Executive Summary .............................................................................................................. 1 Introduction ........................................................................................................................... 4 1. Current market outcomes .................................................................................................. 5 Assessing competition and market outcomes .................................................................... 5 Price, quality and innovation .............................................................................................. 6 Data the paper seeks further information on ...................................................................... 7 2. Looking forward .............................................................................................................. 13 5G network deployment ................................................................................................... 15 Emerging trends .............................................................................................................. 17 Promoting 5G deployment ............................................................................................... 23 3. Industry structure ............................................................................................................ 24 MVNOs ........................................................................................................................... -

Yearbook 2019/2020 Key Trends
YEARBOOK 2019/2020 KEY TRENDS TELEVISION, CINEMA, VIDEO AND ON-DEMAND AUDIOVISUAL SERVICES - THE PAN-EUROPEAN PICTURE → Director of publication Susanne Nikoltchev, Executive Director → Editorial supervision Gilles Fontaine, Head of Department for Market Information → Authors Francisco Javier Cabrera Blázquez, Maja Cappello, Laura Ene, Gilles Fontaine, Christian Grece, Marta Jiménez Pumares, Martin Kanzler, Ismail Rabie, Agnes Schneeberger, Patrizia Simone, Julio Talavera, Sophie Valais → Coordination Valérie Haessig → Special thanks to the following for their contribution to the Yearbook Ampere Analysis, Bureau van Dijk (BvD), European Broadcasting Union - Media Intelligence Service (EBU-M.I.S.), EURODATA-TV, LyngSat, WARC, and the members of the EFARN and the EPRA networks. → Proofreading Anthony Mills → Layout Big Family → Press and public relations Alison Hindhaugh, [email protected] → Publisher European Audiovisual Observatory 76 Allée de la Robertsau, 67000 Strasbourg, France www.obs.coe.int If you wish to reproduce tables or graphs contained in this publication please contact the European Audiovisual Observatory for prior approval. Please note that the European Audiovisual Observatory can only authorise reproduction of tables or graphs sourced as “European Audiovisual Observatory”. All other entries may only be reproduced with the consent of the original source. Opinions expressed in this publication are personal and do not necessarily represent the view of the Observatory, its members or of the Council of Europe. © European Audiovisual Observatory (Council of Europe), Strasbourg 2020 YEARBOOK 2019/2020 KEY TRENDS TELEVISION, CINEMA, VIDEO AND ON-DEMAND AUDIOVISUAL SERVICES - THE PAN-EUROPEAN PICTURE 4 YEARBOOK 2019/2020 – KEY TRENDS TABLE OF CONTENT INTRODUCTION 0 Six keywords for 2019 and, possibly, 2020 . -
Global SVOD Forecasts
Global SVOD Forecasts Table of Contents Published in October 2017, this 252-page PDF and excel report contains comprehensive coverage of the SVOD sector (TV episodes and movies) for 138 countries [up from 100 in the previous edition]. The report comprises: • Executive Summary. • Major SVOD players, including subscriber and revenues estimates by country (2010 to 2022) for the major platforms. • Country-by-country forecasts from 2010 to 2022 138 countries and 621 platforms covered: Asia Pacific Country SVOD SVOD Platforms ops Australia 4 Netflix; Amazon Prime Video; Stan; Foxtel Now Bangladesh 3 Netflix; Amazon Prime Video; Iflix Cambodia 3 Netflix; Amazon Prime Video; Iflix China 5 Youku Tudou; Iqiyi; Tencent Video; TMall Box Office; LeEco Hong Kong 4 Netflix; Amazon Prime Video; MyTV Super; Viu India 10 Netflix; Amazon Prime Video; Ditto; Hotstar; Sony Liv; Bigflix; Eros Now; HOOQ; Spuul; Viu Indonesia 7 Netflix; Amazon Prime Video; Iflix; HOOQ; Tribe; Catchplay; Viu Japan 7 Netflix; Amazon Prime Video; Hulu; Tsutaya; U-Next; Avex dtv; au Smart Pass Laos 2 Netflix; Amazon Prime Video Malaysia 7 Netflix; Amazon Prime Video; Iflix; Tonton VIP; Viu; HOOQ; Dimsum Mongolia 2 Netflix; Amazon Prime Video Myanmar 3 Netflix; Amazon Prime Video; Iflix Nepal 3 Netflix; Amazon Prime Video; Iflix New Zealand 4 Netflix; Amazon Prime Video; Lightbox; Neon Pakistan 4 Netflix; Amazon Prime Video; Iflix; Icflix Philippines 6 Netflix; Amazon Prime Video; Iflix; HOOQ; Tribe; Viu Singapore 6 Netflix; Amazon Prime Video; HOOQ; Tribe; Catchplay; Viu South Korea -

Subscription Video on Demand: Viewing Preferences Among New Zealand Audiences
Subscription Video on Demand: Viewing preferences among New Zealand audiences Rachel Hayley Daniels A thesis submitted to Auckland University of Technology in partial fulfilment of the requirements for the degree of Master of Communication Studies (MCS) 2017 School of Communication Studies Abstract With the development of digital television platforms in New Zealand and the launch of Subscription Video on Demand (SVOD) services such as Netflix NZ, Lightbox, Quickflix and Neon, a more discerning television audience is emerging. SVOD services are influencing a change within the television broadcasting landscape in New Zealand, fragmenting audiences away from traditional linear television, appealing to viewers in new and innovative ways and changing viewing behaviour. This thesis provides qualitative and quantitative analysis of SVOD viewers’ experiences, expectations, and behaviours with respect to viewing content on the digital platforms and services available to New Zealand subscribers. Quantitative data was collected from an online survey; participants were drawn from readers of the New Zealand Herald online. The quantitative data was collected in order to help position and supplement the qualitative data, which was obtained through focus group interviews. A thematic analysis was used to identify key themes and draw insight from the data sets. The thesis identifies that viewers place a high degree of preference and value on the freedom and opportunities that SVOD provides in personalizing their own viewing practices. Key preferences among these was the ability to control content selection and engage in the practice of anytime viewing, i.e. to choose from an increasingly broad selection of content wherever they are, whenever they like and on whatever device they prefer to view it on. -

Complete Nominations List
2021 Emmy® Awards 73rd Emmy Awards Complete Nominations List Outstanding Animated Program Big Mouth • The New Me • Netflix • Netflix Nick Kroll, Executive Producer Andrew Goldberg, Executive Producer/Teleplay by/Story by Mark Levin, Executive Producer Jennifer Flackett, Executive Producer Joe Wengert, Co-Executive Producer Kelly Galuska, Co-Executive Producer Gil Ozeri, Co-Executive Producer Emily Altman, Supervising Producer Ben Kalina, Supervising Producer Chris Prynoski, Supervising Producer Shannon Prynoski, Supervising Producer Anthony Lioi, Supervising Producer Victor Quinaz, Producer Abe Forman-Greenwald, Producer Nate Funaro, Produced by Patti Harrison, Story by Andres Salaff, Directed by Chris Ybarra, Assistant Director Bob's Burgers • Worms Of In-Rear-Ment • FOX • 20th Television Animation and Bento Box Animation Loren Bouchard, Executive Producer Jim Dauterive, Executive Producer Dan Fybel, Executive Producer Rich Rinaldi, Executive Producer Jon Schroeder, Executive Producer Nora Smith, Executive Producer/Written by Greg Thompson, Executive Producer Steven Davis, Co-Executive Producer Scott Jacobson, Co-Executive Producer Holly Schlesinger, Co-Executive Producer Lizzie Molyneux-Logelin, Co-Executive Producer Wendy Molyneux, Co-Executive Producer Kelvin Yu, Co-Executive Producer Janelle Momary-Neely, Supervising Producer Scott Greenberg, Animation Executive Producer Joel Kuwahara, Animation Executive Producer Michael Penketh, Animation Producer Chris Song, Directed by Bernard Derriman, Supervising Director Tony Gennaro, Supervising -
Download Player for Youtube Gratis
Download player for youtube gratis YouTube Video Player is a tool that lets you play YouTube videos in FLV format. YouTube Video Player leaves the complex operation to other. With Youtube Video Player Downloader now you can play and save captured FLV files on your hard drive and play it unlimited times without Internet connection. From Laguna Beach Biz Software: Looking for a fun video player? Here it is. Nothing complicated here. All you do is select video and you're all set. Download YouTube Videos and automatically convert them to wmv, avi, mpeg, mov, flv, mp4, 3gp, or mp3 file types. Special one-click download Internet. Player for YouTube allows you to browse, play, search, share and bookmark YouTube videos on your BlackBerry® device with a very easy to use interface. The following features are Download plem sek. By. mulyadisangputrbarito. Ummy Video Downloader latest version: Download HD videos or MP3 files in just 2 Ummy Video Downloader allows you to save YouTube videos to your. Free media player for Windows with built-in codecs and support for Youtube. features like the possibility to play Youtube videos or download subtitles. You've been waiting for it now it's here: THE free YouTube smart music player! Stream gives you access to all of YouTube music videos and lets you play them. Free YouTube Download Mit diesem Gratis-Programm "Free YouTube Download" können Sie Videos mit einem Klick von YouTube. You like to listen to music on YouTube or SoundCloud and want to save it for offline playing. Or you want to download soundtrack of a new.