Good Money Still Going Bad: Digital Thieves and the Hijacking of the Online Ad Business
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
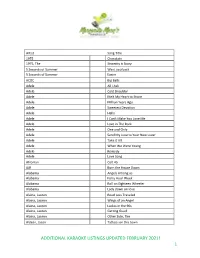
Additional Karaoke Listings Updated February 2021! 1
Artist Song Title 1975 Chocolate 1975, The Sincerity is Scary 5 Seconds of Summer Want you back 5 Seconds of Summer Easier ACDC Big Balls Adele All I Ask Adele Cold Shoulder Adele Melt My Heart to Stone Adele Million Years Ago Adele Sweetest Devotion Adele Hello Adele I Can't Make You Love Me Adele Love in The Dark Adele One and Only Adele Send My Love to Your New Lover Adele Take It All Adele When We Were Young Adele Remedy Adele Love Song Afroman Colt 45 AJR Burn the House Down Alabama Angels Among us Alabama Forty Hour Week Alabama Roll on Eighteen Wheeler Alabama Lady down on love Alaina, Lauren Road Less Traveled Alaina, Lauren Wings of an Angel Alaina, Lauren Ladies in the 90s Alaina, Lauren Getting Good Alaina, Lauren Other Side, The Aldean, Jason Tattoos on this town ADDITIONAL KARAOKE LISTINGS UPDATED FEBRUARY 2021! 1 Aldean, Jason Just Getting Started Aldean, Jason Lights Come On Aldean, Jason Little More Summertime, A Aldean, Jason This Plane Don't Go There Aldean, Jason Tonight Looks Good On You Aldean, Jason Gettin Warmed up Aldean, Jason Truth, The Aldean, Jason You make it easy Aldean, Jason Girl Like you Aldean, Jason Camouflage Hat Aldean, Jason We Back Aldean, Jason Rearview Town Aldean, Jason & Miranda Lambert Drowns The Whiskey Alice in Chains Man In The Box Alice in Chains No Excuses Alice in Chains Your Decision Alice in Chains Nutshell Alice in Chains Rooster Allan, Gary Every Storm (Runs Out of Rain) Allan, Gary Runaway Allen, Jimmie Best shot Anderson, John Swingin' Andress, Ingrid Lady Like Andress, Ingrid More Hearts Than Mine Angels and Airwaves Kiss & Tell Angston, Jon When it comes to loving you Animals, The Bring It On Home To Me Arctic Monkeys Do I Wanna Know Ariana Grande Breathin Arthur, James Say You Won't Let Go Arthur, James Naked Arthur, James Empty Space ADDITIONAL KARAOKE LISTINGS UPDATED FEBRUARY 2021! 2 Arthur, James Falling like the stars Arthur, James & Anne Marie Rewrite the Stars Arthur, James & Anne Marie Rewrite The Stars Ashanti Happy Ashanti Helpless (ft. -

Maxfield, Lori R.; Ratley, Michael E. Case Studies of Talented
DOCUMENT RESUME ED 414 687 EC 306 032 AUTHOR Reis, Sally M.; Hebert, Thomas P.; Diaz, Eva I.; Maxfield, Lori R.; Ratley, Michael E. TITLE Case Studies of Talented Students Who Achieve and Underachieve in an Urban High School. Research Monograph 95120. INSTITUTION National Research Center on the Gifted and Talented, Storrs, CT. SPONS AGENCY Office of Educational Research and Improvement (ED), Washington, DC. PUB DATE 1995-09-00 NOTE 284p. CONTRACT R206R00001 PUB TYPE Reports Descriptive (141) EDRS PRICE MF01/PC12 Plus Postage. DESCRIPTORS *Academic Achievement; Asian Americans; Black Students; Case Studies; Cultural Differences; Disadvantaged Youth; Family Environment; *Gifted; *High Achievement; High School Students; High Schools; Hispanic Americans; Homogeneous Grouping; Parent Participation; Poverty; Puerto Ricans; *Resilience (Personality); Self Esteem; Sex Differences; Social Support Groups; Student Characteristics; *Underachievement; *Urban Education; White Students ABSTRACT This 3-year study compared characteristics of high ability students who were identified as high achievers with students of similar ability who underachieved in school. The 35 students attended a large urban high school comprised of 60 percent Puerto Rican students, 20 percent African American, and the remainder White, Asian, and other. Qualitative methods were used to examine the perceptions of students, teachers, staff, and administrators concerning academic achievement. The study found that achievement and underachievement are not disparate concepts, since many students who underachieved had previously achieved at high levels and some generally high achieving students experienced periods of underachievement. A network of high achieving friends was characteristic of achieving students. No relationships were found between poverty and underachievement, between parental divorce and underachievement, or between family size and underachievement. -

1 | Page the LIGHTNING THIEF Percy Jackson and the Olympians
THE LIGHTNING THIEF Percy Jackson and the Olympians - Book 1 Rick Riordan 1 | Page 1 I ACCIDENTALLY VAPORIZE MY PRE-ALGEBRA TEACHER Look, I didn't want to be a half-blood. If you're reading this because you think you might be one, my advice is: close this book right now. Believe what-ever lie your mom or dad told you about your birth, and try to lead a normal life. Being a half-blood is dangerous. It's scary. Most of the time, it gets you killed in painful, nasty ways. If you're a normal kid, reading this because you think it's fiction, great. Read on. I envy you for being able to believe that none of this ever happened. But if you recognize yourself in these pages-if you feel something stirring inside-stop reading immediately. You might be one of us. And once you know that, it's only a mat-ter of time before they sense it too, and they'll come for you. Don't say I didn't warn you. My name is Percy Jackson. I'm twelve years old. Until a few months ago, I was a boarding student at Yancy Academy, a private school for troubled kids in upstate New York. 2 | Page Am I a troubled kid? Yeah. You could say that. I could start at any point in my short miserable life to prove it, but things really started going bad last May, when our sixth-grade class took a field trip to Manhattan- twenty-eight mental-case kids and two teachers on a yellow school bus, heading to the Metropolitan Museum of Art to look at ancient Greek and Roman stuff. -

How to Download Torrent Anonymously How to Download Torrent Anonymously
how to download torrent anonymously How to download torrent anonymously. Completing the CAPTCHA proves you are a human and gives you temporary access to the web property. What can I do to prevent this in the future? If you are on a personal connection, like at home, you can run an anti-virus scan on your device to make sure it is not infected with malware. If you are at an office or shared network, you can ask the network administrator to run a scan across the network looking for misconfigured or infected devices. Another way to prevent getting this page in the future is to use Privacy Pass. You may need to download version 2.0 now from the Chrome Web Store. Cloudflare Ray ID: 66b6c3aaaba884c8 • Your IP : 188.246.226.140 • Performance & security by Cloudflare. Download Torrents Anonymously: 6 Safe And Easy Ways. Who doesn’t want to know how to download torrents anonymously? The thing is, in order to download torrents anonymously you don’t need to have a lot of technical know-how. All you need to download torrents anonymously is some grit and a computer with an internet connection. The technology world never remains the same. In fact, new development and discoveries come to the surface of this industry every day. They also come into the attention of online users every year. Moreover, this allows us to do much more than we could do in the past, in faster and easier ways. A highly relevant aspect to mention at this stage is that: Now we can also download torrents anonymously from best torrent sites. -

The Effect of Film Sharing on P2P Networks on Box Office Sales
The effect of film sharing on P2P networks on box office sales Kęstutis Černiauskas Faculty of Computing Blekinge Institute of Technology SE-371 79 Karlskrona Sweden i This thesis is submitted to the Faculty of Computing at Blekinge Institute of Technology in partial fulfillment of the requirements for the degree of Master in Informatics (120 credits). Contact Information: Author(s): Kęstutis Černiauskas E-mail: [email protected] University advisor: Sara Eriksén Department Faculty of Computing Internet : www.bth.se Blekinge Institute of Technology Phone : +46 455 38 50 00 SE-371 79 Karlskrona, Sweden Fax : +46 455 38 50 57 ii ABSTRACT Context. Online piracy is widespread, controversial and poorly understood social phenomena that affects content creators, owners, and consumers. Online piracy, born from recent, rapid ITC changes, raises legal, ethical, and business challenges. Content owners, authors and content consumers should benefit from better understanding of online piracy. Improved, better adapted to marketplace and ITC changes content distribution models should benefit content owners and audiences. Objectives. Investigate online piracy effect on pirated product sales. Improve understanding of online piracy behaviors and process scale. Methods. This observational study investigated movie-sharing effect on U.S. box office. Movie sharing was observed over BitTorrent network, the most popular peer-to-peer file-sharing network. Relationship between piracy and sales was analyzed using linear regression model. Results. File sharing was found to have a slightly positive correlation with U.S. box office sales during first few weeks after film release, and no effect afterwards. Most of newly released movies are shared over BitTorrent network. -

Distributed Hash Table Implementation to Enable Security and Combat Malpractices
International Journal on Future Revolution in Computer Science & Communication Engineering ISSN: 2454-4248 Volume: 5 Issue: 2 09 – 12 _______________________________________________________________________________________________ Distributed Hash Table Implementation to Enable Security and Combat Malpractices Dr. T. Venkat Narayana Rao K. Vivek C. Pranita Professor, CSE, Student , CSE, Student , CSE, Sreenidhi Institute of Science and Sreenidhi Institute of Science and Sreenidhi Institute of Science and Technology Technology Technology Yamnampet, Hyderabad, India Yamnampet, Hyderabad, India Yamnampet, Hyderabad, India Abstract: Security has become a global problem in any field. Everyday millions of cyber crimes are being recorded worldwide. Many of them include unethical hacking, unauthorized hampering of files and many more. To avoid such malicious practices many technologies have come up. One such security is DHT or Distributed hash tables. A recently upcoming cyber security, it helps the receiver and sender to send and receive files that are authentic. It also helps to find out if the file is manipulated or tampered by a third party or an unauthorized user by generating unique hash values. This paper mainly focuses on such distributed networks and the security they provide in order to stop malpractices. Keywords: Distributed Hash Value (DHT), Peer to Peer Network, Hashing Algorithms. __________________________________________________*****_________________________________________________ I. Introduction like service over a network where it is distributed, where it We are becoming technologically advanced day by day. provides access to a key value which is commonly shared. With increasing technology the need to be secured has also The key value is distributed over nodes participating in the been increased. Online security and authentication have network with great performance and scalability. -

Edition 2019
YEAR-END EDITION 2019 Global Headquarters Republic Records 1755 Broadway, New York City 10019 © 2019 Mediabase 1 REPUBLIC #1 FOR 6TH STRAIGHT YEAR UMG SCORES TOP 3 -- AS INTERSCOPE, CAPITOL CLAIM #2 AND #3 SPOTS For the sixth consecutive year, REPUBLIC is the #1 label for Mediabase chart share. • The 2019 chart year is based on the time period from November 11, 2018 through November 9, 2019. • All spins are tallied for the full 52 weeks and then converted into percentages for the chart share. • The final chart share includes all applicable label split-credit as submitted to Mediabase during the year. • For artists, if a song had split-credit, each artist featured was given the same percentage for the artist category that was assigned to the label share. REPUBLIC’S total chart share was 19.2% -- up from 16.3% last year. Their Top 40 chart share of 28.0% was a notable gain over the 22.1% they had in 2018. REPUBLIC took the #1 spot at Rhythmic with 20.8%. They were also the leader at Hot AC; where a fourth quarter surge landed them at #1 with 20.0%, that was up from a second place 14.0% finish in 2018. Other highlights for REPUBLIC in 2019: • The label’s total spin counts for the year across all formats came in at 8.38 million, an increase of 20.2% over 2018. • This marks the label’s second highest spin total in its history. • REPUBLIC had several artist accomplishments, scoring three of the top four at Top 40 with Ariana Grande (#1), Post Malone (#2), and the Jonas Brothers (#4). -

An Ideal Distributism Is Only Improbable. Even an Ideal Communism Is Only Impossible
Volume 14 Number 2-3, NoVember/December 2010 $5.50 An ideal Distributism is only improbable. Even an ideal Communism is only impossible. But an ideal Capitalism is inconceivable. —G.K. Chesterton The 29th Annual G.K. Chesterton Conference Talks Are Here! DaLE aHLquIst (President of the American Chesterton society) “In Praise of Jones” Qty DaVID ZaCH (Futurist) “A Great Many Clever Things: The Mistake about Technology” Qty rICHarD aLEmaN (editor of the Distributist review) “The Mistake about Distributism” Qty JosEPH PEarCE (Author) “The Mistake About Progress” Qty JamEs WooDruFF (Mathematics Instructor at Worcester Academy) “GKC and Edmund Burke: The Mistake about Conservatism” Qty rEGINa DomaN (Author) tom martIN (Philosophy Professor at university of nebraska-Kearney) “The Evangelization of the Imagination”Qty “The Mistake about the Social Sciences”Qty Fr. IaN KEr (theology Professor from oxford university) JamEs o’KEEFE (Independent Video Journalist) “Chesterton and Newman” Qty “The Mistake about the Social Services”Qty Fr. PEtEr MilwarD (Professor emeritus from sophia university, tokyo) Dr. WILLIam marsHNEr (theology Professor at Christendom College) “Chesterton and Shakespeare and Today”Qty “The Mistake about Theology” Qty NaNCy BroWN (Author and ACs Blogmistress) “The Woman Who Was Chesterton” Qty 3 Formats: CDs: Single Talk: $6.00 each OR order the Complete set The American Chesterton Society of CDs for $60.00 (save $12) 4117 Pebblebrook Circle, Minneapolis, Mn 55437 mP3 Format: Bundle: 12 Talks in MP3 format on 1 disc: 952-831-3096 -

April 11, 2021 Second Sunday of Easter 13900 Biscayne Ave
APRIL 11, 2021 SECOND SUNDAY OF EASTER 13900 BISCAYNE AVE. W ROSEMOUNT, MN 55068 PHONE: 651-423-4402 www.stjosephcommunity.org Weekend Mass times: Saturday: 5:00 pm Sunday: 7 am, 8:30 am, & 10:30 am Online Auction is OPEN! To Donate to the 2021 GALA event: Text Donation amount to: 8444601236 Or scan QR code www.stjsgala.org PADRE PAUL’S PONDERINGS Doubt as the Companion of Faith I never much cared for the term “doubting Thomas,” because it’s Third, trust. We don’t know the big plan. And it can be hard to a really unfair label to give Saint Thomas, who is front and see past the short-term situation we may be in. I think of Saint center in this week’s Gospel. He is not there when Jesus comes Charles de Foucauld, the saint who ministered to the Muslims in the first time; perhaps upset and troubled about what has Algeria. He once said something to the effect of it maybe just happened and needing to take some time alone. The first time being his job to till the soil when he hadn’t gotten any converts Jesus comes everyone present sees the wounds in His hands and to Christianity. God is working things out, and with God all side as He says “peace be with you.” When Thomas has this things are possible. Sometimes His timeline and ours differ, but opportunity, he says “My Lord and My God,” one of the boldest ultimately things work out because God is in control. proclamations of faith in the Bible. -
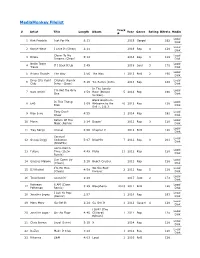
Mediamonkey Filelist
MediaMonkey Filelist Track # Artist Title Length Album Year Genre Rating Bitrate Media # Local 1 Kirk Franklin Just For Me 5:11 2019 Gospel 182 Disk Local 2 Kanye West I Love It (Clean) 2:11 2019 Rap 4 128 Disk Closer To My Local 3 Drake 5:14 2014 Rap 3 128 Dreams (Clean) Disk Nellie Tager Local 4 If I Back It Up 3:49 2018 Soul 3 172 Travis Disk Local 5 Ariana Grande The Way 3:56 The Way 1 2013 RnB 2 190 Disk Drop City Yacht Crickets (Remix Local 6 5:16 T.I. Remix (Intro 2013 Rap 128 Club Intro - Clean) Disk In The Lonely I'm Not the Only Local 7 Sam Smith 3:59 Hour (Deluxe 5 2014 Pop 190 One Disk Version) Block Brochure: In This Thang Local 8 E40 3:09 Welcome to the 16 2012 Rap 128 Breh Disk Soil 1, 2 & 3 They Don't Local 9 Rico Love 4:55 1 2014 Rap 182 Know Disk Return Of The Local 10 Mann 3:34 Buzzin' 2011 Rap 3 128 Macc (Remix) Disk Local 11 Trey Songz Unusal 4:00 Chapter V 2012 RnB 128 Disk Sensual Local 12 Snoop Dogg Seduction 5:07 BlissMix 7 2012 Rap 0 201 Disk (BlissMix) Same Damn Local 13 Future Time (Clean 4:49 Pluto 11 2012 Rap 128 Disk Remix) Sun Come Up Local 14 Glasses Malone 3:20 Beach Cruiser 2011 Rap 128 (Clean) Disk I'm On One We the Best Local 15 DJ Khaled 4:59 2 2011 Rap 5 128 (Clean) Forever Disk Local 16 Tessellated Searchin' 2:29 2017 Jazz 2 173 Disk Rahsaan 6 AM (Clean Local 17 3:29 Bleuphoria 2813 2011 RnB 128 Patterson Remix) Disk I Luh Ya Papi Local 18 Jennifer Lopez 2:57 1 2014 Rap 193 (Remix) Disk Local 19 Mary Mary Go Get It 2:24 Go Get It 1 2012 Gospel 4 128 Disk LOVE? [The Local 20 Jennifer Lopez On the -

Unveiling the I2P Web Structure: a Connectivity Analysis
Unveiling the I2P web structure: a connectivity analysis Roberto Magan-Carri´ on,´ Alberto Abellan-Galera,´ Gabriel Macia-Fern´ andez´ and Pedro Garc´ıa-Teodoro Network Engineering & Security Group Dpt. of Signal Theory, Telematics and Communications - CITIC University of Granada - Spain Email: [email protected], [email protected], [email protected], [email protected] Abstract—Web is a primary and essential service to share the literature have analyzed the content and services offered information among users and organizations at present all over through this kind of technologies [6], [7], [2], as well as the world. Despite the current significance of such a kind of other relevant aspects like site popularity [8], topology and traffic on the Internet, the so-called Surface Web traffic has been estimated in just about 5% of the total. The rest of the dimensions [9], or classifying network traffic and darknet volume of this type of traffic corresponds to the portion of applications [10], [11], [12], [13], [14]. Web known as Deep Web. These contents are not accessible Two of the most popular darknets at present are The Onion by search engines because they are authentication protected Router (TOR; https://www.torproject.org/) and The Invisible contents or pages that are only reachable through the well Internet Project (I2P;https://geti2p.net/en/). This paper is fo- known as darknets. To browse through darknets websites special authorization or specific software and configurations are needed. cused on exploring and investigating the contents and structure Despite TOR is the most used darknet nowadays, there are of the websites in I2P, the so-called eepsites. -

Piratebrowser Artifacts
PirateBrowser Artifacts Written by Chris Antonovich Researched by Olivia Hatalsky 175 Lakeside Ave, Room 300A Phone: 802/865-5744 Fax: 802/865-6446 http://www.lcdi.champlin.edu Published Date Patrick Leahy Center for Digital Investigation (LCDI) Disclaimer: This document contains information based on research that has been gathered by employee(s) of The Senator Patrick Leahy Center for Digital Investigation (LCDI). The data contained in this project is submitted voluntarily and is unaudited. Every effort has been made by LCDI to assure the accuracy and reliability of the data contained in this report. However, LCDI nor any of our employees make no representation, warranty or guarantee in connection with this report and hereby expressly disclaims any liability or responsibility for loss or damage resulting from use of this data. Information in this report can be downloaded and redistributed by any person or persons. Any redistribution must maintain the LCDI logo and any references from this report must be properly annotated. Contents Introduction ............................................................................................................................................................................. 2 Background: ........................................................................................................................................................................ 2 Purpose and Scope: ............................................................................................................................................................