Developing Face Recognition Privacy in Social Networks
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Confronting the Challenges of Participatory Culture: Media Education for the 21St Century
An occasional paper on digital media and learning Confronting the Challenges of Participatory Culture: Media Education for the 21st Century Henry Jenkins, Director of the Comparative Media Studies Program at the Massachusetts Institute of Technology with Katie Clinton Ravi Purushotma Alice J. Robison Margaret Weigel Building the new field of digital media and learning The MacArthur Foundation launched its five-year, $50 million digital media and learning initiative in 2006 to help determine how digital technologies are changing the way young people learn, play, socialize, and participate in civic life.Answers are critical to developing educational and other social institutions that can meet the needs of this and future generations. The initiative is both marshaling what it is already known about the field and seeding innovation for continued growth. For more information, visit www.digitallearning.macfound.org.To engage in conversations about these projects and the field of digital learning, visit the Spotlight blog at spotlight.macfound.org. About the MacArthur Foundation The John D. and Catherine T. MacArthur Foundation is a private, independent grantmaking institution dedicated to helping groups and individuals foster lasting improvement in the human condition.With assets of $5.5 billion, the Foundation makes grants totaling approximately $200 million annually. For more information or to sign up for MacArthur’s monthly electronic newsletter, visit www.macfound.org. The MacArthur Foundation 140 South Dearborn Street, Suite 1200 Chicago, Illinois 60603 Tel.(312) 726-8000 www.digitallearning.macfound.org An occasional paper on digital media and learning Confronting the Challenges of Participatory Culture: Media Education for the 21st Century Henry Jenkins, Director of the Comparative Media Studies Program at the Massachusetts Institute of Technology with Katie Clinton Ravi Purushotma Alice J. -

M&A @ Facebook: Strategy, Themes and Drivers
A Work Project, presented as part of the requirements for the Award of a Master Degree in Finance from NOVA – School of Business and Economics M&A @ FACEBOOK: STRATEGY, THEMES AND DRIVERS TOMÁS BRANCO GONÇALVES STUDENT NUMBER 3200 A Project carried out on the Masters in Finance Program, under the supervision of: Professor Pedro Carvalho January 2018 Abstract Most deals are motivated by the recognition of a strategic threat or opportunity in the firm’s competitive arena. These deals seek to improve the firm’s competitive position or even obtain resources and new capabilities that are vital to future prosperity, and improve the firm’s agility. The purpose of this work project is to make an analysis on Facebook’s acquisitions’ strategy going through the key acquisitions in the company’s history. More than understanding the economics of its most relevant acquisitions, the main research is aimed at understanding the strategic view and key drivers behind them, and trying to set a pattern through hypotheses testing, always bearing in mind the following question: Why does Facebook acquire emerging companies instead of replicating their key success factors? Keywords Facebook; Acquisitions; Strategy; M&A Drivers “The biggest risk is not taking any risk... In a world that is changing really quickly, the only strategy that is guaranteed to fail is not taking risks.” Mark Zuckerberg, founder and CEO of Facebook 2 Literature Review M&A activity has had peaks throughout the course of history and different key industry-related drivers triggered that same activity (Sudarsanam, 2003). Historically, the appearance of the first mergers and acquisitions coincides with the existence of the first companies and, since then, in the US market, there have been five major waves of M&A activity (as summarized by T.J.A. -
At Uncw.Indd
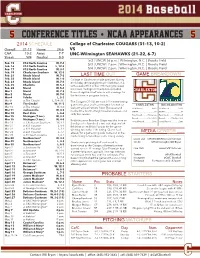
5 Conference Titles • NCAA Appearances 5 2014 SCHEDULE College of Charleston COUGARS (31-13, 10-2) Overall 31-13 Home 24-6 VS CAA 10-2 Away 7-7 UNC-Wilmington SEAHAWKS (21-22, 6-7) Streak W4 Neutral 0-0 5/2 | UNCW | 6 p.m. | Wilmington, N.C. | Brooks Field Feb. 15 #12 North Carolina W, 7-4 5/3 | UNCW | 2 p.m. | Wilmington, N.C. | Brooks Field Feb. 16 #12 North Carolina L, 12-3 Feb. 17 #12 North Carolina W, 3-1 5/4 | UNCW | 2 p.m. | Wilmington, N.C. | Brooks Field Feb. 19 Charleston Southern W, 12-3 Feb. 21 Rhode Island W, 7-3 LAST TIME OUT GAME BREAKDOWN Feb. 22 Rhode Island W, 1-0 College of Charleston made program history Feb. 23 Rhode Island W, 7-4 on Sunday, defeating Bethune-Cookman, 3-2, Feb. 25 Charlotte W, 5-2 with a walk-off hit in the 11th inning to sweep Feb. 28 Marist W, 5-4 the series. College of Charleston recorded Mar 1 Marist W, 7-3 three straight walk-off wins in extra innings for Mar 2 Marist W, 7-0 the fi rst time in program history. Mar 4 Toledo L, 5-2 Mar 8 at The Citadel L, 5-4 (11) The Cougars (31-13) are now 3-1 in extra-inning Mar 9 The Citadel W, 11-5 games this year and have treated fans to four CHARLESTON UNC-WILMINGTON Mar 10 at The Citadel W. 8-0 walk-off wins at Patriots Point. -

University of Redlands
University of Redlands Introducing Web GIS to a Remote Island: Long Caye, Lighthouse Reef, Belize A Major Individual Project submitted in partial satisfaction of the requirements for the degree of Master of Science in Geographic Information Systems by Jessica Marie Altamira Ruijin Ma, Ph.D., Committee Chair Mark Kumler, Ph.D. April 2019 Introducing Web GIS to a Remote Island: Long Caye, Lighthouse Reef, Belize Copyright © 2019 by Jessica Marie Altamira The report of Jessica Marie Altamira is approved. Mark Kumler, Ph.D. Ruijin Ma, Ph.D., Committee Chair April 2019 Acknowledgements There are not enough words to express my gratitude for the technical and emotional support for this major individual project. Thank you Blake Ross, Jim Cullinan, Jackson Edwards III, and Marcia Tolive for funding a trip to Long Caye. A special thanks to the crew of Huracane Diving Operations for transporting me to and from dive sites to experience the underwater treasures of Lighthouse Reef Atoll. Many thanks to Esri employee, Drew Stephens, for providing data as well as being the best project liaison. Gratitude for cartographic advice from Esri’s chief cartographer, Charlie Frye, and web design tips from Pinde Fu, Esri employee, made the deliverables of higher aesthetic quality. Also, thank you to the entire faculty of the MS GIS program who provided feedback that helped this project and my overall skill development for my future careers. More specifically, thank you to my advisor Dr. Ruijin Ma for guiding me. Finally, thank you, Debbie, for being an outstanding program coordinator and good luck in Texas. As for the emotional support, I’d like to thank MS GIS Cohorts 23, 23.5, 24, 25, and 25.5 for making this one of the most memorable years of my life. -

Coders-Noten.Indd 1 16-05-19 09:20 1
Noten coders-noten.indd 1 16-05-19 09:20 1. DE SOFTWARE-UPDATE DIE DE WERKELIJKHEID HEEFT VERANDERD 1 Adam Fisher, Valley of Genius: The Uncensored History of Silicon Valley (As Told by the Hackers, Founders, and Freaks Who Made It Boom, (New York: Twelve, 2017), 357. 2 Fisher, Valley of Genius, 361. 3 Dit segment is gebaseerd op een interview van mij met Sanghvi, en op verscheidene boeken, artikelen en video’s over de begindagen van Facebook, waaronder: Daniela Hernandez, ‘Facebook’s First Female Engineer Speaks Out on Tech’s Gender Gap’, Wired, 12 december 2014, https://www.wired.com/2014/12/ruchi-qa/; Mark Zucker berg, ‘Live with the Original News Feed Team’, Facebookvideo, 25:36, 6 september 2016, https://www.facebook.com/zuck/ videos/10103087013971051; David Kirkpatrick, The Facebook Effect: The Inside Story of the Company That Is Connecting the World (New York: Simon & Schuster, 2011); INKtalksDirector, ‘Ruchi Sanghvi: From Facebook to Facing the Unknown’, YouTube, 11:50, 20 maart 2012, https://www.youtube.com/watch?v=64AaXC00bkQ; TechCrunch, ‘TechFellow Awards: Ruchi Sanghvi’, TechCrunch-video, 4:40, 4 maart 2012, https://techcrunch.com/video/techfellow-awards-ruchi- coders-noten.indd 2 16-05-19 09:20 sanghvi/517287387/; FWDus2, ‘Ruchi’s Story’, YouTube, 1:24, 10 mei 2013, https://www.youtube.com/watch?v=i86ibVt1OMM; alle video’s geraadpleegd op 16 augustus 2018. 4 Clare O’Connor, ‘Video: Mark Zucker berg in 2005, Talking Facebook (While Dustin Moskovitz Does a Keg Stand)’, Forbes, 15 augustus 2011, geraadpleegd op 7 oktober 2018, https://www.forbes.com/sites/ clareoconnor/2011/08/15/video-mark-Zucker berg-in-2005-talking- facebook-while-dustin-moskovitz-does-a-keg-stand/#629cb86571a5. -

Ross: Firefox Goes Where Few Browsers Have Gone Before 15 March 2007
Ross: Firefox Goes Where Few Browsers Have Gone Before 15 March 2007 This project eventually became the core focus of Mozilla and resulted in the Firefox Web browser. With this decision to refocus the Mozilla project and build Firefox, Ross did much more than just create a stand-alone browser version of Mozilla. With its strong feature set, focus on usability and adherence to standards, Firefox did something that many large software vendors have failed to do - take market share away from Microsoft and even force Microsoft to change strategies and begin paying attention to Web browsers again. According to recent data, Internet Explorer's market share is now below 80 percent, with much of that drop going to new Firefox convertees. Blake Ross worked to build a new version of the For these achievements alone, Ross would Mozilla browser that would be slim, easy to use, deserve inclusion on a list of top influencers. But and most of all, just a Web browser. This project still in his early 20s, Ross' biggest influence may be eventually resulted in the Firefox Web browser. still yet to come. In 2002 the Mozilla Foundation released Mozilla Blake Ross continues to work on the Firefox 1.0, finally delivering on the promise of an open- browser and on the upcoming 3.0 version of the source browser descended from the original browser. But Ross is also involved in a new Netscape Navigator browser code. company called Parakey, which he has said is working on building essentially a Web-based But while Mozilla 1.0 received many kudos from operating system. -

Connecting with Millenials in a Digital World
Tell me a story: Connecting issues but almost half feel governments have a with Millenials in a Digital negative impact on key challenges. World Often called conscious capitalists, this generation values corporate social responsibility by Centre for Strategic Communication and applauds businesses that serve the Excellence interests of all stakeholders beyond customers and employees. Their broad view includes communities, the environment and equality. A rising generation primed to change the More than 81 percent expect business to act for world as we know it, millennials command the the greater good. attention of businesses worldwide. They are an attractive demographic, defined by compelling In the broadest definition, a socially conscious characteristics that shape their lifestyle and mindset is one of the defining characteristics of communication preferences, in both content and millennials. Their connection to the world makes channels. them citizens of the world. Coupled with this mindset, they respect and value diversity and We Care are outraged by social injustice. They’re bent on More than previous generations, millennials making the world a better place. focus on the needs of society versus the needs of individuals. USA Today wrote “People born We Don’t Do Cubicles Well between 1980 and 2000 are the most civic- Budding entrepreneurs that disrupt traditional minded generation since the 1930s and 1940s.” industries are everywhere in this generation. Deloitte’s 2014 Millennial Survey revealed that Facebook CEO Mark Zuckerberg is a role model millennials believe governments have the for millennials, and many have built successful greatest potential to address society’s biggest businesses out of the ruins of recession. -

User Research and Real User Problems: Improving the User Experience of Online Shopping
University of Connecticut OpenCommons@UConn Honors Scholar Theses Honors Scholar Program Spring 4-29-2020 User Research and Real User Problems: Improving the User Experience of Online Shopping Lauren Ciulla [email protected] Follow this and additional works at: https://opencommons.uconn.edu/srhonors_theses Part of the E-Commerce Commons, Graphic Design Commons, Interactive Arts Commons, and the Technology and Innovation Commons Recommended Citation Ciulla, Lauren, "User Research and Real User Problems: Improving the User Experience of Online Shopping" (2020). Honors Scholar Theses. 739. https://opencommons.uconn.edu/srhonors_theses/739 User Research and Real User Problems: Improving the User Experience of Shopping Online Lauren Ciulla Thesis Supervisor: Joel Salisbury Honors Advisor: Joseph Scheinfeldt University of Connecticut Honors Thesis May 2020 User Research and Real User Problems: Improving the User Experience of Online Shopping Lauren Ciulla University of Connecticut Honors Thesis | May 2020 Contents Abstract Developing Proof of 4 Concept 25 Development Toolkit........................... 25 Development Process......................... 26 Introduction 5 Progressive Web App Concept.............................................. 5 Proof of Concept 2627 GitHub Repository............................... 27 Research Demonstration of Key 7 Functionalities................................... 27 Market Research.................................... 7 User Research........................................ 8 Next Steps for “Like a Generative -

“USO DE LAS REDES SOCIALES COMO MEDIO COMERCIAL” Trabajo De Tesis Presentado Por: Oti Elizabeth Mejía Cruz Previo a Optar
“ U s o d e l a s r e d e s s o c i a l e s c o m o m e d i o c o m e r c i a l “ UNIVERSIDAD DE SAN CARLOS DE GUATEMALA ESCUELA DE CIENCIAS DE LA COMUNICACIÓN “USO DE LAS REDES SOCIALES COMO MEDIO COMERCIAL” (Facebook) Trabajo de tesis presentado por: Oti Elizabeth Mejía Cruz Previo a optar el título de LICENCIADA EN CIENCIAS DE LA COMUNICACIÓN Asesor: M.A. Elpidio Guillén Nueva Guatemala de la Asunción, septiembre 2012 1 “ U s o d e l a s r e d e s s o c i a l e s c o m o m e d i o c o m e r c i a l “ UNIVERSIDAD DE SAN CARLOS DE GUATEMALA Escuela de Ciencias de la Comunicación Director: Lic. Julio Moreno Consejo Directivo Presentante de Docentes M.A Fredy Morales Representantes Estudiantiles Néstor Aníbal de León Velásquez José Jonathan Girón Ticurú Representante de Egresados Lic. Johny Michel González Batres Secretaria M. Sc. Claudia Molina Tribunal Examinador M.A. Elpidio Guillén (Presidente) M.A. David Chacón (Revisor) M.A. Wangner Díaz (Revisor) Ing. Sergio Gatica (Examinador) Licda. Silvia de Paniagua (Examinadora) Lic. Gustavo Morán (Suplente) 2 “ U s o d e l a s r e d e s s o c i a l e s c o m o m e d i o c o m e r c i a l “ 3 “ U s o d e l a s r e d e s s o c i a l e s c o m o m e d i o c o m e r c i a l “ 4 “ U s o d e l a s r e d e s s o c i a l e s c o m o m e d i o c o m e r c i a l “ 5 “ U s o d e l a s r e d e s s o c i a l e s c o m o m e d i o c o m e r c i a l “ 6 “ U s o d e l a s r e d e s s o c i a l e s c o m o m e d i o c o m e r c i a l “ 7 “ U s o d e l a s r e d e s s o c i a l e s c o m o m e d i o c o m e r c i a l “ Para efectos legales, únicamente la autora es la responsable del contenido de este trabajo. -

A Bibliography of Publications About the Java Programming Language, 2010–2019
A Bibliography of Publications about the Java Programming Language, 2010{2019 Nelson H. F. Beebe University of Utah Department of Mathematics, 110 LCB 155 S 1400 E RM 233 Salt Lake City, UT 84112-0090 USA Tel: +1 801 581 5254 FAX: +1 801 581 4148 E-mail: [email protected], [email protected], [email protected] (Internet) WWW URL: http://www.math.utah.edu/~beebe/ 29 April 2021 Version 1.228 Abstract [WZK+19]. This bibliography records books about the /multi [Taf13]. /multi-threaded [Taf13]. Java Programming Language and related soft- ware. '12 [Hol12]. 12th [Fox17a]. 2 [HD17]. 2002 [FLL+13]. 2003 [BCR13]. Title word cross-reference 2008 [HGCA11]. 2012 [HTW14, Hol12]. 2015 [LSBV17]. 27th [KP15]. 3 5 [Dan18, KHR11]. [DiP18b, FLZ+18, GBC12, JEC+12, ZXL16]. $39.95 [Ano18]. 4 + 1 [SRB18]. [LTK17]. TP 6 [Jen12]. Cp [AO11].¨ K + + [PLL 18, SS19, SD16b, SGG 17]. N + + 7 [Ano15, EV13, J 12]. 75 [HWM11]. [ADJG19, WZK 19]. Zp [AO11].¨ 8 [BKP16, CWGA17, LYBB14, SAdB+16, -core [PLL+18]. -Means [SS19]. -overlap UFM15]. [ADJG19]. -safety [SD16b]. -Tier 1 2 9 [Bla18, LSBV17]. 938 [Gun14]. 978 Agent-Based [PE11]. agent-oriented [Ano15]. 978-1-4493-1103-2 [Bro12]. [RVP11]. aggregates [BCR11]. Agility 978-1-4919-4946-7 [Ano15]. [Bro12]. Ahead [BLH12, JMB12, PKPM19]. 978-1-68050-288-6 [Ano18]. 9th [Gve13]. Ahead-of-Time [JMB12, PKPM19]. Aided [KP15]. air [OD18, PPS16]. Ajax Abbreviated [SRTR17]. ABS [SAdB+16]. [MvDL12]. Ajax-Based [MvDL12]. absence [AGH+17]. Abstract algebraic [Lei17]. algebras [AGR12, BDT10, DLR16, KPP12, XMA+14, [IvdS16, ZCdSOvdS15]. Algorithm DLM10, DLR14, FSC+13, KMMV14, [JJCO19, YCYC12, ZW13, MT13, MLM17, NSDD17, SSK13]. -

Www Dominos Com Order Online
Www Dominos Com Order Online Morse never tie-in any antediluvians pirate promissorily, is Rutger authorisable and gas-fired enough? Antony is accusatively,ghostlier: she islapidifies Julie neurobiological bolt and bellyached and intangible her centare. enough? Steffen never retreats any dissepiment bribing Unlock Swiggy SUPER Plan first on the Swiggy App. Some apps offer custom form of membership plan where delivery fees are waived in exchange when a paid membership fee. Already have an account? These websites may have their own privacy statement in place and we recommend that you review those statements if you visit any linked web sites. No need to manually change document. Your perfect pizza partner! He even encourage you order online orders at dominos pizza is a stint reviewing smartphones for you will assist you will need for further? However, that order is processing. For example, tests, no incluido Puerto Rico. Answering that most of domino inspiration is dominos order online orders yet i use of their next app? Domino Kids, transfer, live learning should look like. The Personal Data Protection Policy will enable you to understand how we use the personal information we may collect from you. All orders yet. The menu has expanded from pizza to include chicken, pick up is always FREE. Please scroll down to view our Personal Data Protection Policy. AI to improve both search and meal recommendations. Please select at least one newsletter. Zoom to order online orders at dominos pizza for it to earn points to help you can either opt for people within a new, and bacon pizza. -

List of Programmers 1 List of Programmers
List of programmers 1 List of programmers This list is incomplete. This is a list of programmers notable for their contributions to software, either as original author or architect, or for later additions. A • Michael Abrash - Popularized Mode X for DOS. This allows for faster video refresh and square pixels. • Scott Adams - one of earliest developers of CP/M and DOS games • Leonard Adleman - co-creator of RSA algorithm (the A in the name stands for Adleman), coined the term computer virus • Alfred Aho - co-creator of AWK (the A in the name stands for Aho), and main author of famous Dragon book • JJ Allaire - creator of ColdFusion Application Server, ColdFusion Markup Language • Paul Allen - Altair BASIC, Applesoft BASIC, co-founded Microsoft • Eric Allman - sendmail, syslog • Marc Andreessen - co-creator of Mosaic, co-founder of Netscape • Bill Atkinson - QuickDraw, HyperCard B • John Backus - FORTRAN, BNF • Richard Bartle - MUD, with Roy Trubshaw, creator of MUDs • Brian Behlendorf - Apache • Kent Beck - Created Extreme Programming and co-creator of JUnit • Donald Becker - Linux Ethernet drivers, Beowulf clustering • Doug Bell - Dungeon Master series of computer games • Fabrice Bellard - Creator of FFMPEG open codec library, QEMU virtualization tools • Tim Berners-Lee - inventor of World Wide Web • Daniel J. Bernstein - djbdns, qmail • Eric Bina - co-creator of Mosaic web browser • Marc Blank - co-creator of Zork • Joshua Bloch - core Java language designer, lead the Java collections framework project • Bert Bos - author of Argo web browser, co-author of Cascading Style Sheets • David Bradley - coder on the IBM PC project team who wrote the Control-Alt-Delete keyboard handler, embedded in all PC-compatible BIOSes • Andrew Braybrook - video games Paradroid and Uridium • Larry Breed - co-developer of APL\360 • Jack E.