Manycore Operating Systems for Safety-Critical Systems
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

In This Issue
FALL 2019 IN THIS ISSUE JONATHAN BISS CELEBRATING BEETHOVEN: PART I November 5 DANISH STRING QUARTET November 7 PILOBOLUS COME TO YOUR SENSES November 14–16 GABRIEL KAHANE November 23 MFA IN Fall 2019 | Volume 16, No. 2 ARTS LEADERSHIP FEATURE In This Issue Feature 3 ‘Indecent,’ or What it Means to Create Queer Jewish Theatre in Seattle Dialogue 9 Meet the Host of Tiny Tots Concert Series 13 We’re Celebrating 50 Years Empowering a new wave of Arts, Culture and Community of socially responsible Intermission Brain arts professionals Transmission 12 Test yourself with our Online and in-person trivia quiz! information sessions Upcoming Events seattleu.edu/artsleaderhip/graduate 15 Fall 2019 PAUL HEPPNER President Encore Stages is an Encore arts MIKE HATHAWAY Senior Vice President program that features stories Encore Ad 8-27-19.indd 1 8/27/19 1:42 PM KAJSA PUCKETT Vice President, about our local arts community Sales & Marketing alongside information about GENAY GENEREUX Accounting & performances. Encore Stages is Office Manager a publication of Encore Media Production Group. We also publish specialty SUSAN PETERSON Vice President, Production publications, including the SIFF JENNIFER SUGDEN Assistant Production Guide and Catalog, Official Seattle Manager ANA ALVIRA, STEVIE VANBRONKHORST Pride Guide, and the Seafair Production Artists and Graphic Designers Commemorative Magazine. Learn more at encorespotlight.com. Sales MARILYN KALLINS, TERRI REED Encore Stages features the San Francisco/Bay Area Account Executives BRIEANNA HANSEN, AMELIA HEPPNER, following organizations: ANN MANNING Seattle Area Account Executives CAROL YIP Sales Coordinator Marketing SHAUN SWICK Senior Designer & Digital Lead CIARA CAYA Marketing Coordinator Encore Media Group 425 North 85th Street • Seattle, WA 98103 800.308.2898 • 206.443.0445 [email protected] encoremediagroup.com Encore Arts Programs and Encore Stages are published monthly by Encore Media Group to serve musical and theatrical events in the Puget Sound and San Francisco Bay Areas. -

Automated and Modular Refinement Reasoning for Concurrent Programs
Automated and modular refinement reasoning for concurrent programs Chris Hawblitzel Erez Petrank Shaz Qadeer Serdar Tasiran Microsoft Technion Microsoft Ko¸cUniversity Abstract notable successes using the refinement approach in- clude the work of Abrial et al. [2] and the proof of full We present civl, a language and verifier for concur- functional correctness of the seL4 microkernel [37]. rent programs based on automated and modular re- This paper presents the first general and automated finement reasoning. civl supports reasoning about proof system for refinement verification of shared- a concurrent program at many levels of abstraction. memory multithreaded software. Atomic actions in a high-level description are refined We present our verification approach in the context to fine-grain and optimized lower-level implementa- of civl, an idealized concurrent programming lan- tions. A novel combination of automata theoretic guage. In civl, a program is described as a collection and logic-based checks is used to verify refinement. of procedures whose implementation can use the stan- Modular specifications and proof annotations, such dard features such as assignment, conditionals, loops, as location invariants and procedure pre- and post- procedure calls, and thread creation. Each procedure conditions, are specified separately, independently at accesses shared global variables only through invoca- each level in terms of the variables visible at that tions of atomic actions. A subset of the atomic ac- level. We have implemented as an extension to civl tions may be refined by new procedures and a new the language and verifier. We have used boogie civl program is obtained by replacing the invocation of an to refine a realistic concurrent garbage collection al- atomic action by a call to the corresponding proce- gorithm from a simple high-level specification down dure refining the action. -

Openpiton: an Open Source Manycore Research Framework
OpenPiton: An Open Source Manycore Research Framework Jonathan Balkind Michael McKeown Yaosheng Fu Tri Nguyen Yanqi Zhou Alexey Lavrov Mohammad Shahrad Adi Fuchs Samuel Payne ∗ Xiaohua Liang Matthew Matl David Wentzlaff Princeton University fjbalkind,mmckeown,yfu,trin,yanqiz,alavrov,mshahrad,[email protected], [email protected], fxiaohua,mmatl,[email protected] Abstract chipset Industry is building larger, more complex, manycore proces- sors on the back of strong institutional knowledge, but aca- demic projects face difficulties in replicating that scale. To Tile alleviate these difficulties and to develop and share knowl- edge, the community needs open architecture frameworks for simulation, synthesis, and software exploration which Chip support extensibility, scalability, and configurability, along- side an established base of verification tools and supported software. In this paper we present OpenPiton, an open source framework for building scalable architecture research proto- types from 1 core to 500 million cores. OpenPiton is the world’s first open source, general-purpose, multithreaded manycore processor and framework. OpenPiton leverages the industry hardened OpenSPARC T1 core with modifica- Figure 1: OpenPiton Architecture. Multiple manycore chips tions and builds upon it with a scratch-built, scalable uncore are connected together with chipset logic and networks to creating a flexible, modern manycore design. In addition, build large scalable manycore systems. OpenPiton’s cache OpenPiton provides synthesis and backend scripts for ASIC coherence protocol extends off chip. and FPGA to enable other researchers to bring their designs to implementation. OpenPiton provides a complete verifica- tion infrastructure of over 8000 tests, is supported by mature software tools, runs full-stack multiuser Debian Linux, and has been widespread across the industry with manycore pro- is written in industry standard Verilog. -
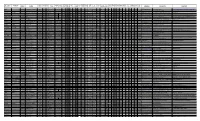
Up Cores T Est Folder Opencores Name Status Author Style / Clone
_uP_cores_t opencores style / data inst repor com LUTs blk F tool MIPS clks/ KIPS src # src tool fltg Ha max max byte # # pipe start last status author FPGA top file doc reference note worthy comments date LUT? est folder name clone size size ter ment ALUT mults ram max ver /clk inst /LUT code files chain pt vd data inst adrs inst reg len year revis cray1 alpha Christopher Fenton cray1 64 16 kintex-7-3 James Brakefield13463 6 19 10 127 ## 14.7 6.00 1.0 56.6 verilog 46 cray_sys_topyes yes Y N 4M 4M N 512 2010 CRAY data sheets homebrew Cray1 www.chrisfenton.com/homebrew-cray-1a/ fpgammix stable Tommy Thorn MMIX 64 32 arria-2 James Brakefield11605 A 8 10 94 ## q13.1 1.50 4.0 3.0 system verilog2 core yes yes Y Y 4G 4G Y 256 288 2006 2008 clone of Knuth's MMIX micro-coded s1_core S1 Core stable Fabrizio Fazzino etal SPARC 64 32 kintex-7-3 James Brakefield52845 6 8 59 56 ## v14.1 2.00 1.0 2.1 verilog 136 s1_top yes yes Y N 4G 4G Y 32 2007 2012 SPARC data sheets reduced version of OpenSPARC T1 Vivado run microblaze proprietaryXilinx uBlaze 32 32 kintex-7 Xilinx 546 6 1 320 1.03 1.0 603.7 not avail yes yes opt 4G 4G Y 86 32 3 2002 www.xilinx.com/tools/microblaze.htmMicroBlaze MCS, smallest configuration70 configuration options, MMU optional ARM_Cortex_A9 ASIC ARM ARM a9 32 16 arria V altera 4500 A 1050 2.50 1.0 583.3 asic yes yes Y 4G 4G Y 80 16 10 2012 altera data sheets uses pro-rated LC area dual issue, includes fltg-pt & MMU & caches nios2 proprietaryAltera Nios II 32 32 stratix-5 Altera 895 A 310 1.13 1.0 389.7 not avail yes yes opt 4G 4G -

Proceedings, the 57Th Annual Meeting, 1981
PROCEEDINGS THE FIFTY-SEVENTH ANNUAL MEETING National Association of Schools of Music NUMBER 70 APRIL 1982 NATIONAL ASSOCIATION OF SCHOOLS OF MUSIC PROCEEDINGS OF THE 57th ANNUAL MEETING Dallas, Texas I98I COPYRIGHT © 1982 ISSN 0190-6615 NATIONAL ASSOCIATION OF SCHOOLS OF MUSIC 11250 ROGER BACON DRIVE, NO. 5, RESTON, VA. 22090 All rights reserved including the right to reproduce this book or parts thereof in any form. CONTENTS Speeches Presented Music, Education, and Music Education Samuel Lipman 1 The Preparation of Professional Musicians—Articulation between Elementary/Secondary and Postsecondary Training: The Role of Competitions Robert Freeman 11 Issues in the Articulation between Elementary/Secondary and Postsecondary Training Kenneth Wendrich 19 Trends and Projections in Music Teacher Placement Charles Lutton 23 Mechanisms for Assisting Young Professionals to Organize Their Approach to the Job Market: What Techniques Should Be Imparted to Graduating Students? Brandon Mehrle 27 The Academy and the Marketplace: Cooperation or Conflict? Joseph W.Polisi 30 "Apples and Oranges:" Office Applications of the Micro Computer." Lowell M. Creitz 34 Microcomputers and Music Learning: The Development of the Illinois State University - Fine Arts Instruction Center, 1977-1981. David L. Shrader and David B. Williams 40 Reaganomics and Arts Legislation Donald Harris 48 Reaganomics and Art Education: Realities, Implications, and Strategies for Survival Frank Tirro 52 Creative Use of Institutional Resources: Summer Programs, Interim Programs, Preparatory Divisions, Radio and Television Programs, and Recordings Ray Robinson 56 Performance Competitions: Relationships to Professional Training and Career Entry Eileen T. Cline 63 Teaching Aesthetics of Music Through Performance Group Experiences David M.Smith 78 An Array of Course Topics for Music in General Education Robert R. -

Small Soft Core up Inventory ©2019 James Brakefield Opencore and Other Soft Core Processors Reverse-U16 A.T
tool pip _uP_all_soft opencores or style / data inst repor com LUTs blk F tool MIPS clks/ KIPS ven src #src fltg max max byte adr # start last secondary web status author FPGA top file chai e note worthy comments doc SOC date LUT? # inst # folder prmary link clone size size ter ents ALUT mults ram max ver /inst inst /LUT dor code files pt Hav'd dat inst adrs mod reg year revis link n len Small soft core uP Inventory ©2019 James Brakefield Opencore and other soft core processors reverse-u16 https://github.com/programmerby/ReVerSE-U16stable A.T. Z80 8 8 cylcone-4 James Brakefield11224 4 60 ## 14.7 0.33 4.0 X Y vhdl 29 zxpoly Y yes N N 64K 64K Y 2015 SOC project using T80, HDMI generatorretro Z80 based on T80 by Daniel Wallner copyblaze https://opencores.org/project,copyblazestable Abdallah ElIbrahimi picoBlaze 8 18 kintex-7-3 James Brakefieldmissing block622 ROM6 217 ## 14.7 0.33 2.0 57.5 IX vhdl 16 cp_copyblazeY asm N 256 2K Y 2011 2016 wishbone extras sap https://opencores.org/project,sapstable Ahmed Shahein accum 8 8 kintex-7-3 James Brakefieldno LUT RAM48 or block6 RAM 200 ## 14.7 0.10 4.0 104.2 X vhdl 15 mp_struct N 16 16 Y 5 2012 2017 https://shirishkoirala.blogspot.com/2017/01/sap-1simple-as-possible-1-computer.htmlSimple as Possible Computer from Malvinohttps://www.youtube.com/watch?v=prpyEFxZCMw & Brown "Digital computer electronics" blue https://opencores.org/project,bluestable Al Williams accum 16 16 spartan-3-5 James Brakefieldremoved clock1025 constraint4 63 ## 14.7 0.67 1.0 41.1 X verilog 16 topbox web N 4K 4K N 16 2 2009 -

Acceleration of Fingerprint Minutiae Extraction Using a VLIW Processor
Acceleration of Fingerprint Minutiae Extraction Using a VLIW Processor M.S.B. Purba, E. Yigit and A.J.J. Regeer Bachelor Thesis Bachelor of Electrical Engineering Acceleration of Fingerprint Minutiae Extraction Using a VLIW Processor Bachelor Thesis M.S.B. Purba, E. Yigit and A.J.J. Regeer August , Faculty of Electrical Engineering, Mathematics and Computer Science · Delft University of Technology Copyright c Faculty of Electrical Engineering, Mathematics and Computer Science All rights reserved. Preface This thesis has been written in the context of the Electrical Engineering bachelor exam at the Delft University of Technology. The project its title is: ‘Acceleration of Embedded Appli- cations Using a VLIW Processor’. The project was conducted at the Computer Engineering group of the department of Electrical Engineering, Mathematics and Computer Science. Chapter 1 gives the introduction of the project and specifies the exact problem. Chapter 2 presents some alternatives of applications using the ρ-VEX and explains why the fingerprint minutiae extraction application was chosen as vehicle to demonstrate the capabilities of the VEX implementation. In chapter 3 relevant theory is presented on embedded systems design, which is used in later chapters to explain our results. In chapter 4 the background of the chosen application is presented and the modified version of the software package is explained. In chapter 5 the setup of the experiment is described such as the FPGA-board, the VEX system, and the additional software tools that were written to extract the binary code for the VEX. In chapter 6 the results of the experiment are discussed, in particular the details of the partitioning of the application and the resulting system is described. -

GPL-3.0 in the Chinese Intellectual Property Court in Beijing 1
GPL-3.0 in the Chinese Intellectual Property Court in Beijing 1 GPL-3.0 in the Chinese Intellectual Property Court in Beijing Lucien C.H. Lin,a Navia Shen,b (a) Legal Adviser, Open Culture Foundation; (b) IP Counsel, Huawei Technologies Co., Ltd. DOI: 10.5033/ifosslr.v 10 i1 .126 Abstract With the increasing use of Free and Open Source Software (FOSS) in the world, the licensing issues and disputes regarding such licenses have been litigated in various jurisdictions. In the past, these lawsuits were concentrated in Europe and the United States, but less so in the Asia Pacific region. However, in 2018, the specialized Intellectual Property Right Court in Beijing, China, acting as a court of first instance, issued a decision in a software copyright infringement lawsuit related to FOSS. The defendant chose to invoke the copyleft mechanism in the GNU General Public License 3.0 (GPL-3.0) license as a defense against claims of copyright infringement. Although the court did not directly interpret the GPL license at this stage, the decision strongly implies that the GPL and the other FOSS licenses can be treated as valid in China. Even so, quite a number of details regarding the use of the GPL in China still require clarification, included as to how the license can substantially be enforced and implemented. Keywords Copyleft, GPL, derivative work, copyright infringement Although most of the academic opinions are positive,1 many commentators and practitioners did have doubts about whether a Free and Open Source Software license written in English could be enforced legally in China. -

An Evaluation of Soft Processors As a Reliable Computing Platform
Brigham Young University BYU ScholarsArchive Theses and Dissertations 2015-07-01 An Evaluation of Soft Processors as a Reliable Computing Platform Michael Robert Gardiner Brigham Young University - Provo Follow this and additional works at: https://scholarsarchive.byu.edu/etd Part of the Electrical and Computer Engineering Commons BYU ScholarsArchive Citation Gardiner, Michael Robert, "An Evaluation of Soft Processors as a Reliable Computing Platform" (2015). Theses and Dissertations. 5509. https://scholarsarchive.byu.edu/etd/5509 This Thesis is brought to you for free and open access by BYU ScholarsArchive. It has been accepted for inclusion in Theses and Dissertations by an authorized administrator of BYU ScholarsArchive. For more information, please contact [email protected], [email protected]. An Evaluation of Soft Processors as a Reliable Computing Platform Michael Robert Gardiner A thesis submitted to the faculty of Brigham Young University in partial fulfillment of the requirements for the degree of Master of Science Michael J. Wirthlin, Chair Brad L. Hutchings Brent E. Nelson Department of Electrical and Computer Engineering Brigham Young University July 2015 Copyright © 2015 Michael Robert Gardiner All Rights Reserved ABSTRACT An Evaluation of Soft Processors as a Reliable Computing Platform Michael Robert Gardiner Department of Electrical and Computer Engineering, BYU Master of Science This study evaluates the benefits and limitations of soft processors operating in a radiation-hardened FPGA, focusing primarily on the performance and reliability of these systems. FPGAs designs for four popular soft processors, the MicroBlaze, LEON3, Cortex- M0 DesignStart, and OpenRISC 1200 are developed for a Virtex-5 FPGA. The performance of these soft processor designs is then compared on ten widely-used benchmark programs. -

Inferable Object-Oriented Typed Assembly Language
Inferable Object-Oriented Typed Assembly Language Ross Tate Juan Chen Chris Hawblitzel University of California, San Diego Microsoft Research Microsoft Research [email protected] [email protected] [email protected] Abstract 1. Introduction A certifying compiler preserves type information through compi- Internet users regularly download and execute safe, untrusted code, lation to assembly language programs, producing typed assembly in the form of Java applets, JavaScript code, Flash scripts, and language (TAL) programs that can be verified for safety indepen- Silverlight programs. In the past, browsers have interpreted much dently so that the compiler does not need to be trusted. There of this code, but the desire for better performance has recently are two challenges for adopting certifying compilation in prac- made just-in-time compilation more common, even for scripting tice. First, requiring every compiler transformation and optimiza- languages. However, compilation poses a security risk: users must tion to preserve types is a large burden on compilers, especially trust the compiler, since a buggy compiler could translate safe when adopting certifying compilation into existing optimizing source code into unsafe assembly language code. Therefore, Nec- non-certifying compilers. Second, type annotations significantly ula and Lee [17] and Morrisett et al. [15] introduced proof-carrying increase the size of assembly language programs. code and typed assembly language (TAL). These technologies an- This paper proposes an alternative to traditional certifying com- notate assembly language with proofs or types that demonstrate the pilers. It presents iTalX, the first inferable TAL type system that safety of the assembly language, so that the user trusts a small proof supports existential types, arrays, interfaces, and stacks. -

Diseño De Un Microcontrolador De 32 Bits Con Base En Un FPGA
UNIVERSIDAD NACIONAL AUTÓNOMA DE MÉXICO FACULTAD DE INGENIERÍA Diseño de un microcontrolador de 32 bits con base en un FPGA TESIS Que para obtener el título de Ingeniero Eléctrico - Electrónico P R E S E N T A Manuel Pérez Aguilar DIRECTOR DE TESIS M.I. Juan Carlos Roa Beiza Ciudad Universitaria, Cd. Mx., 2017 “La cosa más hermosa que podemos experimentar es el misterio. Es la fuente de toda arte y toda ciencia.” - EINSTEIN, Albert i Agradecimientos: Agradezco a la U.N.A.M que me recibió como estudiante y el haberme formado en sus aulas desde preparatoria, a la Facultad de Ingeniería por la preparación que me ha permitido enfrentarme a los retos de la vida profesional, a cada uno de los profesores que me dedicó tiempo, y compartió conmigo no solo información sino formación para la vida, a mi Director de Tesis el M.I. Juan Carlos Roa Beiza por ser tan generoso en compartir su conocimiento y guiarme durante el presente trabajo de Tesis, al Programa de Apoyo a la Titulación (PAT) y al Programa de Vinculación con Egresados (PVE) por brindarme esta oportunidad para culminar una de mis metas, a mis amigos que han hecho de mi etapa universitaria un trayecto de vivencias que nunca olvidaré. Son muchas las personas que han formado parte de mi vida profesional a las que me gustaría agradecerles su amistad, apoyo, ánimo, consejos y compañía durante esta etapa de mi vida, que sin importar en donde se encuentren, quiero darles las gracias por formar parte de mí y por todo lo que me han brindado. -

2014 UPTOWN ARTS STROLL PASEO DE LAS ARTES May 29–June 30 | Guide/Guía Celebrating the Arts in Washington Heights and Inwood Honoring: Annette A
Poster Design: Felipe Galindo 2014 UPTOWN ARTS STROLL PASEO DE LAS ARTES May 29–June 30 | Guide/Guía Celebrating the arts in Washington Heights and Inwood Honoring: Annette A. Aguilar, René De Los Santos, Sky Pape and Janifer Wilson Northern Manhattan Arts Alliance 178 Bennett Avenue, Third Floor - New York, NY 10040 www.artstroll.com | www.nomaanyc.org @NoMAArts | Northern Manhattan Arts Alliance 02 2014 UPTOWN ARTS STROLL KICK-OFF THURSDAY, MAY 29 THE 2014 UPTOWN ARTS STROLL IS FINALLY HERE! ¡LLEGO EL PASEO DE LAS ARTES 2014! Welcome! Northern Manhattan will be, once again, the ¡Bienvenido! La apertura del Paseo se llevara a cabo en center of everything arts related during the month of June. el Parque Highbridge en la Avenida Amsterdam y calle Included among the many activities happening during the 172, en Washington Heights. Este parque histórico fue 2014 Uptown Arts Stroll are art exhibitions, outdoor theatre, bautizado con el nombre “Puente Alto” , en honor al puente dance, music, open studios and much more! The Stroll más antiguo de la ciudad de Nueva York, conocido por la kick- off celebration will be held on Thursday, May 29th from torre Highbridge y sus hermosas vistas del Rio Harlem, 6:00pm-8:30pm at Highbridge Park, Amsterdam Avenue el Puente Washington, los puentes Alexander Hamilton y & West 172nd Street. Landmarked and named after the University Heights, Manhattan y el Bronx. El Highbridge o High Bridge, the city’s oldest standing bridge, Highbridge “Puente Alto” que conecta a Washington Heights con el Park is widely known for its landmarked Highbridge Tower Bronx reabrirá en diciembre del 2014.