Battery-Sensing Intrusion Protection System (B-SIPS)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Official Minutes Cattaraugus-Allegany-Erie-Wyoming BOCES Regular Meeting
Official Minutes Cattaraugus-Allegany-Erie-Wyoming BOCES Regular Meeting DATE: December 9, 2015 TIME: 4:30 PM PLACE: Center at Olean BOARD MEMBERS PRESENT: Lou Nicol, President Brad Sande, Vice President Candace Clemens Michael Conroy Gilbert Green Charles Joyce Robert Keenan Susan Potter BOARD MEMBERS ABSENT: Maxine Dowler STAFF PRESENT: Lynda Quick, District Superintendent Sally Nenno, District Clerk Tim Cox, Assistant Superintendent for ISS Carol Fial, Assistant Superintendent for Special Education Tracie Preston, Assistant Superintendent for CTE Thomas Potter, Controller Mike Graf, Director for Technology Pam Kirkwood, Director for Personnel & Labor Relations Karen Coleman, Treasurer Kathleen Brisky, Principal Steve Dieteman, Principal Noel Sheehy, Principal Dean McKnight, Manager Facility Services Tim Clarke, Program Manager Jen Spong, Program Manager Mary Morris, Program Manager President L. Nicol called the meeting to order at 4:41 p.m. with the Pledge of Allegiance. Welding & Metal Fabrications teachers were introduced and introduced their students Presentations present. Students told of their experiences in the program, projects and areas studied. 4:49 B. Sande arrived T. Preston passed out a report with an overview of CTE enrollment history and reviewed it with the Board. Carol Fial reported on the special opportunity that some of our students got to Citizen’s Input experience last week. They went to the Bills stadium and watched the Bills practice, received t-shirts, had lunch with the Bills and were given $125 to spend in the Bills gift shop. They then went to 716, received another $125 to spend in the Sabres gift shop, watched a Sabres game, went on the ice and then into the locker room after the game. -

A World of Batteries the CONFIGURATOR - the EASY WAY to FIND YOUR PARTS
A world of batteries THE CONFIGURATOR - THE EASY WAY TO FIND YOUR PARTS In our configurator you will find upgrade products to servers, desktops, notebooks, printers, digital cameras etc. The configurator contains more than 3000 different models and systems from manufacturers, among others: IBM, HP, Dell, Toshiba, Fujitsu-Siemens etc. By using the configurator you will be certain that the products you buy will be compatible with your established system. Please be aware that when buying memory or hard disc drives, you will need to have your established system updated to the latest BIOS version of your model. How to use the configurator on your local EET Nordic website: With the configurator you can find products in two ways: Model-tree: Make a choice from the or Searchbox: Search for your model in by scrollbar at each level. The levels are: using the search box where you enter the 1 Producer • Serie • Model 2 your model specifications. After using either the model-tree or the searchbox you can see all the parts that match your search including the specifications, real time stock and price. With MicroBattery you get: • All batteries are 100% compatible • All batteries meet or exceeds the original manufacturers specification • MicroBattery are made with the latest technology using the most up to date cells • MicroBattery provides 1 year warranty • MicroBattery are also able to support old and end of life notebooks • MicroBattery support brands from A-Z (Acer to Zenith) www.eetnordic.com INDEX NOTEBOOK Page ACER ............................................................................................................................ -

Proposal for the Region 14 Education Service Center Acting on Behalf of the National Cooperative Purchasing Alliance
Proposal for the Region 14 Education Service Center acting on behalf of the National Cooperative Purchasing Alliance RFP No. 11-15, Technology Solutions Proposal Due Date: Thursday, September 10, 2015 at 2:00 PM One Dell Way Round Rock TX 78682, USA www.dell.com September 8, 2015 Region 14 Education Service Center 1850 Highway 351 Abilene Texas 79601 Dear Region 14 ESC: Thank you for this opportunity to submit a proposal for Region 14 Education Service Center’s forthcoming technology project. We have studied the information provided to us about your business requirements and carefully analyzed your technology needs. The solution recommended for Region 14 ESC has been designed to meet your needs in the most cost effective way without compromising on quality, service or ongoing support. Dell is helping our customers to bring down the Total Cost of Ownership by simplifying IT. We are committed to providing solutions that will allow Region 14 ESC to reclaim time and cost and increase the productivity of your IT. In addition, we have built environmental consideration into every stage of the Dell product lifecycle including power consumption, helping our customers demonstrate environmentally responsible procurement. Along with award winning products and services, Dell also offers you a dedicated program account team that is committed to working with you and your procurement needs. This team includes: ● An Account Manager to ensure overall account satisfaction ● System Consultants to provide a seamless deployment experience ● Technical Sales Representatives to facilitate order management ● Customer Service Representatives to provide post-sale support Dell looks forward to working with you on this project. -

790€Ht 8 575€Ht
POWEREDGe™ R710 E MC VNXe 3100 IDEAL Serveur rack multifonction Le nouveau stockage unifié UR haute capacité simple, efficace et économique PO PME Une plate-forme de stockage unifié économique pour les petites entreprises. La gamme VNXe vous offre un stockage prêt à l’emploi et HT automatisé grâce à des logiciels conçus pour simplifier la gestion, le € Voir page 6 8 575 provisionnement et la protection. PROSAFE GSM7212P Switch Gigabit manageable L2+ avec PoE+ sur tous les ports pour vos projets de vidéo IP et ToIP ! CHOISISSEZ LA CONFIGURATION ADAPTÉE À VOS BESOINS HT 790€ HT Réf. 2593019 Voir page 23 à partir de 9 960€ Voir page 10 Je ne suis pas un serveur. Je suis votre sauveur. Je suis la solution que vous attendiez Serveur de stockage WD Sentinel™ DX4000 | pour PME Admirez mon design compact qui s’intègre à tout environnement. Appréciez mon installation plug-and-play, ma facilité d’administration et mon accès à distance intégré. Découvrez la solution complète que je propose pour protéger vos données. Elle comprend les modes RAID 1 et 5 et à une sauvegarde automatique centralisée et délocalisable. Il ne vous reste qu’à prendre les rênes. Western Digital, WD, et le logo WD sont des marques déposées aux États-Unis et dans d’autres pays. WD Sentinel est une marque commerciale de Western Digital Technologies, Inc. Les autres marques citées sont la propriété de leurs détenteurs respectifs. Les spécifications de produit sont sujettes à modification sans préavis. Le produit réel peut être différent de l’illustration. © 2011 Western Digital Technologies, Inc. -

Multimodal Interaction with Mobile Devices: Fusing a Broad Spectrum of Modality Combinations
Multimodal Interaction with Mobile Devices: Fusing a Broad Spectrum of Modality Combinations Dissertation zur Erlangung des Grades Doktor der Ingenieurwissenschaften (Dr.-Ing.) der Naturwissenschaftlich-Technischen Fakultat¨ I der Universitat¨ des Saarlandes vorgelegt von Rainer Wasinger Saarbrucken¨ 20. November 2006 ii Datum des Kolloquiums: Montag den 20. November 2006 Dekan und Vorsitzender: Prof. Dr. Thorsten Herfet Gutachter: 1. Prof. Dr. Dr. h.c. mult. Wolfgang Wahlster 2. Prof. Dr. Elisabeth Andre´ Akademischer Beisitzer: Dr. Dominik Heckmann Eidesstattliche Erklarung¨ Hiermit erklare¨ ich, dass ich die vorliegende Arbeit ohne unzulassige¨ Hilfe Dritter und ohne Be- nutzung anderer als der angegebenen Hilfsmittel angefertigt habe. Die aus anderen Quellen oder indirekt ubernommenen¨ Daten und Konzepte sind unter Angabe der Quelle gekennzeichnet. Diese Arbeit wurde bisher weder im In- noch im Ausland in gleicher oder ahnlicher¨ Form in anderen Prufungsverfahren¨ vorgelegt. Saarbrucken,¨ den 20. November 2006 iii iv Acknowledgements Most of all, I would like to thank Professor Wahlster for providing the funds, the time, and the environment, for any and all of this to have been possible. I also thank you for permitting me to work on such an interesting topic at the DFKI. I value your advice, which is always relevant, and your ability to see the interesting aspect of practically any research field. I also thank Elisabeth Andre´ for being the second corrector of this work, and the German Federal Ministry for Education and Research (BMBF), which has funded this work under the contract number 01 IN C02 as part of the projects COLLATE and COLLATE II. I would like to dearly thank my wife Emma and my son Xavier for making everything wor- thwhile. -
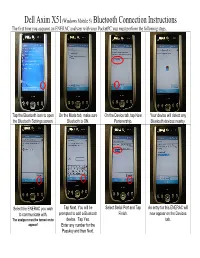
Dell Axim X51(Windows Mobile 5) Bluetooth Connection Instructions
Dell Axim X51(Windows Mobile 5) Bluetooth Connection Instructions The first time you acquaint an ENERAC analyzer with your PocketPC you must perform the following steps: Tap the Bluetooth icon to open On the Mode tab, make sure On the Device tab, tap New Your device will detect any the Bluetooth Settings screen. Bluetooth is ON. Partenership. Bluetooth devices nearby. Select the ENERAC you wish Tap Next. You will be Select Serial Port and Tap An entry for this ENERAC will to communicate with. prompted to add a Bluetooth Finish. now appear on the Devices The analyzer must be turned on to device. Tap Yes. tab. appear! Enter any number for the Passkey and then Next. On the COM Ports tab, Select Select the ENERAC you wish Unselect Secure Connection. The Bluetooth Commport is New Outgoing Port. to connect with. Port must be COM7. now mapped to this particular If you want to switch to another ENERAC, Tap Finish. Bluetooth ENERAC. you must first delete any COM7 connection that appears here (Tap-and-Hold). To Run Enercom Enercom will now connect to EnercomCE continues to run If Enercom stops responding, Tap Start, Programs, your ENERAC analyzer. on your PocketPC even after you can kill it by selecting, EnercomCE. you dismiss the program. Start, Settings, System tab, Memory, Running Programs When the Bluetooth connection tab, Enercom, Stop, OK. has been severed, due to: 1) Your PDA has powered Resetting the PDA is also an down, or effiective means of starting 2) Your ENERAC has fresh. Use the stylus to press been powered down, or the reset switch, located on the 3) You have gone back side. -

Acclaimed Security Researcher and Author of Nmap. • Ira Winkler - Author of "Spies Among Us"
With 2006 just starting off many are happy to have left a myriad of security problems behind in 2005. I hope you see more security awareness and experience a cleaner network environment this year. This issue brings more technical articles and reflections on the past year. Many of you e-mailed us asking us to review software titles and hardware, so you’ll be glad to know that we have a review in this issue. Keep those comments coming and thanks for the support! Mirko Zorz Chief Editor Visit the magazine website at www.insecuremag.com (IN)SECURE Magazine contacts Feedback and contributions: Mirko Zorz, Chief Editor - [email protected] Marketing: Berislav Kucan, Director of Marketing - [email protected] Distribution (IN)SECURE Magazine can be freely distributed in the form of the original, non modified PDF document. Distribution of substantively modified versions of (IN)SECURE Magazine content is prohibited without the explicit permission from the editor. For reprinting information please send an email to [email protected] or send a fax to 1-866-420-2598. Copyright HNS Consulting Ltd. 2006. www.insecuremag.com The popularity of web application firewalls is on the rise. These tools used to be reserved for a very small percentage of high profile deployments, but, with the number of less costly products appearing on the market and an open source option available for anyone to try out (ModSecurity - modsecurity.org), they are finally available to the majority. In this article I will describe what web application time I thought it was a beautiful idea. Other people firewalls do and give you a quick overview of their must have liked the idea too because by mid 2005 most useful features. -
Dell Axim Software Sync
Dell axim software sync Standard Microsoft USB driver for ActiveSync with Dell Axim X5 PID/VID included. By downloading, you accept the terms of the Dell Software License. You can download the Active Sync software by clicking below. me to the correct place to purchase the installation cd for a Dell Axim X30?Dell Axim x51 with MS Win Mobil - Windows 8. Download the latest drivers for your Dell Axim USB Sync to keep your Computer All drivers available for download have been scanned by antivirus program. Just installed windows professional and now can not connect with active sync. It will not recognize the usb connection. The computer has a. I have a Dell AXIM X51v PDA running Microsoft Active Sync. I want to run this with Windows 7 64bit Home Premium within Windows Mobile DELL AXIM X51V PDA WINDOWS 10 COMPATABILLITY. It's worth noting that Remote PC Sync (via Wi-Fi or LAN) has been . sync with my Dell Axim X50v. This final version does the exact same thing. I just got a Dell Axim X30 and want to sync it to my PB. I also have some programs saved on my PBs hard drive for the Pocket PC that I'd like to. does anyone know of where i can get a program that will allow my axim to sync with my mac mini for free or at a low price? the axim has. This Charge- Sync cable for Dell Axim X50/X51/X50u/X50v/X51v series Pocket PC is an all-in-one cabling solution that allows synchronization of data and. -
Fictionwise/Ereader - List of Unmatched Titles
Fictionwise/eReader - List of Unmatched Titles Title Author Publisher 'Twas the Night Before Christmas [From the New Adventures of Sherlock Holmes] Dennis Green Boondock Books 'Twixt Land and Sea Joseph Conrad EbooksLib 'Twixt Land and Sea Tales Joseph Conrad PDM Classics ...And Dreams Are Dreams: A Novel in Seven Parts Vassilis Vassilikos Random House, Inc. ...And Dreams Are Dreams: A Novel in Seven Parts Vassilis Vassilikos Random House, Inc. ...To End All War [The Survivalist #21] Jerry Ahern Jerry Ahern ...Was Yesterday Robert E. Brisbin CyberRead 1...2...3...Count With Me Leta Nolan Childers DiskUs Publishing 10 Insider Secrets Career Transition Workshop: Your Complete Guide to Discovering the Ideal Job Todd Bermont 10 Step Corporation 10 Insider Secrets To Job Hunting Success: Everything You Need To Get The Job You Want In 24 Hours--Or Less! Todd L. Bermont Publishing Dimensions 10 Reasons to Abolish the IMF & World Bank Kevin Danaher Random House, Inc. 10 Reasons to Abolish the IMF and the World Bank Kevin Danaher Random House, Inc. 10 Secrets to Successful Home Buying and Selling Lois A. Vitt Financial Times Prentice Hall 10 Steps To Success In Direct Sales Bussiness Reports CyberRead 10,000 Dreams Interpreted Gustavus Miller World Digital Library 10-Minute Talks Jonathan Mckee Harper Collins, Inc. 100 Bullshit Jobs ... And How to Get Them Stanley Bing Harper Collins, Inc. 100 Days in the Secret Place Gene Edwards Treasures Media Inc 100 Haiku Francis Gallagher Iumix Limited 100 Rants on Why Men Are Pants Amy Charter Summersdale Publishers Ltd 100 Super Supplements for a Longer Life Frank Murray McGraw-Hill Companies 100 Thematic Word Search Puzzles John F. -

Axim X51v Software
Axim x51v software click here to download Axim X51v system update utility with A04 English ROM image for By downloading, you accept the terms of the Dell Software License. Axim X51v system update utility with A12 English ROM image for Windows By downloading, you accept the terms of the Dell Software License Agreement. AmAze is a first of its kind free navigation and local search service. It is free to download and use and it contains wide coverage of maps including aerial photo in. Hello All, I am need of installation software/drivers for my Axim X51 as the CD is damaged. I am running Vista Home Premium, bit. How to Update Dell AXIM X51 to WM Dell Axim X51v Windows Mobile L16 build Dell has posted on its support web site a pair of ROM updates for the Axim X51 and X51v. The first will update both X51 models with a QVGA. This list will include all the software that has been verified by other users to work on the Dell Axim X51v. For those not aware, the X51v is running the latest. The purchasable upgrades I have seen for WM6 have been for the axim x50 and NOT x51v for some strange reason. The x51v is a better and [Q] possible to downgrade dell axim x51v fro. Just installed windows professional and now can not connect with active sync. It will not recognize the usb connection. The computer has a. I want to know what software you would install on them. Maybe a good for years I own an Axim X51v and would like to give it a second life. -

Dell™ Axim™ X51/X51v Manuel De L'utilisateur
Dell™ Axim™ X51/X51v Manuel de l'utilisateur www.dell.com | support.dell.com Remarques, avis et précautions REMARQUE : Une REMARQUE indique des informations importantes qui peuvent vous aider à mieux utiliser votre ordinateur. AVIS : Un AVIS vous avertit d’un risque de dommage matériel ou de perte de données et vous indique comment éviter le problème. PRÉCAUTION : Une PRÉCAUTION indique un risque potentiel d'endommagement du matériel, de blessure corporelle ou de mort. Abréviations et sigles Pour une liste complète des abréviations et des sigles, reportez- vous à la section « Glossaire » à la page 135. ____________________ Les informations contenues dans ce document sont sujettes à modification sans préavis. © 2006 Dell Inc. Tous droits réservés. La reproduction de ce document, de quelque manière que ce soit, sans l'autorisation écrite de Dell Inc. est strictement interdite. Marques utilisées dans ce document : Dell, le logo DELL, Axim, TrueMobile, Dimension, Inspiron, OptiPlex, Latitude, Dell Precision, PowerApp, PowerVault, PowerEdge, PowerConnect et DellNet sont des marques de Dell Inc. ; Intel, Pentium et Celeron sont des marques déposées et XScale et StrataFlash sont des marques d'Intel Corporation ; Microsoft, Windows, Windows Media et ActiveSync sont des marques déposées et Windows Mobile est une marque de Microsoft Corporation ; Bluetooth est une marque déposée de Bluetooth SIG, Inc. et est utilisée par Dell Inc. sous licence. D'autres marques et noms commerciaux peuvent être utilisés dans ce document pour faire référence aux entités se réclamant de ces marques et de ces noms ou à leurs produits. Dell Inc. rejette tout intérêt propriétaire dans les marques et les noms commerciaux autres que les siens. -

Dell Axim X51 and X51v Handhelds
Dell Axim™ X51 and X51v handhelds Dell Axim X51 and X51v handhelds The most recent additions to The powerful Dell Axim X51v (624MHz) features a large 3.7" VGA display that provides brilliant, clear images at 640x480 resolution. The large viewing area makes documents easy to see so you can work efficiently and quickly. It also gives you an excellent entertainment experience. The integrated Intel® the exciting Dell Axim family, 2700G graphics accelerator enables DVD-quality playback for video ranging from cartoons to full-length movies. Play intense 3D games like Tony the new X51 and X51v Hawk Pro Skater 2, access the Web or enjoy your favourite music, movies and TV programmes.7 The X51v delivers crisp, vivid images for an incredible viewing experience on the go. handhelds deliver the The Dell Axim X51 features a bright 3.5" QVGA display with a 320x240 resolution, and includes the power and storage capacity to handle work and performance and multimedia applications. expandability to stay Both handheld models have a sleek and stylish design with CF and SDIO expansion slots for additional memory, scanners, GPS systems, network cards and modems. productive, connected and Productive – stay productive while you are away from your desk entertained. These handhelds The Axim X51 and X51v are powered by Intel PXA270 processors, providing technology to help deliver great multimedia performance along with ® provide the level of Microsoft Windows Mobile™ 5.0 software for Pocket PCs running familiar applications in the new Office Mobile suite including Word Mobile, Excel Mobile and the latest PowerPoint Mobile, allowing you to stay productive while you are away from your home or office.