TCM Report, Summer
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

1 Oral History Interview with Brian Randell January 7, 2021 Via Zoom
Oral History Interview with Brian Randell January 7, 2021 Via Zoom Conducted by William Aspray Charles Babbage Institute 1 Abstract Brian Randell tells about his upbringing and his work at English Electric, IBM, and Newcastle University. The primary topic of the interview is his work in the history of computing. He discusses his discovery of the Irish computer pioneer Percy Ludgate, the preparation of his edited volume The Origins of Digital Computers, various lectures he has given on the history of computing, his PhD supervision of Martin Campbell-Kelly, the Computer History Museum, his contribution to the second edition of A Computer Perspective, and his involvement in making public the World War 2 Bletchley Park Colossus code- breaking machines, among other topics. This interview is part of a series of interviews on the early history of the history of computing. Keywords: English Electric, IBM, Newcastle University, Bletchley Park, Martin Campbell-Kelly, Computer History Museum, Jim Horning, Gwen Bell, Gordon Bell, Enigma machine, Curta (calculating device), Charles and Ray Eames, I. Bernard Cohen, Charles Babbage, Percy Ludgate. 2 Aspray: This is an interview on the 7th of January 2021 with Brian Randell. The interviewer is William Aspray. We’re doing this interview via Zoom. Brian, could you briefly talk about when and where you were born, a little bit about your growing up and your interests during that time, all the way through your formal education? Randell: Ok. I was born in 1936 in Cardiff, Wales. Went to school, high school, there. In retrospect, one of the things I missed out then was learning or being taught Welsh. -

Early Stored Program Computers
Stored Program Computers Thomas J. Bergin Computing History Museum American University 7/9/2012 1 Early Thoughts about Stored Programming • January 1944 Moore School team thinks of better ways to do things; leverages delay line memories from War research • September 1944 John von Neumann visits project – Goldstine’s meeting at Aberdeen Train Station • October 1944 Army extends the ENIAC contract research on EDVAC stored-program concept • Spring 1945 ENIAC working well • June 1945 First Draft of a Report on the EDVAC 7/9/2012 2 First Draft Report (June 1945) • John von Neumann prepares (?) a report on the EDVAC which identifies how the machine could be programmed (unfinished very rough draft) – academic: publish for the good of science – engineers: patents, patents, patents • von Neumann never repudiates the myth that he wrote it; most members of the ENIAC team contribute ideas; Goldstine note about “bashing” summer7/9/2012 letters together 3 • 1.0 Definitions – The considerations which follow deal with the structure of a very high speed automatic digital computing system, and in particular with its logical control…. – The instructions which govern this operation must be given to the device in absolutely exhaustive detail. They include all numerical information which is required to solve the problem…. – Once these instructions are given to the device, it must be be able to carry them out completely and without any need for further intelligent human intervention…. • 2.0 Main Subdivision of the System – First: since the device is a computor, it will have to perform the elementary operations of arithmetics…. – Second: the logical control of the device is the proper sequencing of its operations (by…a control organ. -

Technical Details of the Elliott 152 and 153
Appendix 1 Technical Details of the Elliott 152 and 153 Introduction The Elliott 152 computer was part of the Admiralty’s MRS5 (medium range system 5) naval gunnery project, described in Chap. 2. The Elliott 153 computer, also known as the D/F (direction-finding) computer, was built for GCHQ and the Admiralty as described in Chap. 3. The information in this appendix is intended to supplement the overall descriptions of the machines as given in Chaps. 2 and 3. A1.1 The Elliott 152 Work on the MRS5 contract at Borehamwood began in October 1946 and was essen- tially finished in 1950. Novel target-tracking radar was at the heart of the project, the radar being synchronized to the computer’s clock. In his enthusiasm for perfecting the radar technology, John Coales seems to have spent little time on what we would now call an overall systems design. When Harry Carpenter joined the staff of the Computing Division at Borehamwood on 1 January 1949, he recalls that nobody had yet defined the way in which the control program, running on the 152 computer, would interface with guns and radar. Furthermore, nobody yet appeared to be working on the computational algorithms necessary for three-dimensional trajectory predic- tion. As for the guns that the MRS5 system was intended to control, not even the basic ballistics parameters seemed to be known with any accuracy at Borehamwood [1, 2]. A1.1.1 Communication and Data-Rate The physical separation, between radar in the Borehamwood car park and digital computer in the laboratory, necessitated an interconnecting cable of about 150 m in length. -

The Advent of Recursion & Logic in Computer Science
The Advent of Recursion & Logic in Computer Science MSc Thesis (Afstudeerscriptie) written by Karel Van Oudheusden –alias Edgar G. Daylight (born October 21st, 1977 in Antwerpen, Belgium) under the supervision of Dr Gerard Alberts, and submitted to the Board of Examiners in partial fulfillment of the requirements for the degree of MSc in Logic at the Universiteit van Amsterdam. Date of the public defense: Members of the Thesis Committee: November 17, 2009 Dr Gerard Alberts Prof Dr Krzysztof Apt Prof Dr Dick de Jongh Prof Dr Benedikt Löwe Dr Elizabeth de Mol Dr Leen Torenvliet 1 “We are reaching the stage of development where each new gener- ation of participants is unaware both of their overall technological ancestry and the history of the development of their speciality, and have no past to build upon.” J.A.N. Lee in 1996 [73, p.54] “To many of our colleagues, history is only the study of an irrele- vant past, with no redeeming modern value –a subject without useful scholarship.” J.A.N. Lee [73, p.55] “[E]ven when we can't know the answers, it is important to see the questions. They too form part of our understanding. If you cannot answer them now, you can alert future historians to them.” M.S. Mahoney [76, p.832] “Only do what only you can do.” E.W. Dijkstra [103, p.9] 2 Abstract The history of computer science can be viewed from a number of disciplinary perspectives, ranging from electrical engineering to linguistics. As stressed by the historian Michael Mahoney, different `communities of computing' had their own views towards what could be accomplished with a programmable comput- ing machine. -

Next Generation Tool
INSIDE! COMPUTING TRENDS: WHAT ARE TODAY'S CIO'S LOOKING FOR? $7.00 U.S. INTERNATIONAL ® SPECTRUMSPECTRUMTHE BUSINESS COMPUTER MAGAZINE SEPT/OCT 2002 • AN IDBMA, INC. PUBLICATION NextNext GenerationGeneration ToolTool XXCreateCreate OneOne CodeCode BaseBase forfor AnyAny NetworkNetwork Configuration,Configuration, AnyAny OperatingOperatingTT System,System, andand AnyAny DataData SourceSource —— MultiValueMultiValue andand RelationalRelational —— WithoutWithoutTT BeingBeing aa JavaJava Expert!Expert! Come in from the rain Featuring the UniVision MultiValue database - compatible with existing applications running on Pick AP, D3, R83, General Automation, Mentor, mvBase and Ultimate. We’re off to see the WebWizard Starring a “host” centric web integration solution. Watch WebWizard create sophisticated web-based applications from your existing computing environment. Why a duck? Featuring ViaDuct 2000, the world’s easiest-to-use terminal emulation and connectivity software, designed to integrate your host data and applications with your Windows desktop. Caught in the middle? With an all-star cast from the WinLink32 product family (ViaOD- BC, ViaAPI for Visual Basic, ViaObjects, and mvControls), Via Sys- tems’ middleware solutions will entertain (and enrich!) you. Appearing soon on a screen near you. Advanced previews available from Via Systems. Via Systems Inc. 660 Southpointe Court, Suite 300 Colorado Springs, Colorado 80906 Phone: 888 TEAMVIA Fax: 719-576-7246 e-mail: [email protected] On the web: www.via.com The Freedom To Soar. With jBASE – the remarkably liberating multidimensional database – there are no limits to where you can go. Your world class applications can now run on your choice of database: jBASE, Oracle, SQL Server or DB2 without modification and can easily share data with other applications using those databases. -

LABORATORY for COMPUTER SCIENCE'progress REPORT Ig JULY 1/3 1986-JUNE 1981(U) MASSACHUSETTS INST of TECH CAMBRIDGE LAB for COMPUTER SCIENCE
-R127 586 LABORATORY FOR COMPUTER SCIENCE'PROGRESS REPORT ig JULY 1/3 1986-JUNE 1981(U) MASSACHUSETTS INST OF TECH CAMBRIDGE LAB FOR COMPUTER SCIENCE. M L DERTOUZOS 01 APR 82 UNCLASSIFIEDEhE0 LCS-PR-i8 00 N9014-75-C-8661 0 0 0 1iEF/G 9/2 N EhhhhhhhhhhhhE EhhhhhhhhhhhhE EhhhhhhhmhhhhE EhhhhhhhhhhhhI EhhhhhhohmhhhE ".2 111.0 t IL8125 IL .2 j'Ill-'liii 111.25 111. ~lI MICROCOPY RESOLUTION TEST CHART NATIONAL BUREAU OF SIANDARDS-1963-A a-, MASSACHUSETTS LABORATORY FOR INSTITUTE OF COMPUTER SCIENCE TECHNOLOGY PROGRESS REPORT 18 July 1980- June 1981 1i MAY 2 1.83 CL- Prepared for the Defense Advanced Research Projects Agency 545 TECHNOLOGY SQUARE. CAMBRIDGE, MASSACHUSETTS 02139 83 04 29 018 ,' -.^. %. '" * ' 4. .-,. -i .- - k 7 . - . -. _. - .. .. .. - • . ... ..• . Unclassified "ECUtITY CLASSIFICATION OF THIS PAGE (When Data Entered) REPOT DCUMETATONPGE READ INSTRUCTIONS REPEN RTATIN OCU P GEBEFORE COMPLETING FORM 1. REPORT NUMBER 2. G 3. RECIPIENT'S CATALOG NUMBER LCS Progress Report 18 8'k, 4. TITLE (and Subtitle) S. TYPE OF REPORT & PERIOD COVERED Laboratory for Computer Science DARPA/DOD, Progress Progress Report 18 Report 7/80 - 6/81 . July 1980 - June 1981 6. PERFORMING ORG. REPORT NUMBER LCS-PR 18 7. AUTHOR(s) 8. CONTRACT OR GRANT NUMBER(*) *Laboratory for Computer Science - Michael L. Dertouzos N00014-75-0661 9. PERFORMING ORGANIZATION NAME AND ADDRESS 10. PROGRAM ELEMENT. PROJECT, TASK - Laboratory for Computer Science AREA & WORK UNIT NUMBERS Massachusetts Institute of Technology .. 545 Tech. Sq. Cambridge, MA 02139 1i. CONTROLLING OFFICE NAME AND ADDRESS 12. REPORT DATE -Defense Advanced Research Projects Agency April 1, 1983 * Information Processing Techniques Office 13. -

The Evolution of Lisp
1 The Evolution of Lisp Guy L. Steele Jr. Richard P. Gabriel Thinking Machines Corporation Lucid, Inc. 245 First Street 707 Laurel Street Cambridge, Massachusetts 02142 Menlo Park, California 94025 Phone: (617) 234-2860 Phone: (415) 329-8400 FAX: (617) 243-4444 FAX: (415) 329-8480 E-mail: [email protected] E-mail: [email protected] Abstract Lisp is the world’s greatest programming language—or so its proponents think. The structure of Lisp makes it easy to extend the language or even to implement entirely new dialects without starting from scratch. Overall, the evolution of Lisp has been guided more by institutional rivalry, one-upsmanship, and the glee born of technical cleverness that is characteristic of the “hacker culture” than by sober assessments of technical requirements. Nevertheless this process has eventually produced both an industrial- strength programming language, messy but powerful, and a technically pure dialect, small but powerful, that is suitable for use by programming-language theoreticians. We pick up where McCarthy’s paper in the first HOPL conference left off. We trace the development chronologically from the era of the PDP-6, through the heyday of Interlisp and MacLisp, past the ascension and decline of special purpose Lisp machines, to the present era of standardization activities. We then examine the technical evolution of a few representative language features, including both some notable successes and some notable failures, that illuminate design issues that distinguish Lisp from other programming languages. We also discuss the use of Lisp as a laboratory for designing other programming languages. We conclude with some reflections on the forces that have driven the evolution of Lisp. -

Engineering Strategy Overview Preliminary
March 1982 Engineering Preliminary Strategy Company Overview Confidential If.-t8···· L..4L ~ \:')' j.~.! / .;.' ' 1985 1990 1995 2000 - P,O S SIB L E DEC PRO Due T S - $lJOO cellular radio net discontinouous.100 word ~ lim! ted context HANDHELD speaker independent speaker independent $1.0K speech recogn. • sketchpad , interpretation Glata structures , ' & relat~onsh~ps object filing natural languaqe (invisible, protected structures) $40K I CAB I NET I ,4 (dedicated fixture) ~~~n limited context [:~~~~e~ ~~~:~~i:ti~n ~ ak rind pendent • voice ~tuate~ retrieval spe ~ e _ .. • te1econferenc1ng center cont1nued speechlrecogn~tion " ;., encryption associa tiveJparallel a;;;'e'los (, ..j." .---~ provide CAtt= ASSISTANT -------...--- .. • LIBRARlj\N ~ ?ertified "best match" retrieval ~ (secure) os (holographic? ) $650K BD 1/15/81 PRELIMINARY ENGINEERING STRATEGY OVERVIEW MARCH lYtil SECONIJ IJRAFT PRELIMINARY ENGINEERING STRATEGY OVERVIEW TABLE OF CONTENTS ,Preface Chapter I fhe Product Strategy and Transitioning to the Fifth Generation - Product Strategy Overview - The Transitions - Personal Computer Clusters, PCC, Are An Alternative to Timeshared Computers - The Product Strategy - Fifth and Sixth Computer Technology Generations - Uistributed Processing and Limits to Its Growth Chapter II Essays on the Criteria for Allocation of Engineering Resources - Overview, - Heuristics for Building Great Products, - Proposed Resource Allocation Criteria - UEC's Position in the VAN - Buyout Philosophy/Process/Criteria - Example of a "Make vs Buy" Analysis - Engineering Investment Sieve Chapter III Essays on Strategic Threats and Opportunities - Uverview, - Strategic Threats - Getting Organized in Engineering and Manufacturing to Face Our Future Competitors p - View of Competitors ---~,.~".~.-~ l f;t-1) IPrT Co?"! v. 7U/L, / IJ ...J - Te-Iecommunications Environment ) ;2f e-c.. - Competitive TeChnology Exercise, ltv • Chapter IV TeChnology Managers Committee Report ,MC- . -
Timeline of Computer History
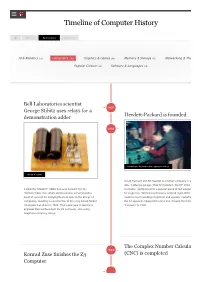
Timeline of Computer History By Year By Category Search AI & Robotics (55) Computers (145)(145) Graphics & Games (48) Memory & Storage (61) Networking & The Popular Culture (50) Software & Languages (60) Bell Laboratories scientist 1937 George Stibitz uses relays for a Hewlett-Packard is founded demonstration adder 1939 Hewlett and Packard in their garage workshop “Model K” Adder David Packard and Bill Hewlett found their company in a Alto, California garage. Their first product, the HP 200A A Called the “Model K” Adder because he built it on his Oscillator, rapidly became a popular piece of test equipm “Kitchen” table, this simple demonstration circuit provides for engineers. Walt Disney Pictures ordered eight of the 2 proof of concept for applying Boolean logic to the design of model to test recording equipment and speaker systems computers, resulting in construction of the relay-based Model the 12 specially equipped theatres that showed the movie I Complex Calculator in 1939. That same year in Germany, “Fantasia” in 1940. engineer Konrad Zuse built his Z2 computer, also using telephone company relays. The Complex Number Calculat 1940 Konrad Zuse finishes the Z3 (CNC) is completed Computer 1941 The Zuse Z3 Computer The Z3, an early computer built by German engineer Konrad Zuse working in complete isolation from developments elsewhere, uses 2,300 relays, performs floating point binary arithmetic, and has a 22-bit word length. The Z3 was used for aerodynamic calculations but was destroyed in a bombing raid on Berlin in late 1943. Zuse later supervised a reconstruction of the Z3 in the 1960s, which is currently on Operator at Complex Number Calculator (CNC) display at the Deutsches Museum in Munich. -

Turing — the Father of Computer Science”
Towards a Historical Notion of \Turing | the Father of Computer Science" Third and last draft, submitted in August 2013 to the Journal History and Philosophy of Logic Edgar G. Daylight? Eindhoven University of Technology Department of Technology Management [email protected] Abstract. In the popular imagination, the relevance of Turing's the- oretical ideas to people producing actual machines was significant and appreciated by everybody involved in computing from the moment he published his 1936 paper `On Computable Numbers'. Careful historians are aware that this popular conception is deeply misleading. We know from previous work by Campbell-Kelly, Aspray, Akera, Olley, Priestley, Daylight, Mounier-Kuhn, and others that several computing pioneers, in- cluding Aiken, Eckert, Mauchly, and Zuse, did not depend on (let alone were they aware of) Turing's 1936 universal-machine concept. Further- more, it is not clear whether any substance in von Neumann's celebrated 1945 `First Draft Report on the EDVAC' is influenced in any identifiable way by Turing's work. This raises the questions: (i) When does Turing enter the field? (ii) Why did the Association for Computing Machin- ery (ACM) honor Turing by associating his name to ACM's most pres- tigious award, the Turing Award? Previous authors have been rather vague about these questions, suggesting some date between 1950 and the early 1960s as the point at which Turing is retroactively integrated into the foundations of computing and associating him in some way with the movement to develop something that people call computer science. In this paper, based on detailed examination of hitherto overlooked pri- mary sources, attempts are made to reconstruct networks of scholars and ideas prevalent to the 1950s, and to identify a specific group of ACM actors interested in theorizing about computations in computers and attracted to the idea of language as a frame in which to understand computation. -

From Cyber-Utopia to Cyber-War. Advocacy Coalitions and the Normative Change in Cyberspace
From Cyber-Utopia to Cyber-War. Normative Change in Cyberspace. Dissertation zur Erlangung des akademischen Grades doctor philosophiae (Dr. phil.) vorgelegt dem Rat der Fakultät für Sozial- und Verhaltenswissenschaften der Friedrich- Schiller-Universität Jena von Matthias Schulze (M.A.) geboren am 28.03.1986 in Weimar 15.03.2017 1 Gutachter 1. Prof. Dr. Rafael Biermann (Friedrich-Schiller Universität Jena) 2. Dr. Myriam Dunn Cavelty (ETH Zürich) 3. Prof. Dr. Georg Ruhrmann (Friedrich-Schiller Universität Jena) Tag der mündlichen Prüfung: 08.08.2017 2 Copyright © 2018 by Matthias Schulze. Some Rights reserved. This work is licensed under the Creative Commons Attribution 4.0 International License (CC BY 4.0). To view a copy of this license, visit http://creativecommons.org/licenses/by/4.0/ or send a letter to Creative Commons, PO Box 1866, Mountain View, CA 94042, USA. 3 Table of Contents Table of Contents 4 Acknowledgement 7 Abstract 10 List of Abbreviations 11 List of Tables and Graphics 13 1. Introduction 15 1.1 Puzzle & Research Question 18 1.2 Literature Review 22 1.3 Contributions of the Study 27 1.4 Case Selection: The United States 30 1.5 Structure and Logic of the Argument 32 2. Explaining Normative Change 38 2.1 Norms and Theories of Normative Change 39 2.1.1 Norm Diffusion and Norm Entrepreneurs 41 2.1.2 Critique of Deontological Norms 42 2.1.3 Critique of Diffusion Models 44 2.2 Paradigms and Norm-Change 47 2.2.1 Discursive Struggles between Paradigms 53 2.2.2 Framing 59 2.2.3 Degrees of Change 63 2.2.4 Explaining Change 67 -

Alan Turingturing –– Computercomputer Designerdesigner
AlanAlan TuringTuring –– ComputerComputer DesignerDesigner Brian E. Carpenter with input from Robert W. Doran The University of Auckland May 2012 Turing, the theoretician ● Turing is widely regarded as a pure mathematician. After all, he was a B-star Wrangler (in the same year as Maurice Wilkes) ● “It is possible to invent a single machine which can be used to compute any computable sequence. If this machine U is supplied with the tape on the beginning of which is written the string of quintuples separated by semicolons of some computing machine M, then U will compute the same sequence as M.” (1937) ● So how was he able to write Proposals for development in the Mathematics Division of an Automatic Computing Engine (ACE) by the end of 1945? 2 Let’s read that carefully ● “It is possible to inventinvent a single machinemachine which can be used to compute any computable sequence. If this machinemachine U is supplied with the tapetape on the beginning of which is writtenwritten the string of quintuples separated by semicolons of some computing machinemachine M, then U will compute the same sequence as M.” ● The founding statement of computability theory was written in entirely physical terms. 3 What would it take? ● A tape on which you can write, read and erase symbols. ● Poulsen demonstrated magnetic wire recording in 1898. ● A way of storing symbols and performing simple logic. ● Eccles & Jordan patented the multivibrator trigger circuit (flip- flop) in 1919. ● Rossi invented the coincidence circuit (AND gate) in 1930. ● Building U in 1937 would have been only slightly more bizarre than building a differential analyser with Meccano.