Cyberspace in Deep Water: Protecting Undersea Communication Cables
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
![Submarine Cable Protection) Bill 2013 [Provisions]](https://docslib.b-cdn.net/cover/6488/submarine-cable-protection-bill-2013-provisions-36488.webp)
Submarine Cable Protection) Bill 2013 [Provisions]
The Senate Environment and Communications Legislation Committee Telecommunications Legislation Amendment (Submarine Cable Protection) Bill 2013 [Provisions] March 2014 © Commonwealth of Australia 2014 ISBN 978-1-74229-980-8 Committee address PO Box 6100 Parliament House Canberra ACT 2600 Tel: 02 6277 3526 Fax: 02 6277 5818 Email: [email protected] Internet: http://www.aph.gov.au/Parliamentary_Business/Committees/Senate/Environment_and_Com munications This work is licensed under the Creative Commons Attribution-NonCommercial-NoDerivs 3.0 Australia License. The details of this licence are available on the Creative Commons website: http://creativecommons.org/licenses/by-nc-nd/3.0/au/. This document was printed by the Senate Printing Unit, Parliament House, Canberra Committee membership Committee members Senator John Williams, Chair NATS, New South Wales Senator Anne Urquhart, Deputy Chair ALP, Tasmania Senator David Fawcett LP, South Australia Senator Louise Pratt ALP, Western Australia Senator Anne Ruston LP, South Australia Senator Larissa Waters AG, Queensland Substitute member for this inquiry Senator Scott Ludlam (AG, WA) to replace Senator Larissa Waters (AG, QLD) for this inquiry. Committee secretariat Ms Christine McDonald, Committee Secretary Mr Chris Lawley, Senior Research Officer Mrs Dianne Warhurst, Administration Officer iii iv Table of Contents Committee membership ................................................................................... iii Chapter 1 - Introduction ................................................................................... -

THE BULLYTIN Official News Letter of Field Marshal Shellhole
THE BULLYTIN Official News Letter of Field Marshal Shellhole JUNE 2017 Dear Readers, This will be my last “GO” at “the Bullytin” as duty calls elsewhere for now, thank you to those who took the time to read it. To all who provided articles and photographs your contributions were always greatly appreciated. Best wishes to you all Yours Aye – The Editor Moth Johnny Demetroudes. Australia's First National Boer War Memorial in Canberra 1 The 31st May is the anniversary of the signing of the Treaty of Vereeniging that ended the South African War in 1902. In 2017, 115 years from the day peace was concluded, the completed Australian National Boer War Memorial will be dedicated in ANZAC Parade Canberra. – Article supplied by Moth Renaud Booysen – Gorgeous Wrecks Shellhole. http://www.bwm.org.au/site/Boer_War_Day2017.php 2 Somme sketches: British soldier’s beautiful pencil drawings detailing life on the Western Front revealed in stunning artwork - By Rachael Burford For Mailonline Lieutenant Morris Meredith Williams filled 15 sketch books while serving on the Western Front during WW1 He drew at every opportunity and there are some shocking sights, including a body caught in barbed wire His drawings are included in book An Artist's War along with letters Lt Williams sent to his wife Alice Williams Lt Williams served in the 17th Battalion of the Welsh Regiment in France from 1916 until the end of the war A Tommy's drawings showing life on the front line during the First World War are set to be published for the first time. -

Before the FEDERAL COMMUNICATIONS COMMISSION Washington, D.C
Before the FEDERAL COMMUNICATIONS COMMISSION Washington, D.C. 20554 In the Matter of ) ) GU HOLDINGS INC. and EDGE CABLE ) File Nos. SCL-LIC-2020_________ HOLDINGS USA, LLC ) ) Application for a License to Construct, Land, ) and Operate the Pacific Light Cable Network ) to Connect the United States to Taiwan and ) the Philippines ) APPLICATION FOR A CABLE LANDING LICENSE (STREAMLINED PROCESSING REQUESTED) Pursuant to the Act Relating to the Landing and Operation of Submarine Cables in the United States, 47 U.S.C. §§ 34-39, Executive Order 10,530, and 47 C.F.R. § 1.767, GU Holdings Inc. (“GU Holdings”) and Edge Cable Holdings USA, LLC (“Edge USA”) (together, the “Applicants”), request a license to construct, land, and operate a high-capacity fiber-optic submarine cable system connecting the United States to Taiwan and the Philippines. For purposes of this application, the system is referred to as the Pacific Light Cable Network (“PLCN”). PLCN will be made up of the following elements: ● The fiber pair owned by GU Holdings and its affiliates connecting the United States to Branching Unit 2 (Fiber Pair 2 on each of Segments S1.1.1, S1.1.2, and S1.2 1); ● The branch owned by GU Holdings’ affiliates connecting Taiwan to Branching Unit 1, including the two fiber pairs on that branch (Segment S2); ● The fiber pair owned by Edge USA and its affiliates connecting the United States to Branching Unit 2 (Fiber Pair 1 on each of Segments S1.1.1, S1.1.2, and S1.2); ● The branch owned by Edge USA’s affiliates connecting Baler, Philippines, to 1 For segment references, see Appendix A hereto. -

Alexander Graham Bell
WEEK 2 LEVEL 7 Alexander Graham Bell Alexander Graham Bell is the famous inventor of the telephone. Born in Scotland on March 3, 1847, he was the second son of Alexander and Eliza Bell. His father taught students the art of speaking clearly, or elocution, and his mother played the piano. Bell’s mother was almost deaf. His father’s career and his mother’s hearing impairment influenced the course of his career. He became a teacher of deaf people. As a child, Bell didn’t care for school, and he eventually dropped out. He did like to solve problems though. For example, when he was only 12, he invented a new farm implement. The tool removed the tiny husks from wheat grains. After the deaths of his two brothers from tuberculosis, Bell and his parents moved from Europe to Canada in 1870. They thought the climate there was healthier than in Scotland. A year later, Bell moved to the United States. He got a job teaching at the Boston School for Deaf Mutes. © 2019 Scholar Within, Inc. WEEK 2 LEVEL 7 One of his students was a 15-year-old named Mabel Hubbard. He was 10 years older than she was, but they fell in love and married in 1877. The Bells raised two daughters but lost two sons who both died as babies. Bell’s father-in-law, Gardiner Hubbard, knew Bell was interested in inventing things, so he asked him to improve the telegraph. Telegraph messages were tapped out with a machine using dots and dashes known as Morse code. -

Anchoring the African Internet Ecosystem
Anchoring the African Internet Ecosystem Anchoring the African Internet Ecosystem: Lessons from Kenya and Nigeria’s Internet Exchange Point Growth By Michael Kende June 2020 CC BY-NC-SA 4.0 internetsociety.org 1 Anchoring the African Internet Ecosystem Table of contents 3 Executive summary 6 Background: A vision for Africa 8 Introduction: How to get there from here 13 Success stories: Kenya and Nigeria today 18 Results that stand the test of time 20 Change factors: Replicable steps toward measurable outcomes 27 Market gaps 29 Recommendations 33 Conclusions 34 Annex A: Kenya Internet Exchange Point 35 Annex B: Internet Exchange Point of Nigeria 36 Annex C: Acknowledgments 37 Annex D: Glossary of terms 38 Annex E: List of figures and tables CC BY-NC-SA 4.0 internetsociety.org 2 Anchoring the African Internet Ecosystem Executive summary In 2010, the Internet Society’s team in Africa set an The rapid pace of Internet ecosystem ambitious goal that 80% of African Internet traffic development in both Kenya and Nigeria since would be locally accessible by 2020. 2012 underscores the critical role that IXPs Internet Exchange Points (IXPs) are key to realizing and the accompanying infrastructure play in this goal in that they enable local traffic exchange and the establishment of strong and sustainable access to content. To document this role, in 2012, the Internet ecosystems. Internet Society commissioned a study to identify and quantify the significant benefits of two leading African This development produces significant day-to-day IXPs at the time: KIXP in Kenya and IXPN in Nigeria. value—the present COVID-19 crisis magnifies one such The Internet Society is pleased to publish this update benefit in the smooth accommodation of sudden of the original study. -
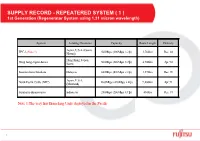
SUPPLY RECORD - REPEATERED SYSTEM ( 1 ) 1St Generation (Regenerator System Using 1.31 Micron Wavelength)
SUPPLY RECORD - REPEATERED SYSTEM ( 1 ) 1st Generation (Regenerator System using 1.31 micron wavelength) System Landing Countries Capacity Route Length Delivery Japan, U.S.A. (Guam, TPC-3 (Note 1) 560Mbps (280Mbps x 2fp) 3,760km Dec. 88 Hawaii) Hong Kong, Japan, Hong Kong-Japan-Korea 560Mbps (280Mbps x 2fp) 4,700km Apr. 90 Korea Kuantan-Kota Kinabaru Malaysia 840Mbps (420Mbps x 2fp) 1,570km Dec. 90 Japan, U.S.A. North Pacific Cable (NPC) 1680Mbps (420Mbps x 4fp) 9,400km Apr. 91 (Mainland) Surabaya-Banjarmasin Indonesia 280Mbps (280Mbps x 1fp) 410km Dec. 91 N. ote 1:The very first Branching Units deployed in the Pacific 1 SUPPLY RECORD - REPEATERED SYSTEM ( 2 ) 2nd Generation (Regenerator System using 1.55 micron wavelength) System Landing Sites Capacity Route Length Delivery UK-Germany No.5 (Note 2) UK, Germany 3.6Gbps (1.8Gbps x 2fp) 500km Oct. 91 Brunei-Singapore Brunei, Singapore 1120Mbps (560Mbps x 2fp) 1500km Nov. 91 Brunei, Malaysia, Brunei-Malaysia-Philippines (BMP) 1120Mbps (560Mbps x 2fp) 1500km Jan. 92 Philippines Japan, U.S.A. TPC-4 1680Mbps (560Mbps x 3fp) 5000km Oct. 92 (Mainland) Japan, Hong Kong, APC Taiwan, Malaysia, 1680Mbps (560Mbps x 3fp) 7600km Aug. 93 Singapore Malaysia-Thailand Malaysia, Thailand 1120Mbps (560Mbps x 2fp) 1500km Aug. 94 (incl. Petchaburi-Sri Racha) Russia-Japan-Korea (RJK) Russia, Japan, Korea 1120Mbps (560Mbps x 2fp) 1700km Nov. 94 Thailand, Vietnam, Thailand-Vietnam-Hong Kong (T-V-H) 1120Mbps (560Mbps x 2fp) 3400km Nov. 95 Hong Kong N. ote 2: The very first giga bit submarine cable system in the world 2 SUPPLY RECORD - REPEATERED SYSTEM ( 3 ) 3rd Generation (Optical Amplifier System) System Landing Sites Capacity Route Length Delivery Malaysia Domestic (Southern Link) Malaysia 10Gbps (5Gbps x 2fp) 2,300km Jul. -

Submarine Cables
SUBMARINE CABLES The business of constructing and then maintaining DLA Piper is one of the largest global law firms in and selling capacity over submarine fibreoptic cables the world. We have a particular focus on this sector is fascinating, and is absolutely fundamental to and are very familiar with its specific idiosyncrasies modern day communications. The sector has its own and requirements. Whether it’s negotiating a new unique challenges due to the extraordinarily rapid consortium agreement, arranging finance, undertaking pace of development in transmission technologies pre-investment due diligence, advising on taxation as well as the timescales and levels of investment matters, dealing with regulatory matters, purchasing required to build new systems. infrastructure or capacity (on a lease or “IRU” basis) or advising on the effects of insolvency we have sector-specific experience which we don’t think can be matched by any other law firm in the world. UNRIVALLED SECTOR EXPERTISE ■ Advising Main One in connection with the extension of their existing West African cable system to other Offering outstanding legal support to the industry requires countries in the region. a complex mix of international law, financing, tax, regulatory, property and commercial expertise. It requires ■ Advising Broadband Infraco, one of the principal a thorough understanding of the sector in all its aspects, investors in the (consortium) West Africa Cable and it requires experience going back many years. System (WACS) in relation to its investment in WACS. The bulk of the work was to help them sell a significant Our unrivalled international network matches perfectly percentage of their entitlement under the consortium’s the international nature of the business, and allows the construction and maintenance agreement (the firm to provide timely and relevant advice to submarine “C&MA”) to another African telecoms operator. -

Before the FEDERAL COMMUNICATIONS COMMISSION Washington, D.C
Before the FEDERAL COMMUNICATIONS COMMISSION Washington, D.C. In the Matter of EDGE CABLE HOLDINGS USA, LLC, File No. SCL-LIC-2020-____________ AQUA COMMS (AMERICAS) INC., AQUA COMMS (IRELAND) LIMITED, CABLE & WIRELESS AMERICAS SYSTEMS, INC., AND MICROSOFT INFRASTRUCTURE GROUP, LLC, Application for a License to Land and Operate a Private Fiber-Optic Submarine Cable System Connecting the United States, the United Kingdom, and France, to Be Known as THE AMITIÉ CABLE SYSTEM JOINT APPLICATION FOR CABLE LANDING LICENSE— STREAMLINED PROCESSING REQUESTED Pursuant to 47 U.S.C. § 34, Executive Order No. 10,530, and 47 C.F.R. § 1.767, Edge Cable Holdings USA, LLC (“Edge USA”), Aqua Comms (Americas) Inc. (“Aqua Comms Americas”), Aqua Comms (Ireland) Limited (“Aqua Comms Ireland,” together with Aqua Comms Americas, “Aqua Comms”), Cable & Wireless Americas Systems, Inc. (“CWAS”), and Microsoft Infrastructure Group, LLC (“Microsoft Infrastructure”) (collectively, the “Applicants”) hereby apply for a license to land and operate within U.S. territory the Amitié system, a private fiber-optic submarine cable network connecting the United States, the United Kingdom, and France. The Applicants and their affiliates will operate the Amitié system on a non-common-carrier basis, either by providing bulk capacity to wholesale and enterprise customers on particularized terms and conditions pursuant to individualized negotiations or by using the Amitié cable system to serve their own internal business connectivity needs. The existence of robust competition on U.S.-U.K., U.S.-France, and (more broadly) U.S.-Western Europe routes obviates any need for common-carrier regulation of the system on public-interest grounds. -
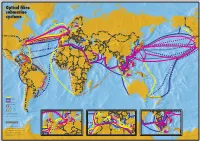
Optical Fibre Submarine Systems
Optical fibre submarine GREENLAND systems D N ALASKA A (USA) ICELAND L Umeå N Vestmannaeyjar BOTNIA I Vaasa F Faroes SWEDEN Rauma RUSSIA 6 x 622 Turku Hallstavik Whittier Valdez Karst 2 + 1 x 2.5 Gbit/s Norrtälje Kingisepp Seward Tallin NORWAY ESTONIA U N Lena I 2 x 560 LATVIA CANTAT-3 T point AC-1 E DENMARK CANADA D Westerland LITHUANIA Northstar 2 x 4 (WDM) x 2.5 Gbit/s TAT-14 K I N REP. OF IRELAND G BELORUSSIA TAT-10 2 + 1 x 560 D S D Norden/ N O LA Grossheide ER POLAND M TH NE GERMANY Gemini North 2 x 6 (WDM) x 2.5 Gbit/s BELGIUM CZECH Dieppe REP. Port UKRAINE Alberni NPC 3 + 1 x 420 St Brieuc SLOVAK REP. M O KAZAKHSTAN L FRANCE D Seattle AC-1 AUSTRIA A V TPC-5 2 x 5 Gbit/s HUNGARY I Tillamook PTAT-1 3 + 1 x 420 Gbit/s SWITZ. I A A Odessa DM) x 2.5 St Hilaire de Riez SLOVEN 2 x 6 (W MONGOLIA i South FLAG Atlantic-1 160 Gbit/s emin CROATIA ROMANIA Pacific G Y I U Novorossijsk City Pennant Point HERZEGOVINABOSNIA- G s T O 2.5 SochiGbit/s PC-1 Medway Harbour Gbit/ S x 5 L TAT-11 3 DxM 560) A Varna Shirley x 3 (W A V Nakhodka TAT-12 2 x 3 (WDM) x 5 Gbit/s 2 I GEORGIA Ishikati TAT-13 A BULGARIA UZBEKISTAN Rhode Island F L PC-1 L ALBANIA Poti A KYRGYZSTAN N Long Island G Y TAT-9 2 + 1 x 560 ARMENIA AZERBAIJAN New York MACEDONIA TURKMENISTAN NORTH Bandon TAT-8 2 x 280 Istanbul KOREA FLAG Atlantic-1 160 Gbit/s Azores SPAIN E R-J-K C 2 x 560 0 EE 6 R 5 G Dalian A CANUS-1 TAT-14 PORTUGAL TURKEY JIH CableProject Japan-US Manasquan Lisbon UNITED STATES 3x TAJIKISTAN Point Sesimbra PC-1 Arena Tuckerton Marmaris Yantaï SOUTH P TPC-4 2 x 560 A S -

Grammar for Academic Writing
GRAMMAR FOR ACADEMIC WRITING Tony Lynch and Kenneth Anderson (revised & updated by Anthony Elloway) © 2013 English Language Teaching Centre University of Edinburgh GRAMMAR FOR ACADEMIC WRITING Contents Unit 1 PACKAGING INFORMATION 1 Punctuation 1 Grammatical construction of the sentence 2 Types of clause 3 Grammar: rules and resources 4 Ways of packaging information in sentences 5 Linking markers 6 Relative clauses 8 Paragraphing 9 Extended Writing Task (Task 1.13 or 1.14) 11 Study Notes on Unit 12 Unit 2 INFORMATION SEQUENCE: Describing 16 Ordering the information 16 Describing a system 20 Describing procedures 21 A general procedure 22 Describing causal relationships 22 Extended Writing Task (Task 2.7 or 2.8 or 2.9 or 2.11) 24 Study Notes on Unit 25 Unit 3 INDIRECTNESS: Making requests 27 Written requests 28 Would 30 The language of requests 33 Expressing a problem 34 Extended Writing Task (Task 3.11 or 3.12) 35 Study Notes on Unit 36 Unit 4 THE FUTURE: Predicting and proposing 40 Verb forms 40 Will and Going to in speech and writing 43 Verbs of intention 44 Non-verb forms 45 Extended Writing Task (Task 4.10 or 4.11) 46 Study Notes on Unit 47 ii GRAMMAR FOR ACADEMIC WRITING Unit 5 THE PAST: Reporting 49 Past versus Present 50 Past versus Present Perfect 51 Past versus Past Perfect 54 Reported speech 56 Extended Writing Task (Task 5.11 or 5.12) 59 Study Notes on Unit 60 Unit 6 BEING CONCISE: Using nouns and adverbs 64 Packaging ideas: clauses and noun phrases 65 Compressing noun phrases 68 ‘Summarising’ nouns 71 Extended Writing Task (Task 6.13) 73 Study Notes on Unit 74 Unit 7 SPECULATING: Conditionals and modals 77 Drawing conclusions 77 Modal verbs 78 Would 79 Alternative conditionals 80 Speculating about the past 81 Would have 83 Making recommendations 84 Extended Writing Task (Task 7.13) 86 Study Notes on Unit 87 iii GRAMMAR FOR ACADEMIC WRITING Introduction Grammar for Academic Writing provides a selective overview of the key areas of English grammar that you need to master, in order to express yourself correctly and appropriately in academic writing. -

Abu Dhabi NREN ME-SIG April 6 2009
Partner and participant in Global R&E networking NREN ME-SIG meeting Abu Dhabi April 6th 2009 Yves Poppe ©2008 Tata Communications, Ltd. All Rights Reserved Member of the Tata Group 125-year old largest private sector group $62.5 billion in revenues Acquired VSNL in February 2002 § VSNL acquired Tyco in Nov 2004 § VSNL acquired Teleglobe in Feb 2006 Teleglobe, Tyco, VSNL and VSNL International become Tata Communications on February 13th 2008 Tata Consultancy Services (TCS) Cofounder and major shareholder in Neotel South Africa GROUP COMPANIES • Annual Spend ~ USD 85 Mn: 66% Equity of Tata Sons in Public Trusts Social Welfare Expenditure Sir Dorabji Tata Trust Sir Ratan Tata Trust budgeted before preparation of P&L account ACTIVITIES Indian Institute of Science, • Endowments for Creation of National Institutions: • Commitment to adjacent Bangalore communities incorporated in (1911) Indian Institute of Science company Articles of (1936) Tata Institute of Social Sciences Association (1941) Tata Memorial Hospital • Active volunteering (1945) Tata Institute of Fundamental programme: over 10,000 Research volunteers (1966) National Centre for the Performing Tata Institute of Fundamental • Company Examples: Research, Mumbai Arts • Development assistance in water harvesting, medical • Tata Steel: HIV / AIDS Programme - research, microfinance, bio-diversity Global Business Council Foreign scholarships - science & engineering Tata• Council for Community Initiatives winner Facilitating Role for companies’CSR activities • Triple Bottom-line Global -

KDDI Global ICT Brochure
https://global.kddi.com KDDI-Global Networks and IT Solutions Networking, Colocation, System Integration around the world BUILDING YOUR BUSINESS TOGETHER KDDI solutions are at the cutting-edge in all fields of information and communications KDDI, a Fortune Global 500 company, is one of Asia’s largest telecommunications providers, with approximately US$48 billion in annual revenue and a proven track record extending over many years and around the world. We deliver all-round services, from mobile phones to fixed-line communications, making us your one-stop solution provider for telecommunications and IT environments. The high praise and trust enjoyed by our TELEHOUSE data centers positioned around the world have kept us at the forefront of service and quality. Since our establishment in 1953, we have expanded our presence into 28 countries and 60 cities, with over 100 offices around the world supporting the success of our international customers through our high quality services. KDDI’s mobile telephone brand “au” has achieved significant market share in Japan, one of the world’s most comprehensive KDDI Quick Facts communications markets. KDDI’s relationship with over 600 carriers worldwide enables us to provide high-quality international network services in over 190 countries. Our exciting ventures, built on extensive experience, include investment in the “South-East Asia Japan 2 Cable”, which connects 11 locations in 9 countries and territories in Asia. Moreover, as the world moves toward the age of IoT and 5G, KDDI is taking steps to promote IoT business, such as connected cars, support for companies engaged in global business, and the creation of new value for our society.