Kentucky's Election Voting Systems and Certijicationprocess (October 23,2007), Comprised of an Investigative Report by My Staff and the Expert Report of Mr
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Surveymonkey Analyze
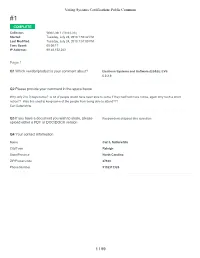
Voting Systems Certification: Public Comment #1 COMPLETE Collector: Web Link 1 (Web Link) Started: Tuesday, July 24, 2018 1:50:42 PM Last Modified: Tuesday, July 24, 2018 1:57:00 PM Time Spent: 00:06:17 IP Address: 99.46.152.243 Page 1 Q1 Which vendor/product is your comment about? Elections Systems and Software (ES&S): EVS 5.2.2.0 Q2 Please provide your comment in the space below Why only 2 to 3 days notice? A lot of people would have been able to come if they had had more notice, again why such a short notice?? Was this used to keep some of the people from being able to attend??? Carl Satterwhite Q3 If you have a document you wish to share, please Respondent skipped this question upload either a PDF or DOC/DOCX version Q4 Your contact information Name Carl L Satterwhite City/Town Raleigh State/Province North Carolina ZIP/Postal Code 27610 Phone Number 9192313328 1 / 59 Voting Systems Certification: Public Comment #2 COMPLETE Collector: Web Link 1 (Web Link) Started: Tuesday, July 24, 2018 2:01:57 PM Last Modified: Tuesday, July 24, 2018 2:04:52 PM Time Spent: 00:02:54 IP Address: 76.182.31.92 Page 1 Q1 Which vendor/product is your comment about? All Q2 Please provide your comment in the space below I would be very interested in attending, but I have to take my husband to an appointment at the VA Hospital. Q3 If you have a document you wish to share, please Respondent skipped this question upload either a PDF or DOC/DOCX version Q4 Your contact information Name Pauline Hoffmann City/Town Raleigh State/Province NC ZIP/Postal Code 27613 Country USA Email Address [email protected] 2 / 59 Voting Systems Certification: Public Comment #3 COMPLETE Collector: Web Link 1 (Web Link) Started: Wednesday, July 25, 2018 12:16:23 PM Last Modified: Wednesday, July 25, 2018 12:20:56 PM Time Spent: 00:04:32 IP Address: 99.173.129.35 Page 1 Q1 Which vendor/product is your comment about? All Q2 Please provide your comment in the space below You must include a paper ballot back up. -

Pilot Studies
GEO-ENABLED ELECTIONS | PILOT STUDIES NSGIC’s Geo-Enabled Elections Project NSGIC partnered with states and subject matter experts to develop Best Practices for integrating GIS in electoral systems. This pilot study helped inform those Best Practices. Learn more on elections.nsgic.org. Kentucky STATE PROJECT BACKGROUND The Commonwealth sees the NSGIC Geo-Enabled Elections project as an opportunity to enhance the integrity and efficiency of elections. Additionally, there are Core Team identified business processes within State Government Kent Anness, GIS Branch Manager that could benefit greatly if voting precinct data was Office of IT Architecture & Governance Commonwealth Office of Technology accurate, current, and readily accessible. Kentucky Kimberly Anness hopes to establish an ongoing relationship between the Office of IT Architecture & Governance GIS community and the agencies that are involved in Commonwealth Office of Technology the election process and subsequently, build upon that Jared Dearing, Executive Director relationship with an aim of geo-enabling the election Board of Elections Kentucky process. It is felt that if appropriate best practices are Jennifer Morrell embraced the citizens in Kentucky will have more faith Former Election Official now Consultant in the election process and taxpayer savings could be Veronica Degraffenreid realized. Director of Elections State Board of Elections North Carolina Stakeholders Kentucky State Board of Elections (SBE) Secretary of State (SOS) Kentucky Legislative Research Commission -

Is This Any Way to Vote?
IS THIS ANY WAY TO VOTE? Vulnerable Voting Machines and the Mysterious Industry Behind Them CELESTE KATZ MARSTON AND GABRIELLA NOVELLO WhoWhatWhy New York City Copyright © 2020 by WhoWhatWhy All rights reserved. No part of this book may be used or reproduced in any manner whatsoever without written permission from the publisher, except in the case of brief quotations embodied in critical articles and reviews. Cover design by Cari Schmoock. Cover art and photo editing by Michael Samuels. Data visualizations by Lizzy Alves. Published in the United States by WhoWhatWhy. eBook ISBN 978-1-7329219-1-7 WhoWhatWhy® is a registered trademark of Real News Project, Inc. CONTENTS Initialisms and Acronyms Used in This Book vi Introduction 1 1. The Voting-Machine Manufacturers 5 2. The Voting Machines 25 3. Voting Machine Accessibility 42 4. Voting Machine Vulnerabilities 55 5. Solutions and Global Perspectives 77 6. Conclusion 102 7. Addendum: Is Mail-in Voting the Answer? 108 About the Authors 116 About WhoWhatWhy 118 Glossary 119 INITIALISMS AND ACRONYMS USED IN THIS BOOK ADA Americans with Disabilities Act BMD ballot-marking device COIB Conflicts of Interest Board DRE direct-recording electronic machine EAC Election Assistance Commission EMS election management system ES&S Election Systems & Software FVAP Federal Voting Assistance Program FWAB Federal Write-In Absentee Ballot HAVA Help America Vote Act MPSA Military Postal System Agency NPRM notice of proposed rulemaking OSET Open Source Election Technology Institute RFP request for proposal RLA risk-limiting audit SQL Structure Query Language TGDC Technical Guidelines Development Committee UOCAVA Uniformed and Overseas Citizens Absentee Voting Act VSAP Voting Solutions for All People VVPAT Voter Verified Paper Audit Trail VVSG Voluntary Voting System Guidelines Photo credit: Florida Memory / Flickr 2 | INTRODUCTION When we talk about elections, we often focus on the campaign horserace, who is up or down in the polls, the back and forth between candidates, and maybe a little about which issues matter most to voters. -

Do Newspapers Matter? Short-Run and Long-Run Evidence from the Closure of the Cincinnati Post
NBER WORKING PAPER SERIES DO NEWSPAPERS MATTER? SHORT-RUN AND LONG-RUN EVIDENCE FROM THE CLOSURE OF THE CINCINNATI POST Sam Schulhofer-Wohl Miguel Garrido Working Paper 14817 http://www.nber.org/papers/w14817 NATIONAL BUREAU OF ECONOMIC RESEARCH 1050 Massachusetts Avenue Cambridge, MA 02138 March 2009 A previous version of this paper circulated under the title "Do Newspapers Matter? Evidence from the Closure of The Cincinnati Post." We are grateful to employees of The Cincinnati Post and the E.W. Scripps Co., several of whom requested anonymity, for helpful conversations. They are not responsible in any way for the content of this paper. We also thank Alícia Adserà, Anne Case, Taryn Dinkelman, Ying Fan, Douglas Gollin, Bo Honoré, James Schmitz, Jesse Shapiro, and numerous seminar participants for valuable suggestions, and Joan Gieseke for editorial assistance. Miryam Hegazy, Tony Hu, and Xun Liu provided excellent research assistance. The views expressed herein are those of the authors and not necessarily those of the Federal Reserve Bank of Minneapolis, the Federal Reserve System, Edgeworth Economics, or the views of the National Bureau of Economic Research. NBER working papers are circulated for discussion and comment purposes. They have not been peer- reviewed or been subject to the review by the NBER Board of Directors that accompanies official NBER publications. © 2009 by Sam Schulhofer-Wohl and Miguel Garrido. All rights reserved. Short sections of text, not to exceed two paragraphs, may be quoted without explicit permission provided that full credit, including © notice, is given to the source. Do Newspapers Matter? Short-run and Long-run Evidence from the Closure of The Cincinnati Post Sam Schulhofer-Wohl and Miguel Garrido NBER Working Paper No. -

Issues Confronting the 2011 Kentucky General Assembly
Issues Confronting the 2011 Kentucky General Assembly Informational Bulletin No. 233 Legislative Research Commission Frankfort, Kentucky Issues Confronting the 2011 Kentucky General Assembly Prepared by Members of the Legislative Research Commission Staff Informational Bulletin No. 233 Legislative Research Commission Frankfort, Kentucky lrc.ky.gov November 2010 Paid for with state funds. Available in alternative form by request. Legislative Research Commission Foreword Issues Confronting the 2011 Kentucky General Assembly Foreword As public servants, legislators confront many issues potentially affecting citizens across the Commonwealth. These issues are varied and far-reaching. The staff of the Legislative Research Commission each year attempt to compile and to explain those issues that may be addressed during the upcoming legislative session. This publication is a compilation of major issues confronting the 2011 General Assembly. It is by no means an exhaustive list; new issues will arise with the needs of Kentucky’s citizens. Effort has been made to present these issues objectively and concisely, given the complex nature of the subjects. The discussion of each issue is not necessarily exhaustive but provides a balanced look at some of the possible alternatives. The issues are grouped according to the jurisdictions of the interim joint committees of the Legislative Research Commission; no particular meaning should be placed on the order in which they appear. LRC staff members who prepared these issue briefs were selected on the basis of their knowledge of the subject. Robert Sherman Director Legislative Research Commission Frankfort, Kentucky November 15, 2010 i Legislative Research Commission Contents Issues Confronting the 2011 Kentucky General Assembly Contents Agriculture Cost-of-care Bonds for Impounded Animals............................................................................... -

The Price of Voting
The Price of Voting Today’s Voting Machine Marketplace March 2021 CONTRIBUTORS Matthew Caulfield (Principal Investigator) Andrew Coopersmith (Co-author) Arnav Jagasia (Co-author) Olivia Podos (Co-author) August Gebhard-Koenigstein (Research Assistant) John Sarihan (Research Assistant) ACKNOWLEDGEMENTS This research was conducted by a team of students and staff of The Wharton School and University of Pennsylvania. We are thankful to the generous administrative and financial support offered by the Wharton Public Policy Initiative as we pursued this project. The authors assume sole responsibility for the findings and views expressed in this report, which do not necessarily reflect the views of the Wharton School and should not be attributed to the School itself. Composing this report required a lot of help in obtaining data. We are indebted to the hundreds of local election officials who kindly provided us with documentation detailing their most recent voting system procurements, without which the voting machine pricing analysis offered here would not have been possible. And we are grateful as well to the several industry professionals who took time to give us their perspective on the current state of the election technology market. This report draws heavily on the 2017 study, The Business of Voting: Market Structure and Innovation in the Election Technology Industry. We thank Lorin Hitt, who led the study, and the student researchers who contributed. We are also indebted to the many voting industry and policy stakeholders who took the time to read and respond to the report. We appreciate their input and encouragement to continue. Matthew Caulfield et al.The Price of Voting: Today's Voting Machine Marketplace. -

Certified Voting Systems in Idaho
Idaho Certified Voting Systems As of August 19, 2016 Descriptions of Certified Voting Systems on page 12. Vendor Voting Software Hardware/Firmware System ID #/ Final Report Idaho System/System Qualified to 1990, Date Certification Component 2002 or 2005 Date Standards Hart Hart InterCivic Verity Data 2.0.2 Verity Print 2.0.3 InterCivic Verity 2.0 Verity Build 2.0.2 Verity Scan 2.0.3 EAC Certification # 4/27/2016 8/19/2016 Voting System Verity Central 2.0.2 Verity Touch Writer with Access 2.0.3 HRTVerity2.0 Verity Count 2.0.2 2005 VVSG Verity User Management software 2.0.2 Verity Election Management software 2.0.2 ES&S EVS 5.2.1.0 Election Reporting ExpressVote (Universal Voting Manager (ERM) Device) (1.4.1.0) DS200 (Precinct 2005 12/18/2015 7/22/2016 (8.12.1.0) Event Log Count Tabulator) (2.12.1.0) DS850 Service (1.5.5.0) (Central Count Tabulator) 2.10.1.0) Removable Media AutoMARK (Voter Assist Terminal Service (RMS) (1.8.6.0) (1.4.5.0) Vat Previewer (1.8.6.0) ExpressVote Previewer (1.4.1.0) ES&S DS200, DS200, DS850, ExpressVote N/A 4/19/2016 6/28/2016 DS850, ExpressVote Various De Minimis changes. Introduced ExpressVote Rolling Kiosk. Idaho Certified Voting Systems 1 As of August 19, 2016 Idaho Certified Voting Systems As of August 19, 2016 Vendor Voting Software Hardware/Firmware System ID #/ Final Report Idaho System/System Qualified to 1990, Date Certification Component 2002 or 2005 Date Standards ES&S DS200 DS200 1.3 N/A N/A May 5, 2016 ECO 1880 Multi-feed Sensor Replacement ES&S AutoMARK AutoMARK v. -
Role-Play the Vote
Role-Play the Vote Uses Vote Worthy Part 1 Segment 1 Listen here Background Reading Many people feel that the Electoral College is an outmoded method for electing the United States president but dismantling it – or even modifying it – could have unexpected consequences. The original intent of the Electoral College as outlined in the Constitution was to protect the importance of states as geopolitical units. Each state elects a number of electors equal to the number of U.S. Congressional districts in the state plus two (the number of U.S. senators from each state), thus ensuring that every state has at least three electors. In 1961, the 23rd Amendment provided Electoral College representation for the District of Columbia. The Constitution does not specify how the members of the Electoral College will be determined. In almost all states, the winner of all electoral votes is determined by the statewide winner of the popular vote in a winner-take-all contest. However, two states have a different system. In Maine and Nebraska, each congressional district is represented by an elector selected by the popular vote in that district, and two electors are awarded to the winner of the statewide popular vote. Maine also uses an innovative approach to voting known as ranked choice voting. Instead of selecting only one candidate, voters rank all candidates in their order of preference. If no candidate receives at least 50% of the vote, the candidate with the fewest number of votes is dropped. Ballots that were cast for the dropped candidate as first choice are recounted with each voter’s second choice counting as their vote. -
Policy Mechanisms for Increasing Transparency in Electronic Voting
Policy Mechanisms for Increasing Transparency in Electronic Voting by Joseph Lorenzo Hall B.S. (Astrophysics, Northern Arizona University) 2000 M.A. (Astrophysics, University of California, Berkeley) 2003 M.I.M.S. (Information, University of California, Berkeley) 2005 A dissertation submitted to the Graduate Division of the University of California at Berkeley in partial fulfillment of the requirements for the degree of Doctor of Philosophy in Information Management and Systems Committee in charge: Professor Pamela Samuelson, Chair Professor Coye Cheshire Professor Deirdre Mulligan Professor David Wagner Fall 2008 The dissertation of Joseph Lorenzo Hall is approved. Professor Pamela Samuelson (Chair) Date Professor Coye Cheshire Date Professor Deirdre Mulligan Date Professor David Wagner Date University of California, Berkeley Spring 2008 Policy Mechanisms for Increasing Transparency in Electronic Voting Copyright c 2008, Some Rights Reserved (See: Appendix F) Joseph Lorenzo Hall Abstract Policy Mechanisms for Increasing Transparency in Electronic Voting by Joseph Lorenzo Hall Doctor of Philosophy in Information Management and Systems University of California, Berkeley Professor Pamela Samuelson, Chair In the early years of the American republic, only white male landowners could vote, and then typically by expressing their preferences in a public setting, for all to witness. Our electoral system has changed drastically since that time; now almost all Americans cast votes with the assistance of computerized equipment. While much good stems from the use of computerized equipment in elections—notably increased efficiency, enfranchisement and flexibility—unintended consequences of this mechanization have left us with complicated, insecure and opaque voting systems. My PhD thesis focuses on the issue of transparency in e-voting; that is, what public pol- icy mechanisms can serve to make our voting systems less opaque? After exploring what we mean by “electoral transparency”, I examine the question of e-voting transparency on three fronts. -

Why Kentucky Should Retain Nonpartisan Elective Selection of Its Supreme Court Justices Nolan M
Kentucky Law Journal Volume 105 | Issue 3 Article 3 2017 What the Polls Produce: Why Kentucky Should Retain Nonpartisan Elective Selection of its Supreme Court Justices Nolan M. Jackson Frost Brown Todd LLC Follow this and additional works at: https://uknowledge.uky.edu/klj Part of the Courts Commons, and the Election Law Commons Right click to open a feedback form in a new tab to let us know how this document benefits you. Recommended Citation Jackson, Nolan M. (2017) "What the Polls Produce: Why Kentucky Should Retain Nonpartisan Elective Selection of its Supreme Court Justices," Kentucky Law Journal: Vol. 105 : Iss. 3 , Article 3. Available at: https://uknowledge.uky.edu/klj/vol105/iss3/3 This Article is brought to you for free and open access by the Law Journals at UKnowledge. It has been accepted for inclusion in Kentucky Law Journal by an authorized editor of UKnowledge. For more information, please contact [email protected]. What the Polls Produce: Why Kentucky Should Retain Nonpartisan Elective Selection of its Supreme Court Justices Nolan M. Jackson' TABLE OF CONTENTS TABLE OF CONTENTS ............................................ 453 INTRODUCTION ................................................. 455 I. How KENTUCKY'S NONPARTISAN ELECTIVE SELECTION SYSTEM COMPARES TO ALTERNATIVE SELECTION SYSTEMS..........456 A. How Kentucky Selects its Supreme CourtJustices........................ 456 B. How Other States Select Their Supreme CourtJustices............... 457 i. Elective Selection ............................... 457 ii. Appointive Selection .......................... 458 II. WHY THE GENERAL ASSEMBLY PROPOSED ELECTIVE SELECTION.............................460 A. History offudicial Selection in Kentucky.... ............. 461 B. Secondary Sources and "Recollections....................462 III. WHETHER NONPARTISAN ELECTIVE SELECTION WORKS EFFICACIOUSLY IN KENTUCKY........................ 464 A. MeasuingEfficacy ................................ 464 B. -

Curriculum Vitae
Cross vita 1 Curriculum Vitae ALVIN M. (AL) CROSS 123 West Todd St., Frankfort KY 40601 [email protected]; 502-223-8525 Education American Press Institute, “Interactive Community News,” March 10-12, 2008 American Press Institute, “Editing the Weekly and Community Newspaper,” May 16-18, 2007 Poynter Institute for Media Studies, “Best Practices for Newsroom Training,” Oct. 5-7, 2006 Poynter Institute for Media Studies, “Doing Ethics,” 40-hour residential course, 1999 Western Kentucky University, Bowling Green, Ky., B.A., mass communications, 1978 Academic Council representative, Associated Student Government, 1972-73 Work Experience University of Kentucky, Lexington, Ky. Associate extension professor, School of Journalism & Telecommunications, 2011-present Director, Institute for Rural Journalism and Community Issues, 2005-present Assistant extension professor, School of Journalism & Telecommunications, 2005-2011 Interim IRJCI Director/Lecturer, School of Journalism & Telecomm., 2004-2005 The Courier-Journal, Louisville, Ky. South Central Kentucky Bureau chief, Somerset, 1978 Central Kentucky Bureau chief, Bardstown, 1979-84 City Desk reporter (education, transportation, politics), 1984-86 State Capital Bureau reporter, Frankfort, 1987-88 Political writer and columnist, 1989-2004 Grayson County News-Gazette, Leitchfield, Ky. Editor, 1977-78 Leitchfield Gazette, Leitchfield, Ky. Editor and general manager, 1977 Logan Leader and News-Democrat, Russellville, Ky. Assistant managing editor, 1975-77 The Reporter, Monticello, Ky. News editor, 1974 Editor and general manager, 1975 College Heights Herald, Western Kentucky University Copy editor, 1972 Advertising manager, 1972-73 Chief reporter, 1973-74 Editor, 1974 Circulation manager and anniversary edition coordinator, 1975 WANY AM-FM, Albany, Ky. Sports announcer, 1967-71; staff announcer, 1967-75 Clinton County News, Albany, Ky. -

Faculty Member's Name
Dewey M. Clayton Faculty Member’s Name Political Science Department CURRICULM VITAE August 9, 2016 For Personnel Actions Date College of Arts and Sciences Faculty Member’s Signature I. EMPLOYMENT HISTORY: A. Academic Institutions other than University of Louisville Institution Years Title of (Name and Location) of Service Position North Carolina Central University 2 Instructor Durham, NC27573 B. University of Louisville Date appointed: July 1, 1994 Rank when appointed: Assistant Professor Credit toward tenure when appointed? (Years) None Date tenured: July 1, 2001 If currently untenured: date of mandatory tenure decision: Promotion record: (if applicable, please fill in following dates): If appointed Instructor, date of promotion to Assistant Professor: Date of promotion to Associate Professor: July 1, 2000 Date of promotion to Professor: July 1, 2008 C. Other relevant employment. (Please give title, type of work, location, dates and other pertinent information.) Columbia College – Adjunct Instructor – Columbia, MO, March 1992-March 1993 Lincoln University – Adjunct Instructor – Jefferson City, MO, January-August 1993 North Carolina Department of Commerce, Small Business Development Division – Minority Business Research Specialist – December 1986-August 1987 D. Honors received: American Political Science Association 2016 Distinguished Teaching Award, May 2016 Nominated by the Vice Provost for Diversity and International Relations as the University of Louisville Black Achiever for 2016. Nominated by the Vice Provost for Diversity and International Relations for Who’s Who Louisville: 2016 African American Profiles, August 2015. In February 2015, I was featured in the Spring 2015 edition of the Commission on Diversity and Racial Equality (CODRE) newsletter at UofL for my contributions as a member.