(12) Patent Application Publication (10) Pub. No.: US 2013/0210470 A1 Davies Et Al
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Creating a Patch and Vulnerability Management Program
Special Publication 800-40 Version 2.0 Creating a Patch and Vulnerability Management Program Recommendations of the National Institute of Standards and Technology (NIST) Peter Mell Tiffany Bergeron David Henning NIST Special Publication 800-40 Creating a Patch and Vulnerability Version 2.0 Management Program Recommendations of the National Institute of Standards and Technology Peter Mell Tiffany Bergeron David Henning C O M P U T E R S E C U R I T Y Computer Security Division Information Technology Laboratory National Institute of Standards and Technology Gaithersburg, MD 20899-8930 November 2005 U.S. Department of Commerce Carlos M. Gutierrez, Secretary Technology Administration Michelle O'Neill, Acting Under Secretary of Commerce for Technology National Institute of Standards and Technology William A. Jeffrey, Director CREATING A PATCH AND VULNERABILITY MANAGEMENT PROGRAM Reports on Computer Systems Technology The Information Technology Laboratory (ITL) at the National Institute of Standards and Technology (NIST) promotes the U.S. economy and public welfare by providing technical leadership for the nation’s measurement and standards infrastructure. ITL develops tests, test methods, reference data, proof of concept implementations, and technical analysis to advance the development and productive use of information technology. ITL’s responsibilities include the development of technical, physical, administrative, and management standards and guidelines for the cost-effective security and privacy of sensitive unclassified information in Federal computer systems. This Special Publication 800-series reports on ITL’s research, guidance, and outreach efforts in computer security and its collaborative activities with industry, government, and academic organizations. National Institute of Standards and Technology Special Publication 800-40 Version 2.0 Natl. -

Emerald 5 Administrator Guide
Emerald Administrator’s Guide Version 5.0.85 Emerald Management Suite IEA Software, Inc. Emerald v5 – Administrator’s Guide 1 IEA Software, Inc. Software License Agreement By purchasing or installing all or part of the Emerald Management Suite, you indicate your acceptance of the following License Agreement. Ownership of Software You acknowledge and agree that the computer program(s) and associated documentation contained with the Emerald Management Suite (collectively, the “Software”) are owned exclusively by IEA Software, Inc. and/or its licensors. The Software contained in the package is protected under copyright laws and all copyright and other intellectual property rights relating to the Software are and remain the exclusive property of IEA Software, Inc. and/or its licensors. You may not rent or lease the Software, but you may transfer the Software and accompanying materials on a permanent basis provided you retain no copies and the recipient agrees to the terms of this Agreement. License IEA Software, Inc. grunts to you, and you accept, a limited, non- exclusive and revocable license to use the Software. You agree to use the Software in machine-readable object code form only as authorized in this License Agreement. This License Agreement does not convey any title or interest in the Software to you. You may only use the licensed number of Master Billing Records (MBRs) with the Software as stated in your purchase agreement. Scope of License You may not make any changes or modifications to the Software, and you may not decompile, disassemble, or otherwise reverse engineer the Software. You may not load, rent, lease or sublicense the Software or any copy to others for any purpose. -

9.1 Mailsite Reviewer's Guide
MailSite Reviewer’s Guide End User Reviewer’s Guide Revision 3 21st October 2014 Rockliffe Systems 1901 South Bascom Avenue Campbell, CA95008 Main: (408) 879-5600 Fax: (408) 879-5610 www.rockliffe.com ©2014 Rockliffe Systems Incorporated Table of Contents 1 Introduction ............................................................................................................................................................... 3 2 Company Overview .................................................................................................................................................. 3 3 Mailsite Package ...................................................................................................................................................... 3 4 MailSite Product Highlights ...................................................................................................................................... 4 5 Installing MailSite ..................................................................................................................................................... 5 6 Installing MailSite SE, LE, and SP ......................................................................................................................... 6 7 Reviewing MailSite ................................................................................................................................................. 12 8 Summary ............................................................................................................................................................... -

SMTP Reply Codes Reference & List
AnswersThatWorkTM SMTP Status codes – SMTP Error Codes – SMTP Reply Codes SMTP Status Codes & SMTP Error Codes Reference There comes a time in the life of a Computer Consultant where, one day, he/she will have to deal with email server problems. It is inevitable. Sometimes these problems will be with the interfacing of the mail server with the ISP, in particular an inability to send mail. After checking the usual suspects such as lack of connection (your broadband line is dead), faulty router, firewall problems, DNS problems, or an incorrect SMTP server name (thanks to some clever ISP changing its SMTP server name without informing anyone – it happens!!), you will likely start delving a little deeper by checking if your email server reports any errors. Depending on the actual problem it is encountering, your mail server may not be able to provide detailed help on how to resolve the problem, and may instead only be able to provide you with an SMTP Status Code in your server’s log (these codes are also known as SMTP Error Codes or SMTP Reply Codes). It is just for such cases that we have produced this document (we use it too !! J ). So, use this document as a quick reference to common SMTP status codes or SMTP error codes for SMTP mail servers such as AA Mail Server, Alt-N MDaemon, ArGoSoft Mail Server, Axigen Mail Server, Barracuda Spam Firewall, CMail, CMailServer, E-Mail Anywhere, FTGate, GMS Mail, Internet Anywhere, Kerio MailServer (KMS), Lotus Notes, MailEnable, MailMax, Mailtraq, Merak Mail Server, Microsoft Exchange (Exchange Server 2003 NDR, Non-Delivery Report, error codes), Novell GroupWise, Qmail, PostCast Server, PostConf, PostFix, PowerMTA, QK SMTP Server, Rockliffe MailSite, SendMail, SurgeMail, TFS Secure Message Server, VisNetic Mail Server, WinMail, Zimbra, or any other SMTP / ESMTP standards compliant e-mail MTA. -

Mailsite® Expresspro
DATA SHEET MailSite® ExpressPro MailSite ExpressPro is WHAT IS IT? WHAT’S NEW? a state-of-the-art web MailSite ExpressPro is a state-of-the-art web MailSite ExpressPro is a totally new client for managing client for managing email, calendars and contacts product written from the ground up using email, calendars and that has been built using the latest AJAX the latest AJAX web technology. MailSite contacts built using technology. MailSite ExpressPro has the look and ExpressPro allows users to manage their the latest AJAX feel of Outlook, so users that are familiar with personal email, calendars and contacts Outlook will be right at home. from a web browser. technology MICROSOFT OUTLOOK 2007 CALENDAR SHARING MailSite ExpressPro can be configured to MailSite ExpressPro allows users to automatically synchronize Calendar and Contact subscribe to remote calendars such as data with Outlook 2007. This means that the Google Calendars. It also allows users to user’s email, calendar and contact data is always share their own calendars with others available from any web browser anywhere in the who use clients such as Apple Mac iCal, world. Mozilla Lightning and Google Calendar. Users can share all of their calendar details or just their free-busy information. FULL FEATURED ExpressPro includes support for right-click and drag-and-drop functionality just like a desktop client. ExpressPro comes with support for 18 languages. Administrators can use the default “skins” or can create their own “skins” to brand the user interface to match the rest of their website. Users can even select a ”skin” to suit their own taste. -

Messaging Platforms for Service Providers - Market Quadrant 2017 ∗
. The Radicati Group, Inc. www.radicati.com . THE RADICATI GROUP, INC. Messaging Platforms for Service Providers - Market Quadrant 2017 ∗ ........ An Analysis of the Market for Messaging Platforms for Service Providers, Revealing Top Players, Trail Blazers, Specialists and Mature Players. June 2017 SM ∗ Radicati Market Quadrant is copyrighted June 2017 by The Radicati Group, Inc. Reproduction in whole or in part is prohibited without expressed written permission of the Radicati Group. Vendors and products depicted in Radicati Market QuadrantsSM should not be considered an endorsement, but rather a measure of The Radicati Group’s opinion, based on product reviews, primary research studies, vendor interviews, historical data, and other metrics. The Radicati Group intends its Market Quadrants to be one of many information sources that readers use to form opinions and make decisions. Radicati Market QuadrantsSM are time sensitive, designed to depict the landscape of a particular market at a given point in time. The Radicati Group disclaims all warranties as to the accuracy or completeness of such information. The Radicati Group shall have no liability for errors, omissions, or inadequacies in the information contained herein or for interpretations thereof. Messaging Platforms for Service Providers - Market Quadrant 2017 TABLE OF CONTENTS RADICATI MARKET QUADRANTS EXPLAINED .................................................................................. 2 MARKET SEGMENTATION – MESSAGING PLATFORMS FOR SERVICE PROVIDERS ............................ -

Outlook, Lotus Notes, Groupwise, Netscape Windows Platforms
Skills: Email Applications: Outlook, Lotus Notes, GroupWise, Netscape Windows Platforms: Windows 7, Windows 9x, NT, 2000, 2003, XP, Vista Windows Applications: Office 2010, Word, Excel, Power Point, Access Law Applications: Filesite 8.0, Mailsite, Interwoven, iManage Desksite 6.5, Pro Law, Hummingbird Document Management system, Portable 32, Crosswords, iCreate, i Scrub, iRedline and iDocID macro system, Hotdocs, Hotdocs PDF, LegalKEY Records, Intem, Enhanced Time Entry, Juris, Taxdocs, Deltaview, Redax, ISYS, Lexis Nexis , West Law, Ecopy, TraxOpen, LegalKey, AIM, IP Master, Perfect Law Document mana gement system Other Applications: Word Perfect 12, Adobe Professional, Visio, Micromedia Dre am Weaver 3, Xvision, Crystal Reports, Photofinish, HummingBird Exceed, NFS Mes tro, Citrix Neighborhood, Expert Advicer, Form Flow, Infoflow, Meeting Maker, Me ssage Manager, Stars, Remis, Call link, Act, Slick, Sequencer, Abra, Spotfire, G lovia, DCAMS, Reflections/MANMAN, ManageSoft, iNet, Softwise MacroSuite, Swiftwr iter, WestCheck 4.52, InterAction 5, Summation Blazer, Intelli-sync, Handspring, Constructware, Optika, Acorde, JDE, BizFlow, MS Office Communicator, Reference Manager, Endnote; Print Key; Suddan; SAS; TABS32; Sharepoint; File Maker Pro, F rontpage, ISAIC, Sunflower, Quosa, Sudaan; Pointsec for PC's, Symantec Ghost , Backup Exec, SharePoint 2007 Remote Software: Citrix, RAS, VPN, VNC, DSL, Dialup, Desktop Authority, NetOp R emote Control, Internet, Intranet, PC Anywhere, Net Meeting, Alta Vista Tunnel, Internet Service Providers, -
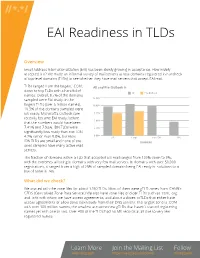
EAI Readiness in Tlds
EAI Readiness in TLDs Overview Email Address Internationalization (EAI) has been slowly growing in acceptance. How widely accepted is it? We made an informal survey of mail servers across domains registered in hundreds of top-level domains (TLDs) to see whether they have mail servers that accept EAI mail. TLDs ranged from the largest, .COM, All and Pre-Outlook % down to tiny TLDs with a handful of All Pre-Outlook names. Overall, 9.7% of the domains sampled were EAI ready. In the 12.50% largest TLDs (over a million names), 10.00% 10.5% of the domains sampled were EAI ready. Microsoft’s Outlook.com 7.50% recently became EAI ready; before 5.00% that the numbers would have been 7.41% and 7.93%. IDN TLDs were 2.50% significantly less ready than non-IDN, 0.00% 4.7% rather than 9.8%, but most All Large non-IDN IDN IDN TLDs are small and none of the DOMAINS ones sampled have many active mail servers. The fraction of domains within a TLD that accepted EAI mail ranged from 100% down to 0%, with the extremes all being in domains with very few mail servers. In domains with over 50,000 registrations, it ranged from a high of 25% of sampled domains being EAI ready in .solutions to a low of none in .ren. What did we check? We started with the zone files for about 1250 TLDs. Most of them were gTLD zones from ICANN’s CZDS (Centralized Zone Data Service.) We also have zone files of older TLDs such as .com, .org, and .info with whom we have access agreements, and about a dozen ccTLDs that either have access agreements or allow zone downloads from their DNS servers. -

Connecting to Mailsite Through Outlook
15 Commerce Dr. Cromwell, CT 06416 http://www.computercompany.net Tel: 860-635-0500 Fax: 860-635-3550 CONNECTING TO MAILSITE THROUGH OUTLOOK A TUTORIAL ON HOW TO ACCESS YOUR T.C.C. MAILSITE ACCOUNT THROUGH MICROSOFT OUTLOOK ON A WINDOWS PC 1. Ensure Microsoft Outlook is completely closed before continuing. 2. Open up Control Panel through the Start menu (Start Control Panel) 1 | P a g e 3. Click on the “Mail” icon 4. A Mail Setup window will pop-up. Click on “Show Profiles”. 5. A Mail window will appear. We are going to create a new profile for use with MailSite. Click on the “Add…” button. 6. A “New Profile” window will appear. Put in the name of the profile you wish to create. It does not have to be a username – this is just to help you identify multiple profiles. Once you enter the profile name you want, click “OK” to continue. 2 | P a g e 7. An “Add Account” window will appear. Click the radio button that says, “Manual setup or additional server types” and then click “Next >”. 8. At “Choose Service”, select the radio button that mentions “POP or IMAP” and then click “Next >” 9. You will be brought to the “POP and IMAP Account Settings” window. Here, you will fill in the details of your MailSite account. The following fields need to be filled in: 3 | P a g e a. Your Name: your first and last name b. Email Address: your email address c. Account Type: IMAP d. Incoming mail server: mail.computercompany.net e. -

Exchange Activesync Guide
IceWarp Unified Communications Exchange ActiveSync Guide Version 10.3 Printed on 30 March, 2011 Contents Exchange ActiveSync Guide 1 About ................................................................................................................................................................. 1 On-server Setup ............................................................................................................................................................. 8 Security Policies ............................................................................................................................................................ 11 Local and Remote Device Wipe ....................................................................................................................... 12 Local Device Wipe ............................................................................................................................... 12 Remote Device Wipe ........................................................................................................................... 13 E-mail Confirmation ............................................................................................................................ 13 Defining the Policies ........................................................................................................................................ 13 Global Level Policies ........................................................................................................................... -

Mailsite Administration Guide I Table of Contents
® Rockliffe MailSite Internet Mail and List Server For Windows 2000/2003 Servers Scalable - Reliable - Fast MailSite, Version 6.1 What’s New Guide for SE, LE, MP, and SP systems Rockliffe Systems, Inc. Rock Solid Messaging Software http://www.rockliffe.com ACKNOWLEDGMENTS MailSite is based on the Freeware IMS for Windows NT that was developed under the EMWAC project. Datalink Computers, Digital, Microsoft, Research Machines, Sequent and the University of Edinburgh funded EMWAC. Certain algorithms used in parts of this software are derived from the RSA Data Security, Inc. MD5 Message-Digest Algorithm. Copyright 1995-2004 Rockliffe Systems, Inc. All rights reserved. Portions of this product are Copyright The University of Edinburgh and The Regents of the University of Michigan. The information in this document is subject to change without notice. Rockliffe Systems, Inc. makes no warranty of any kind regarding this material and assumes no responsibility for any errors that may appear in this document. Rockliffe Systems, Rockliffe Systems, Inc., Rockliffe, and MailSite are trademarks of Rockliffe Systems, Inc. Microsoft, Windows, Windows 95, Windows NT, Windows 2000, Windows XP, Windows 2003, Exchange, Windows Messaging, Outlook and Internet Explorer are registered trademarks of Microsoft Corporation. Eudora and Eudora Pro are registered trademarks of Qualcomm Inc. Netscape Navigator, Communicator and Messenger are registered trademarks of Netscape Communications Corporation. UNIX is a registered trademark in the United States and other countries, licensed exclusively through X/Open Company, Ltd. Product names mentioned in this document are for identification purposes only and may be trademarks or registered trademarks of their respective companies. An asterisk indicates a trademark of another company. -

Creating a Patch and Vulnerability Management Program
Archived NIST Technical Series Publication The attached publication has been archived (withdrawn), and is provided solely for historical purposes. It may have been superseded by another publication (indicated below). Archived Publication Series/Number: NIST Special Publication 800-40 Version 2.0 Title: Creating a Patch and Vulnerability Management Program Publication Date(s): November 2005 Withdrawal Date: July 2013 Withdrawal Note: SP 800-40 is superseded by the publication of SP 800-40 Revision 3 (July 2013). Superseding Publication(s) The attached publication has been superseded by the following publication(s): Series/Number: NIST Special Publication 800-40 Revision 3 Title: Guide to Enterprise Patch Management Technologies Author(s): Murugiah Souppaya, Karen Scarfone Publication Date(s): July 2013 URL/DOI: http://dx.doi.org/10.6028/NIST.SP.800-40r3 Additional Information (if applicable) Contact: Computer Security Division (Information Technology Lab) Latest revision of the SP 800-40 Revision 3 (as of June 19, 2015) attached publication: Related information: http://csrc.nist.gov/ Withdrawal SP 800-40 Version 2 provides basic guidance on establishing patch announcement (link): management programs, and guidance to organizations with legacy needs. Date updated: June Ϯϯ, 2015 Special Publication 800-40 Version 2.0 Creating a Patch and Vulnerability Management Program Recommendations of the National Institute of Standards and Technology (NIST) Peter Mell Tiffany Bergeron David Henning NIST Special Publication 800-40 Creating a Patch and Vulnerability Version 2.0 Management Program Recommendations of the National Institute of Standards and Technology Peter Mell Tiffany Bergeron David Henning C O M P U T E R S E C U R I T Y Computer Security Division Information Technology Laboratory National Institute of Standards and Technology Gaithersburg, MD 20899-8930 November 2005 U.S.