Creating a Patch and Vulnerability Management Program
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Internet Security Threat Report VOLUME 21, APRIL 2016 TABLE of CONTENTS 2016 Internet Security Threat Report 2
Internet Security Threat Report VOLUME 21, APRIL 2016 TABLE OF CONTENTS 2016 Internet Security Threat Report 2 CONTENTS 4 Introduction 21 Tech Support Scams Go Nuclear, 39 Infographic: A New Zero-Day Vulnerability Spreading Ransomware Discovered Every Week in 2015 5 Executive Summary 22 Malvertising 39 Infographic: A New Zero-Day Vulnerability Discovered Every Week in 2015 8 BIG NUMBERS 23 Cybersecurity Challenges For Website Owners 40 Spear Phishing 10 MOBILE DEVICES & THE 23 Put Your Money Where Your Mouse Is 43 Active Attack Groups in 2015 INTERNET OF THINGS 23 Websites Are Still Vulnerable to Attacks 44 Infographic: Attackers Target Both Large and Small Businesses 10 Smartphones Leading to Malware and Data Breaches and Mobile Devices 23 Moving to Stronger Authentication 45 Profiting from High-Level Corporate Attacks and the Butterfly Effect 10 One Phone Per Person 24 Accelerating to Always-On Encryption 45 Cybersecurity, Cybersabotage, and Coping 11 Cross-Over Threats 24 Reinforced Reassurance with Black Swan Events 11 Android Attacks Become More Stealthy 25 Websites Need to Become Harder to 46 Cybersabotage and 12 How Malicious Video Messages Could Attack the Threat of “Hybrid Warfare” Lead to Stagefright and Stagefright 2.0 25 SSL/TLS and The 46 Small Business and the Dirty Linen Attack Industry’s Response 13 Android Users under Fire with Phishing 47 Industrial Control Systems and Ransomware 25 The Evolution of Encryption Vulnerable to Attacks 13 Apple iOS Users Now More at Risk than 25 Strength in Numbers 47 Obscurity is No Defense -

Vulnerability Management: Overview
Resource ID: w-013-3774 Cybersecurity Tech Basics: Vulnerability Management: Overview SEAN ATKINSON, CIS™ (CENTER FOR INTERNET SECURITY), WITH PRACTICAL LAW INTELLECTUAL PROPERTY & TECHNOLOGY Search the Resource ID numbers in blue on Westlaw for more. A Practice Note providing an overview of what Design, implementation, or other vendor oversights that create defects in commercial IT products (see Hardware and Software cyber vulnerability management programs Defects). are, how they work, and the key role they play Poor setup, mismanagement, or other issues in the way an in any organization’s information security organization installs and maintains its IT hardware and software components (see Unsecured Configurations). program. This Note discusses common types of Vulnerability management programs address these issues. Other cyber vulnerabilities and core process steps for common vulnerabilities that organizations must also tackle in their implementing and maintaining a vulnerability information security programs include: management program to decrease cybersecurity Gaps in business processes. Human weaknesses, such as lack of user training and awareness. risks. It also addresses common pitfalls that Poorly designed access controls or other safeguards. can lead to unnecessary cyber incidents and Physical and environmental issues. data breaches. Unlike threats, organizations can often directly control their vulnerabilities and therefore minimize the opportunities for threat actors. Most organizations depend on a combination of commercial and custom-developed hardware and software products to support their Organizations that develop their own in-house software should information technology (IT) needs. These technology components use security by design techniques to avoid creating vulnerabilities. inevitably include vulnerabilities in their design, setup, or the code that For more information on assessing overall data security risks and runs them. -

Malware Risks and Mitigation Report
MALWARE RISKS AND MITIGATION REPORT June 2011 BITS A DIVISION OF THE FINANCIAL SERVICES ROUNDTABLE 1001 PENNSYLVANIA AVENUE NW SUITE 500 SOUTH WASHINGTON, DC 20004 202-289-4322 WWW.BITS.ORG BITS Malware Risk and Mitigation Report Table of Contents 1. Executive Summary ..............................................................................................................3 2. Malware Evolution................................................................................................................3 2.1 Malware Categories...............................................................................................................................5 2.2 Malware Example .................................................................................................................................8 2.3 Polymorphic Malware ........................................................................................................................10 3. Malware Supply and Demand ............................................................................................ 10 3.1 The Malware Industry ........................................................................................................................11 3.2 Malware Supply Chain........................................................................................................................13 3.3 Beyond Crime......................................................................................................................................14 4. Malware in Financial -

Emerald 5 Administrator Guide
Emerald Administrator’s Guide Version 5.0.85 Emerald Management Suite IEA Software, Inc. Emerald v5 – Administrator’s Guide 1 IEA Software, Inc. Software License Agreement By purchasing or installing all or part of the Emerald Management Suite, you indicate your acceptance of the following License Agreement. Ownership of Software You acknowledge and agree that the computer program(s) and associated documentation contained with the Emerald Management Suite (collectively, the “Software”) are owned exclusively by IEA Software, Inc. and/or its licensors. The Software contained in the package is protected under copyright laws and all copyright and other intellectual property rights relating to the Software are and remain the exclusive property of IEA Software, Inc. and/or its licensors. You may not rent or lease the Software, but you may transfer the Software and accompanying materials on a permanent basis provided you retain no copies and the recipient agrees to the terms of this Agreement. License IEA Software, Inc. grunts to you, and you accept, a limited, non- exclusive and revocable license to use the Software. You agree to use the Software in machine-readable object code form only as authorized in this License Agreement. This License Agreement does not convey any title or interest in the Software to you. You may only use the licensed number of Master Billing Records (MBRs) with the Software as stated in your purchase agreement. Scope of License You may not make any changes or modifications to the Software, and you may not decompile, disassemble, or otherwise reverse engineer the Software. You may not load, rent, lease or sublicense the Software or any copy to others for any purpose. -

9.1 Mailsite Reviewer's Guide
MailSite Reviewer’s Guide End User Reviewer’s Guide Revision 3 21st October 2014 Rockliffe Systems 1901 South Bascom Avenue Campbell, CA95008 Main: (408) 879-5600 Fax: (408) 879-5610 www.rockliffe.com ©2014 Rockliffe Systems Incorporated Table of Contents 1 Introduction ............................................................................................................................................................... 3 2 Company Overview .................................................................................................................................................. 3 3 Mailsite Package ...................................................................................................................................................... 3 4 MailSite Product Highlights ...................................................................................................................................... 4 5 Installing MailSite ..................................................................................................................................................... 5 6 Installing MailSite SE, LE, and SP ......................................................................................................................... 6 7 Reviewing MailSite ................................................................................................................................................. 12 8 Summary ............................................................................................................................................................... -

SMTP Reply Codes Reference & List
AnswersThatWorkTM SMTP Status codes – SMTP Error Codes – SMTP Reply Codes SMTP Status Codes & SMTP Error Codes Reference There comes a time in the life of a Computer Consultant where, one day, he/she will have to deal with email server problems. It is inevitable. Sometimes these problems will be with the interfacing of the mail server with the ISP, in particular an inability to send mail. After checking the usual suspects such as lack of connection (your broadband line is dead), faulty router, firewall problems, DNS problems, or an incorrect SMTP server name (thanks to some clever ISP changing its SMTP server name without informing anyone – it happens!!), you will likely start delving a little deeper by checking if your email server reports any errors. Depending on the actual problem it is encountering, your mail server may not be able to provide detailed help on how to resolve the problem, and may instead only be able to provide you with an SMTP Status Code in your server’s log (these codes are also known as SMTP Error Codes or SMTP Reply Codes). It is just for such cases that we have produced this document (we use it too !! J ). So, use this document as a quick reference to common SMTP status codes or SMTP error codes for SMTP mail servers such as AA Mail Server, Alt-N MDaemon, ArGoSoft Mail Server, Axigen Mail Server, Barracuda Spam Firewall, CMail, CMailServer, E-Mail Anywhere, FTGate, GMS Mail, Internet Anywhere, Kerio MailServer (KMS), Lotus Notes, MailEnable, MailMax, Mailtraq, Merak Mail Server, Microsoft Exchange (Exchange Server 2003 NDR, Non-Delivery Report, error codes), Novell GroupWise, Qmail, PostCast Server, PostConf, PostFix, PowerMTA, QK SMTP Server, Rockliffe MailSite, SendMail, SurgeMail, TFS Secure Message Server, VisNetic Mail Server, WinMail, Zimbra, or any other SMTP / ESMTP standards compliant e-mail MTA. -

Mailsite® Expresspro
DATA SHEET MailSite® ExpressPro MailSite ExpressPro is WHAT IS IT? WHAT’S NEW? a state-of-the-art web MailSite ExpressPro is a state-of-the-art web MailSite ExpressPro is a totally new client for managing client for managing email, calendars and contacts product written from the ground up using email, calendars and that has been built using the latest AJAX the latest AJAX web technology. MailSite contacts built using technology. MailSite ExpressPro has the look and ExpressPro allows users to manage their the latest AJAX feel of Outlook, so users that are familiar with personal email, calendars and contacts Outlook will be right at home. from a web browser. technology MICROSOFT OUTLOOK 2007 CALENDAR SHARING MailSite ExpressPro can be configured to MailSite ExpressPro allows users to automatically synchronize Calendar and Contact subscribe to remote calendars such as data with Outlook 2007. This means that the Google Calendars. It also allows users to user’s email, calendar and contact data is always share their own calendars with others available from any web browser anywhere in the who use clients such as Apple Mac iCal, world. Mozilla Lightning and Google Calendar. Users can share all of their calendar details or just their free-busy information. FULL FEATURED ExpressPro includes support for right-click and drag-and-drop functionality just like a desktop client. ExpressPro comes with support for 18 languages. Administrators can use the default “skins” or can create their own “skins” to brand the user interface to match the rest of their website. Users can even select a ”skin” to suit their own taste. -

Messaging Platforms for Service Providers - Market Quadrant 2017 ∗
. The Radicati Group, Inc. www.radicati.com . THE RADICATI GROUP, INC. Messaging Platforms for Service Providers - Market Quadrant 2017 ∗ ........ An Analysis of the Market for Messaging Platforms for Service Providers, Revealing Top Players, Trail Blazers, Specialists and Mature Players. June 2017 SM ∗ Radicati Market Quadrant is copyrighted June 2017 by The Radicati Group, Inc. Reproduction in whole or in part is prohibited without expressed written permission of the Radicati Group. Vendors and products depicted in Radicati Market QuadrantsSM should not be considered an endorsement, but rather a measure of The Radicati Group’s opinion, based on product reviews, primary research studies, vendor interviews, historical data, and other metrics. The Radicati Group intends its Market Quadrants to be one of many information sources that readers use to form opinions and make decisions. Radicati Market QuadrantsSM are time sensitive, designed to depict the landscape of a particular market at a given point in time. The Radicati Group disclaims all warranties as to the accuracy or completeness of such information. The Radicati Group shall have no liability for errors, omissions, or inadequacies in the information contained herein or for interpretations thereof. Messaging Platforms for Service Providers - Market Quadrant 2017 TABLE OF CONTENTS RADICATI MARKET QUADRANTS EXPLAINED .................................................................................. 2 MARKET SEGMENTATION – MESSAGING PLATFORMS FOR SERVICE PROVIDERS ............................ -

Outlook, Lotus Notes, Groupwise, Netscape Windows Platforms
Skills: Email Applications: Outlook, Lotus Notes, GroupWise, Netscape Windows Platforms: Windows 7, Windows 9x, NT, 2000, 2003, XP, Vista Windows Applications: Office 2010, Word, Excel, Power Point, Access Law Applications: Filesite 8.0, Mailsite, Interwoven, iManage Desksite 6.5, Pro Law, Hummingbird Document Management system, Portable 32, Crosswords, iCreate, i Scrub, iRedline and iDocID macro system, Hotdocs, Hotdocs PDF, LegalKEY Records, Intem, Enhanced Time Entry, Juris, Taxdocs, Deltaview, Redax, ISYS, Lexis Nexis , West Law, Ecopy, TraxOpen, LegalKey, AIM, IP Master, Perfect Law Document mana gement system Other Applications: Word Perfect 12, Adobe Professional, Visio, Micromedia Dre am Weaver 3, Xvision, Crystal Reports, Photofinish, HummingBird Exceed, NFS Mes tro, Citrix Neighborhood, Expert Advicer, Form Flow, Infoflow, Meeting Maker, Me ssage Manager, Stars, Remis, Call link, Act, Slick, Sequencer, Abra, Spotfire, G lovia, DCAMS, Reflections/MANMAN, ManageSoft, iNet, Softwise MacroSuite, Swiftwr iter, WestCheck 4.52, InterAction 5, Summation Blazer, Intelli-sync, Handspring, Constructware, Optika, Acorde, JDE, BizFlow, MS Office Communicator, Reference Manager, Endnote; Print Key; Suddan; SAS; TABS32; Sharepoint; File Maker Pro, F rontpage, ISAIC, Sunflower, Quosa, Sudaan; Pointsec for PC's, Symantec Ghost , Backup Exec, SharePoint 2007 Remote Software: Citrix, RAS, VPN, VNC, DSL, Dialup, Desktop Authority, NetOp R emote Control, Internet, Intranet, PC Anywhere, Net Meeting, Alta Vista Tunnel, Internet Service Providers, -
EAI Readiness in Tlds
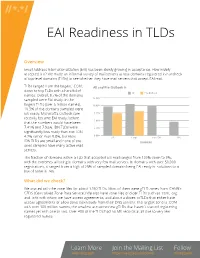
EAI Readiness in TLDs Overview Email Address Internationalization (EAI) has been slowly growing in acceptance. How widely accepted is it? We made an informal survey of mail servers across domains registered in hundreds of top-level domains (TLDs) to see whether they have mail servers that accept EAI mail. TLDs ranged from the largest, .COM, All and Pre-Outlook % down to tiny TLDs with a handful of All Pre-Outlook names. Overall, 9.7% of the domains sampled were EAI ready. In the 12.50% largest TLDs (over a million names), 10.00% 10.5% of the domains sampled were EAI ready. Microsoft’s Outlook.com 7.50% recently became EAI ready; before 5.00% that the numbers would have been 7.41% and 7.93%. IDN TLDs were 2.50% significantly less ready than non-IDN, 0.00% 4.7% rather than 9.8%, but most All Large non-IDN IDN IDN TLDs are small and none of the DOMAINS ones sampled have many active mail servers. The fraction of domains within a TLD that accepted EAI mail ranged from 100% down to 0%, with the extremes all being in domains with very few mail servers. In domains with over 50,000 registrations, it ranged from a high of 25% of sampled domains being EAI ready in .solutions to a low of none in .ren. What did we check? We started with the zone files for about 1250 TLDs. Most of them were gTLD zones from ICANN’s CZDS (Centralized Zone Data Service.) We also have zone files of older TLDs such as .com, .org, and .info with whom we have access agreements, and about a dozen ccTLDs that either have access agreements or allow zone downloads from their DNS servers. -

Vulnerability Management in Software: Before Patch Tuesday KYMBERLEE PRICE BUGCROWD Whoami?
Vulnerability Management in Software: Before Patch Tuesday KYMBERLEE PRICE BUGCROWD whoami? Senior Director of a Red Team PSIRT Case Manager Data Analyst Internet Crime Investigator Security Evangelist Behavioral Psychologist @kym_possible Vulnerability Management Vulnerability management is the "cyclical practice of identifying, classifying, remediating, and mitigating vulnerabilities", especially in software and firmware. Vulnerability management is integral to computer security and network security. Vulnerabilities can be discovered with a vulnerability scanner, which analyzes a computer system in search of known vulnerabilities, such as open ports, insecure software configuration, and susceptibility to malware. Unknown vulnerabilities, such as a zero-day attack may be found with fuzz testing, which can identify certain kinds of vulnerabilities, such as a buffer overflow exploit with relevant test cases. Such analyses can be facilitated by test automation. In addition, antivirus software capable of heuristic analysis may discover undocumented malware if it finds software behaving suspiciously (such as attempting to overwrite a system file). Correcting vulnerabilities may variously involve the installation of a patch, a change in network security policy, reconfiguration of software (such as a firewall), or educating users about social engineering. So Vuln Mgmt is A NetSec Issue! Cost to Fix Vulnerabilities The National Institute of Standards and Technology (NIST) estimates that code fixes performed after release can result in -

Attackers and Their Tools Who Is Attacking Our Network? in This Presentation We Will Investigate Threat, Vulnerability, and Risk
Principles of Cyber Security Attackers and Their Tools Who is Attacking Our Network? In this presentation we will investigate Threat, Vulnerability, and Risk . Threat • Is a potential danger to an asset such as data or the network. Vulnerability and Attack Surface • A vulnerability is a weakness in a system or its design that could be exploited by a threat. • Attack surface describes different points where an attacker could get into a system and could get to the data (Example – operating system without security patches) . Exploit • Is a mechanism used to leverage a vulnerability to compromise an asset. • A Remote exploit works over the network. • A Local exploit is when a threat actor has user or administrative access to the end system. Risk • Likelihood that a threat will exploit a vulnerability of an asset and result in an undesirable consequence. © 2016 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 2 Who is Attacking Our Network? What exactly are Hackers? Hacker vs. Threat Actor . White Hat Hackers • Ethical hackers who use their programming skills for good, ethical, and legal purposes. • Perform penetration tests to discover vulnerabilities and work with developers to address cyber issues . Grey Hat Hackers • Commit crimes and do unethical things but not for personal gain or to cause damage. Black Hat Hackers • Unethical criminals who violate security for personal gain, or for malicious reasons, such as attacking networks. It is important to note: Threat actors is a term used to describe grey and black hat hackers. © 2016 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 3 Who is Attacking Our Network? Evolution of Threat Actors .