Risk of Processes and Their Management
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

ˇcısla Z Prvnı Ruky Praha
C´ıslazˇ prvn´ıruky Praha - 2013 Ceskˇ y´ statisticky´ u´radˇ 2014 Dostupny´ z http://www.nusl.cz/ntk/nusl-203630 D´ılo je chran´ enoˇ podle autorskeho´ zakona´ c.ˇ 121/2000 Sb. Tento dokument byl stazenˇ zN arodn´ ´ıho ulo´ ziˇ stˇ eˇ sedˇ e´ literatury (NUSL)ˇ . Datum stazenˇ ´ı: 04.10.2021 Dalsˇ´ı dokumenty mu˚zeteˇ naj´ıt prostrednictvˇ ´ım vyhledavac´ ´ıho rozhran´ı nusl.cz. FIRST HAND FIGURES 2013 PRAGUE www.praha.czso.cz Code: 330123-14 Prepared by: Regional Offi ce of the Czech Statistical Offi ce in the Capital City of Prague, Information Services Department Prague, June 2014 Contact person: Marcela Píšová phone: +420 274 052 507 e-mail: [email protected] Send your orders to: Czech Statistical Offi ce, Information Service Unit Na padesátém 81, 100 82 Praha 10 Fax: +420 274 054 070 e-mail: [email protected] ISBN 978-80-250-2550-5 Ref. no.: 0487/2014 - 7101 © Czech Statistical Offi ce, Prague, 2014 INTRODUCTORY OVERVIEW CONTACTS Regional Office of the Czech Statical Office Area km2 496 in the Capital City of Prague Altitude – Maximum (Zličín) m 399 Information Services Department – Minimum (Suchdol) m 177 e-mail: [email protected] Number of administrative districts 22 Head of Section: Tomáš Mládek Number of city sections 57 phone: +420 274 052 673, e-mail: [email protected] Number of cadastral districts 112 Link for Queries in English Number of basic settlement units 916 Pavla Tuháčková Mid-year population, 1 July persons 1 244 762 phone: +420 274 054 223, e-mail: [email protected] Density of population pers./km2 2 506 Information Services at Headquarters of the CZSO Life expectancy at birth – Males years 77.3 phone: +420 274 052 304, +420 274 052 451 – Females years 82.1 e-mail: [email protected] Average registered number Providing Information, Introductory Consultations, Making Orders of employees1) (thousands) FTE equiv. -

Prague Participatory Budget
PRAGUE PARTICIPATORY BUDGET CASE STUDY REPORT & ANALYSIS Prepared by AGORA CE Author: Vojtěch Černý The publication is a result of the project ”Participatory Budgeting for Sustainable Development of V4 Capital Cities” supported by International Visegrad Fund. Project coordinator: Collegium Civitas, Warsaw, Poland Partners of the project: Mindspace - Budapest, Agora CE - Prague, Utopia - Bratislava, Inicjatywy - Warsaw 2 This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license 3 This publication reflects the views only of the authors, and the IVF cannot be held responsible for any use which may be made of the information contained therein. CONTENTS Preface ..................................................................................................................................................... 5 Prague – main facts about the city .......................................................................................................... 6 Origins of PB in Prague ............................................................................................................................ 8 Development of the Participative Budget(s) in Prague ......................................................................... 15 Preparation of the PB procedure ...................................................................................................... 16 Participatory budgeting ..................................................................................................................... 19 -
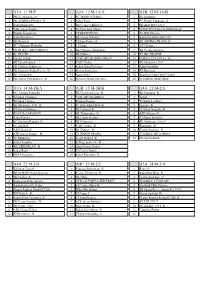
A1a 11 M-P A2a 12 M-1A/A A2b 13 M-1A/B A3a 14 M-1B/A A3b 15 M-1B
A1A 11 M-P A2A 12 M-1A/A A2B 13 M-1A/B 1 FK Újezd nad Lesy 1 FC TEMPO PRAHA 1 SK Modřany 2 FK ADMIRA PRAHA B 2 Sokol Troja 2 FC Přední Kopanina B 3 Sokol Kolovraty 3 SK Čechie Uhříněves 3 FK ZLÍCHOV 1914 4 AFK Slavoj Podolí 4 FC Háje Jižní Město 4 SPORTOVNÍ KLUB ZBRASLAV 5 Přední Kopanina 5 TJ BŘEZINĚVES 5 TJ AFK Slivenec 6 Sokol Královice 6 SK Union Vršovice 6 Sportovní klub Libuš 838 7 SK Hostivař 7 TJ Kyje Praha 14 7 SK ARITMA PRAHA B 8 SC Olympia Radotín 8 TJ Praga 8 1999 Praha 9 FK DUKLA JIŽNÍ MĚSTO 9 SK Viktoria Štěrboholy 9 SK Čechie Smíchov 10 FC ZLIČÍN 10 SK Ďáblice 10 TJ ABC BRANÍK 11 Uhelné sklady 11 TJ SPARTAK HRDLOŘEZY 11 LOKO VLTAVÍN z.s. B 12 SK Újezd Praha 4 12 ČAFC Praha 12 SK Střešovice 1911 13 FK Viktoria Žižkov a.s. 13 Sokol Dolní Počernice 13 Sokol Stodůlky 14 FK Motorlet Praha B s.r.o. B 14 Slovan Kunratice 14 FK Řeporyje 15 SK Třeboradice 15 Spoje Praha 15 Sportovní klub Dolní Chabry 16 FK Slavoj Vyšehrad a.s. B 16 Xaverov Horní Počernice 16 TJ SOKOL NEBUŠICE A3A 14 M-1B/A A3B 15 M-1B/B A4A 21 M-2/A 1 FC Tempo Praha B 1 FK Újezd nad Lesy B 1 SK Modřany B 2 TJ Sokol Cholupice 2 TJ SPARTAK KBELY 2 Točná 3 TJ Sokol Lipence 3 Partisan Prague 3 TJ Sokol Lochkov 4 SK Střešovice 1911 B 4 FC Háje Jižní Město B 4 Lipence B 5 TJ Slovan Bohnice 5 SK Hostivař B 5 TJ Sokol Nebušice B 6 TJ AVIA ČAKOVICE 6 SK Třeboradice B 6 AFK Slivenec B 7 Sokol Písnice 7 FK Union Strašnice 7 TJ Slavoj Suchdol 8 SC Olympia Radotín B 8 FK Klánovice 8 SK Střešovice 1911 C 9 FC Zličín B 9 ČAFC Praha B 9 Řeporyje B 10 ABC Braník B 10 SK Ďáblice -

GUIDELINES for the Land Use Plan for the Capital City of Prague Approved 9.9.1999, by the Capital City of Prague City Hall Resolution No
GUIDELINES for the Land Use Plan for the Capital City of Prague approved 9.9.1999, by the Capital City of Prague City Hall Resolution no. 10/05 Complete text as at 1.11.2002 Prague City Hall CCP Development Authority Section 10.2002 CONTENTS PART I. – PRELIMINARY PROVISIONS 3 1. GUIDELINES 3 1.1. BREAKDOWN OF THE LAND USE PLAN ACCORDING TO ITS MANDATORY NATURE 3 1.1.1. Overview of the mandatory and directive elements of the functional and spatial arrangement in the graphical part of the LUP 4 PART II. – MANDATORY PART 12 1. EXPLANATION OF TERMS 12 1.1. CONSTRUCTION PERMITTED UNDER EXCEPTIONAL CIRCUMSTANCES 12 1.2. HISTORICAL GARDENS 12 1.3. GREEN (PARK) BELTS 12 1.4. STRUCTURES AND EQUIPMENT FOR OPERATIONS AND MAINTENANCE 12 1.5. GREENERY AS A COMPLEMENTARY FEATURE 12 1.6. FLOATING FUNCTIONAL SIGN IN A DIFFERENT FUNCTIONAL AREA 12 2. TRANSFER OF SIGNS, SYMBOLS, CODES AND GREEN SPACES 12 2.1. VALUABLE GREENERY REQUIRING SPECIAL PROTECTION (•) 12 2.2. “HISTORICAL GARDENS” SYMBOL ( ) 12 2.3. “GARDEN PLOTS” SYMBOL ( ) 12 2.4. “VINEYARD” SYMBOL ( ) 12 2.5. “CEMETERY” SYMBOL ( ) 12 2.6. HISTORICAL GARDENS, PARKS AND LANDSCAPED AREAS” SIGN ( PP ) 12 located in another existing functional area 2.7. HISTORICAL GARDENS, PARKS AND LANDSCAPED AREAS” SIGN ( PP ) 12 located in the development functional area 3. NATURE CONSERVATION ZONES IN BUILT-UP AREAS 13 3.1. AREAS WITH PROTECTION FOR VALUABLE GREEN SPACES 13 4. LAND USE RATE 13 4.1. MINIMUM HOUSING SHARE 13 5. MAJOR DEVELOPMENT AREA (MDA) 13 5.1. -

Vyhodnocení Urbanistických Hodnot Jihozápadní Části Prahy (MO Praha 5)
Vysoká škola regionálního rozvoje a Bankovní institut – AMBIS Management rozvoje měst a regionů Vyhodnocení urbanistických hodnot jihozápadní části Prahy (MO Praha 5) Diplomová práce Autor: Bc. David Poduška Management rozvoje měst a regionů Vedoucí práce: prof. Ing. arch. ThLic. Jiří Kupka, Ph.D. Praha Rok 2020 Prohlášení Prohlašuji, že jsem diplomovou práci zpracoval samostatně a v seznamu uvedl veškerou použitou literaturu. Svým podpisem stvrzuji, že odevzdaná elektronická podoba práce je identická s její tištěnou verzí, a jsem seznámen se skutečností, že se práce bude archivovat v knihovně VŠ AMBIS a dále bude zpřístupněna třetím osobám prostřednictvím interní databáze elektronických vysokoškolských prací. V Praze dne 26.04.2020 Poděkování Tímto bych chtěl poděkovat především vedoucímu mé diplomové práce, prof. Ing. arch. ThLic. Jiřímu Kupkovi Ph.D., za odborné vedení diplomové práce, cenné rady a čas, který mi věnoval v průběhu příprav a zpracování diplomové práce. Anotace Diplomová práce se zabývá zmapováním a vyhodnocením urbanistických hodnot historických jader obcí (původní venkovská sídla) v jihozápadní části Prahy, spadajících pod městskou část Praha 5, Praha-Slivenec, Praha 13, Praha-Řeporyje, Praha 16, Praha-Lipence, Praha-Lochkov, Praha-Velká Chuchle, Praha-Zbraslav, Praha-Zličín, která se v průběhu 20. století postupně připojovala k Praze. Vybrané území Prahy bylo osidlováno od doby kamenné přes období středověku, novověku, 19. století, začátku 20. století až po současnost. Každé z těchto období mělo na vybranou lokalitu určitý vliv, kdy dosahovalo takového rozsahu, že urbanistické hodnoty v těchto lokalitách byly dochovány dodnes. Hlavními zdroji k zmapování a vyhodnocení urbanistických hodnot dané části Prahy je literatura o Praze společně s literaturou zaměřující se na dané lokality, mapové podklady, vlastní terénní průzkum a územně analytické podklady hl. -

Heat in Shape
HEAT IN SHAPE ISAN OFFERS CUSTOM-BUILT S HEATING UNITS IT We are a Czech manufacture with a history on the heating unit market dating back to 1953. We offer several product ranges of heating units, such as bathroom radiators, design radiators, floor convectors and lamellar N radiators, tube and finned radiators. U MARKET DEVELOPMENT Our specialists are keeping abreast of the trends and new market requirements, implementing them in the existing manufacturing programmes. Together with development specialists, ISAN’s technicians permanently seek for new way of bringing innovative and original solutions. Our key objective NG is to provide our customers with further possibilities and functional designs that will contribute to their quality of life and housing. QUALITY Quality of all products and their accessories on offer is our primary concern. The whole manufacturing and development has been certified in accordance with the ISO 9001:2008 system. Furthermore, all heating units comply with the certification requirements of individual states so that they meet even the most stringent quality criteria. ECOLOGY Nowadays every manufacture is required to follow ecological principles of production. ISAN has incorporated these principles directly into its manufacturing guidelines, considering them as common practice. At the same time, we also constantly attempt to develop and find new solutions leading to energy savings and thus environment protection. M-BUILT HEATI M-BUILT DESIGN AND CUSTOMISED O PRODUCTION The customer requires not only the classical function of heating units but we have also installed, with a growing frequency, radiators intended as powerful, yet design accessories in interiors. They are intended to complement the overall visual aspect of the space. -

In Heaven and on Earth: Church Treasure in Late Medieval Bohemia
In Heaven and on Earth: Church Treasure in Late Medieval Bohemia by Kateřina Horníčková Submitted to Central European University Department of Medieval Studies in partial fulfilment of the requirements for the degree of Doctor of Philosophy Supervisor: Gerhard Jaritz Budapest, Hungary 2009 CEU eTD Collection - i- Table of content Acknowledgements.................................................................................................................................. iv Plates on CD ROM ................................................................................................................................... v Maps.................................................................................................................................................... vii Abbreviations......................................................................................................................................... viii Foreword ................................................................................................................................................... 1 Part I – Treasures of churches in prospective ............................................................................... 3 I. The Medieval Treasure as a Research Subject ...................................................................................... 3 1. The Treasure in Medieval Culture .................................................................................................... 3 2. The Treasury, the Church and the Public......................................................................................... -

In Czech Republic: • 89 Towns and Cities • 269 Polls in D21 App LESSONS from CZECH EXPERIENCE
Lessons from Czech experience LESSONS FROM CZECH EXPERIENCE D21 is a civic tech-advisory enterprise which powers consensus decision-making for individuals and communities in cities, organizations, and businesses. • D21 has developed a suite of online products featuring its hallmark state of the art voting methodology. • Our multi-disciplinary team consists of 35 people in Prague, Paris and New York using expertise in policy design and stakeholder engagement for projects with cities, schools, civil society, and governemnts worldwide. • We have worked on more than 263 projects on 3 different continents, engaging over 630 000 participants and voters. LESSONS FROM CZECH EXPERIENCE D21 • Reasearch project > business enterprise > NGO • Pioneers of participation in CZ • Using unique D21 voting system • Our own D21 app In Czech republic: • 89 towns and cities • 269 polls in D21 app LESSONS FROM CZECH EXPERIENCE Vote 21 We believe that traditional forms of voting built on a binary logic generate frustration among voters. For this reason, we have developed a voting system that enables voters to cast votes for and against multiple options. This (optional) approach makes it possible to quickly identify points of consensus and controversy and refine the policies and response measures based on the public opinion. PARTICIPATION IN CZ: DEVELOPMENT 1H 2017 LESSONS FROM CZECH EXPERIENCE Participation in CZ: Development • 2014 – first attempts • 2016 – first succesful projects • 2017 – PB organized by more than 40 municipalities • 2018 – number increases -
Základní Informace O Obcích Čr
republika kraj okres město SČÍTÁNÍ LIDU, DOMŮ A BYTŮ K 1. 3. 2001 ZÁKLADNÍINFORMACE O OBCÍCH ČR Hlavní město Praha Český statistický úřad OBYVATELSTVO Ročník 2003 SLDB Praha, 30. května 2003 Kód publikace: e - 4108 - 03 Č.j.: 622 / 03 - 3320 Sčítání lidu, domů a bytů k 1. 3. 2001 - základní informace o obcích Hlavní město Praha Zpracoval: Odbor populačních cenzů Ředitelka odboru: Ing. Jiřina Růžková, CSc. Kontaktní zaměstnanec: Ing. Josef Škrabal, tel.: 241019175, e-mail: [email protected] Ing. Štěpánka Morávková, tel.: 241019177, e-mail: [email protected] Český statistický úřad 2003 Zajímají Vás nejnovější údaje o inflaci, HDP, obyvatelstvu, průměrných mzdách a mnohé další? Najdete je na stránkách ČSÚ na Internetu: www.czso.cz ISBN: 80-7223-965-1 © Český statistický úřad, Praha 2003 OBSAH Strana ÚVOD............................................................................................................................................................................................ 7 METODICKÉ VYSVĚTLIVKY ....................................................................................................................................................... 9 TABULKOVÁ ČÁST Hlavní město Praha ..............................................................................................................................................................................................................14 Okres Praha 1 ........................................................................................................................................................................................................................18 -

Information About Wood & Company Financial Services, A.S
INFORMATION ABOUT WOOD & COMPANY FINANCIAL SERVICES, A.S. Information about the Company WOOD & Company Financial Services, a.s. (“Company”) with a registered address at Palladium, náměstí Republiky 1079/1a, 110 00 Praha 1, Czech Republic, identification number 26503808. The day of entry into the Companies Register was February 1st 2002, the date of last amendment in the company register was September 6th 2018 and the reason of the amendment was termination of SB membership of Mr. Slavomír Veselý and a new Supervisory Board membership of Mr. Jiří Jirman. The value of the Company's registered stock is CZK 445,500,000 which consists of 198,000 registered shares in the nominal value of CZK 2,250.00 per share. The stock was paid up to 100%. Organisation Structure of the Company WOOD & Company Financial Services, a.s., Palladium, nám. Republiky 1079/1a, 110 00 Praha 1, IČ: 26503808; zapsaná v obchodním rejstříku vedeném rejstříkovým soudem v Praze, spis. zn. B 7484 Information about the Members of Board of Directors and Supervisory Board Board of Directors: Chairman of the Board: Jan Sýkora Prague 1, V Kolkovně 4 Start of performance: 1st February 2018 Deputy Chairman of the Board: Vladimír Jaroš Prague 4, Braník, Nad lomem 1189/33 Start of the membership: 1st February 2018 Member of the Board: Lubomír Šoltýs 85110 Bratislava, Starorímská 1360/14 Slovakia Start of the membership: 1st February 2018 Supervisory Board: Chairman of the Supervisory Board: Jiří Jirman Nová Lipová 609, 251 69 Velké Popovice Start of performance: 6th September 2018 Member of the Supervisory Board: Vojtěch Láska Jantarová 950/18, Slivenec, 154 00 Praha 5 Start of performance: 1st February 2018 Member of the Supervisory Board: Marek Herold Za kovárnou 422/19, Dolní Měcholupy, 109 00 Praha 10 Start of performance: 12th December 2016 Information about the Audit Committee The Company hereby proclaims that, under Section 44 (7) of Act No. -

04/26 Výstavba Silničního Okruhu Kolem Hlavního Města Prahy
Částka 2 Věstník Nejvyššího kontrolního úřadu 2005 Strana 231 04/26 Výstavba silničního okruhu kolem hlavního města Prahy Kontrolní akce byla zařazena do plánu kontrolní činnosti Nejvyššího kontrolního úřadu (dále jen „NKÚ“) na rok 2004 pod číslem 04/26. Kontrolní akci řídil a kontrolní závěr vypracoval člen NKÚ Ing. Jiří Adámek. Cílem kontroly bylo prověřit hospodaření s prostředky určenými na přípravu a výstavbu silničního okruhu kolem hlavního města Prahy. Kontrolováno bylo období od roku 2002 do doby ukončení kontroly. V případě věcných souvislostí i předchozí období. Kontrolu provedla od 9. 8. 2004 do 11. 2. 2005 skupina kontrolujících NKÚ z odborů dopravy, průmyslu a hospodářství a životního prostředí a zemědělství. Kontrolované osoby: – Ministerstvo dopravy (dále jen „MD“); – Státní fond dopravní infrastruktury (dále jen „SFDI“); – Ředitelství silnic a dálnic ČR (dále jen „ŘSD“). Námitky proti kontrolnímu protokolu, které podalo ŘSD, byly vypořádány vedoucím skupiny kontrolujících rozhodnutím o námitkách. O odvolání proti rozhodnutí o námitkách, které podalo ŘSD, rozhodl senát NKÚ usnesením. S e n á t NKÚ (ve složení: Ing. Jiří Adámek – předseda, Mgr. Ing. Jiří Kalivoda, Ing. Josef Pohl, Ing. Petr Skála – členové) na svém zasedání konaném dne 10. května 2005 s c h v á l i l usnesením č. 04/26/34 k o n t r o l n í z á v ě r v tomto znění: I. Úvod Okruh kolem hlavního města Prahy (dále jen „hl. m. Praha“) je pozemní komunikací dálničního typu. Je součástí transevropské dálniční sítě IV. multimodálního koridoru Berlín – Istanbul. Okruh je realizován v rámci programů 227 270 „Výstavba silničního okruhu kolem hlavního města Prahy, část jihozápadní“ a 327 270 „Výstavba dálničního okruhu hlavního města Prahy“. -

Lochkovský Fotbal 10.11.2012
rrroočččnníííkkk XX... /// 777 wwwwww...sssookkkoolllllooccchhkkkoovvv...ccczzz 111000...111111...222000111222 Vstupné 25,- Kč, tento program platí zároveň jako vstupenka na fotbalové utkání. Foto: Starší přípravka, Modřany – Lochkov, září 2012 MISTROVSKÉ FOTBALOVÉ UTKÁNÍ II. TŘÍDA – SKUPINA A - 10. KOLO SOKOL LOCHKOV – FK ŘEPORYJE B SOBOTA 10.11.2012 OD 14:00 Hlavní rozhodčí: Martin Bužo ROZPIS ZÁPASŮ – PODZIM 2012 PODZIM 2012 – II.TŘÍDA – SKUPINA A 10.kolo SO 10.11.2012 14:00 Sokol Lochkov – FK Řeporyje B Lochkov T. 11.kolo SO 17.11.2012 13:30 AFK Slivenec B - Sokol Lochkov Slivenec T. VÝSLEDKY A MUŽSTVA – podzim 2012 – II. třída – skupina A Výsledky 6. Kola Sokol Řepy B – AFK Slivenec B 3:3 (2:1), Sokol Lochkov – SK Zbraslav B 4:4 (2:1), SK Modřany B – PSK Olymp 3:0 (1:0), Sokol Nebušice B – SK Střešovice C 1:0 (0:0), FK Řeporyje B – Gordic Kačerov 1:3 (1:0), ČZU Praha – Sokol Lipence B 9:1 (5:0) Výsledky 7. kola Sokol Lipence B – Sokol Lochkov 4:2 (3:0), AFK Slivenec B – SK Modřany B 2:1 (1:0), Gordic Kačerov – Sokol Řepy B 4:0 (1:0), SK Zbraslav B – Sokol Nebušice B 4:3 (2:3), PSK Olymp – ČZU Praha 1:5 (0:1), SK Střešovice C – FK Řeporyje B 4:2 (3:0) Výsledky 8. kola SK Modřany B – Gordic Kačerov 4:2 (1:1), Sokol Lipence B – PSK Olymp 3:1 (3:0), SK Střešovice C – Sokol Řepy B 2:1 (1:1), ČZU Praha – AFK Slivenec B 3:1 (2:1), FK Řeporyje B – SK Zbraslav B 1:1 (0:0), Sokol Lochkov – Sokol Nebušice B 1:0 (0:0) Výsledky 9.