PBFT Vs Proof-Of-Authority: Applying the CAP Theorem to Permissioned Blockchain ∗
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Smart Methods for Retrieving Physiological Data in Physiqual
University of Groningen Bachelor thesis Smart methods for retrieving physiological data in Physiqual Marc Babtist & Sebastian Wehkamp Supervisors: Frank Blaauw & Marco Aiello July, 2016 Contents 1 Introduction 4 1.1 Physiqual . 4 1.2 Problem description . 4 1.3 Research questions . 5 1.4 Document structure . 5 2 Related work 5 2.1 IJkdijk project . 5 2.2 MUMPS . 6 3 Background 7 3.1 Scalability . 7 3.2 CAP theorem . 7 3.3 Reliability models . 7 4 Requirements 8 4.1 Scalability . 8 4.2 Reliability . 9 4.3 Performance . 9 4.4 Open source . 9 5 General database options 9 5.1 Relational or Non-relational . 9 5.2 NoSQL categories . 10 5.2.1 Key-value Stores . 10 5.2.2 Document Stores . 11 5.2.3 Column Family Stores . 11 5.2.4 Graph Stores . 12 5.3 When to use which category . 12 5.4 Conclusion . 12 5.4.1 Key-Value . 13 5.4.2 Document stores . 13 5.4.3 Column family stores . 13 5.4.4 Graph Stores . 13 6 Specific database options 13 6.1 Key-value stores: Riak . 14 6.2 Document stores: MongoDB . 14 6.3 Column Family stores: Cassandra . 14 6.4 Performance comparison . 15 6.4.1 Sensor Data Storage Performance . 16 6.4.2 Conclusion . 16 7 Data model 17 7.1 Modeling rules . 17 7.2 Data model Design . 18 2 7.3 Summary . 18 8 Architecture 20 8.1 Basic layout . 20 8.2 Sidekiq . 21 9 Design decisions 21 9.1 Keyspaces . 21 9.2 Gap determination . -

Blockchain in an Internet-Of-Things Network Based on User Participation
Blockchain in an Internet-of-Things Network Based on User Participation Robert Ljungblad Computer Science and Engineering, bachelor's level 2019 Luleå University of Technology Department of Computer Science, Electrical and Space Engineering ABSTRACT The internet-of-things is the relatively new and rapidly growing concept of connecting everyday devices to the internet. Every day more and more devices are added to the internet-of-things and it is not showing any signs of slowing down. In addition, advancements in new technologies such as blockchains, artificial intelligence, virtual reality and machine learning are made practically every day. However, there are still much to learn about these technologies. This thesis explores the possibilities of blockchain technology by applying it to an internet-of-things network based on user participation. More specifically, it is applied to a use case derived from Luleå Kommun’s wishes to easier keep track of how full the city’s trash cans are. The goal of the thesis is to learn more about how blockchains can help an internet-of-things network as well as what issues can arise. The method takes an exploratory approach to the problem by partaking in a workshop with Luleå Kommun and by performing a literature study. It also takes a qualitative approach by creating a proof-of-concept solution to experience the technology firsthand. The final proof-of-concept as well as issues that arose during the project are analysed with the help of information gathered and experience gained throughout the project. It is concluded that blockchain technology can help communication in an internet-of-things network based on user participation. -
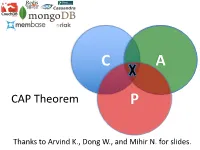
CAP Theorem P
C A CAP Theorem P Thanks to Arvind K., Dong W., and Mihir N. for slides. CAP Theorem • “It is impossible for a web service to provide these three guarantees at the same time (pick 2 of 3): • (Sequential) Consistency • Availability • Partition-tolerance” • Conjectured by Eric Brewer in ’00 • Proved by Gilbert and Lynch in ’02 • But with definitions that do not match what you’d assume (or Brewer meant) • Influenced the NoSQL mania • Highly controversial: “the CAP theorem encourages engineers to make awful decisions.” – Stonebraker • Many misinterpretations 2 CAP Theorem • Consistency: – Sequential consistency (a data item behaves as if there is one copy) • Availability: – Node failures do not prevent survivors from continuing to operate • Partition-tolerance: – The system continues to operate despite network partitions • CAP says that “A distributed system can satisfy any two of these guarantees at the same time but not all three” 3 C in CAP != C in ACID • They are different! • CAP’s C(onsistency) = sequential consistency – Similar to ACID’s A(tomicity) = Visibility to all future operations • ACID’s C(onsistency) = Does the data satisfy schema constraints 4 Sequential consistency • Makes it appear as if there is one copy of the object • Strict ordering on ops from same client • A single linear ordering across client ops – If client a executes operations {a1, a2, a3, ...}, client b executes operations {b1, b2, b3, ...} – Then, globally, clients observe some serialized version of the sequence • e.g., {a1, b1, b2, a2, ...} (or whatever) Notice -

Nosql Databases: Yearning for Disambiguation
NOSQL DATABASES: YEARNING FOR DISAMBIGUATION Chaimae Asaad Alqualsadi, Rabat IT Center, ENSIAS, University Mohammed V in Rabat and TicLab, International University of Rabat, Morocco [email protected] Karim Baïna Alqualsadi, Rabat IT Center, ENSIAS, University Mohammed V in Rabat, Morocco [email protected] Mounir Ghogho TicLab, International University of Rabat Morocco [email protected] March 17, 2020 ABSTRACT The demanding requirements of the new Big Data intensive era raised the need for flexible storage systems capable of handling huge volumes of unstructured data and of tackling the challenges that arXiv:2003.04074v2 [cs.DB] 16 Mar 2020 traditional databases were facing. NoSQL Databases, in their heterogeneity, are a powerful and diverse set of databases tailored to specific industrial and business needs. However, the lack of the- oretical background creates a lack of consensus even among experts about many NoSQL concepts, leading to ambiguity and confusion. In this paper, we present a survey of NoSQL databases and their classification by data model type. We also conduct a benchmark in order to compare different NoSQL databases and distinguish their characteristics. Additionally, we present the major areas of ambiguity and confusion around NoSQL databases and their related concepts, and attempt to disambiguate them. Keywords NoSQL Databases · NoSQL data models · NoSQL characteristics · NoSQL Classification A PREPRINT -MARCH 17, 2020 1 Introduction The proliferation of data sources ranging from social media and Internet of Things (IoT) to industrially generated data (e.g. transactions) has led to a growing demand for data intensive cloud based applications and has created new challenges for big-data-era databases. -

IBM Cloudant: Database As a Service Fundamentals
Front cover IBM Cloudant: Database as a Service Fundamentals Understand the basics of NoSQL document data stores Access and work with the Cloudant API Work programmatically with Cloudant data Christopher Bienko Marina Greenstein Stephen E Holt Richard T Phillips ibm.com/redbooks Redpaper Contents Notices . 5 Trademarks . 6 Preface . 7 Authors. 7 Now you can become a published author, too! . 8 Comments welcome. 8 Stay connected to IBM Redbooks . 9 Chapter 1. Survey of the database landscape . 1 1.1 The fundamentals and evolution of relational databases . 2 1.1.1 The relational model . 2 1.1.2 The CAP Theorem . 4 1.2 The NoSQL paradigm . 5 1.2.1 ACID versus BASE systems . 7 1.2.2 What is NoSQL? . 8 1.2.3 NoSQL database landscape . 9 1.2.4 JSON and schema-less model . 11 Chapter 2. Build more, grow more, and sleep more with IBM Cloudant . 13 2.1 Business value . 15 2.2 Solution overview . 16 2.3 Solution architecture . 18 2.4 Usage scenarios . 20 2.5 Intuitively interact with data using Cloudant Dashboard . 21 2.5.1 Editing JSON documents using Cloudant Dashboard . 22 2.5.2 Configuring access permissions and replication jobs within Cloudant Dashboard. 24 2.6 A continuum of services working together on cloud . 25 2.6.1 Provisioning an analytics warehouse with IBM dashDB . 26 2.6.2 Data refinement services on-premises. 30 2.6.3 Data refinement services on the cloud. 30 2.6.4 Hybrid clouds: Data refinement across on/off–premises. 31 Chapter 3. -

Liquidity Or Leakage Plumbing Problems with Cryptocurrencies
Liquidity Or Leakage Plumbing Problems With Cryptocurrencies March 2018 Liquidity Or Leakage - Plumbing Problems With Cryptocurrencies Liquidity Or Leakage Plumbing Problems With Cryptocurrencies Rodney Greene Quantitative Risk Professional Advisor to Z/Yen Group Bob McDowall Advisor to Cardano Foundation Distributed Futures 1/60 © Z/Yen Group, 2018 Liquidity Or Leakage - Plumbing Problems With Cryptocurrencies Foreword Liquidity is the probability that an asset can be converted into an expected amount of value within an expected amount of time. Any token claiming to be ‘money’ should be very liquid. Cryptocurrencies often exhibit high price volatility and wide spreads between their buy and sell prices into fiat currencies. In other markets, such high volatility and wide spreads might indicate low liquidity, i.e. it is difficult to turn an asset into cash. Normal price falls do not increase the number of sellers but should increase the number of buyers. A liquidity hole is where price falls do not bring out buyers, but rather generate even more sellers. If cryptocurrencies fail to provide easy liquidity, then they fail as mediums of exchange, one of the principal roles of money. However, there are a number of ways of assembling a cryptocurrency and a number of parameters, such as the timing of trades, the money supply algorithm, and the assembling of blocks, that might be done in better ways to improve liquidity. This research should help policy makers look critically at what’s needed to provide good liquidity with these exciting systems. Michael Parsons FCA Chairman, Cardano Foundation, Distributed Futures 2/60 © Z/Yen Group, 2018 Liquidity Or Leakage - Plumbing Problems With Cryptocurrencies Contents Foreword .............................................................................................................. -

Reputation Driven Dynamic Access Control Framework for Iot Atop Poa Ethereum Blockchain
Reputation Driven Dynamic Access Control Framework for IoT atop PoA Ethereum Blockchain Auqib Hamid Lonea,∗, Roohie Naaza aDepartment of Computer Science and Engineering., NIT Srinagar, Jammu and Kashmir,India,190006 Abstract Security and Scalability are two major challenges that IoT is currently fac- ing. Access control to critical IoT infrastructure is considered as top security challenge that IoT faces. Data generated by IoT devices may be driving many hard real time systems, thus it is of utmost importance to guarantee integrity and authenticity of the data and resources at the first place itself. Due to heterogeneous and constrained nature of IoT devices, traditional IoT security frameworks are not able to deliver scalable, efficient and manage- able mechanisms to meet the requirements of IoT devices. On the other hand Blockchain technology has shown great potential to bridge the missing gap towards building a truly decentralized, trustworthy, secure and scalable environment for IoT. Allowing access to IoT resources and data managed through Blockchain will provide an additional security layer backed by the strongest cryptographic algorithms available. In this work we present a rep- utation driven dynamic access control framework for IoT applications based on Proof of Authority Blockchain, we name it as Rep-ACM. In Rep-ACM framework we build two major services, one for Reputation building (for bet- ter IoT device behaviour regulations) and other for Misbehaviour detection (for detecting any Misbehaviour on object resource usage). Both of these services work in coordination with other services of proposed framework to determine who can access what and under what conditions access should be granted. -

Towards Secure Blockchains
Towards Secure Blockchains Concepts, Requirements, Assessments | EDITORIAL Editorial Blockchain is currently one of the most widely Consequently, the analysis on the following discussed topics in the area of information pages presents blockchain technology in detail technology. This technology for distributed data and extensively studies its aspects relevant to IT storage originated from the cryptocurrency security. It also assesses to what extent blockchain Bitcoin, which became famous especially due to technology is able to achieve the security prop- the record highs its market value attained in 2017. erties ascribed to it and how it may be evaluated Based on its promise of preventing manipulation within the current legal framework. of data on a purely technical level using its decen- tralised structure, offering maximum transpar- This document thus supports developers and ency and replacing intermediaries within business potential users of blockchain solutions in per- processes, many ideas for applying blockchain forming a well-founded assessment of risks technology in fairly different areas have been and in taking IT security into account from the developed in recent years. start. Furthermore, the dynamic development of blockchain technology offers the possibility Politics has also increasingly taken up blockchain of using the results of this analysis as a basis for technology. For instance, the term blockchain is future discussions on both the national and inter- used several times within the coalition agreement national level. With blockchain—as with other of the 19th election period of the German parlia- topics in IT security—the BSI thus strives to shape ment dating from 2018, and the German federal information security for government, business government has set itself the target of developing and society. -

A Big Data Roadmap for the DB2 Professional
A Big Data Roadmap For the DB2 Professional Sponsored by: align http://www.datavail.com Craig S. Mullins Mullins Consulting, Inc. http://www.MullinsConsulting.com © 2014 Mullins Consulting, Inc. Author This presentation was prepared by: Craig S. Mullins President & Principal Consultant Mullins Consulting, Inc. 15 Coventry Ct Sugar Land, TX 77479 Tel: 281-494-6153 Fax: 281.491.0637 Skype: cs.mullins E-mail: [email protected] http://www.mullinsconsultinginc.com This document is protected under the copyright laws of the United States and other countries as an unpublished work. This document contains information that is proprietary and confidential to Mullins Consulting, Inc., which shall not be disclosed outside or duplicated, used, or disclosed in whole or in part for any purpose other than as approved by Mullins Consulting, Inc. Any use or disclosure in whole or in part of this information without the express written permission of Mullins Consulting, Inc. is prohibited. © 2014 Craig S. Mullins and Mullins Consulting, Inc. (Unpublished). All rights reserved. © 2014 Mullins Consulting, Inc. 2 Agenda Uncover the roadmap to Big Data… the terminology and technology used, use cases, and trends. • Gain a working knowledge and definition of Big Data (beyond the simple three V's definition) • Break down and understand the often confusing terminology within the realm of Big Data (e.g. polyglot persistence) • Examine the four predominant NoSQL database systems used in Big Data implementations (graph, key/value, column, and document) • Learn some of the major differences between Big Data/NoSQL implementations vis-a-vis traditional transaction processing • Discover the primary use cases for Big Data and NoSQL versus relational databases © 2014 Mullins Consulting, Inc. -

Introduction to Nosql
NoSQL An Introduction Amonra IT - 2019 What is NoSQL? NoSQL is a non-relational database management systems, different from traditional relational database management systems in some significant ways. It is designed for distributed data stores where very large scale of data storing needs (for example Google or Facebook which collects terabits of data every day for their users). This type of data storing may not require fixed schema, avoid join operations and typically scale horizontally. NoSQL ● Stands for Not Only SQL ● No declarative query language ● No predefined schema ● Key-Value pair storage, Column Store, Document Store, Graph databases ● Eventual consistency rather ACID property ● Unstructured and unpredictable data ● CAP Theorem ● Prioritizes high performance, high availability and scalability NoSQL Really Means… focus on non relational, next generation operational datastores and databases…. Why NoSQL? In today’s time data is becoming easier to access and capture through third parties such as Facebook, Google+ and others. Personal user information, social graphs, geo location data, user-generated content and machine logging data are just a few examples where the data has been increasing exponentially. To avail the above service properly, it is required to process huge amount of data. Which SQL databases were never designed. The evolution of NoSql databases is to handle these huge data properly. Web Applications Driving Data Growth Where to use NoSQL ● Social data ● Search ● Data processing ● Caching ● Data Warehousing ● Logging -

Blockchain (R)Evolution
AUGUST 2018 REPORT BLOCKCHAIN (R)EVOLUTION EXPLORING THE PAST, PRESENT, AND FUTURE OF BLOCKCHAIN TECHNOLOGY BLOCKCHAIN (R)EVOLUTION INTRODUCTION Blockchain technology is generating a great deal of excitement as organizations consider its potential implications. Companies announcing blockchain-related initiatives have seen their stock prices spike, and the technology has ushered in talk of new levels of security, data fidelity, and an immutable digital ledger that can serve everything from supply chain data to financial transaction records. Since its early applications in cryptocurrency, blockchain implementations have focused on keeping data secure by ensuring integrity. But the journey of blockchain technology now stretches far beyond Bitcoin. For businesses, blockchain implementations can change the game in terms of providing a secure way to store and track transactions, and they have sparked significant investment and interest, particularly in the financial services industry. As can be expected however, the growing interest in blockchain technology has impacted both the legitimate and illicit economies. Due to its decentralized nature, cryptocurrency and the anonymity it can offer have been leveraged by cybercriminals for years. Beyond that, the growing popularity of cryptocurrency among the public has made it more than just a payment mechanism. It is now a target, as attackers are increasingly deploying cryptomining software onto computers surreptitiously to make money. Looking ahead, innovation is certain — both for cybercriminals and corporations. In this paper, we will examine the past and present uses of blockchain technology, provide an inside look at the growing focus on cryptomining by attackers, and offer predictions of how the technology will have an impact on both the corporate world and the underworld. -

A Survey of Distributed Consensus Protocols for Blockchain Networks
1 A Survey of Distributed Consensus Protocols for Blockchain Networks Yang Xiao∗, Ning Zhang†, Wenjing Lou∗, Y. Thomas Hou∗ ∗Virginia Polytechnic Institute and State University, VA, USA †Washington University in St. Louis, MO, USA Abstract—Since the inception of Bitcoin, cryptocurrencies participants. On the other hand, blockchain is also known for and the underlying blockchain technology have attracted an providing trustworthy immutable record keeping service. The increasing interest from both academia and industry. Among block data structure adopted in a blockchain embeds the hash various core components, consensus protocol is the defining technology behind the security and performance of blockchain. of the previous block in the next block generated. The use of From incremental modifications of Nakamoto consensus protocol hash chain ensures that data written on the blockchain can not to innovative alternative consensus mechanisms, many consensus be modified. In addition, a public blockchain system supports protocols have been proposed to improve the performance of third-party auditing and some blockchain systems support a the blockchain network itself or to accommodate other specific high level of anonymity, that is, a user can transact online application needs. In this survey, we present a comprehensive review and anal- using a pseudonym without revealing his/her true identity. ysis on the state-of-the-art blockchain consensus protocols. To The security properties promised by blockchain is unprece- facilitate the discussion of our analysis, we first introduce the dented and truly inspiring. Pioneering blockchain systems such key definitions and relevant results in the classic theory of fault as Bitcoin have greatly impacted the digital payment world.