Chapter 7. Commands and Arguments
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
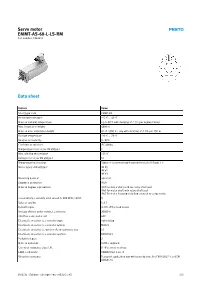
Servo Motor EMMT-AS-60-L-LS-RM Part Number: 5242213
Servo motor EMMT-AS-60-L-LS-RM Part number: 5242213 Data sheet Feature Value Short type code EMMT-AS Ambient temperature -15 °C ... 40 °C Note on ambient temperature Up to 80°C with derating of -1.5% per degree Celsius Max. installation height 4000 m Note on max. installation height As of 1,000 m: only with derating of -1.0% per 100 m Storage temperature -20 °C ... 70 °C Relative air humidity 0 - 90% Conforms to standard IEC 60034 Temperature class as per EN 60034-1 F Max. winding temperature 155 °C Rating class as per EN 60034-1 S1 Temperature monitoring Digital motor temperature transmission via EnDat® 2.2 Motor type to EN 60034-7 IM B5 IM V1 IM V3 Mounting position optional Degree of protection IP40 Note on degree of protection IP40 for motor shaft without rotary shaft seal IP65 for motor shaft with rotary shaft seal IP67 for motor housing including connection components Concentricity, coaxiality, axial runout to DIN SPEC 42955 N Balance quality G 2.5 Detent torque <1.0% of the peak torque Storage lifetime under nominal conditions 20000 h Interface code, motor out 60P Electrical connection 1, connection type Hybrid plug Electrical connection 1, connector system M23x1 Electrical connection 1, number of connections/cores 15 Electrical connection 1, connection pattern 00995913 Pollution degree 2 Note on materials RoHS-compliant Corrosion resistance class CRC 0 - No corrosion stress LABS-Conformity VDMA24364 zone III Vibration resistance Transport application test with severity level 2 to FN 942017-4 and EN 60068-2-6 10/2/21 - Subject to change - Festo AG & Co. -

Autocad Command Aliases
AutoCAD and Its Applications Advanced Appendix D AutoCAD Command Aliases Command Alias 3DALIGN 3AL 3DFACE 3F 3DMOVE 3M 3DORBIT 3DO, ORBIT, 3DVIEW, ISOMETRICVIEW 3DPOLY 3P 3DPRINT 3DP, 3DPLOT, RAPIDPROTOTYPE 3DROTATE 3R 3DSCALE 3S 3DWALK 3DNAVIGATE, 3DW ACTRECORD ARR ACTSTOP ARS -ACTSTOP -ARS ACTUSERINPUT ARU ACTUSERMESSAGE ARM -ACTUSERMESSAGE -ARM ADCENTER ADC, DC, DCENTER ALIGN AL ALLPLAY APLAY ANALYSISCURVATURE CURVATUREANALYSIS ANALYSISZEBRA ZEBRA APPLOAD AP ARC A AREA AA ARRAY AR -ARRAY -AR ATTDEF ATT -ATTDEF -ATT Copyright Goodheart-Willcox Co., Inc. Appendix D — AutoCAD Command Aliases 1 May not be reproduced or posted to a publicly accessible website. Command Alias ATTEDIT ATE -ATTEDIT -ATE, ATTE ATTIPEDIT ATI BACTION AC BCLOSE BC BCPARAMETER CPARAM BEDIT BE BLOCK B -BLOCK -B BOUNDARY BO -BOUNDARY -BO BPARAMETER PARAM BREAK BR BSAVE BS BVSTATE BVS CAMERA CAM CHAMFER CHA CHANGE -CH CHECKSTANDARDS CHK CIRCLE C COLOR COL, COLOUR COMMANDLINE CLI CONSTRAINTBAR CBAR CONSTRAINTSETTINGS CSETTINGS COPY CO, CP CTABLESTYLE CT CVADD INSERTCONTROLPOINT CVHIDE POINTOFF CVREBUILD REBUILD CVREMOVE REMOVECONTROLPOINT CVSHOW POINTON Copyright Goodheart-Willcox Co., Inc. Appendix D — AutoCAD Command Aliases 2 May not be reproduced or posted to a publicly accessible website. Command Alias CYLINDER CYL DATAEXTRACTION DX DATALINK DL DATALINKUPDATE DLU DBCONNECT DBC, DATABASE, DATASOURCE DDGRIPS GR DELCONSTRAINT DELCON DIMALIGNED DAL, DIMALI DIMANGULAR DAN, DIMANG DIMARC DAR DIMBASELINE DBA, DIMBASE DIMCENTER DCE DIMCONSTRAINT DCON DIMCONTINUE DCO, DIMCONT DIMDIAMETER DDI, DIMDIA DIMDISASSOCIATE DDA DIMEDIT DED, DIMED DIMJOGGED DJO, JOG DIMJOGLINE DJL DIMLINEAR DIMLIN, DLI DIMORDINATE DOR, DIMORD DIMOVERRIDE DOV, DIMOVER DIMRADIUS DIMRAD, DRA DIMREASSOCIATE DRE DIMSTYLE D, DIMSTY, DST DIMTEDIT DIMTED DIST DI, LENGTH DIVIDE DIV DONUT DO DRAWINGRECOVERY DRM DRAWORDER DR Copyright Goodheart-Willcox Co., Inc. -

CS101 Lecture 9
How do you copy/move/rename/remove files? How do you create a directory ? What is redirection and piping? Readings: See CCSO’s Unix pages and 9-2 cp option file1 file2 First Version cp file1 file2 file3 … dirname Second Version This is one version of the cp command. file2 is created and the contents of file1 are copied into file2. If file2 already exits, it This version copies the files file1, file2, file3,… into the directory will be replaced with a new one. dirname. where option is -i Protects you from overwriting an existing file by asking you for a yes or no before it copies a file with an existing name. -r Can be used to copy directories and all their contents into a new directory 9-3 9-4 cs101 jsmith cs101 jsmith pwd data data mp1 pwd mp1 {FILES: mp1_data.m, mp1.m } {FILES: mp1_data.m, mp1.m } Copy the file named mp1_data.m from the cs101/data Copy the file named mp1_data.m from the cs101/data directory into the pwd. directory into the mp1 directory. > cp ~cs101/data/mp1_data.m . > cp ~cs101/data/mp1_data.m mp1 The (.) dot means “here”, that is, your pwd. 9-5 The (.) dot means “here”, that is, your pwd. 9-6 Example: To create a new directory named “temp” and to copy mv option file1 file2 First Version the contents of an existing directory named mp1 into temp, This is one version of the mv command. file1 is renamed file2. where option is -i Protects you from overwriting an existing file by asking you > cp -r mp1 temp for a yes or no before it copies a file with an existing name. -

LS-90 Operation Guide
Communicating Thermostat - TheLS-90 has 2 RTM-1 radio ports. These allow your thermostat to communicate with other systems. Depending on your area Power Company, programs may be available to connect your thermostat to power grid status information. This can make it easy for you to moderate your energy use at peak hours and use power when it is less expensive. The RTM-1 ports also allow you to connect yourLS-90 to your home WiFi network. This can give you access to your home’s HVAC system even when you are away. It can also give you access to web based efficient energy management sites that RTM-1 port can help you save money and protect the environment. Customer support:877-254-5625 or www.LockStateConnect.com PG 20 PG 1 LS-90 Operation Guide top cover The LS-90 programmable communicating Wire thermostat operates via a high-quality, easy- terminals Power Grid Reset to-use touch screen. To program or adjust status button your LS-90, simply touch your finger or the indicators Home stylus firmly to the screen. The screen will button SAVE NORMAL automatically light up and you will hear a ENERGY $0.05 KW H FAN 12:30pm “beep.” The screen will respond differently to 5/25 WED different types of touches, so you may want Control o TARGET bar to experiment with both your finger and with F 77o Save TEMP Power the stylus, which is included with the LS-90, Energy HUMI D button HVAC 23% Button STATUS Power Status Normal $.05/kW to see what works best for you. -

The Linux Command Line
The Linux Command Line Fifth Internet Edition William Shotts A LinuxCommand.org Book Copyright ©2008-2019, William E. Shotts, Jr. This work is licensed under the Creative Commons Attribution-Noncommercial-No De- rivative Works 3.0 United States License. To view a copy of this license, visit the link above or send a letter to Creative Commons, PO Box 1866, Mountain View, CA 94042. A version of this book is also available in printed form, published by No Starch Press. Copies may be purchased wherever fine books are sold. No Starch Press also offers elec- tronic formats for popular e-readers. They can be reached at: https://www.nostarch.com. Linux® is the registered trademark of Linus Torvalds. All other trademarks belong to their respective owners. This book is part of the LinuxCommand.org project, a site for Linux education and advo- cacy devoted to helping users of legacy operating systems migrate into the future. You may contact the LinuxCommand.org project at http://linuxcommand.org. Release History Version Date Description 19.01A January 28, 2019 Fifth Internet Edition (Corrected TOC) 19.01 January 17, 2019 Fifth Internet Edition. 17.10 October 19, 2017 Fourth Internet Edition. 16.07 July 28, 2016 Third Internet Edition. 13.07 July 6, 2013 Second Internet Edition. 09.12 December 14, 2009 First Internet Edition. Table of Contents Introduction....................................................................................................xvi Why Use the Command Line?......................................................................................xvi -

Shell Variables
Shell Using the command line Orna Agmon ladypine at vipe.technion.ac.il Haifux Shell – p. 1/55 TOC Various shells Customizing the shell getting help and information Combining simple and useful commands output redirection lists of commands job control environment variables Remote shell textual editors textual clients references Shell – p. 2/55 What is the shell? The shell is the wrapper around the system: a communication means between the user and the system The shell is the manner in which the user can interact with the system through the terminal. The shell is also a script interpreter. The simplest script is a bunch of shell commands. Shell scripts are used in order to boot the system. The user can also write and execute shell scripts. Shell – p. 3/55 Shell - which shell? There are several kinds of shells. For example, bash (Bourne Again Shell), csh, tcsh, zsh, ksh (Korn Shell). The most important shell is bash, since it is available on almost every free Unix system. The Linux system scripts use bash. The default shell for the user is set in the /etc/passwd file. Here is a line out of this file for example: dana:x:500:500:Dana,,,:/home/dana:/bin/bash This line means that user dana uses bash (located on the system at /bin/bash) as her default shell. Shell – p. 4/55 Starting to work in another shell If Dana wishes to temporarily use another shell, she can simply call this shell from the command line: [dana@granada ˜]$ bash dana@granada:˜$ #In bash now dana@granada:˜$ exit [dana@granada ˜]$ bash dana@granada:˜$ #In bash now, going to hit ctrl D dana@granada:˜$ exit [dana@granada ˜]$ #In original shell now Shell – p. -

Unix Programming
P.G DEPARTMENT OF COMPUTER APPLICATIONS 18PMC532 UNIX PROGRAMMING K1 QUESTIONS WITH ANSWERS UNIT- 1 1) Define unix. Unix was originally written in assembler, but it was rewritten in 1973 in c, which was principally authored by Dennis Ritchie ( c is based on the b language developed by kenThompson. 2) Discuss the Communication. Excellent communication with users, network User can easily exchange mail,dta,pgms in the network 3) Discuss Security Login Names Passwords Access Rights File Level (R W X) File Encryption 4) Define PORTABILITY UNIX run on any type of Hardware and configuration Flexibility credits goes to Dennis Ritchie( c pgms) Ported with IBM PC to GRAY 2 5) Define OPEN SYSTEM Everything in unix is treated as file(source pgm, Floppy disk,printer, terminal etc., Modification of the system is easy because the Source code is always available 6) The file system breaks the disk in to four segements The boot block The super block The Inode table Data block 7) Command used to find out the block size on your file $cmchk BSIZE=1024 8) Define Boot Block Generally the first block number 0 is called the BOOT BLOCK. It consists of Hardware specific boot program that loads the file known as kernal of the system. 9) Define super block It describes the state of the file system ie how large it is and how many maximum Files can it accommodate This is the 2nd block and is number 1 used to control the allocation of disk blocks 10) Define inode table The third segment includes block number 2 to n of the file system is called Inode Table. -

Useful Commands in Linux and Other Tools for Quality Control
Useful commands in Linux and other tools for quality control Ignacio Aguilar INIA Uruguay 05-2018 Unix Basic Commands pwd show working directory ls list files in working directory ll as before but with more information mkdir d make a directory d cd d change to directory d Copy and moving commands To copy file cp /home/user/is . To copy file directory cp –r /home/folder . to move file aa into bb in folder test mv aa ./test/bb To delete rm yy delete the file yy rm –r xx delete the folder xx Redirections & pipe Redirection useful to read/write from file !! aa < bb program aa reads from file bb blupf90 < in aa > bb program aa write in file bb blupf90 < in > log Redirections & pipe “|” similar to redirection but instead to write to a file, passes content as input to other command tee copy standard input to standard output and save in a file echo copy stream to standard output Example: program blupf90 reads name of parameter file and writes output in terminal and in file log echo par.b90 | blupf90 | tee blup.log Other popular commands head file print first 10 lines list file page-by-page tail file print last 10 lines less file list file line-by-line or page-by-page wc –l file count lines grep text file find lines that contains text cat file1 fiel2 concatenate files sort sort file cut cuts specific columns join join lines of two files on specific columns paste paste lines of two file expand replace TAB with spaces uniq retain unique lines on a sorted file head / tail $ head pedigree.txt 1 0 0 2 0 0 3 0 0 4 0 0 5 0 0 6 0 0 7 0 0 8 0 0 9 0 0 10 -

Linux Cheat Sheet
1 of 4 ########################################### # 1.1. File Commands. # Name: Bash CheatSheet # # # # A little overlook of the Bash basics # ls # lists your files # # ls -l # lists your files in 'long format' # Usage: A Helpful Guide # ls -a # lists all files, including hidden files # # ln -s <filename> <link> # creates symbolic link to file # Author: J. Le Coupanec # touch <filename> # creates or updates your file # Date: 2014/11/04 # cat > <filename> # places standard input into file # Edited: 2015/8/18 – Michael Stobb # more <filename> # shows the first part of a file (q to quit) ########################################### head <filename> # outputs the first 10 lines of file tail <filename> # outputs the last 10 lines of file (-f too) # 0. Shortcuts. emacs <filename> # lets you create and edit a file mv <filename1> <filename2> # moves a file cp <filename1> <filename2> # copies a file CTRL+A # move to beginning of line rm <filename> # removes a file CTRL+B # moves backward one character diff <filename1> <filename2> # compares files, and shows where differ CTRL+C # halts the current command wc <filename> # tells you how many lines, words there are CTRL+D # deletes one character backward or logs out of current session chmod -options <filename> # lets you change the permissions on files CTRL+E # moves to end of line gzip <filename> # compresses files CTRL+F # moves forward one character gunzip <filename> # uncompresses files compressed by gzip CTRL+G # aborts the current editing command and ring the terminal bell gzcat <filename> # -

Programming Project #2 Due: Thursday, May 13Th, 2004, 11:59 Pm
CS155: Computer Security Spring 2004 Programming Project #2 Due: Thursday, May 13th, 2004, 11:59 pm 1 Introduction 1.1 Summary In this project, you will write Josh, the journaling operator shell. Josh is a setuid-root shell that allows users to undertake a subset of root’s capabilities. Your starting point is OSH, a minimal shell developed by Gunnar Ritter. You may work alone, or in pairs. You should not collaborate with others outside your group. You will use the Boxes system again. Remember to test your Josh in a closedbox. This as- signment specification is quite long, but much of it is intended to clarify points of confusion raised by previous years’ students. Please be sure to read it carefully before beginning to code. 1.2 The Problem As discussed in class, the classical Unix permissions model does not manage privilege delegation effectively. To perform routine administrative tasks (such as cleaning out the /tmp directory), one must possess the root password, and can therefore perform other, undesirable actions (such as reading users’ mail). This limitation manifests itself most acutely in large Unix installations, where there are typically many administrators tasked with various duties. Finer granularity of access is required for such systems, along with the ability to correctly log the important events for post-attack analysis. Various systems have been devised to overcome this limitation, and allow unprivileged users to un- dertake some subset of root’s capabilities. A commonly-used example is Sudo (http://www.sudo.ws/). We will take an approach more like that taken by OSH, the Operator Shell by Michael Neuman. -
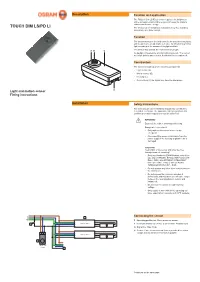
Mounting Instructions OSRAM Sensor Touch DIM LS/PD LI Light And
Description Function and application The TOUCH DIM LS/PD LI sensor regulates the brightness at the workplace and in office areas to increase the working comfort and to save energy. TOUCH DIM LS/PD LI The sensor can be installed in luminaires (e.g. floor standing luminaires) or in false ceilings. Function The sensor measures the brightness in the area to be regulated and keeps this to an adjustable set value by introducing artificial light according to the amount of daylight available. A B C The sensor also detects the movements of people. As daylight increases the artificial light is reduced . The sensor no longer detects any motions, it switches the luminaires off. Construction The sensor is made up of the following components: • Light sensor (A) • Motion sensor (B) • Housing (C) • Connections (D) for signal line, zero line and phase D Light and motion sensor Fitting instructions Installation Safety instructions The sensor must only be installed and put into operation by a qualified electrician. The applicable safety regulations and accident prevention regulations must be observed. WARNING! Exposed, live cables or damaged housing. Danger of electric shock! • Only work on the sensor when it is de- energized. • Disconnect the sensor or luminaire from the power supply if the housing or plastic lens is damaged. CAUTION! Destruction of the sensor and other devices through incorrect mounting! • Only use electronic OSRAM ballast coils of the type QUICKTRONIC INTELLIGENT DALI (QTi DALI…DIM), HALOTRONIC INTELLIGENT DALI (HTi DALI…DIM) or OPTOTRONIC INTELLIGENT DALI (OT…DIM). • Do not operate any other other control units on the control line. -

Configuring Your Login Session
SSCC Pub.# 7-9 Last revised: 5/18/99 Configuring Your Login Session When you log into UNIX, you are running a program called a shell. The shell is the program that provides you with the prompt and that submits to the computer commands that you type on the command line. This shell is highly configurable. It has already been partially configured for you, but it is possible to change the way that the shell runs. Many shells run under UNIX. The shell that SSCC users use by default is called the tcsh, pronounced "Tee-Cee-shell", or more simply, the C shell. The C shell can be configured using three files called .login, .cshrc, and .logout, which reside in your home directory. Also, many other programs can be configured using the C shell's configuration files. Below are sample configuration files for the C shell and explanations of the commands contained within these files. As you find commands that you would like to include in your configuration files, use an editor (such as EMACS or nuTPU) to add the lines to your own configuration files. Since the first character of configuration files is a dot ("."), the files are called "dot files". They are also called "hidden files" because you cannot see them when you type the ls command. They can only be listed when using the -a option with the ls command. Other commands may have their own setup files. These files almost always begin with a dot and often end with the letters "rc", which stands for "run commands".