Laksa: a Probabilistic Proof-Of-Stake Protocol
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

American Bar Association Business Law Section Committee on Derivatives and Futures Law
American Bar Association Business Law Section Committee on Derivatives and Futures Law Winter Meeting 2018 Naples, Florida Friday, January 19, 2018 10:15 a.m. to 11:30 a.m. NEW PRODUCTS / FINANCIAL TECHNOLOGY Moderator for the Program: Conrad G. Bahlke, Willkie Farr &Gallagher LLP Speakers: Geoffrey F. Aronow, Sidley Austin LLP Debra W. Cook, Depository Trust & Clearing Corporation Katherine Cooper, Law Office of Katherine Cooper Isabelle Corbett, R3 David Lucking, Allen & Overy LLP Brian D. Quintenz, Commissioner, U.S. Commodity Futures Trading Commission ABA BUSINESS LAW SECTION DERIVATIVES & FUTURES LAW COMMITTEE 2018 WINTER MEETING NEW PRODUCTS / FIN TECH PANEL 2017 Developments in US Regulation of Virtual Currencies and Related Products: Yin and Yang January 5, 2018 By Katherine Cooper1 2017 was a year during which virtual currencies began to move into the mainstream financial markets. This generated significant legal and regulatory developments as U.S. regulators faced numerous novel products attempting to blend the old with the new. Although facing so many novel issues, the regulators’ responses tell a familiar story of the struggle to balance the yin of customer protection with the yang of encouraging financial innovation and competition. Below is a summary of 2017 developments from the SEC, CFTC, OCC, FinCEN and the States. I. Securities and Exchange Commission a. Bitcoin Exchange-Traded Products A number of sponsors of proposed Bitcoin exchange traded products had applications for approval pending before the Securities and Exchange Commission at the beginning of 2017. In March 2017, the SEC rejected a proposal backed by Tyler and Cameron Winklevoss.2 The Bats Exchange proposed a rule amendment which would list the shares of the Winklevoss Bitcoin Trust for trading. -

Rev. Rul. 2019-24 ISSUES (1) Does a Taxpayer Have Gross Income Under
26 CFR 1.61-1: Gross income. (Also §§ 61, 451, 1011.) Rev. Rul. 2019-24 ISSUES (1) Does a taxpayer have gross income under § 61 of the Internal Revenue Code (Code) as a result of a hard fork of a cryptocurrency the taxpayer owns if the taxpayer does not receive units of a new cryptocurrency? (2) Does a taxpayer have gross income under § 61 as a result of an airdrop of a new cryptocurrency following a hard fork if the taxpayer receives units of new cryptocurrency? BACKGROUND Virtual currency is a digital representation of value that functions as a medium of exchange, a unit of account, and a store of value other than a representation of the United States dollar or a foreign currency. Foreign currency is the coin and paper money of a country other than the United States that is designated as legal tender, circulates, and is customarily used and accepted as a medium of exchange in the country of issuance. See 31 C.F.R. § 1010.100(m). - 2 - Cryptocurrency is a type of virtual currency that utilizes cryptography to secure transactions that are digitally recorded on a distributed ledger, such as a blockchain. Units of cryptocurrency are generally referred to as coins or tokens. Distributed ledger technology uses independent digital systems to record, share, and synchronize transactions, the details of which are recorded in multiple places at the same time with no central data store or administration functionality. A hard fork is unique to distributed ledger technology and occurs when a cryptocurrency on a distributed ledger undergoes a protocol change resulting in a permanent diversion from the legacy or existing distributed ledger. -

Crypto-Asset Markets: Potential Channels for Future Financial Stability
Crypto-asset markets Potential channels for future financial stability implications 10 October 2018 The Financial Stability Board (FSB) is established to coordinate at the international level the work of national financial authorities and international standard-setting bodies in order to develop and promote the implementation of effective regulatory, supervisory and other financial sector policies. Its mandate is set out in the FSB Charter, which governs the policymaking and related activities of the FSB. These activities, including any decisions reached in their context, shall not be binding or give rise to any legal rights or obligations under the FSB’s Articles of Association. Contacting the Financial Stability Board Sign up for e-mail alerts: www.fsb.org/emailalert Follow the FSB on Twitter: @FinStbBoard E-mail the FSB at: [email protected] Copyright © 2018 Financial Stability Board. Please refer to: www.fsb.org/terms_conditions/ Contents Executive Summary ................................................................................................................... 1 1. Introduction ......................................................................................................................... 3 2. Primary risks in crypto-asset markets ................................................................................. 5 2.1 Market liquidity risks ............................................................................................... 5 2.2 Volatility risks ......................................................................................................... -
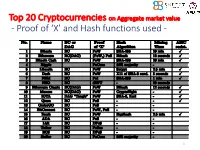
Proof of 'X' and Hash Functions Used
Top 20 Cryptocurrencies on Aggregate market value - Proof of ‘X’ and Hash functions used - 1 ISI Kolkata BlockChain Workshop, Nov 30th, 2017 CRYPTOGRAPHY with BlockChain - Hash Functions, Signatures and Anonymization - Hiroaki ANADA*1, Kouichi SAKURAI*2 *1: University of Nagasaki, *2: Kyushu University Acknowledgements: This work is supported by: Grants-in-Aid for Scientific Research of Japan Society for the Promotion of Science; Research Project Number: JP15H02711 Top 20 Cryptocurrencies on Aggregate market value - Proof of ‘X’ and Hash functions used - 3 Table of Contents 1. Cryptographic Primitives in Blockchains 2. Hash Functions a. Roles b. Various Hash functions used for Proof of ‘X’ 3. Signatures a. Standard Signatures (ECDSA) b. Ring Signatures c. One-Time Signatures (Winternitz) 4. Anonymization Techniques a. Mixing (CoinJoin) b. Zero-Knowledge proofs (zk-SNARK) 5. Conclusion 4 Brief History of Proof of ‘X’ 1992: “Pricing via Processing or Combatting Junk Mail” Dwork, C. and Naor, M., CRYPTO ’92 Pricing Functions 2003: “Moderately Hard Functions: From Complexity to Spam Fighting” Naor, M., Foundations of Soft. Tech. and Theoretical Comp. Sci. 2008: “Bitcoin: A peer-to-peer electronic cash system” Nakamoto, S. Proof of Work 5 Brief History of Proof of ‘X’ 2008: “Bitcoin: A peer-to-peer electronic cash system” Nakamoto, S. Proof of Work 2012: “Peercoin” Proof of Stake (& Proof of Work) ~ : Delegated Proof of Stake, Proof of Storage, Proof of Importance, Proof of Reserves, Proof of Consensus, ... 6 Proofs of ‘X’ 1. Proof of Work 2. Proof of Stake Hash-based Proof of ‘X’ 3. Delegated Proof of Stake 4. Proof of Importance 5. -

Blockchain Law: the Fork Not Taken
Blockchain Law The fork not taken Robert A. Schwinger, New York Law Journal — November 24, 2020 I shall be telling this with a sigh Somewhere ages and ages hence: Two roads diverged in a wood, and I— I took the one less traveled by, And that has made all the difference. — Robert Frost Is the token holder — often the holder of some form of digital currency — always free to choose which branch of the fork to take? A blockchain is often envisioned as a record of a single continuous Background: ‘Two roads diverged in a sequential series of transactions, like the links of the metaphorical chain from which the term “blockchain” derives. But sometimes yellow wood’ the chain turns out to be not so single or continuous. Sometimes situations can arise where a portion of the chain can branch off A blockchain fork occurs when someone seeks to divide a into a new direction from the original chain, while the original chain blockchain into two branches by changing its source code, which also continues to move forward separately. This presents a choice is possible to do because the code is open. For those users who for the current holders of the digital tokens on that blockchain choose to upgrade their software, the software then “rejects about which direction they wish to follow going forward. In the all transactions from older software, effectively creating a new world of blockchain, this scenario is termed a “fork.” branch of the blockchain. However, those users who retain the old software continue to process transactions, meaning that But is the tokenholder—often the holder of some form of digital there is a parallel set of transactions taking place across two currency—always free to choose which branch of the fork to different chains.” See generally N. -

Review Articles
review articles DOI:10.1145/3372115 system is designed to achieve common Software weaknesses in cryptocurrencies security goals: transaction integrity and availability in a highly distributed sys- create unique challenges in responsible tem whose participants are incentiv- revelations. ized to cooperate.38 Users interact with the cryptocurrency system via software BY RAINER BÖHME, LISA ECKEY, TYLER MOORE, “wallets” that manage the cryptograph- NEHA NARULA, TIM RUFFING, AND AVIV ZOHAR ic keys associated with the coins of the user. These wallets can reside on a local client machine or be managed by an online service provider. In these appli- cations, authenticating users and Responsible maintaining confidentiality of crypto- graphic key material are the central se- curity goals. Exchanges facilitate trade Vulnerability between cryptocurrencies and between cryptocurrencies and traditional forms of money. Wallets broadcast cryptocur- Disclosure in rency transactions to a network of nodes, which then relay transactions to miners, who in turn validate and group Cryptocurrencies them together into blocks that are ap- pended to the blockchain. Not all cryptocurrency applications revolve around payments. Some crypto- currencies, most notably Ethereum, support “smart contracts” in which general-purpose code can be executed with integrity assurances and recorded DESPITE THE FOCUS on operating in adversarial on the distributed ledger. An explosion of token systems has appeared, in environments, cryptocurrencies have suffered a litany which particular functionality is ex- of security and privacy problems. Sometimes, these pressed and run on top of a cryptocur- rency.12 Here, the promise is that busi- issues are resolved without much fanfare following ness logic can be specified in the smart a disclosure by the individual who found the hole. -

Segwit2x –
SegWit2x – A New Statement The Overwhelming power of SegWit2x In order to safeguard the community from an undesired chain split, the upgrade should be overwhelming, but it’s not enough. It should also ‘appear’ as overwhelming. People, businesses and services needs to be certain about what is going to happen and the risks if they won’t follow. My impression is that still too many speaking english people in the western world think the upgrade will be abandoned before or immediately after block 494784 is mined, thus they are going to simply ignore it. That could lead to unprepared patch up and confusion, while naïve users risk to harm themselves. For this reason and for the sake of the Bitcoin community as a whole, we need to show again, clearly and publicly the extent of the support to SegWit2x. We also need to commit ourselves in a widespread communication campaign. I know this is not a strict technical matter, but it could help a lot avoiding technical issues in the future. What we have to do First, we need a new statement from the original NYA signers and all the business, firms and individuals who joined the cause later. That statement should be slightly different from the original NYA though, and I am explaining why. We all know that what Bitcoin is will be ultimately determined by market forces, comprehensive of all the stakeholders involved: businesses, miners, users, developers, traders, investors, holders etc. Each category has its own weight in the process, and everybody has incentives in following the market. -

MYBTGWALLET SCAM the Dark Side of the Fork
MYBTGWALLET SCAM The dark side of the fork Intro After Bitcoin Cash fork on Aug. 1st, Bitcoin was involved in two other forks between October and November: before the so disputed Segwit2x announced fork, on Oct. 24th a new crypto was launched. Bitcoin Gold was a new greedy chance for Bitcoin owners to earn some free money: importing mnemonic seeds or private keys belonging to a BTC wallet in a BTG one they had the opportunity to redeem their free BTG. This was possible through local BTG clients or through some web services such as MyBTGWallet.com, a website listed directly on BTG official webpage. This particular case turned in a scam that stole an impressive number of Bitcoin from “unexperienced” users. The Scam Site MyBTGWallet scam worked in a very simple way: users imported the mnemonic seed of their BTC wallet on the scam page providing in this way the scammer with the private keys needed to steal the balance of bitcoin still on the wallet and any other cryptocurrencies stored on the same wallet (e.g. Ethereum or Litecoin in case it was a multicurrency wallet). MyBTGWallet page The site used a clever trick to save the mnemonic seed into the cookies of the browser and then siphoned the cookies via a google tracking javascript having this way access to all seeds checked on the website. 2 The numbers The website was used by many bitcoin holders after the fork happened. The scammers progressively moved the stolen funds to other bitcoin addresses. Thanks to open source intelligence activities, we were able to create the clusters of the stolen bitcoin and determine that the number of compromised addresses is almost 4500. -

Transparent and Collaborative Proof-Of-Work Consensus
StrongChain: Transparent and Collaborative Proof-of-Work Consensus Pawel Szalachowski, Daniël Reijsbergen, and Ivan Homoliak, Singapore University of Technology and Design (SUTD); Siwei Sun, Institute of Information Engineering and DCS Center, Chinese Academy of Sciences https://www.usenix.org/conference/usenixsecurity19/presentation/szalachowski This paper is included in the Proceedings of the 28th USENIX Security Symposium. August 14–16, 2019 • Santa Clara, CA, USA 978-1-939133-06-9 Open access to the Proceedings of the 28th USENIX Security Symposium is sponsored by USENIX. StrongChain: Transparent and Collaborative Proof-of-Work Consensus Pawel Szalachowski1 Daniel¨ Reijsbergen1 Ivan Homoliak1 Siwei Sun2;∗ 1Singapore University of Technology and Design (SUTD) 2Institute of Information Engineering and DCS Center, Chinese Academy of Sciences Abstract a cryptographically-protected append-only list [2] is intro- duced. This list consists of transactions grouped into blocks Bitcoin is the most successful cryptocurrency so far. This and is usually referred to as a blockchain. Every active pro- is mainly due to its novel consensus algorithm, which is tocol participant (called a miner) collects transactions sent based on proof-of-work combined with a cryptographically- by users and tries to solve a computationally-hard puzzle in protected data structure and a rewarding scheme that incen- order to be able to write to the blockchain (the process of tivizes nodes to participate. However, despite its unprece- solving the puzzle is called mining). When a valid solution dented success Bitcoin suffers from many inefficiencies. For is found, it is disseminated along with the transactions that instance, Bitcoin’s consensus mechanism has been proved to the miner wishes to append. -
![Arxiv:1907.02434V1 [Cs.CY] 4 Jul 2019 1 Introduction](https://docslib.b-cdn.net/cover/6379/arxiv-1907-02434v1-cs-cy-4-jul-2019-1-introduction-716379.webp)
Arxiv:1907.02434V1 [Cs.CY] 4 Jul 2019 1 Introduction
Cryptocurrency Egalitarianism: A Quantitative Approach Dimitris Karakostas1,3, Aggelos Kiayias1,3, Christos Nasikas2,4, and Dionysis Zindros2,3 1 University of Edinburgh 2 University of Athens 3 IOHK 4 “ATHENA” Research Center Abstract. Since the invention of Bitcoin one decade ago, numerous cryptocurrencies have sprung into existence. Among these, proof-of-work is the most common mechanism for achieving consensus, whilst a num- ber of coins have adopted “ASIC-resistance” as a desirable property, claiming to be more “egalitarian,” where egalitarianism refers to the power of each coin to participate in the creation of new coins. While proof-of-work consensus dominates the space, several new cryptocurren- cies employ alternative consensus, such as proof-of-stake in which block minting opportunities are based on monetary ownership. A core criti- cism of proof-of-stake revolves around it being less egalitarian by making the rich richer, as opposed to proof-of-work in which everyone can con- tribute equally according to their computational power. In this paper, we give the first quantitative definition of a cryptocurrency’s egalitarian- ism. Based on our definition, we measure the egalitarianism of popular cryptocurrencies that (may or may not) employ ASIC-resistance, among them Bitcoin, Ethereum, Litecoin, and Monero. Our simulations show, as expected, that ASIC-resistance increases a cryptocurrency’s egalitar- ianism. We also measure the egalitarianism of a stake-based protocol, Ouroboros, and a hybrid proof-of-stake/proof-of-work cryptocurrency, Decred. We show that stake-based cryptocurrencies, under correctly se- lected parameters, can be perfectly egalitarian, perhaps contradicting folklore belief. arXiv:1907.02434v1 [cs.CY] 4 Jul 2019 1 Introduction In 2008, Satoshi Nakamoto proposed Bitcoin [25], the first and most suc- cessful cryptocurrency to date. -

A Regulatory System for Optimal Legal Transaction Throughput in Cryptocurrency Blockchains
A Regulatory System for Optimal Legal Transaction Throughput in Cryptocurrency Blockchains Aditya Ahuja Vinay J. Ribeiro Ranjan Pal Indian Institute of Technology Indian Institute of Technology University of Michigan Delhi Bombay Ann Arbor, USA New Delhi, India Mumbai, India [email protected] [email protected] [email protected] ABSTRACT correctness of the underlying computational principles, which are a Permissionless blockchain consensus protocols have been designed basis of the efficacy of these economies. More specifically, in order primarily for defining decentralized economies for the commercial to sustain these cryptocurrency based decentralized economies, trade of assets, both virtual and physical, using cryptocurrencies. blockchain consensus protocols serve as a technical foundation. In most instances, the assets being traded are regulated, which man- Existing blockchain protocols for cryptocurrencies address one dates that the legal right to their trade and their trade value are of (or any combination of) the following system goals: speed, se- determined by the governmental regulator of the jurisdiction in curity and decentralization. Unfortunately, these system goals are which the trade occurs. Unfortunately, existing blockchains do not necessary but insufficient. Illegal activities propelled through the formally recognise proposal of legal cryptocurrency transactions, as strategic use of blockchain based cryptocurrencies, is a serious part of the execution of their respective consensus protocols, result- problem staring at the face of many world governments today ing in rampant illegal activities in the associated crypto-economies. [47]. These illegal activities exploit the permissionless nature of In this contribution, we motivate the need for regulated blockchain the blockchain networks for illegal trade, to strategically defeat consensus protocols with a case study of the illegal, cryptocurrency regulation by obfuscating the jurisdictions of the blockchain users based, Silk Road darknet market. -

Incentives in Ethereum's Hybrid Casper Protocol
Incentives in Ethereum’s Hybrid Casper Protocol Vitalik Buterin∗, Daniel¨ Reijsbergeny, Stefanos Leonardosy, Georgios Piliourasy ∗Ethereum Foundation ySingapore University of Technology and Design Abstract We present an overview of hybrid Casper the Friendly Finality Gadget (FFG): a Proof-of-Stake checkpointing protocol overlaid onto Ethereum’s Proof-of-Work blockchain. We describe its core functionalities and reward scheme, and explore its properties. Our findings indicate that Casper’s implemented incentives mechanism ensures liveness, while providing safety guarantees that improve over standard Proof-of-Work protocols. Based on a minimal-impact implementation of the protocol as a smart contract on the blockchain, we discuss additional issues related to parametrisation, funding, throughput and network overhead and detect potential limitations. Index Terms Proof of Stake, Ethereum, Consensus I. INTRODUCTION In 2008, the seminal Bitcoin paper by Satoshi Nakamoto [50] introduced the blockchain as a means for an open network to extend and reach consensus about a distributed ledger of digital token transfers. The main innovation of Ethereum [16] was to use the blockchain to maintain a history of code creation and execution. As such, Ethereum functions as a global computer that executes code uploaded by users in the form of smart contracts. Like Bitcoin [31], [32], Ethereum’s block proposal mechanism is based on the concept of Proof-of-Work (PoW). In PoW, network participants utilise computational power to win the right to add blocks to the blockchain. However, the alarming global energy consumption of PoW-based blockchains has made the concept increasingly controversial [22], [45], [65]. One of the main alternatives to PoW is virtual mining or Proof-of-Stake (PoS) [1], [5], [46], [55].