Why Crypto-Detectors Fail: a Systematic Evaluation of Cryptographic Misuse Detection Techniques
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

“Why So Serious?” Comics, Film and Politics, Or the Comic Book Film As the Answer to the Question of Identity and Narrative in a Post-9/11 World
ABSTRACT “WHY SO SERIOUS?” COMICS, FILM AND POLITICS, OR THE COMIC BOOK FILM AS THE ANSWER TO THE QUESTION OF IDENTITY AND NARRATIVE IN A POST-9/11 WORLD by Kyle Andrew Moody This thesis analyzes a trend in a subgenre of motion pictures that are designed to not only entertain, but also provide a message for the modern world after the terrorist attacks of September 11, 2001. The analysis provides a critical look at three different films as artifacts of post-9/11 culture, showing how the integration of certain elements made them allegorical works regarding the status of the United States in the aftermath of the attacks. Jean Baudrillard‟s postmodern theory of simulation and simulacra was utilized to provide a context for the films that tap into themes reflecting post-9/11 reality. The results were analyzed by critically examining the source material, with a cultural criticism emerging regarding the progression of this subgenre of motion pictures as meaningful work. “WHY SO SERIOUS?” COMICS, FILM AND POLITICS, OR THE COMIC BOOK FILM AS THE ANSWER TO THE QUESTION OF IDENTITY AND NARRATIVE IN A POST-9/11 WORLD A Thesis Submitted to the Faculty of Miami University in partial fulfillment of the requirements for the degree of Master of Arts Department of Communications Mass Communications Area by Kyle Andrew Moody Miami University Oxford, Ohio 2009 Advisor ___________________ Dr. Bruce Drushel Reader ___________________ Dr. Ronald Scott Reader ___________________ Dr. David Sholle TABLE OF CONTENTS ACKNOWLEDGMENTS .......................................................................................................................... III CHAPTER ONE: COMIC BOOK MOVIES AND THE REAL WORLD ............................................. 1 PURPOSE OF STUDY ................................................................................................................................... -

Cipher Code of Words, Phrases, Names of Organizations and Titles of Their
r/^i OF Words, Phrases, Names of Organizations and Ti- tles of Their Officers, Names of Principal Rail- roads, Months, Days, Time of Day, Al- phabet and Figures. FOR Use of Organizations of Railway Employes in TELEGRAPHIC CORRESPONDENCE ARRANGED BY Galesburg, 1892. Digitized by tine Internet Arcliive in 2010 witli funding from Dul<e University Libraries littp://www.arcliive.org/details/cipliercodeofworOOsliea PREFACE. In assuming, with pardonaljle pride, the labor of preparing a Cipher Code adapted to the business of the several Organizations of Railway Employes, the au- thor has endeavored to bring it thoroughly up to the requirements of the times. It is not to be expected that a work of this kind can be perfected by any one man in the first edition and the author requests those using this little book to note its short-comings for future reference, that he who undertakes the labor of revision, may have the benefit of their experience. The need of a work of this kind has at times been sorely felt by every organization and if this work meets the requirements so far as to lighten the burden of any organization in time of trouble, or to assist in gaining a single point in favor of the laboring man. then the author will feel that he has been fully repaid for his labor. To the several Organizations of Railway Emplo3'es this vrork is dedicated with the good will and best Avishes of the author. INSTRUCTIONS. This Cipher Code arranged for use of the several Organizations of Railway Employes is intended more especiall}' for Telegraphic Correspondence in time of trouble, when it is desirable or necessary to send tele- grams that can not be read by any but those for whom they are intended, as is the case in time of strikes or other important moves on the part of an Organization, as it is often necessary to use the Company's wire to reach members of the Organization on other parts of the road and unless such telegrams can be sent in a safe cipher it would be better the}^ were not sent, as the Company would be forewarned of every contem- plated move mentioned in the telegram. -

Narratives of Contamination and Mutation in Literatures of the Anthropocene Dissertation Presented in Partial
Radiant Beings: Narratives of Contamination and Mutation in Literatures of the Anthropocene Dissertation Presented in Partial Fulfillment of the Requirements for the Degree of Doctor of Philosophy in the Graduate School of The Ohio State University By Kristin Michelle Ferebee Graduate Program in English The Ohio State University 2019 Dissertation Committee Dr. Thomas S. Davis, Advisor Dr. Jared Gardner Dr. Brian McHale Dr. Rebekah Sheldon 1 Copyrighted by Kristin Michelle Ferebee 2019 2 Abstract The Anthropocene era— a term put forward to differentiate the timespan in which human activity has left a geological mark on the Earth, and which is most often now applied to what J.R. McNeill labels the post-1945 “Great Acceleration”— has seen a proliferation of narratives that center around questions of radioactive, toxic, and other bodily contamination and this contamination’s potential effects. Across literature, memoir, comics, television, and film, these narratives play out the cultural anxieties of a world that is itself increasingly figured as contaminated. In this dissertation, I read examples of these narratives as suggesting that behind these anxieties lies a more central anxiety concerning the sustainability of Western liberal humanism and its foundational human figure. Without celebrating contamination, I argue that the very concept of what it means to be “contaminated” must be rethought, as representations of the contaminated body shape and shaped by a nervous policing of what counts as “human.” To this end, I offer a strategy of posthuman/ist reading that draws on new materialist approaches from the Environmental Humanities, and mobilize this strategy to highlight the ways in which narratives of contamination from Marvel Comics to memoir are already rejecting the problematic ideology of the human and envisioning what might come next. -

Scholar Adventurers Also by Richard D
ichard THE SCHOLAR ADVENTURERS ALSO BY RICHARD D. ALTICK Preface to Critical Reading The Cowden Clarkes The English Common Reader: A Social History of the Mass Reading Public, 1800-1900 The Art of Literary Research Lives and Letters: A History of Literary Biography in England and America Browning's Roman Murder Story: A Reading of The Ring and the Book (with James F. Loucks II) To Be in England Victorian Studies in Scarlet Victorian People and Ideas The Shows of London Paintings from Books: Art and Literature in Britain, 1760-1900 Deadly Encounters: Two Victorian Sensations EDITIONS Thomas Carlyle: Past and Present Robert Browning: The Ring and the Book THE Scholar Adventurers RICHARD D. ALTICK Ohio State University Press, Columbus Copyright ©1950, 1987 by Richard D. Altick. All rights reserved. Library of Congress Cataloging-in-Publicatlon Data Altick, Richard Daniel, 1915- The scholar adventurers. Reprint. Originally published: New York : Macmillan, 1950. With new pref. Bibliography: p. Includes index. 1. English literature—Research. 2. Learning and scholarship—History. 3. Great Britain—Intellectual life. I. Title. P56.A7 1987 820'.72'0922 87-11064 ISBN O-8142-O435-X CONTENTS Preface to the Ohio State University Press Edition vii Introduction: The Unsung Scholar 1 I. The Secret of the Ebony Cabinet 16 II. The Case of the Curious Bibliographers 37 III. The Quest of the Knight-Prisoner 65 IV. Hunting for Manuscripts 86 V. Exit a Lady, Enter Another 122 VI. A Gallery of Inventors 142 VII. The Scholar and the Scientist 176 VIII. Secrets in Cipher 200 IX. The Destructive Elements 211 X. -

A Qualitative Content Analysis of How Superheroines Are Portrayed in Comic Books
CALIFORNIA STATE UNIVERSITY, NORTHRIDGE Fight Like a Girl: A Qualitative Content Analysis of How Superheroines are Portrayed in Comic Books A graduate project submitted in partial fulfillment of the requirements for the degree of Master of Arts in Sociology By Kimberly Romero December 2020 Copyright by Kimberly Romero 2020 ii The graduate project of Kimberly Romero is approved: _________________________________________ ______________ Dr. Michael Carter Date _________________________________________ ______________ Dr. Stacy Missari Date _________________________________________ ______________ Dr. Moshoula Capous-Desyllas, Chair Date California State University, Northridge iii ACKNOWLEDGEMENTS I would like to start off by acknowledging my parents for braving through a civil war, poverty, pain, political criticisms, racial stereotypes, and the constant bouts of uncertainty that immigrating to the United States, seeking asylum from the dangers plaguing their home country of El Salvador, has presented them with throughout the years. If it were not for your sacrifices, we would not have the lives and opportunities we have now. Having your constant love and support means the world to me. You are both my North Stars for everything I do. I would also like to acknowledge my sister for convincing Mom and Dad to let you name me after two of your greatest childhood role models, superheroines, and cultural icons. The Pink Power Ranger and The Queen of Tejano music are both pretty huge namesakes to live up to. I hope I do their legacies justice and that I am making you proud. I know I do not say this to you often but know that, through all our ups and downs, you were my hero growing up. -

2News Summer 05 Catalog
Comics’Fast & Furious Artist by Jim Amash with Eric Nolen-Weathington Table of Contents Introduction by Walter Simonson. 4 Chapter One: Inspiration All Around. 6 Chapter Two: A Heroic Departurre. 17 Chapter Three: How to Break in the Marvel Way . 33 Chapter Four: The Workhorse Hits His Stride . 59 Chapter Five: A New Start with a Different Company . 87 Chapter Six: The Craft of Creating Comic Book Art . 97 Art Gallery . 110 DR. STRANGE, HULK, SILVER SURFER ™ AND ©2010 MARVEL CHARACTERS, INC. 3 Chapter One Inspiration All Around Jim Amash: You probably don’t remember recollection from when I was five or six years when this happened, but I know you know old — when my brothers both painted a land- when and where you were born. scape of some kind. It was sort of a friendly Sal Buscema: Of course. [laughs] I was born competition. I think they may have been in Brooklyn, New York, on January 26, 1936. painting from a photograph. They were both My father’s name was John, and my mother’s working in oils, and having a good time. It was Sadie. My brother John was eight years was just a fun thing that they were doing. older than I, born December 11, 1927. John was always dabbling in this kind of stuff. He loved to draw and paint. I think Al JA: Do you have any other brothers or sisters? — there was a very friendly sibling rivalry (below) For many years, SB: Yes, though unfortunately they’re all between them. They were very close, very Sal participated in Friday deceased. -

DISAPPEAR HERE Violence After Generation X
· · · · · · · · · · · · · · · · DISAPPEAR HERE Violence after Generation X Naomi Mandel THE OHIO STATE UNIVERSITY PRESS / COLUMBUS All Rights Reserved. Copyright © The Ohio State University Press, 2015. Batch 1. Copyright © 2015 by The Ohio State University. All rights reserved. Library of Congress Cataloging-in-Publication Data Mandel, Naomi, 1969– author. Disappear here : violence after Generation X / Naomi Mandel. pages cm Includes bibliographical references and index. ISBN 978-0-8142-1286-8 (cloth : alk. paper) 1. Violence in literature. 2. Violence—United States—20th century. 3. Generation X— United States—20th century. I. Title. PN56.V53M36 2015 809'.933552—dc23 2015010172 Cover design by Janna Thompson-Chordas Text design by Juliet Williams Type set in Adobe Sabon Printed by Thomson-Shore, Inc. Cover image: Young woman with knife behind foil. © Bernd Friedel/Westend61/Corbis. The paper used in this publication meets the minimum requirements of the American National Standard for Information Sciences—Permanence of Paper for Printed Library Materials. ANSI Z39.48-1992. 9 8 7 6 5 4 3 2 1 All Rights Reserved. Copyright © The Ohio State University Press, 2015. Batch 1. To Erik with love and x x x All Rights Reserved. Copyright © The Ohio State University Press, 2015. Batch 1. All Rights Reserved. Copyright © The Ohio State University Press, 2015. Batch 1. contents · · · · · · · · · List of Illustrations vi Acknowledgments vii introduction The Middle Children of History 1 one Why X Now? Crossing Out and Marking the Spot 9 two Nevermind: An X Critique of Violence 41 three The Game That Moves: Bret Easton Ellis, 1985–2010 79 four Something Empty in the Sky: 9/11 after X 111 five Not Yes or No: Fact, Fiction, Fidelity in Jonathan Safran Foer 150 six I Am Jack’s Revolution: Fight Club, Hacking, Violence after X 178 conclusion X Out 210 Works Cited 227 Index 243 All Rights Reserved. -

Journal of Hip Hop Studies
et al.: Journal of Hip Hop Studies Published by VCU Scholars Compass, 2017 1 Journal of Hip Hop Studies, Vol. 4 [2017], Iss. 1, Art. 1 Editor in Chief: Daniel White Hodge, North Park University Senior Editorial Advisory Board: Anthony Pinn, Rice University James Paterson, Lehigh University Book Review Editor: Gabriel B. Tait, Arkansas State University Associate Editors: Cassandra Chaney, Louisiana State University Jeffrey L. Coleman, St. Mary’s College of Maryland Monica Miller, Lehigh University Associate & Copy Editor: Travis Harris, Doctoral Candidate, College of William and Mary Editorial Board: Dr. Rachelle Ankney, North Park University Dr. Shanté Paradigm Smalls, St. John’s University (NYC) Dr. Jim Dekker, Cornerstone University Ms. Martha Diaz, New York University Mr. Earle Fisher, Rhodes College/Abyssinian Baptist Church, United States Mr. Jon Gill, Claremont University Dr. Daymond Glenn, Warner Pacific College Dr. Deshonna Collier-Goubil, Biola University Dr. Kamasi Hill, Interdenominational Theological Center Dr. Andre Johnson, Memphis Theological Seminary Dr. David Leonard, Washington State University Dr. Terry Lindsay, North Park University Ms. Velda Love, North Park University Dr. Anthony J. Nocella II, Hamline University Dr. Priya Parmar, SUNY Brooklyn, New York Dr. Soong-Chan Rah, North Park University Dr. Rupert Simms, North Park University Dr. Darron Smith, University of Tennessee Health Science Center Dr. Jules Thompson, University Minnesota, Twin Cities Dr. Mary Trujillo, North Park University Dr. Edgar Tyson, Fordham University Dr. Ebony A. Utley, California State University Long Beach, United States Dr. Don C. Sawyer III, Quinnipiac University https://scholarscompass.vcu.edu/jhhs/vol4/iss1/1 2 et al.: Journal of Hip Hop Studies Sponsored By: North Park Universities Center for Youth Ministry Studies (http://www.northpark.edu/Centers/Center-for-Youth-Ministry-Studies) Save The Kids Foundation (http://savethekidsgroup.org/) Published by VCU Scholars Compass, 2017 3 Journal of Hip Hop Studies, Vol. -

Speculative Blackness This Page Intentionally Left Blank Speculative Blackness
Speculative BlackneSS This page intentionally left blank SPECULATIVE BLACKNESS The Future of Race in Science Fiction andré m. carrington University of Minnesota Press Minneapolis London A version of chapter 4 appeared as “Drawn into Dialogue: Comic Book Culture and the Scene of Controversy in Milestone Media’s Icon,” in The Blacker the Ink, ed. Frances Gateward and John Jennings (New Brunswick, N.J.: Rutgers University Press, 2015). Por- tions of chapter 6 appeared as “Dreaming in Colour: Fan Fiction as Critical Reception,” in Race/Gender/Class/Media, 3d ed., ed. Rebecca Ann Lind (Upper Saddle River, N.J.: Pearson, 2013), 95–101; copyright 2013, printed and electronically reproduced by per- mission of Pearson Education, Inc. Copyright 2016 by the Regents of the University of Minnesota All rights reserved. No part of this publication may be reproduced, stored in a retrieval system, or transmitted, in any form or by any means, electronic, mechanical, photocopy- ing, recording, or otherwise, without the prior written permission of the publisher. Published by the University of Minnesota Press 111 Third Avenue South, Suite 290 Minneapolis, MN 55401- 2520 http://www.upress.umn.edu Library of Congress Cataloging-in-Publication Data Carrington, André M. Speculative blackness: the future of race in science fiction / andré m. carrington. Includes bibliographical references and index. ISBN 978-0-8166-7895-2 (hc) ISBN 978-0-8166-7896-9 (pb) 1. American fiction—African American authors—History and criticism. 2. Science fiction, American—History and criticism. 3. Race in literature. 4. African Americans in mass media. 5. African Americans in popular culture I. -

Alternative Comics: an Emerging Literature
ALTERNATIVE COMICS Gilbert Hernandez, “Venus Tells It Like It Is!” Luba in America 167 (excerpt). © 2001 Gilbert Hernandez. Used with permission. ALTERNATIVE COMICS AN EMERGING LITERATURE Charles Hatfield UNIVERSITY PRESS OF MISSISSIPPI • JACKSON www.upress.state.ms.us The University Press of Mississippi is a member of the Association of American University Presses. Copyright © 2005 by University Press of Mississippi All rights reserved Manufactured in the United States of America First edition 2005 ϱ Library of Congress Cataloging-in-Publication Data Hatfield, Charles, 1965– Alternative comics : an emerging literature / Charles Hatfield. — 1st ed. p. cm. Includes bibliographical references and index. ISBN 1-57806-718-9 (cloth : alk. paper) — ISBN 1-57806-719-7 (pbk. : alk. paper) 1. Underground comic books, strips, etc.—United States—History and criticism. I. Title. PN6725.H39 2005 741.5'0973—dc22 2004025709 British Library Cataloging-in-Publication Data available CONTENTS Acknowledgments vii Introduction ix Alternative Comics as an Emerging Literature 1 Comix, Comic Shops, and the Rise of 3 Alternative Comics, Post 1968 2 An Art of Tensions 32 The Otherness of Comics Reading 3 A Broader Canvas: Gilbert Hernandez’s Heartbreak Soup 68 4 “I made that whole thing up!” 108 The Problem of Authenticity in Autobiographical Comics 5 Irony and Self-Reflexivity in Autobiographical Comics 128 Two Case Studies 6 Whither the Graphic Novel? 152 Notes 164 Works Cited 169 Index 177 This page intentionally left blank ACKNOWLEDGMENTS Who can do this sort of thing alone? Not I. Thanks are due to many. For permission to include passages from my article, “Heartbreak Soup: The Interdependence of Theme and Form” (Inks 4:2, May 1997), the Ohio State University Press. -
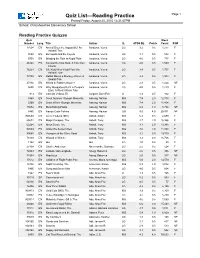
August Quiz List by Author.Pdf
Quiz List—Reading Practice Page 1 Printed Friday, August 20, 2010 12:31:07PM School: Chattahoochee Elementary School Reading Practice Quizzes Quiz Word Number Lang. Title Author IL ATOS BL Points Count F/NF 17504 EN Anansi Does the Impossible! An Aardema, Verna LG 3.2 0.5 1,277 F Ashanti Tale 7659 EN Borreguita and the Coyote Aardema, Verna LG 3.1 0.5 832 F 9758 EN Bringing the Rain to Kapiti Plain Aardema, Verna LG 4.6 0.5 717 F 46144 EN Koi and the Kola Nuts: A Tale from Aardema, Verna LG 4.0 0.5 1,599 F Liberia 76201 EN Oh, Kojo! How Could You! An Aardema, Verna LG 3.4 0.5 1,757 F Ashanti Tale 73785 EN Rabbit Makes a Monkey of Lion: A Aardema, Verna LG 3.3 0.5 1,333 F Swahili Tale 27104 EN Who's in Rabbit's House? Aardema, Verna LG 2.8 0.5 1,464 NF 5550 EN Why Mosquitoes Buzz in People's Aardema, Verna LG 4.0 0.5 1,219 F Ears: A West African Tale 913 EN Conejito Velloso, El Aargent, Dave/Pat U 1.3 0.5 182 F 5365 EN Great Summer Olympic Moments Aaseng, Nathan MG 7.9 2.0 12,708 F 5366 EN Great Winter Olympic Moments Aaseng, Nathan MG 7.4 2.0 11,404 F 15652 EN Meat-Eating Plants Aaseng, Nathan MG 6.8 1.0 5,734 NF 8480 EN Navajo Code Talkers Aaseng, Nathan UG 9.5 4.0 20,971 NF 900503 EN Life in Flatland (MH) Abbott, Edwin MG 5.2 0.5 2,099 F 65672 EN Magic Escapes, The Abbott, Tony MG 3.7 2.0 16,966 F 62264 EN Moon Scroll, The Abbott, Tony MG 3.7 2.0 13,345 F 54503 EN Under the Serpent Sea Abbott, Tony MG 3.6 2.0 11,398 F 89665 EN Voyagers of the Silver Sand Abbott, Tony MG 4.1 3.0 19,700 F 78108 EN Wizard or Witch? Abbott, Tony MG 3.3 -

Truth, Justice, and American Myth: the Manifestation of American Mythology in the Superhero Narrative
TRUTH, JUSTICE, AND AMERICAN MYTH: THE MANIFESTATION OF AMERICAN MYTHOLOGY IN THE SUPERHERO NARRATIVE by Richard Thomas Cruz A Thesis Submitted in Partial Fulfillment of the Requirements for the Degree of Master of Arts in English Middle Tennessee State University December 2014 Thesis Committee: Dr. David Lavery, Chair Dr. Jimmie Cain This thesis is dedicated to my father and my mother, the first superheroes I ever met. ii ACKNOWLEDGMENTS I thank my fiancé and best friend Laura Wilbanks for her continual encouragement and moral support. I also thank Caty Chapman, Jenny Rowan, Patricia Baines, and the entire Writing Center community for their academic and professional support. Were it not for the Writing Center and the professional opportunities it afforded me, I would never have completed this thesis. I thank Dr. Allison Smith and Dr. Julie Barger for their dedication to the MTSU teaching assistant community. I have grown more in the past two years thanks to my time working with them than perhaps at any other time in my professional life. Next, I thank Dr. Jimmie Cain for encouraging me to pursue English as my field of study. Your English 3000 class helped frighten and reassure a scared sophomore several years ago to continue writing, studying, and applying himself. Your constant support will forever stick with me as I continue my academic life. Finally, I thank Dr. David Lavery for his open-mindedness and support during the writing of this thesis. Thank you for tolerating my panicked moments, for remaining patient with me when I made mistakes and errors, and especially for never making me feel embarrassed for writing nearly 100 pages about costumed superheroes.