Santricity Storage Manager Installation Guide for Version 8.3X
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Beyond BIOS Developing with the Unified Extensible Firmware Interface
Digital Edition Digital Editions of selected Intel Press books are in addition to and complement the printed books. Click the icon to access information on other essential books for Developers and IT Professionals Visit our website at www.intel.com/intelpress Beyond BIOS Developing with the Unified Extensible Firmware Interface Second Edition Vincent Zimmer Michael Rothman Suresh Marisetty Copyright © 2010 Intel Corporation. All rights reserved. ISBN 13 978-1-934053-29-4 This publication is designed to provide accurate and authoritative information in regard to the subject matter covered. It is sold with the understanding that the publisher is not engaged in professional services. If professional advice or other expert assistance is required, the services of a competent professional person should be sought. Intel Corporation may have patents or pending patent applications, trademarks, copyrights, or other intellectual property rights that relate to the presented subject matter. The furnishing of documents and other materials and information does not provide any license, express or implied, by estoppel or otherwise, to any such patents, trademarks, copyrights, or other intellectual property rights. Intel may make changes to specifications, product descriptions, and plans at any time, without notice. Fictitious names of companies, products, people, characters, and/or data mentioned herein are not intended to represent any real individual, company, product, or event. Intel products are not intended for use in medical, life saving, life sustaining, critical control or safety systems, or in nuclear facility applications. Intel, the Intel logo, Celeron, Intel Centrino, Intel NetBurst, Intel Xeon, Itanium, Pentium, MMX, and VTune are trademarks or registered trademarks of Intel Corporation or its subsidiaries in the United States and other countries. -

Software Engineering a Abnormal End: Abend Abnormaal Einde De Beëindiging Van Een Proces Voordat Dat Proces Geheel Is Afgewerkt
1 Verklarende terminologielijst voor de Software Engineering A abnormal end: abend abnormaal einde De beëindiging van een proces voordat dat proces geheel is afgewerkt. abort (to) afbreken Een proces afbreken voordat het volledig is afgewerkt. absolute address absoluut adres Een adres dat permanent aan een eenheid of geheugenplaats is toegewezen en dat de eenheid of de geheugenplaats identificeert zonder dat daarvoor een vertaling of berekening nodig is. absolute assembler absoluut assembleerprogramma Een assembleerprogramma dat uitsluitend absolute code genereert. absolute code absolute code Code waarin alle adressen absoluut zijn. absolute coding absolute codering Een coderingsmethode waarin gebruik wordt gemaakt van instructies die absolute adressen bevatten. absolute expression absolute uitdrukking Een uitdrukking voorafgaande aan het moment waarop het assembleren van een programma plaatsvindt. Dit moment wordt niet beïnvloed door het verplaatsen van het programma. Een absolute uitdrukking kan een absoluut adres in een assembleertaal weergeven. absolute instruction absolute instructie 1. Een instructie in de definitieve uitvoerbare vorm. 2. Een computerinstructie waarin alle adressen uit absolute adressen bestaan. absolute loader absoluut laadprogramma Een programma dat een ander programma in het hoofdgeheugen kan plaatsen. Dit begint bij het initiële adres dat aan de code door het assembleerprogramma of de compiler is toegewezen en dat de adressen in de code niet verder wijzigt of aanpast. absolute load module absolute laadmodule 2 Een combinatie van werkmodules die op een gespecificeerd adres in het werkgeheugen wordt uitgevoerd. absolute machine code absolute machinecode Machinecode die steeds in vaste geheugenplaatsen moet worden geladen en niet mag worden verplaatst. Dit in tegenstelling tot verplaatsbare machinecode. absolute pathname absolute padnaam Een padnaam die de informatie bevat over de wijze waarop een bestand kan worden gevonden. -

IT Acronyms.Docx
List of computing and IT abbreviations /.—Slashdot 1GL—First-Generation Programming Language 1NF—First Normal Form 10B2—10BASE-2 10B5—10BASE-5 10B-F—10BASE-F 10B-FB—10BASE-FB 10B-FL—10BASE-FL 10B-FP—10BASE-FP 10B-T—10BASE-T 100B-FX—100BASE-FX 100B-T—100BASE-T 100B-TX—100BASE-TX 100BVG—100BASE-VG 286—Intel 80286 processor 2B1Q—2 Binary 1 Quaternary 2GL—Second-Generation Programming Language 2NF—Second Normal Form 3GL—Third-Generation Programming Language 3NF—Third Normal Form 386—Intel 80386 processor 1 486—Intel 80486 processor 4B5BLF—4 Byte 5 Byte Local Fiber 4GL—Fourth-Generation Programming Language 4NF—Fourth Normal Form 5GL—Fifth-Generation Programming Language 5NF—Fifth Normal Form 6NF—Sixth Normal Form 8B10BLF—8 Byte 10 Byte Local Fiber A AAT—Average Access Time AA—Anti-Aliasing AAA—Authentication Authorization, Accounting AABB—Axis Aligned Bounding Box AAC—Advanced Audio Coding AAL—ATM Adaptation Layer AALC—ATM Adaptation Layer Connection AARP—AppleTalk Address Resolution Protocol ABCL—Actor-Based Concurrent Language ABI—Application Binary Interface ABM—Asynchronous Balanced Mode ABR—Area Border Router ABR—Auto Baud-Rate detection ABR—Available Bitrate 2 ABR—Average Bitrate AC—Acoustic Coupler AC—Alternating Current ACD—Automatic Call Distributor ACE—Advanced Computing Environment ACF NCP—Advanced Communications Function—Network Control Program ACID—Atomicity Consistency Isolation Durability ACK—ACKnowledgement ACK—Amsterdam Compiler Kit ACL—Access Control List ACL—Active Current -

Certif Ication Handbook
Certification Handbook EXAM FC0-U51 TM TM CompTIA® IT Fundamentals™ (Exam FC0-U51) CompTIA® IT Fundamentals™ (Exam FC0-U51) 2 Chapter # | Name of chapter CompTIA® IT Fundamentals™ (Exam FC0-U51) CompTIA® IT Fundamentals™ (Exam FC0-U51) Part Number: 099004 Course Edition: 1.0 Acknowledgements We wish to thank the following project team for their contributions to the development of this certification study guide: Pamela J. Taylor, Laurie A. Perry, Gail Sandler, Jason Nufryk, Alex Tong, and Catherine M. Albano. Notices DISCLAIMER While CompTIA Properties, LLC takes care to ensure the accuracy and quality of these materials, we cannot guarantee their ac- curacy, and all materials are provided without any warranty whatsoever, including, but not limited to, the implied warranties of merchantability or fitness for a particular purpose. The name used in the data files for this course is that of a fictitious com- pany. Any resemblance to current or future companies is purely coincidental. We do not believe we have used anyone’s name in creating this course, but if we have, please notify us and we will change the name in the next revision of the course. Use of screenshots, photographs of another entity’s products, or another entity’s product name or service in this book is for edito- rial purposes only. No such use should be construed to imply sponsorship or endorsement of the book by, nor any affiliation of such entity with CompTIA Properties, LLC. This courseware may contain links to sites on the internet that are owned and operated by third parties (the “External Sites”). -

PC 97 Hardware Design Guide Provide Guidelines for Designing PC Systems That Best Run Windows 95 and Windows NT
Part 1 — Basic Design Issues C H A P T E R 1 PC 97 Design Issues “PC 97” represents the collection of PC system definitions and bus and device design requirements that make up the next generation of guidelines for the “Designed for Microsoft Windows” logo. This chapter introduces the PC 97 design issues for computer systems that run the Microsoft Windows family of operating systems for x86-based PCs and that run Windows NT on the RISC-based processor platform. For more information about design issues related to the OnNow design initiative and Win32 Driver Model, see the “OnNow and WDM for PC 97” chapter. Important The system requirements defined in PC 97 Hardware Design Guide provide guidelines for designing PC systems that best run Windows 95 and Windows NT. These design requirements are not related to the basic system requirements for running a Windows operating system. For information about the basic system requirements for running Windows 95 and Windows NT, see: http://www.microsoft.com/windows/mix/ Contents Evolving the PC Platform ........................... ................. 2 Logo Program at Microsoft for Hardware . .................... 3 Designing PCs for Windows 95 and Windows NT . ................... 5 Designing with New Bus and Device Support . .................... 6 SIPC and Designing for Ease of Use. .................... 7 Plug and Play and Designing for Extensibility . ........................ 9 Designing for x86-based and RISC-based PCs. .................... 11 References for PC 97 Design Issues . ................... 13 2 PC 97 Design — Part 1 Basic Design Issues Evolving the PC Platform Every member of the PC industry has an important business goal that involves growing the PC market among business and home users. -

Digital Alphastation 250 Series User Information
Digital AlphaStation™ 250 Series User Information Order Number: EK-PCCTA-UI. A01 Digital Equipment Corporation Maynard, Massachusetts January 1995 The information in this document is subject to change without notice and should not be construed as a commitment by Digital Equipment Corporation. Digital Equipment Corporation assumes no responsibility for any errors that might appear in this document. The software, if any, described in this document is furnished under a license and may be used or copied only in accordance with the terms of such license. No responsibility is assumed for the use or reliability of software or equipment that is not supplied by Digital Equipment Corporation or its affiliated companies. Restricted Rights: Use, duplication, or disclosure by the U.S. Government is subject to restrictions as set forth in subparagraph (c) (1) (ii) of the Rights in Technical Data and Computer Software clause at DFARS 252.227-7013. Copyright 1995 Digital Equipment Corporation. All Rights Reserved. The following are trademarks of Digital Equipment Corporation: AlphaGeneration, AlphaStation, DEC, Digital, OpenVMS, ThinWire, and the DIGITAL logo. The following are third-party trademarks: Microsoft and Windows NT are registered trademarks of Microsoft Corporation. SIMM is a trademark of Molex Corporation. OSF/1 is a trademark of the Open Software Foundation, Inc. All other trademarks or registered trademarks are the property of their respective holders. This document was produced with Microsoft Word for Windows, V2.0c. FCC Information - Class B This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to Part 15 of the FCC rules. -

1. Installing Gentoo
1. Installing Gentoo In this part you learn how to install Gentoo on your system. Content: 1. About the Gentoo Linux Installation Users not familiar with Gentoo do not always know that choice is what Gentoo is all about. 2. Choosing the Right Installation Medium You can install Gentoo in many ways. You can use our LiveCD, an existing distribution etc. 3. Configuring your Network If you want to install Gentoo using the Internet, you need to setup networking. 4. Preparing the Disks To be able to install Gentoo, you must create the necessary partitions. This chapter describes how to partition a disk for future usage. 5. Installing the Gentoo Installation Files Gentoo installs work through socalled stage-files. In this chapter we describe how you extract a stage-file and configure Portage. 6. Installing the Gentoo Base System Independent of what stage you chose, the eventual result is that you have a Gentoo base system at your disposal. This chapter describes how to progress to that stadium. 7. Configuring the Kernel The Linux kernel is the core of every distribution. This chapter explains how to configure your kernel. 8. Configuring your System You need to edit some important configuration files. In this chapter you receive an overview of these files and an explanation on how to proceed. 9. Configuring the Bootloader Several bootloaders exist. Each one of them has its own way of configuration. In this chapter we'll describe all possibilities for you and step you through the process of configuring a bootloader to your needs. 10. Installing Necessary System Tools As mentioned before, Gentoo is about choices. -

Computer Abbreviation Dictionary
A... AA Auto Answer AAB All-to-All Broadcast AAL Asynchronous Transfer Mode Adaptation Layer AAP Applications Access Point [DEC] AAS All-to-All Scatter AASP ASCII Asynchronous Support Package AAT Average Access Time ABC * Atanasoff-Berry Computer (First digital Calculating machine that used vacuum tubes) ABEND Abnormal End ABI Application Binary Interface ABIOS Advanced BIOS ABIST Automatic Built-In Self-Test [IBM] ABLE Adaptive Battery Life Extender ABR Available Bit Rate ABRS Automated Book Request System [British Library] ABS Absolute ABT Abort ABTS ASCII Block Terminal Services AC Autocheck + Automatic Computer + Alternating Current ACC Accumulator ACD Automated Call Distribution + Automatic Call Distributor ACDI Asynchronous Communications Device Interface ACE Advanced Computing Environment [SCO] + Adverse Channel Enhancements [Microcom] + * Automatic Computing Engine ACF Access Control Field + Advanced Communications Function ACH Automated Clearing House ACIAS Automated Calibration Interval Analysis System ACIS American Committee for Interoperable Systems ACK Acknowledgment ACL Access Control List ACM Association for Computing Machinery Audio Compression Manager [Microsoft] ACMS Application Control Management System ACP Ancillary Control Program + Auxiliary Control Process ACROSS Automated Cargo Release and Operations Service System ACS Access + Access Control Set + Access Control System + Asynchronous Communication Server ACTS Automated Computer Time Service ACTT Advanced Communication and Timekeeping Technology [Seiko] ACU Automatic -

COMPUTER ABBREVIATIONS [Copyright: TECHNOART Co
COMPUTER ABBREVIATIONS [Copyright: TECHNOART Co. Ltd.] References: Magazines: Nikkei Electronics, Nikkei Microdevices, Nikkei Mechanical, etc. News papers: Nikkei Industrial Journal, Dempa Journal White papers: IEEE, IEC, SMPTE, Internet Websites, format specifications, etc. Others: encyclopedias, instruction booklets, catalogues, product spec., etc. ABBREVIATION DERIVATION OF ABBREVIATION 3D DDI 3 Dimensional Device Driver Interface 4GL 4th generation language A3D Aural 3D ABI application binary interface ABS air bearing surface ACSM Application Control State Machine ADB Apple Desktop Bus ADE automatic design engineering AIF application integration feature AOAC always on/always connected APIC Advanced Programmable Interrupt Controller APM Advanced Power Management APNIC Asia Pacific Network Information Center ARC Advanced RISC Computing ATMS Automated Traffic Management Systems AT-UD Unimodem Diagnostics Command AWT Abstract Window Toolkit BAR base address register BBS bulletin board system bcc blind carbon copy BCL bias compensation layer BIPS billion instructions per second BIS boot integrity services BLOB Binary Large Object BML Broadcast Markup Language BNF Backup Naur Form BPR business process reengineering BSDL Boundary Scan Description Language BTL backplane transceiver logic BTRON Business TRON C&C computer and communication CBQ class-based queuing CDA Compound Document Architecture CDB Command Description Block CDC Connected Device Configuration CDDI copper distributed data interface CDF Channel Definition Format CDFF Common -
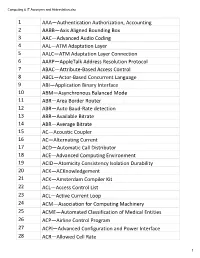
Computing & IT Acronyms and Abbreviation.Xlsx
Computing & IT Acronyms and Abbreviation.xlsx 1 AAA—Authentication Authorization, Accounting 2 AABB—Axis Aligned Bounding Box 3 AAC—Advanced Audio Coding 4 AAL—ATM Adaptation Layer 5 AALC—ATM Adaptation Layer Connection 6 AARP—AppleTalk Address Resolution Protocol 7 ABAC—Attribute-Based Access Control 8 ABCL—Actor-Based Concurrent Language 9 ABI—Application Binary Interface 10 ABM—Asynchronous Balanced Mode 11 ABR—Area Border Router 12 ABR—Auto Baud-Rate detection 13 ABR—Available Bitrate 14 ABR—Average Bitrate 15 AC—Acoustic Coupler 16 AC—Alternating Current 17 ACD—Automatic Call Distributor 18 ACE—Advanced Computing Environment 19 ACID—Atomicity Consistency Isolation Durability 20 ACK—ACKnowledgement 21 ACK—Amsterdam Compiler Kit 22 ACL—Access Control List 23 ACL—Active Current Loop 24 ACM—Association for Computing Machinery 25 ACME—Automated Classification of Medical Entities 26 ACP—Airline Control Program 27 ACPI—Advanced Configuration and Power Interface 28 ACR—Allowed Cell Rate 1 Computing & IT Acronyms and Abbreviation.xlsx 29 ACR—Attenuation to Crosstalk Ratio 30 AD—Active Directory 31 AD—Administrative Domain 32 ADC—Analog-to-Digital Converter 33 ADC—Apple Display Connector 34 ADB—Apple Desktop Bus 35 ADCCP—Advanced Data Communications Control Procedures 36 ADO—ActiveX Data Objects 37 ADSL—Asymmetric Digital Subscriber Line 38 ADT—Abstract Data Type 39 AE—Adaptive Equalizer 40 AES—Advanced Encryption Standard 41 AF—Anisotropic Filtering 42 AFP—Apple Filing Protocol 43 AGP—Accelerated Graphics Port 44 AH—Active Hub 45 AI—Artificial -

Installing Debian GNU/Linux 3.0 for Alpha
Installing Debian GNU/Linux 3.0 For Alpha Bruce Perens Sven Rudolph Igor Grobman James Treacy Adam Di Carlo version 3.0.24, 18 December, 2002 Abstract This document contains installation instructions for the Debian GNU/Linux 3.0 system, for the Alpha (“alpha”) architecture. It also contains pointers to more information and information on how to make the most of your new Debian system. The procedures in this document are not to be used for users upgrading existing systems; if you are upgrading, see the Release Notes for Debian 3.0 (http://www.debian.org/releases/woody/alpha/release-notes/). Copyright Notice This document may be distributed and modified under the terms of the GNU General Public License. © 1996 Bruce Perens © 1996, 1997 Sven Rudolph © 1998 Igor Grobman, James Treacy © 1998–2002 Adam Di Carlo This manual is free software; you may redistribute it and/or modify it under the terms of the GNU General Public License as published by the Free Software Foundation; either version 2, or (at your option) any later version. This manual is distributed in the hope that it will be useful, but without any warranty; without even the implied warranty of merchantability or fitness for a particular purpose. See the GNU General Public License for more details. A copy of the GNU General Public License is available as /usr/share/common-licenses /GPL in the Debian GNU/Linux distribution or on the World Wide Web at the GNU website (http://www.gnu.org/copyleft/gpl.html). You can also obtain it by writing to the Free Software Foundation, Inc., 59 Temple Place - Suite 330, Boston, MA 02111-1307, USA. -

CYBERSECURITY When Will You Be Hacked?
SUFFOLK ACADEMY OF LAW The Educational Arm of the Suffolk County Bar Association 560 Wheeler Road, Hauppauge, NY 11788 (631) 234-5588 CYBERSECURITY When Will You Be Hacked? FACULTY Victor John Yannacone, Jr., Esq. April 26, 2017 Suffolk County Bar Center, NY Cybersecurity Part I 12 May 2017 COURSE MATERIALS 1. A cybersecurity primer 3 – 1.1. Cybersecurity practices for law firms 5 – 1.2. Cybersecurity and the future of law firms 11 – 2. Information Security 14 – 2.1. An information security policy 33 – 2.2. Data Privacy & Cloud Computing 39 – 2.3. Encryption 47 – 3. Computer security 51 – 3.1. NIST Cybersecurity Framework 77 – 4. Cybersecurity chain of trust; third party vendors 113 – 5. Ransomware 117 – 5.1. Exploit kits 132 – 6. Botnets 137 – 7. BIOS 139 – 7.1. Universal Extensible Firmware Interface (UEFI) 154– 8. Operating Systems 172 – 8.1. Microsoft Windows 197 – 8.2. macOS 236– 8.3. Open source operating system comparison 263 – 9. Firmware 273 – 10. Endpoint Security Buyers Guide 278 – 11. Glossaries & Acronym Dictionaries 11.1. Common Computer Abbreviations 282 – 11.2. BABEL 285 – 11.3. Information Technology Acronymns 291 – 11.4. Glossary of Operating System Terms 372 – 2 Cyber Security Primer Network outages, hacking, computer viruses, and similar incidents affect our lives in ways that range from inconvenient to life-threatening. As the number of mobile users, digital applications, and data networks increase, so do the opportunities for exploitation. Cyber security, also referred to as information technology security, focuses on protecting computers, networks, programs, and data from unintended or unauthorized access, change, or destruction.