In Concert with Teaching Strategies That Have a Solid Theoretical Basis
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

A Method of Content-Based Image Retrieval for the Generation of Image Mosaics
University of Central Florida STARS Electronic Theses and Dissertations, 2004-2019 2007 A Method Of Content-based Image Retrieval For The Generation Of Image Mosaics Michael Snead University of Central Florida Part of the Computer Engineering Commons Find similar works at: https://stars.library.ucf.edu/etd University of Central Florida Libraries http://library.ucf.edu This Masters Thesis (Open Access) is brought to you for free and open access by STARS. It has been accepted for inclusion in Electronic Theses and Dissertations, 2004-2019 by an authorized administrator of STARS. For more information, please contact [email protected]. STARS Citation Snead, Michael, "A Method Of Content-based Image Retrieval For The Generation Of Image Mosaics" (2007). Electronic Theses and Dissertations, 2004-2019. 3358. https://stars.library.ucf.edu/etd/3358 A METHOD OF CONTENT-BASED IMAGE RETRIEVAL FOR THE GENERATION OF IMAGE MOSAICS by MICHAEL CHRISTOPHER SNEAD B.S. University of Central Florida, 2005 A thesis submitted in partial fulfillment of the requirements for the degree of Master of Science in the School of Electrical Engineering and Computer Science in the College of Engineering & Computer Science at the University of Central Florida Orlando, Florida Spring Term 2007 © 2007 Michael Christopher Snead ii ABSTRACT An image mosaic is an artistic work that uses a number of smaller images creatively combined together to form another larger image. Each building block image, or tessera, has its own distinctive and meaningful content, but when viewed from a distance the tesserae come together to form an aesthetically pleasing montage. This work presents the design and implementation of MosaiX, a computer software system that generates these image mosaics automatically. -

First Semester
NATIONAL UNIVERSITY F o u r t h Y e a r S y l l a b u s D e p a r t m e n t of Computer Science and Engineering Four Year B.Sc. Honours Course Effective from the Session: 2017–2018 National University Subject: Computer Science and Engineering Syllabus for Four Year B.Sc. Honours Course Effective from the Session: 2017-2018 Year wise courses and marks distribution FOURTH YEAR Semester VII Course Code Course Title Credit Hours 540201 Artificial Intelligence 3.0 540202 Artificial Intelligence Lab 1.5 540203 Compiler Design and Construction 3.0 540204 Compiler Design Lab 1.5 540205 Computer Graphics 3.0 540206 Computer Graphics Lab 1.5 540207 E-Commerce and Web Engineering 3.0 540208 E-Commerce and Web Engineering Lab 1.5 Total Credits in 7th Semester 18.0 Semester VIII Course Code Course Title Credit Hours Major Theory Courses 540209 Network and Information Security 3.0 540210 Network and Information Security Lab 1.5 540211 Information System Management 3.0 Project/Industry Attachment 540240 Project/Industry Attachment 6.0 Optional Course (any one) 3.0 540212 Simulation and Modeling 540214 Parallel and Distributed Systems 540216 Digital Signal Processing 540218 Digital Image Processing 540220 Multimedia 540222 Pattern Recognition 540224 Design and Analysis of VLSI Systems 540226 Micro-controller and Embedded System 540228 Cyber Law and Computer Forensic 540230 Natural Language Processing 540232 System Analysis and Design 540234 Optical Fiber Communication 540236 Human Computer Interaction 540238 Graph Theory Page 2 of 18 Optional Course -

Working with Colors
Working With Colors INK: The physical form of color; Ink is how color is applied to paper There are two different types of inks: • TRANSPARENT INKS are commonly used in printing • OPAQUE INKS are considered a specialty ink and generally cost more COLOR: in printing, there are two types of color modes: • SPOT COLOR; aka: Match color, PMS color, Solid color • 4-COLOR PRocESS; aka: Process, CMYK Working With Colors With Working SPot COLOR • A pre-mixed color; a color mixed prior to the printing press PMS : PANtoNE MAtcHING SYSTEM • Color system that has several color libraries for reference in reproducing color • Popular PMS color libraries: • Spot color Formula guide (coated, uncoated, and matte versions) solid color guide that identifies specific colors • 4-Color Process Guide (coated and uncoated versions) identifies colors using CMYK inks • Color Bridge (coated and uncoated versions) using the colors from the spot color Formula guide this book shows the difference Working With Colors With Working between a spot color and the same color when converted to CMYK • Metallic Inks • Pastels • Tints • www.pantone.com COATED: Paper stock that has been treated with a special coating in order to have a glossy appearance. • Ink sits on this type of paper stock as a result of the glossy coating • Colors appear to be brighter compared to uncoated paper Matte: coated paper stock that has been dulled UNcoATED : Paper stock that has not been treated; it has no coating. • Ink is absorbed into this type of paper stock • Ink color appears darker and duller Working With Colors With Working BENEFit OF USING SPot coLOR: • consistent color within a print job. -

Chapter 2 Fundamentals of Digital Imaging
Chapter 2 Fundamentals of Digital Imaging Part 4 Color Representation © 2016 Pearson Education, Inc., Hoboken, 1 NJ. All rights reserved. In this lecture, you will find answers to these questions • What is RGB color model and how does it represent colors? • What is CMY color model and how does it represent colors? • What is HSB color model and how does it represent colors? • What is color gamut? What does out-of-gamut mean? • Why can't the colors on a printout match exactly what you see on screen? © 2016 Pearson Education, Inc., Hoboken, 2 NJ. All rights reserved. Color Models • Used to describe colors numerically, usually in terms of varying amounts of primary colors. • Common color models: – RGB – CMYK – HSB – CIE and their variants. © 2016 Pearson Education, Inc., Hoboken, 3 NJ. All rights reserved. RGB Color Model • Primary colors: – red – green – blue • Additive Color System © 2016 Pearson Education, Inc., Hoboken, 4 NJ. All rights reserved. Additive Color System © 2016 Pearson Education, Inc., Hoboken, 5 NJ. All rights reserved. Additive Color System of RGB • Full intensities of red + green + blue = white • Full intensities of red + green = yellow • Full intensities of green + blue = cyan • Full intensities of red + blue = magenta • Zero intensities of red , green , and blue = black • Same intensities of red , green , and blue = some kind of gray © 2016 Pearson Education, Inc., Hoboken, 6 NJ. All rights reserved. Color Display From a standard CRT monitor screen © 2016 Pearson Education, Inc., Hoboken, 7 NJ. All rights reserved. Color Display From a SONY Trinitron monitor screen © 2016 Pearson Education, Inc., Hoboken, 8 NJ. -

Computational RYB Color Model and Its Applications
IIEEJ Transactions on Image Electronics and Visual Computing Vol.5 No.2 (2017) -- Special Issue on Application-Based Image Processing Technologies -- Computational RYB Color Model and its Applications Junichi SUGITA† (Member), Tokiichiro TAKAHASHI†† (Member) †Tokyo Healthcare University, ††Tokyo Denki University/UEI Research <Summary> The red-yellow-blue (RYB) color model is a subtractive model based on pigment color mixing and is widely used in art education. In the RYB color model, red, yellow, and blue are defined as the primary colors. In this study, we apply this model to computers by formulating a conversion between the red-green-blue (RGB) and RYB color spaces. In addition, we present a class of compositing methods in the RYB color space. Moreover, we prescribe the appropriate uses of these compo- siting methods in different situations. By using RYB color compositing, paint-like compositing can be easily achieved. We also verified the effectiveness of our proposed method by using several experiments and demonstrated its application on the basis of RYB color compositing. Keywords: RYB, RGB, CMY(K), color model, color space, color compositing man perception system and computer displays, most com- 1. Introduction puter applications use the red-green-blue (RGB) color mod- Most people have had the experience of creating an arbi- el3); however, this model is not comprehensible for many trary color by mixing different color pigments on a palette or people who not trained in the RGB color model because of a canvas. The red-yellow-blue (RYB) color model proposed its use of additive color mixing. As shown in Fig. -

C9600 Printing Guide V1.0
Copyright Information Copyright © 2007 by Oki Data. All Rights Reserved Document Information ________________________________ C9600 Printing Guide P/N 59373001 Revision 3.0 February, 2007 Disclaimer__________________________________________ Every effort has been made to ensure that the information in this document is complete, accurate, and up-to-date. The manufacturer assumes no responsibility for the results of errors beyond its control. The manufacturer also cannot guarantee that changes in software and equipment made by other manufacturers and referred to in this guide will not affect the applicability of the information in it. Mention of software products manufactured by other companies does not necessarily constitute endorsement by the manufacturer . While all reasonable efforts have been made to make this document as accurate and helpful as possible, we make no warranty of any kind, expressed or implied, as to the accuracy or completeness of the information contained herein. The most up-to-date drivers and manuals are available from the web site: http://www.okiprintingsolutions.com Trademark Information _______________________________ Oki and Oki Printing Solutions are registered trademarks of Oki Electric Industry Company Ltd. Adobe and PostScript are registered trademarks of Adobe Systems. Apple, Macintosh, Mac, and Mac OS are registered trademarks of Apple Computers Inc. Hewlett-Packard, HP, and LaserJet are registered trademarks of Hewlett-Packard Company. Microsoft, MS-DOS and Windows are either registered trademarks or trademarks -

Basics of Color Management
Application Notes Basics of Color Management Basics of Color Management ErgoSoft AG Moosgrabenstr. 13 CH-8595 Altnau, Switzerland © 2010 ErgoSoft AG, All rights reserved. The information contained in this manual is based on information available at the time of publication and is sub- ject to change without notice. Accuracy and completeness are not warranted or guaranteed. No part of this manual may be reproduced or transmitted in any form or by any means, including electronic me- dium or machine-readable form, without the expressed written permission of ErgoSoft AG. Brand or product names are trademarks of their respective holders. The ErgoSoft RIP is available in different editions. Therefore the description of available features in this document does not necessarily reflect the license details of your edition of the ErgoSoft RIP. For information on the features included in your edition of the ErgoSoft RIPs refer to the ErgoSoft homepage or contact your dealer. Rev. 1.1 Basics of Color Management i Contents Introduction ................................................................................................................................................................. 1 Color Spaces ................................................................................................................................................................ 1 Basics ........................................................................................................................................................................ 1 CMYK ....................................................................................................................................................................... -

14. Color Mapping
14. Color Mapping Jacobs University Visualization and Computer Graphics Lab Recall: RGB color model Jacobs University Visualization and Computer Graphics Lab Data Analytics 691 CMY color model • The CMY color model is related to the RGB color model. •Itsbasecolorsare –cyan(C) –magenta(M) –yellow(Y) • They are arranged in a 3D Cartesian coordinate system. • The scheme is subtractive. Jacobs University Visualization and Computer Graphics Lab Data Analytics 692 Subtractive color scheme • CMY color model is subtractive, i.e., adding colors makes the resulting color darker. • Application: color printers. • As it only works perfectly in theory, typically a black cartridge is added in practice (CMYK color model). Jacobs University Visualization and Computer Graphics Lab Data Analytics 693 CMY color cube • All colors c that can be generated are represented by the unit cube in the 3D Cartesian coordinate system. magenta blue red black grey white cyan yellow green Jacobs University Visualization and Computer Graphics Lab Data Analytics 694 CMY color cube Jacobs University Visualization and Computer Graphics Lab Data Analytics 695 CMY color model Jacobs University Visualization and Computer Graphics Lab Data Analytics 696 CMYK color model Jacobs University Visualization and Computer Graphics Lab Data Analytics 697 Conversion • RGB -> CMY: • CMY -> RGB: Jacobs University Visualization and Computer Graphics Lab Data Analytics 698 Conversion • CMY -> CMYK: • CMYK -> CMY: Jacobs University Visualization and Computer Graphics Lab Data Analytics 699 HSV color model • While RGB and CMY color models have their application in hardware implementations, the HSV color model is based on properties of human perception. • Its application is for human interfaces. Jacobs University Visualization and Computer Graphics Lab Data Analytics 700 HSV color model The HSV color model also consists of 3 channels: • H: When perceiving a color, we perceive the dominant wavelength. -

Color Detection and Mixing System
International Journal of Computer Applications Technology and Research Volume 6–Issue 9, 431-433, 2017, ISSN:-2319–8656 Color Detection and Mixing System Khalid Ammar Amira Duhair Lara Bilal Department of Computer Eng Department of Computer Eng Department of Computer Eng Ajman University Ajman University Ajman University Ajman, UAE Ajman, UAE Ajman, UAE Abstract: The detection of the color value and the automation of its production is very useful for many industrial applications. [3, 4]. We have developed a microcontroller-based system that detects colors and controls the mixing of the primary colors to get the matching colors. The system can be used as a tool to determine the compositions of chosen colors and produce a matching colors that meets the requirement of the required colors. The system can make the production of the colors much faster, more reliable and more consistent. This document describes the design, the implementation of the system. The system can be used as a tool in different industries such as digital printing, textile, cosmetics, wallpaper, gift-wrap, building materials, signage, etc [3, 4]. Keywords: Digital paint, Color making and mixing, digital printing, paint products. 1. INTRODUCTION All colors that we can see can be composed from a set of primary colors [5,6,7]. Detection of the composition of chosen color and its automated generation has a wide range of applications [3,4]. A color models (known as color spaces) can represent a chosen color using a set of primary colors mapped to the color model in discrete values. Many color models are used to describe colors, each model is used for RGB CMYK different purposes and different areas of applications. -
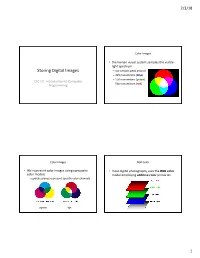
Storing Digital Images – Our Sensors Peak Around – 425 Nanometers (Blue) – 550 Nanometers (Green) CSC121, Introduction to Computer – 560 Nanometers (Red) Programming
2/3/18 Color Images • the human visual system samples the visible light spectrum Storing Digital Images – our sensors peak around – 425 nanometers (blue) – 550 nanometers (green) CSC121, Introduction to Computer – 560 nanometers (red) Programming Color Images RGB Color • We represent color images using composite • most digital photography uses the RGB color color models model employing additive color primaries – separate planes represent specific color channels pigments light 1 2/3/18 RGB Color RGB Color • has three distinct channels: RED, GREEN, and • We will separate the image to compare the BLUE color channels each channel is shown as an intensity image to indicate the relative amount that the color contributes to the composite image RGB Color RGB Color • We will separate the image to compare the • We will separate the image to compare the color channels color channels RED CHANNEL GREEN CHANNEL NOTE: high intensity means high amounts of red; dark means low amounts 2 2/3/18 RGB Color CMYK Color • We will separate the image to compare the • The CYAN-MAGENTA- CYAN color channels YELLOW-BLACK* or CMYK color model is GREEN used for printing and BLUE based on subtractive BLACK WHITE BLUE CHANNEL primaries YELLOW MAGENTA RED *Black is added for print efficiency CMY Color Cube Color Images Color Images • the alpha channel is a fourth channel that is • We will be using mostly used as a mask to specify the JPEG images for our transparency/opacity of pixels in the programming composite image • Joint Photographers Expert Group images – baseline: -

2 9215FQ14 FREQUENTLY ASKED QUESTIONS Category Pages Facilities & Buildings 3-10 General Reference 11-20 Human Resources
2 FREQUENTLY ASKED QUESTIONS Category Pages Facilities & Buildings 3-10 General Reference 11-20 Human Resources 21-22 Legal 23-25 Marketing 26 Personal Names (Individuals) 27 Predecessor Companies 28-29 Products & Services 30-89 Public Relations 90 Research 91-97 April 10, 2007 9215FQ14 3 Facilities & Buildings Q. When did IBM first open its offices in my town? A. While it is not possible for us to provide such information for each and every office facility throughout the world, the following listing provides the date IBM offices were established in more than 300 U.S. and international locations: Adelaide, Australia 1914 Akron, Ohio 1917 Albany, New York 1919 Albuquerque, New Mexico 1940 Alexandria, Egypt 1934 Algiers, Algeria 1932 Altoona, Pennsylvania 1915 Amsterdam, Netherlands 1914 Anchorage, Alaska 1947 Ankara, Turkey 1935 Asheville, North Carolina 1946 Asuncion, Paraguay 1941 Athens, Greece 1935 Atlanta, Georgia 1914 Aurora, Illinois 1946 Austin, Texas 1937 Baghdad, Iraq 1947 Baltimore, Maryland 1915 Bangor, Maine 1946 Barcelona, Spain 1923 Barranquilla, Colombia 1946 Baton Rouge, Louisiana 1938 Beaumont, Texas 1946 Belgrade, Yugoslavia 1926 Belo Horizonte, Brazil 1934 Bergen, Norway 1946 Berlin, Germany 1914 (prior to) Bethlehem, Pennsylvania 1938 Beyrouth, Lebanon 1947 Bilbao, Spain 1946 Birmingham, Alabama 1919 Birmingham, England 1930 Bogota, Colombia 1931 Boise, Idaho 1948 Bordeaux, France 1932 Boston, Massachusetts 1914 Brantford, Ontario 1947 Bremen, Germany 1938 9215FQ14 4 Bridgeport, Connecticut 1919 Brisbane, Australia -

LCSH Section I
I(f) inhibitors I-215 (Salt Lake City, Utah) Interessengemeinschaft Farbenindustrie USE If inhibitors USE Interstate 215 (Salt Lake City, Utah) Aktiengesellschaft Trial, Nuremberg, I & M Canal National Heritage Corridor (Ill.) I-225 (Colo.) Germany, 1947-1948 USE Illinois and Michigan Canal National Heritage USE Interstate 225 (Colo.) Subsequent proceedings, Nuremberg War Corridor (Ill.) I-244 (Tulsa, Okla.) Crime Trials, case no. 6 I & M Canal State Trail (Ill.) USE Interstate 244 (Tulsa, Okla.) BT Nuremberg War Crime Trials, Nuremberg, USE Illinois and Michigan Canal State Trail (Ill.) I-255 (Ill. and Mo.) Germany, 1946-1949 I-5 USE Interstate 255 (Ill. and Mo.) I-H-3 (Hawaii) USE Interstate 5 I-270 (Ill. and Mo. : Proposed) USE Interstate H-3 (Hawaii) I-8 (Ariz. and Calif.) USE Interstate 255 (Ill. and Mo.) I-hadja (African people) USE Interstate 8 (Ariz. and Calif.) I-270 (Md.) USE Kasanga (African people) I-10 USE Interstate 270 (Md.) I Ho Yüan (Beijing, China) USE Interstate 10 I-278 (N.J. and N.Y.) USE Yihe Yuan (Beijing, China) I-15 USE Interstate 278 (N.J. and N.Y.) I Ho Yüan (Peking, China) USE Interstate 15 I-291 (Conn.) USE Yihe Yuan (Beijing, China) I-15 (Fighter plane) USE Interstate 291 (Conn.) I-hsing ware USE Polikarpov I-15 (Fighter plane) I-394 (Minn.) USE Yixing ware I-16 (Fighter plane) USE Interstate 394 (Minn.) I-K'a-wan Hsi (Taiwan) USE Polikarpov I-16 (Fighter plane) I-395 (Baltimore, Md.) USE Qijiawan River (Taiwan) I-17 USE Interstate 395 (Baltimore, Md.) I-Kiribati (May Subd Geog) USE Interstate 17 I-405 (Wash.) UF Gilbertese I-19 (Ariz.) USE Interstate 405 (Wash.) BT Ethnology—Kiribati USE Interstate 19 (Ariz.) I-470 (Ohio and W.