Kerio-Control-Adminguide-En.Pdf
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Variational Text Linguistics: Revisiting Register in English
Christoph Schubert and Christina Sanchez-Stockhammer (Eds.) Variational Text Linguistics Topics in English Linguistics Editors Elizabeth Closs Traugott Bernd Kortmann Volume 90 Variational Text Linguistics Revisiting Register in English Edited by Christoph Schubert Christina Sanchez-Stockhammer ISBN 978-3-11-044310-3 e-ISBN (PDF) 978-3-11-044355-4 e-ISBN (EPUB) 978-3-11-043533-7 ISSN 1434-3452 Library of Congress Cataloging-in-Publication Data A CIP catalog record for this book has been applied for at the Library of Congress. Bibliographic information published by the Deutsche Nationalbibliothek The Deutsche Nationalbibliothek lists this publication in the Deutsche Nationalbibliografie; detailed bibliographic data are available on the Internet at http://dnb.dnb.de. © 2016 Walter de Gruyter GmbH, Berlin/Boston Cover image: Brian Stablyk/Photographer’s Choice RF/Getty Images Typesetting: fidus Publikations-Service GmbH, Nördlingen Printing and binding: CPI books GmbH, Leck ♾ Printed on acid-free paper Printed in Germany www.degruyter.com Acknowledgements The foundations for this edited collection of articles were laid at the interna- tional conference Register revisited: New perspectives on functional text variety in English, which took place at the University of Vechta, Germany, from June 27 to 29, 2013. The aim of the present volume is to conserve the research papers and many inspiring discussions which were stimulated then and to make them available to a larger audience. It was only possible to achieve this aim thanks to the help of many people joining us in the effort. First and foremost, we would like to thank all contributors for their continued cooperation in this project. -

Anyconnect および Host Scan のアンチウイルス/アンチスパイウェア
AnyConnect および Host Scan のアンチウイルス/アンチスパイウェア/ファイアウォール サポート表 AnyConnect ポスチャ モジュールにより、AnyConnect Secure Mobility クライアントはホストにインス トールされているオペレーティング システム、およびアンチウイルス、アンチスパイウェア、ファイアウォールの 各ソフトウェアを識別できます。 Host Scan アプリケーションはポスチャ モジュールのコンポーネントに含まれ る、こうした情報を収集するアプリケーションです。 AnyConnect 3.0 より、Host Scan パッケージは AnyConnect Secure Mobility クライアントおよび Cisco Secure Desktop(CSD)の共有コンポーネントになっています。 それ以前は、Host Scan パッケージは CSD を インストールすることによってのみ利用可能になるコンポーネントの 1 つでした。 Host Scan パッケージを CSD から分離したのは、CSD の一部として提供されていたときよりも、ユー ザが頻繁に Host Scan サポート表を更新できるようにするためです。 このサポート表には、ユーザが動的なア クセス ポリシーで使用しているアンチウイルス/アンチスパイウェア/ファイアウォール アプリケーションの製品 名とバージョン情報が記載されています。 シスコでは、Host Scan パッケージに Host Scan アプリケーション、 Host Scan サポート表、および他のコンポーネントを含めて提供しています。 Host Scan サポート表のリスト アンチウイルス アプリケーション総合リスト アンチスパイウェア アプリケーション総合リスト ファイアウォール アプリケーション総合リスト Windows 用アンチウイルス Windows 用アンチスパイウェア Windows 用ファイアウォール Linux 用アンチウイルス Linux 用ファイアウォール Mac OS 用アンチウイルス Mac OS 用アンチスパイウェア Mac OS 用ファイアウォール A B C D E F G H I J K L M N O P Q R S T U V W X Y Z AA AB AC AD AE ファイル データ ファ バージョ データ ファイ データ ファイル データ ファイ エンジンのバー RTP の RTP の 前回のスキャン スキャン/クリー システムのフル アンイン GUI のアク トレイ アイコンの トレイ アイコン 有効期 脅威ログの取 スキャン プログラ フル スキャンの進捗 インストール ディ 一括スキャ メモリ スキャ アンチウイルス製品名 ライブ更新 サービス GUI の表示 のスキャ 有効日の取得 更新の進捗表示 プログラム言語の取得 イル dir の取 市場での別名 ン ルの時刻 のバージョン ルの署名 ジョン チェック 設定 時刻 ニング スキャン ストール ティブ化 表示 の非表示 限 得 ムの実行 表示 レクトリの取得 ン ン 1 ン 得 2 3 360Safe.com 4 360 Antivirus 1.x 9989999898888898 8888 8 9 8 9 9 9 88 5 360杀毒 1.x 9999988898888898 8889 8 8 8 9 9 9 88 6 AEC, spol. s r.o. 7 TrustPort Antivirus 2.x 8888998899888999 9888 8 9 8 9 8 988 8 Agnitum Ltd. -

Biology 3596B – Genomics and Beyond – Winter 2021
Department of Biology BIOLOGY 3596B – GENOMICS AND BEYOND – WINTER 2021 Welcome to Bio 3596! My goal is to help you learn and be successful! Please, read and keep this course outline handy, because it is an official document that contains important course information. 1. General Course Information ...................................................................................................................................... 2 1.1. Course Information ............................................................................................................................ 2 Course description .............................................................................................................................................................. 2 List of Prerequisites ............................................................................................................................................................ 2 Mode of delivery ................................................................................................................................................................ 2 Technical requirements: ..................................................................................................................................................... 2 1.2. Online Participation and Engagement: contribution to community learning ....................................... 3 1.3. Key Sessional Dates ........................................................................................................................... -

Personal Firewalls Are a Necessity for Solo Users
Personal firewalls are a necessity for solo users COMPANY PRODUCT PLATFORM NOTES PRICE Aladdin Knowledge Systems Ltd. SeSafe Desktop Windows Combines antivirus with content filtering, blocking and $72 Arlington Heights, Ill. monitoring 847-808-0300 www.ealaddin.com Agnitum Inc. Outpost Firewall Pro Windows Blocks ads, sites, programs; limits access by specific times $40 Nicosia, Cyprus www.agnitum.com Computer Associates International Inc. eTrust EZ Firewall Windows Basic firewall available only by download $40/year Islandia, N.Y. 631-342-6000 my-etrust.com Deerfield Canada VisNetic Firewall Windows Stateful, packet-level firewall for workstations, mobile $101 (Canadian) St. Thomas, Ontario for Workstations users or telecommuters 519-633-3403 www.deerfieldcanada.ca Glucose Development Corp. Impasse Mac OS X Full-featured firewall with real-time logging display $10 Sunnyvale, Calif. www.glu.com Intego Corp. NetBarrier Personal Firewall Windows Full-featured firewall with cookie and ad blocking $50 Miami 512-637-0700 NetBarrier 10.1 Mac OS X Full-featured firewall $60 www.intego.com NetBarrier 2.1 Mac OS 8 and 9 Full-featured firewall $60 Internet Security Systems Inc. BlackIce Windows Consumer-oriented PC firewall $30 Atlanta 404-236-2600 RealSecure Desktop Windows Enterprise-grade firewall system for remote, mobile and wireless users Varies blackice.iss.net/ Kerio Technologies Inc. Kerio Personal Firewall Windows Bidirectional, stateful firewall with encrypted remote-management option $39 Santa Clara, Calif. 408-496-4500 www.kerio.com Lava Software Pty. Ltd. AdWare Plus Windows Antispyware blocks some advertiser monitoring but isn't $27 Falköping, Sweden intended to block surveillance utilities 46-0-515-530-14 www.lavasoft.de Network Associates Inc. -

Kerio Powerpoint Template
Bezpečnost v IT: Firewally Jan Ježek, Kerio Technologies / Samepage Labs Úvod Jan Ježek • Do r. 2012 vedoucí vývoje produktu Kerio Control (dříve Kerio WinRoute Firewall, ještě dříve WinRoute Pro) • Kerio Technologies teké známé díky: Kerio Connect, Kerio Operator Samepage Program přednášky • Firewall: co to je / původ / dělení / historie • Princip fungování / komponenty • Překlad adres (NAT) • Doplňkové funkce • Obcházení firewallu / lidský faktor Program přednášky • Firewall: co to je / původ / dělení / historie • Princip fungování / komponenty • Překlad adres (NAT) • Doplňkové funkce • Obcházení firewallu / lidský faktor Firewall: co to je? Firewall: co to je? Firewall = „Protipožární zeď“ Původ slova není znám. Poprvé snad ve filmu WarGames. Firewall: co to je? Definice: Jeden bod mezi dvěma sítěmi, kterým musí procházet veškerý provoz mezi nimi. Bariéra mezi námi a nimi, pro libovolnou hodnotu „nimi“. Dělení firewallů Podle použití: • Síťové • Osobní • Serverové • Web Application Firewalls Podle platformy: • Hardwarové • Softwarové • Virtuální • Cloudové – spravované (managed) Historie firewallů Počátky lze vysledovat na přelomu 80. a 90. let: • Objevuje se Internet ;-) • resp. přestává být doménou „kolegů z univerzit“ 2.11.1988 – první internetový červ „Morris“ • Robert Tappan Morris, student na Cornell University, NY • Údajně 6000 nakažených počítačů (10% tehdejšího internetu) • Přinesl vystřízlivění ohledně bezpečnosti • Červ neměl škodit (dle Morrise) • 400 hodin prací, $10,000 pokuta, podmínka Historie firewallů 1987 – AT&T Gate -

CHARON-AXP V4.9 for Linux Users Guide
Document number: 60-16-034-001 CHARON-AXP V4.9 for Linux Users Guide September, 2018 1 / 255 Contents Introduction . 3 Conventions . 6 CHARON-AXP for Linux installation . 7 Running CHARON-AXP for Linux . 22 CHARON-AXP for Linux configuration . 27 Migration to CHARON-AXP for Linux . 43 CHARON-AXP for Linux virtual network . 51 CHARON-AXP for Linux licensing . 55 CHARON-AXP for Linux utilities . 65 mkdskcmd . 66 mtd . 69 hasp_srm_view . 71 hasp_update . 73 ncu . 74 CHARON Guest Utilities for OpenVMS . 82 CHARON-AXP for Linux configuration details . 86 General Settings . 87 Core Devices . 95 Console . 115 Placement of peripheral devices on PCI bus . 121 PBXDA PCI serial lines adapter . 159 Disks and tapes . 162 KZPBA PCI SCSI adapter . 163 KGPSA-CA PCI Fibre Channel adapter . 172 Acer Labs 1543C IDE/ATAPI CD-ROM adapter . 188 PCI I/O Bypass controller . 190 Finding the target "/dev/sg" device . 197 Networking . 199 AlphaStation Sound Card (AD1848) emulation . 206 Sample configuration files . 207 HP AlphaServer 800 configuration file . 208 HP AlphaServer 4000 configuration file . 215 HP AlphaServer DS20 configuration file . 222 HP AlphaServer ES40 configuration file . 229 HP AlphaServer GS80 configuration file . 236 CHARON-AXP for Linux deinstallation . 243 Appendixes . 244 glibc.i686 installation without Internet connection . 245 How to implement time synchronisation between CHARON-AXP Host OS and Guest OS . 249 2 / 255 Document number: 60-16-034-001 Introduction Table of Contents General Description The principles of HP Alpha Hardware Virtualization Virtualized hardware Host platform General Description HP Alpha Hardware Virtualization allows users of HP Alpha (Previously known as DIGITAL Alpha) computers to move application software and user data to a modern Intel or AMD based x64 compatible platform without having to make changes to software and data. -

A Case Study
A Case Study The Lady of May: a Case Study in the Rhetoric of Electronic Text R.S. Bear Arts And Administration University of Oregon Abstract This paper examines the history of the print editions and the online edition of Philip Sidney's early pageant known as "The Lady of May." Electronic image scans of pages from print editions are iconically compared with the same text as typed into a computer and as coded in increasingly complex HTML code, culminating in an interactive presentation with online helps. This examination will seek an answer to the following question: Will traditional book arts continue to influence text design in the online world? Keywords: Etext, HTML, Internet, Markup, World Wide Web, Design Suzi Gablik in The Reenchantment of Art (5) reminds us that for some time now the focus of art has been on the individual acting alone, defying the gods[1], defying society. Even the reaction to this ethos in what has been called postmodernism retains this disconnectedness, or rather extends it, by proposing nihilism, the death that is final because it is individual death, denying to society the locus of what is to be called life (40). In literature this disconnectedness has been possible only through cognitive dissonance, for every act of publication is an act of making public, of making to the world the gift of the textual object, and publication has generally been a team effort in any case, as it is a complex maneuver: author, editor, publisher, designer, printer and distributor have all been required. The Internet seems to offer a new field for the play of individualism in publication, yet it is the most communal medium (Leppert 7) yet devised, as the give-and- take of communication between authors and readers becomes what is known as a "thread" or single intertwining strand of textuality. -

Way of the Ferret: Finding and Using Resources on the Internet
W&M ScholarWorks School of Education Books School of Education 1995 Way of the Ferret: Finding and Using Resources on the Internet Judi Harris College of William & Mary Follow this and additional works at: https://scholarworks.wm.edu/educationbook Part of the Education Commons Recommended Citation Harris, Judi, "Way of the Ferret: Finding and Using Resources on the Internet" (1995). School of Education Books. 1. https://scholarworks.wm.edu/educationbook/1 This Book is brought to you for free and open access by the School of Education at W&M ScholarWorks. It has been accepted for inclusion in School of Education Books by an authorized administrator of W&M ScholarWorks. For more information, please contact [email protected]. DOCUMENT RESUME IR 018 778 ED 417 711 AUTHOR Harris, Judi TITLE Way of the Ferret: Finding andUsing Educational Resources on the Internet. SecondEdition. Education, Eugene, INSTITUTION International Society for Technology in OR. ISBN ISBN-1-56484-085-9 PUB DATE 1995-00-00 NOTE 291p. Education, Customer AVAILABLE FROM International Society for Technology in Service Office, 480 Charnelton Street,Eugene, OR 97401-2626; phone: 800-336-5191;World Wide Web: http://isteonline.uoregon.edu (members: $29.95,nonmembers: $26.95). PUB TYPE Books (010)-- Guides -Non-Classroom (055) EDRS PRICE MF01/PC12 Plus Postage. Mediated DESCRIPTORS *Computer Assisted Instruction; Computer Communication; *Educational Resources;Educational Technology; Electronic Mail;Information Sources; Instructional Materials; *Internet;Learning Activities; Telecommunications; Teleconferencing IDENTIFIERS Electronic Resources; Listservs ABSTRACT This book is designed to assist educators'exploration of the Internet and educational resourcesavailable online. An overview lists the five basic types of informationexchange possible on the Internet, and outlines five corresponding telecomputingoptions. -

Kerio-Control-Adminguide.Pdf
ADMINISTRATOR GUIDE Find out how to install and configure Kerio Control in different environments and how to set up advanced features The information and content in this document is provided for informational purposes only and is provided "as is" with no warranties of any kind, either express or implied, including without limitation any warranties of merchantability, fitness for a particular purpose, and non-infringement. GFI Software disclaims and in no event shall be liable for any losses or damages of any kind, including any consequential or incidental damages in connection with the furnishing, performance or use of this document. The information is obtained from publicly available sources. Though reasonable effort has been made to ensure the accuracy of the data provided, GFI makes no warranty, promise or guarantee about the completeness, accuracy, recency or adequacy of information contained in this document and is not responsible for misprints, out-of-date information, or errors. GFI reserves the right to revise or update its products, software or documentation without notice. You must take full responsibility for your use and application of any GFI product or service. No part of this documentation may be reproduced in any form by any means without prior written authorization of GFI Software. If you believe there are any factual errors in this document, please contact us and we will review your concerns as soon as practical. GFI and Kerio Control are trademarks or registered trademarks of GFI Software or its affiliates in the US and other countries. Any other trademarks contained herein are the property of their respective owners. -
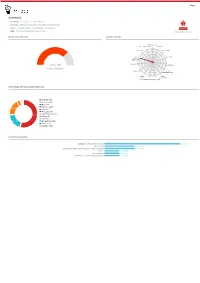
Advanced File Analysis System | Valkyrie
Page 1 Summary File Name: Packing_list_and_Draft_BL.exe File Type: PE32 executable (GUI) Intel 80386, for MS Windows SHA1: 948482095bade1c1d72cda2a08b165a47ca128f3 MALWARE MD5: 7828dd5b474006b86ffe30dce57520bc Valkyrie Final Verdict DETECTION SECTION CLASSIFICATION Backdoor(1.74%) Ransomware(0.00%) Bot(0.60%) 81% Worm(3.46%) Exploit(0.00%) 65% 48% Trojan 32% Pua(5.26%) Password Stealer(75.74%) 16% Rootkit(0.00%) Trojan Severity: High Generic(3.43%) Verdict: Malware Spyware(0.00%) Trojan Downloader(4.23%) Remote Trojan Access Dropper(3.60%) Trojan(0.00%V)irus(0.77%) Rogue(1.17%) HIGH LEVEL BEHAVIOR DISTRIBUTION Network (19) Process (128) Misc (47) System (1493) 18.2% Crypto (12) Threading (7) Synchronization (6) 54.0% Device (2) Windows (1) 19.7% File System (543) Services (3) Registry (502) ACTIVITY OVERVIEW Stealing of Sensitive Information 5 (41.67%) Networking 2 (16.67%) Hooking and other Techniques for Hiding Protection 2 (16.67%) Packer 1 (8.33%) Static Anomaly 1 (8.33%) Persistence and Installation Behavior 1 (8.33%) Page 2 Activity Details NETWORKING HTTP traffic contains suspicious features which may be indicative of malware related traffic Show sources Performs some HTTP requests Show sources PACKER The binary likely contains encrypted or compressed data. Show sources STEALING OF SENSITIVE INFORMATION Collects information to fingerprint the system Show sources Steals private information from local Internet browsers Show sources Harvests information related to installed instant messenger clients Show sources Harvests credentials -

Intel Open Network Platform Server Reference Architecture
Intel® Open Network Platform Server Reference Architecture (Version 1.1) NFV/SDN Solutions with Intel® Open Network Platform Server Revision 1.1 September 2014 LEGAL By using this document, in addition to any agreements you have with Intel, you accept the terms set forth below. You may not use or facilitate the use of this document in connection with any infringement or other legal analysis concerning Intel products described herein. You agree to grant Intel a non-exclusive, royalty-free license to any patent claim thereafter drafted which includes subject matter disclosed herein. INFORMATION IN THIS DOCUMENT IS PROVIDED IN CONNECTION WITH INTEL PRODUCTS. NO LICENSE, EXPRESS OR IMPLIED, BY ESTOPPEL OR OTHERWISE, TO ANY INTELLECTUAL PROPERTY RIGHTS IS GRANTED BY THIS DOCUMENT. EXCEPT AS PROVIDED IN INTEL'S TERMS AND CONDITIONS OF SALE FOR SUCH PRODUCTS, INTEL ASSUMES NO LIABILITY WHATSOEVER AND INTEL DISCLAIMS ANY EXPRESS OR IMPLIED WARRANTY, RELATING TO SALE AND/OR USE OF INTEL PRODUCTS INCLUDING LIABILITY OR WARRANTIES RELATING TO FITNESS FOR A PARTICULAR PURPOSE, MERCHANTABILITY, OR INFRINGEMENT OF ANY PATENT, COPYRIGHT OR OTHER INTELLECTUAL PROPERTY RIGHT. A “Mission Critical Application” is any application in which failure of the Intel Product could result, directly or indirectly, in personal injury or death. SHOULD YOU PURCHASE OR USE INTEL'S PRODUCTS FOR ANY SUCH MISSION CRITICAL APPLICATION, YOU SHALL INDEMNIFY AND HOLD INTEL AND ITS SUBSIDIARIES, SUBCONTRACTORS AND AFFILIATES, AND THE DIRECTORS, OFFICERS, AND EMPLOYEES OF EACH, HARMLESS AGAINST ALL CLAIMS COSTS, DAMAGES, AND EXPENSES AND REASONABLE ATTORNEYS' FEES ARISING OUT OF, DIRECTLY OR INDIRECTLY, ANY CLAIM OF PRODUCT LIABILITY, PERSONAL INJURY, OR DEATH ARISING IN ANY WAY OUT OF SUCH MISSION CRITICAL APPLICATION, WHETHER OR NOT INTEL OR ITS SUBCONTRACTOR WAS NEGLIGENT IN THE DESIGN, MANUFACTURE, OR WARNING OF THE INTEL PRODUCT OR ANY OF ITS PARTS. -

Bid Item Workbook Bidder/Contractor Data
BID ITEM WORKBOOK COSTARS-6 Packaged Software BIDDER/CONTRACTOR DATA BIDDER/CONTRACTOR'S LEGAL NAME: CDW Government LLC D/B/A NAME, IF APPLICABLE: BIDDER ADDRESS: 230 N. Milwaukee Ave. Vernon Hills, IL, 60061 COUNTY LOCATED IN: Lake County PA Legislative House District Number PA Legislative Senate District Number VENDOR NUMBER: 163101 DGS Self-Certified Small Business (SB) Certification Number Primary POC regarding IFB/Contract: Rick Martinez Secondary POC regarding IFB/Contract: Jumana Dihu PHONE NUMBER: Primary: 847-371-7182 Secondary: 312-547-2495 FAX NUMBER: Primary: 312 705-8649 Secondary: 312-705-9437 EMAIL ADDRESS: [email protected] COMPANY'S GENERAL WEBSITE ADDRESS www.cdwg.com SEND PURCHASE ORDER(S) TO NAME: CDW Government LLC D/B/A NAME, IF APPLICABLE: ADDRESS: 230 N. Milwaukee Ave. Vernon Hills, IL, 60061 COUNTY LOCATED IN: Lake County HOURS OF OPERATION: Monday-Friday 7:00AM-7:30PM POC regarding PURCHASE ORDER(S): Mike Truncone PHONE NUMBER: 866-769-8471 FAX NUMBER: 847-990-8050 EMAIL ADDRESS: [email protected] SEND PAYMENT(S) TO NAME: CDW Government LLC D/B/A NAME, IF APPLICABLE: ADDRESS: 75 Remittance Dr. Suite 1515 Chicago, IL, 60675-1515 POC regarding PAYMENT(S): Janet Pishotta PHONE NUMBER: 847-419-6284 FAX NUMBER: 847-465-6884 EMAIL ADDRESS: [email protected] BID ITEM WORKBOOK COSTARS-6 Packaged Software QUESTIONS BIDDERS/CONTRACTOR'S LEGAL NAME: CDW Government LLC. PLEASE BE ADVISED - COMPLETE ALL QUESTIONS AND EXPLANATIONS FOR YOUR BID TO BE ACCEPTED AS A RESPONSIBLE AND RESPONSIVE BID The bidder must answer the following questions: QUESTION YES NO EXPLANATION 1) Does the Bidder-Contractor have any minimum order requirements? If yes, please explain.