Kerio-Control-Adminguide.Pdf
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Anyconnect および Host Scan のアンチウイルス/アンチスパイウェア
AnyConnect および Host Scan のアンチウイルス/アンチスパイウェア/ファイアウォール サポート表 AnyConnect ポスチャ モジュールにより、AnyConnect Secure Mobility クライアントはホストにインス トールされているオペレーティング システム、およびアンチウイルス、アンチスパイウェア、ファイアウォールの 各ソフトウェアを識別できます。 Host Scan アプリケーションはポスチャ モジュールのコンポーネントに含まれ る、こうした情報を収集するアプリケーションです。 AnyConnect 3.0 より、Host Scan パッケージは AnyConnect Secure Mobility クライアントおよび Cisco Secure Desktop(CSD)の共有コンポーネントになっています。 それ以前は、Host Scan パッケージは CSD を インストールすることによってのみ利用可能になるコンポーネントの 1 つでした。 Host Scan パッケージを CSD から分離したのは、CSD の一部として提供されていたときよりも、ユー ザが頻繁に Host Scan サポート表を更新できるようにするためです。 このサポート表には、ユーザが動的なア クセス ポリシーで使用しているアンチウイルス/アンチスパイウェア/ファイアウォール アプリケーションの製品 名とバージョン情報が記載されています。 シスコでは、Host Scan パッケージに Host Scan アプリケーション、 Host Scan サポート表、および他のコンポーネントを含めて提供しています。 Host Scan サポート表のリスト アンチウイルス アプリケーション総合リスト アンチスパイウェア アプリケーション総合リスト ファイアウォール アプリケーション総合リスト Windows 用アンチウイルス Windows 用アンチスパイウェア Windows 用ファイアウォール Linux 用アンチウイルス Linux 用ファイアウォール Mac OS 用アンチウイルス Mac OS 用アンチスパイウェア Mac OS 用ファイアウォール A B C D E F G H I J K L M N O P Q R S T U V W X Y Z AA AB AC AD AE ファイル データ ファ バージョ データ ファイ データ ファイル データ ファイ エンジンのバー RTP の RTP の 前回のスキャン スキャン/クリー システムのフル アンイン GUI のアク トレイ アイコンの トレイ アイコン 有効期 脅威ログの取 スキャン プログラ フル スキャンの進捗 インストール ディ 一括スキャ メモリ スキャ アンチウイルス製品名 ライブ更新 サービス GUI の表示 のスキャ 有効日の取得 更新の進捗表示 プログラム言語の取得 イル dir の取 市場での別名 ン ルの時刻 のバージョン ルの署名 ジョン チェック 設定 時刻 ニング スキャン ストール ティブ化 表示 の非表示 限 得 ムの実行 表示 レクトリの取得 ン ン 1 ン 得 2 3 360Safe.com 4 360 Antivirus 1.x 9989999898888898 8888 8 9 8 9 9 9 88 5 360杀毒 1.x 9999988898888898 8889 8 8 8 9 9 9 88 6 AEC, spol. s r.o. 7 TrustPort Antivirus 2.x 8888998899888999 9888 8 9 8 9 8 988 8 Agnitum Ltd. -

Personal Firewalls Are a Necessity for Solo Users
Personal firewalls are a necessity for solo users COMPANY PRODUCT PLATFORM NOTES PRICE Aladdin Knowledge Systems Ltd. SeSafe Desktop Windows Combines antivirus with content filtering, blocking and $72 Arlington Heights, Ill. monitoring 847-808-0300 www.ealaddin.com Agnitum Inc. Outpost Firewall Pro Windows Blocks ads, sites, programs; limits access by specific times $40 Nicosia, Cyprus www.agnitum.com Computer Associates International Inc. eTrust EZ Firewall Windows Basic firewall available only by download $40/year Islandia, N.Y. 631-342-6000 my-etrust.com Deerfield Canada VisNetic Firewall Windows Stateful, packet-level firewall for workstations, mobile $101 (Canadian) St. Thomas, Ontario for Workstations users or telecommuters 519-633-3403 www.deerfieldcanada.ca Glucose Development Corp. Impasse Mac OS X Full-featured firewall with real-time logging display $10 Sunnyvale, Calif. www.glu.com Intego Corp. NetBarrier Personal Firewall Windows Full-featured firewall with cookie and ad blocking $50 Miami 512-637-0700 NetBarrier 10.1 Mac OS X Full-featured firewall $60 www.intego.com NetBarrier 2.1 Mac OS 8 and 9 Full-featured firewall $60 Internet Security Systems Inc. BlackIce Windows Consumer-oriented PC firewall $30 Atlanta 404-236-2600 RealSecure Desktop Windows Enterprise-grade firewall system for remote, mobile and wireless users Varies blackice.iss.net/ Kerio Technologies Inc. Kerio Personal Firewall Windows Bidirectional, stateful firewall with encrypted remote-management option $39 Santa Clara, Calif. 408-496-4500 www.kerio.com Lava Software Pty. Ltd. AdWare Plus Windows Antispyware blocks some advertiser monitoring but isn't $27 Falköping, Sweden intended to block surveillance utilities 46-0-515-530-14 www.lavasoft.de Network Associates Inc. -

Kerio Powerpoint Template
Bezpečnost v IT: Firewally Jan Ježek, Kerio Technologies / Samepage Labs Úvod Jan Ježek • Do r. 2012 vedoucí vývoje produktu Kerio Control (dříve Kerio WinRoute Firewall, ještě dříve WinRoute Pro) • Kerio Technologies teké známé díky: Kerio Connect, Kerio Operator Samepage Program přednášky • Firewall: co to je / původ / dělení / historie • Princip fungování / komponenty • Překlad adres (NAT) • Doplňkové funkce • Obcházení firewallu / lidský faktor Program přednášky • Firewall: co to je / původ / dělení / historie • Princip fungování / komponenty • Překlad adres (NAT) • Doplňkové funkce • Obcházení firewallu / lidský faktor Firewall: co to je? Firewall: co to je? Firewall = „Protipožární zeď“ Původ slova není znám. Poprvé snad ve filmu WarGames. Firewall: co to je? Definice: Jeden bod mezi dvěma sítěmi, kterým musí procházet veškerý provoz mezi nimi. Bariéra mezi námi a nimi, pro libovolnou hodnotu „nimi“. Dělení firewallů Podle použití: • Síťové • Osobní • Serverové • Web Application Firewalls Podle platformy: • Hardwarové • Softwarové • Virtuální • Cloudové – spravované (managed) Historie firewallů Počátky lze vysledovat na přelomu 80. a 90. let: • Objevuje se Internet ;-) • resp. přestává být doménou „kolegů z univerzit“ 2.11.1988 – první internetový červ „Morris“ • Robert Tappan Morris, student na Cornell University, NY • Údajně 6000 nakažených počítačů (10% tehdejšího internetu) • Přinesl vystřízlivění ohledně bezpečnosti • Červ neměl škodit (dle Morrise) • 400 hodin prací, $10,000 pokuta, podmínka Historie firewallů 1987 – AT&T Gate -

Bid Item Workbook Bidder/Contractor Data
BID ITEM WORKBOOK COSTARS-6 Packaged Software BIDDER/CONTRACTOR DATA BIDDER/CONTRACTOR'S LEGAL NAME: CDW Government LLC D/B/A NAME, IF APPLICABLE: BIDDER ADDRESS: 230 N. Milwaukee Ave. Vernon Hills, IL, 60061 COUNTY LOCATED IN: Lake County PA Legislative House District Number PA Legislative Senate District Number VENDOR NUMBER: 163101 DGS Self-Certified Small Business (SB) Certification Number Primary POC regarding IFB/Contract: Rick Martinez Secondary POC regarding IFB/Contract: Jumana Dihu PHONE NUMBER: Primary: 847-371-7182 Secondary: 312-547-2495 FAX NUMBER: Primary: 312 705-8649 Secondary: 312-705-9437 EMAIL ADDRESS: [email protected] COMPANY'S GENERAL WEBSITE ADDRESS www.cdwg.com SEND PURCHASE ORDER(S) TO NAME: CDW Government LLC D/B/A NAME, IF APPLICABLE: ADDRESS: 230 N. Milwaukee Ave. Vernon Hills, IL, 60061 COUNTY LOCATED IN: Lake County HOURS OF OPERATION: Monday-Friday 7:00AM-7:30PM POC regarding PURCHASE ORDER(S): Mike Truncone PHONE NUMBER: 866-769-8471 FAX NUMBER: 847-990-8050 EMAIL ADDRESS: [email protected] SEND PAYMENT(S) TO NAME: CDW Government LLC D/B/A NAME, IF APPLICABLE: ADDRESS: 75 Remittance Dr. Suite 1515 Chicago, IL, 60675-1515 POC regarding PAYMENT(S): Janet Pishotta PHONE NUMBER: 847-419-6284 FAX NUMBER: 847-465-6884 EMAIL ADDRESS: [email protected] BID ITEM WORKBOOK COSTARS-6 Packaged Software QUESTIONS BIDDERS/CONTRACTOR'S LEGAL NAME: CDW Government LLC. PLEASE BE ADVISED - COMPLETE ALL QUESTIONS AND EXPLANATIONS FOR YOUR BID TO BE ACCEPTED AS A RESPONSIBLE AND RESPONSIVE BID The bidder must answer the following questions: QUESTION YES NO EXPLANATION 1) Does the Bidder-Contractor have any minimum order requirements? If yes, please explain. -
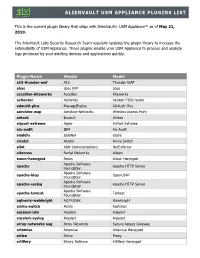
Alienvault Usm Appliance Plugins List
ALIENVAULT USM APPLIANCE PLUGINS LIST This is the current plugin library that ships with AlienVault USM Appliance as of May 21, 2019. The AlienVault Labs Security Research Team regularly updates the plugin library to increase the extensibility of USM Appliance. These plugins enable your USM Appliance to process and analyze logs produced by your existing devices and applications quickly. Plugin Name Vendor Model a10-thunder-waf A10 Thunder WAF abas abas ERP abas accellion-kiteworks Accellion Kiteworks actiontec Actiontec Verizon FIOS router adaudit-plus ManageEngine ADAudit Plus aerohive-wap Aerohive Networks Wireless Access Point airlock Envault Airlock airport-extreme Apple AirPort Extreme aix-audit IBM Aix Audit aladdin SafeNet eSafe alcatel Alcatel Arista Switch allot Allot Communications NetEnforcer alteonos Nortel Networks Alteon amun-honeypot Amun Amun Honeypot Apache Software apache Apache HTTP Server Foundation Apache Software apache-ldap OpenLDAP Foundation Apache Software apache-syslog Apache HTTP Server Foundation Apache Software apache-tomcat Tomcat Foundation aqtronix-webknight AQTRONiX WebKnight arista-switch Arista Switches arpalert-idm Arpalert Arpalert arpalert-syslog Arpalert Arpalert array-networks-sag Array Networks Secure Access Gateway artemisa Artemisa Artemisa Honeypot artica Artica Proxy artillery Binary Defense Artillery Honeypot ALIENVAULT USM APPLIANCE PLUGINS LIST aruba Aruba Networks Mobility Access Switches aruba-6 Aruba Networks Wireless aruba-airwave Aruba Networks Airwave aruba-clearpass Aruba Networks -

N Software Furman PLANON 1/4 TAPE FUTURE DESIGNS Planters 16X9 Inc
Positively Web Partners and Affiliates /n software Furman PLANON 1/4 TAPE FUTURE DESIGNS Planters 16x9 Inc. FUTURE MEMORY SOLUTIONS PLANTRONIC 1E SOFTWARE Future-Call Plantronics 2GIG FutureIT PLASMON 2N G Data PLDA 2X Software Gable Louvers & Vents Plews 2XL GammaTech Plextor 360Heros Ganz PLUSTEK 3CX Garmin Pneumatic Actuators 3M Garrett Pneumatic Control Valves 3M - ERGO Gateworks Pneumatic Cylinders 3M - OPTICAL SYSTEMS DIVISION GATOR Pneumatic Fittings 3M Industrial GBC Pneumatic Hoses 3M TOUCH SCREEN GE Pneumatic Parts Washers 3M VISUAL SYSTEMS DIVISION GE Critical Power Pneumatic Quick Connect Couplings 3NG Private Label Voip GE Lighting Pneumatic Solenoid Valves 3R Technologies GEAR HEAD-COMPUTER Pneumatic Tools Accessories 3WARE/AMCC Gearboxes Pneumatic Vibrators 4 Flute Countersinks GearWrench PNY 4MM TAPE Geemarc PNY MEMORY 4XEM GEFEN PNY QUADRO 5NINE GELID Solutions PNY VIDEO GRAPHICS 6 Flute Chatterless Countersinks GEM Electronics PoE Technologies 80/20 GENEVA PolarCool 8MM TAPE GENICOM Polaroid 8x8 Genie-Soft Polycom 9 Circle Genius POLYCOM AUDIO 9940/9840 GENOVATION POLYCOM CX Aaeon Electronics Gentex Corp. POLYCOM SPECTRALINK Aastra George Risk Industries POLYCOM VIDEO Aavid Thermalloy Georgia Pacific Polymer Bathroom Partitions ABA Cable Georgia SoftWorks Polypropylene ABBYY Geovision Pomona Electronics ABILITYONE Gerson PORELON ABLE BAY - NITHO GESTETNER Port-A-Cool AbleNet GFI Portescap Ableton GFX Power Porto-Power Abracon Ghent Portwell Absoft GIGABYTE POSITIVELY WEB ABSOLUTE LICENSE Gigaset Potter Absolute Software -

Administrator's Guide
Kerio Control Administrator’s Guide Kerio Technologies 2012 Kerio Technologies s.r.o. All rights reserved. This guide provides detailed description on configuration and administration of Kerio Control, version 7.3. All additional modifications and updates reserved. User interfaces Kerio StaR and Kerio Clientless SSL-VPN are focused in a standalone document, Kerio Control — User’s Guide. Kerio VPN Client for Windows and Mac OS X is focused in the separate document Kerio VPN Client — User’s Guide. For current version of the product, go to http://www.kerio.com/control/download. For other documents addressing the product, see http://www.kerio.com/control/manual. Information regarding registered trademarks and trademarks are provided in appendix A. Products Kerio Control and Kerio VPN Client include open source software. To view the list of open source items included, refer to attachment B. Contents 1 Quick Checklist ................................................................ 8 2 Installation .................................................................... 10 2.1 Product Editions ......................................................... 10 2.2 System requirements .................................................... 10 2.3 Windows: Conflicting Software ........................................... 11 2.4 Windows: Installation .................................................... 12 2.5 Windows: Upgrade and Uninstallation .................................... 16 2.6 Appliance Edition: Installation .......................................... -

DISYS Proposal
City of Charlotte – Charlotte Cooperative Purchasing Alliance RFP# 269-2011-065 for Technology Products and Associated Services Cover Letter January 30, 2012 City of Charlotte Procurement Services Division 600 East 4th Street, CMGC 9th Floor Charlotte, NC 28202 Attn: Sarah Poulton Re: RFP # 269-2011-065 for Technology Products and Associated Services Dear Ms. Poulton, DISYS Solutions, Inc. (DSI) is pleased to submit our proposal to provide Technology Products and Associated Services to the City of Charlotte and the Charlotte Cooperative Purchasing Alliance (CCPA). Our submission is in compliance with all the terms and conditions listed throughout the above referenced solicitation and its addenda. Please consider this transmittal letter, the completed bid documents, and the following proposal as our response. Headquarter Office: DISYS Solutions, Inc 4151 Lafayette Center Drive, Suite 600 Chantilly, VA 20151 Phone: (888) 286-3896 or (703) 802-0500 Fax: (800) 601-2944 or (703) 802-0798 Executive Officer Vinu Luthra, Chief Operating Officer Project Understanding The City of Charlotte has established the CCPA and would like to establish a comprehensive Master Agreement that will allow the City’s Procurement Services Division and CCPA members to purchase technology products and associated services. Summary of Approach DSI has the capability to provide a complete breath of products and services to meet the City of Charlotte and CCPA’s needs. We are able to provide a full range of technology hardware, software, and associate peripherals through our many distributor and manufacturer partnerships. In order to offer the City and CCPA contracts users with a full scope of services, DSI has established partnerships with industry leading companies in Cloud, Data Center, Unified Security, Unified Communications, Web Hosting, Disaster Recovery and Backup. -

Instituto Tecnológico Y De Estudios Superiores De Monterrey a Unified
Instituto Tecnol´ogico y de Estudios Superiores de Monterrey Monterrey Campus GRADUATE PROGRAM IN MECHATRONICS AND INFORMATION TECHNOLOGIES A Unified Software Security Enhancement Proposal Based on a Thorough Software Security Compendium. THESIS PRESENTED AS A PARTIAL FULFILLMENT OF THE REQUIREMENTS FOR THE DEGREE OF: Master of Science in Information Technology BY: Armando de Anda Gonz´alez Monterrey, N.L., November 2007 Instituto Tecnol´ogico y de Estudios Superiores de Monterrey Monterrey Campus DIVISION OF MECHATRONICS AND INFORMATION TECHNOLOGIES GRADUATE PROGRAM IN MECHATRONICS AND INFORMATION TECHNOLOGIES The members of the thesis committee hereby approve the thesis of Armando de Anda Gonz´alez to be accepted as partial fulfillment of the requirements for the Degree of Master of Science, in: Information Technology Thesis Committee: Arturo Galv´an Rodr´ıguez, Ph. D. Thesis advisor Suku Nair, Ph. D. MSc Alejandro Parra Briones Synodal Synodal Graciano Dieck Assad, Ph. D. Director of the Graduate Programs in Mechatronics and Information Technologies November 2007 A Unified Software Security Enhancement Proposal Based on a Thorough Software Security Compendium. BY: Armando de Anda Gonz´alez THESIS Presented to the Graduate Program in Mechatronics and Information Technologies This Thesis is a partial requirement for the degree of Master of Science in: Information Technology Instituto Tecnol´ogico y de Estudios Superiores de Monterrey Monterrey Campus November 2007 To God, for the wonderful gift of life and with whom anything is possible. To the love of my life, Paola, for being my inspiration, my strength, my everything. To my parents, Armando and Layda, the greatest example of love and sacrifice. To my aunt Martha, for believing in me and keeping this dream alive. -

Accessing Security Incident Information on the Internet
Firewall or FireFolly – An initial investigation into the effectiveness of Personal Firewalls in securing personal computers from attack. Jeshua Yee School of Computer and Information Science Edith Cowan University E-mail: [email protected]; ABSTRACT With the increase in the use of Personal Computer (PC) firewall, this study looks at the security features provided by eight PC firewall; they are BlackICE, Deerfield, Kirio, MacAfee, Outpost, Sygate, Tiny and Zonealarm. The Nessus network scanner was used to probe these systems in a variety of configurations. The paper discusses the results and their implications for users of this new range of software. Keywords: Personal Computer firewall, Nessus network scanner, firewall security features INTRODUCTION Today, with the advent of Personal Computer (PC), a PC no longer acts as a mere word processor or for calculating simple spreadsheets. It has now become an important tool for communications, program organisation and business processes in traditional places of commerce and enterprise. In addition, many of the company’s personnel work regularly by logging on the company’s network remotely (Yasin, 2000). Therefore, a malicious attack on a home PC could have a detrimental effect on the user’s daily routine, business and financial well-being (Hulme, 2002). This problem is further compounded with the increasing deployment of affordable broadband in the form of cable and ADSL services. These services provide reliable 24-hour high bandwidth connectivity to the Internet (Fleishman, 2001; Goldsborough, 2002; Janss, 2000; Radcliff, 2001). With the increase in hacking incidences (Ravendran, 2002), small and large organisations alike are moving to protect their PC’s and the valuable data they contain (Clark, 2001; Goldsborough, 2000a; Schwartz, et. -
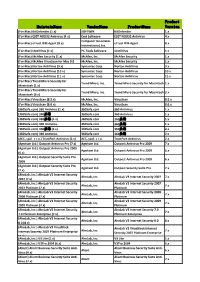
Maintainname Vendorname Productname Product Version
Product MaintainName VendorName ProductName Version (For Mac) BitDefender (1.x) SOFTWIN BitDefender 1.x (For Mac) ESET NOD32 Antivirus (4.x) Eset Software ESET NOD32 Antivirus 4.x Computer Associates (For Mac) eTrust ITM Agent (8.x) eTrust ITM Agent 8.x International, Inc. (For Mac) iAntiVirus (1.x) PC Tools Software iAntiVirus 1.x (For Mac) McAfee Security (1.x) McAfee, Inc. McAfee Security 1.x (For Mac) McAfee VirusScan for Mac 9.0 McAfee, Inc. McAfee Security 1.x (For Mac) Norton AntiVirus (9.x) Symantec Corp. Norton AntiVirus 9.x (For Mac) Norton AntiVirus (10.x) Symantec Corp. Norton AntiVirus 10.x (For Mac) Norton AntiVirus (11.x) Symantec Corp. Norton AntiVirus 11.x (For Mac) Trend Micro Security for Trend Micro, Inc. Trend Micro Security for Macintosh 1.x Macintosh (1.x) (For Mac) Trend Micro Security for Trend Micro, Inc. Trend Micro Security for Macintosh 3.x Macintosh (3.x) (For Mac) VirusScan (8.5.x) McAfee, Inc. VirusScan 8.5.x (For Mac) VirusScan (8.6.x) McAfee, Inc. VirusScan 8.6.x (360Safe.com) 360 Antivirus (1.x) 360Safe.com 360 Antivirus 1.x (360Safe.com) 360杀毒 360Safe.com 360 Antivirus 1.x (360Safe.com) 360杀毒 (1.x) 360Safe.com 360杀毒 1.x (360Safe.com) 360 Antivirus 360Safe.com 360杀毒 1.x (360Safe.com) 360杀毒 (2.x) 360Safe.com 360杀毒 2.x (360Safe.com) 360 Antivirus 360Safe.com 360杀毒 2.x (AEC, spol. s r.o.) TrustPort Antivirus (2.x) AEC, spol. s r.o. TrustPort Antivirus 2.x (Agnitum Ltd.) Outpost Antivirus Pro (7.x) Agnitum Ltd. -

Kerio-Control-Adminguide-En.Pdf
Kerio Control Administrator’s Guide Kerio Technologies 2017 Kerio Technologies s.r.o. Contents Installing Kerio Control ................................................ 17 Product editions .......................................................... 17 Installing Software Appliance edition ........................................ 17 Installing VMware Virtual Appliance ........................................ 18 Installing virtual appliance for Hyper-V ...................................... 19 Configuring the Activation Wizard ...................................... 21 Configuring the Activation Wizard .......................................... 21 Step 1: Select a language ............................................ 21 Step 2: Setup connection ............................................ 21 Step 3: Set the time zone, date and time .............................. 21 Step 4: Activate Kerio Control ....................................... 21 Register Kerio Control trial version ............................ 22 Insert Kerio Control license number ........................... 23 Purchasing Kerio Control ..................................... 25 Register offline with a licence key .............................. 25 Activate Kerio Control in unregistered mode .................... 25 Step 5: Help us make Kerio Control even better ........................ 25 Step 6: Set the password for the administrator user account and sending alerts ...................................................... 25 Setting administrator password ............................... 25