Small Nation, Big Difference How the Norwegian Armed Forces Should Conduct Counterinsurgency Operations
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

It's So Easy Being Green
National Aeronautics and Space Administration roundupLyndon B. Johnson Space Center JSC2008E020395 NASA/BLAIR It’s so easy being green APRIL 2008 ■ volume 47 ■ number 4 A few safetyrelated events have been on my mind recently, and I need your help! First of all, I want to emphasize there is nothing we do in our space program that would require us to take safety shortcuts or unnecessary risks. Spaceflight is inherently risky, including the development and testing of stateoftheart materials and designs. To be perfectly safe, we would never leave the ground, but that is not the business we chose and it is not the mission our nation gave us. But we should not and cannot add unnecessary risks. None of us should ever feel pressured to do anything we deem unsafe in order to meet a schedule. We have learned to launch when we are ready and not before, and I’m impressed with the number of times we have delayed launches because of reasonable concerns expressed by individuals. My point is: don’t let anyone pressure you into doing something that you consider unsafe. I will back you up. Second, I am concerned that there is reluctance on the part of some folks to report safety incidents such as minor injuries or mishaps or close calls. Their fear is that such reports will affect our safety metrics, such as lost time, days away, Occupational Safety and Health Administration recordable, etc. Let me state very clearly and forcefully that the sole goal of director our safety program is to make our work environment as safe as possible for all our employees. -

Air Defence in Northern Europe
FINNISH DEFENCE STUDIES AIR DEFENCE IN NORTHERN EUROPE Heikki Nikunen National Defence College Helsinki 1997 Finnish Defence Studies is published under the auspices of the National Defence College, and the contributions reflect the fields of research and teaching of the College. Finnish Defence Studies will occasionally feature documentation on Finnish Security Policy. Views expressed are those of the authors and do not necessarily imply endorsement by the National Defence College. Editor: Kalevi Ruhala Editorial Assistant: Matti Hongisto Editorial Board: Chairman Prof. Pekka Sivonen, National Defence College Dr. Pauli Järvenpää, Ministry of Defence Col. Erkki Nordberg, Defence Staff Dr., Lt.Col. (ret.) Pekka Visuri, Finnish Institute of International Affairs Dr. Matti Vuorio, Scientific Committee for National Defence Published by NATIONAL DEFENCE COLLEGE P.O. Box 266 FIN - 00171 Helsinki FINLAND FINNISH DEFENCE STUDIES 10 AIR DEFENCE IN NORTHERN EUROPE Heikki Nikunen National Defence College Helsinki 1997 ISBN 951-25-0873-7 ISSN 0788-5571 © Copyright 1997: National Defence College All rights reserved Oy Edita Ab Pasilan pikapaino Helsinki 1997 INTRODUCTION The historical progress of air power has shown a continuous rising trend. Military applications emerged fairly early in the infancy of aviation, in the form of first trials to establish the superiority of the third dimension over the battlefield. Well- known examples include the balloon reconnaissance efforts made in France even before the birth of the aircraft, and it was not long before the first generation of flimsy, underpowered aircraft were being tested in a military environment. The Italians used aircraft for reconnaissance missions at Tripoli in 1910-1912, and the Americans made their first attempts at taking air power to sea as early as 1910-1911. -

Assessment and Selection Process for the Bulgarian Special Forces
Calhoun: The NPS Institutional Archive DSpace Repository Theses and Dissertations 1. Thesis and Dissertation Collection, all items 2019-12 ASSESSMENT AND SELECTION PROCESS FOR THE BULGARIAN SPECIAL FORCES Vlahov, Petar Georgiev Monterey, CA; Naval Postgraduate School http://hdl.handle.net/10945/64090 Downloaded from NPS Archive: Calhoun NAVAL POSTGRADUATE SCHOOL MONTEREY, CALIFORNIA THESIS ASSESSMENT AND SELECTION PROCESS FOR THE BULGARIAN SPECIAL FORCES by Petar Georgiev Vlahov December 2019 Thesis Advisor: Kalev I. Sepp Second Reader: Michael Richardson Approved for public release. Distribution is unlimited. THIS PAGE INTENTIONALLY LEFT BLANK Form Approved OMB REPORT DOCUMENTATION PAGE No. 0704-0188 Public reporting burden for this collection of information is estimated to average 1 hour per response, including the time for reviewing instruction, searching existing data sources, gathering and maintaining the data needed, and completing and reviewing the collection of information. Send comments regarding this burden estimate or any other aspect of this collection of information, including suggestions for reducing this burden, to Washington headquarters Services, Directorate for Information Operations and Reports, 1215 Jefferson Davis Highway, Suite 1204, Arlington, VA 22202-4302, and to the Office of Management and Budget, Paperwork Reduction Project (0704-0188) Washington, DC 20503. 1. AGENCY USE ONLY 2. REPORT DATE 3. REPORT TYPE AND DATES COVERED (Leave blank) December 2019 Master’s thesis 4. TITLE AND SUBTITLE 5. FUNDING NUMBERS ASSESSMENT AND SELECTION PROCESS FOR THE BULGARIAN SPECIAL FORCES 6. AUTHOR(S) Petar Georgiev Vlahov 7. PERFORMING ORGANIZATION NAME(S) AND ADDRESS(ES) 8. PERFORMING Naval Postgraduate School ORGANIZATION REPORT Monterey, CA 93943-5000 NUMBER 9. SPONSORING / MONITORING AGENCY NAME(S) AND 10. -

Defence Strategies of the Smaller NATO States – a Comparative Study Obranné Strategie Malých Států NATO – Komparativní Studie
Vojenské rozhledy č. 4/2020 DOI: 10.3849/2336-2995.29.2020.04.023-045 Peer-reviewed Defence strategies of the smaller NATO states – a comparative study Obranné strategie malých států NATO – komparativní studie Lukáš Dyčka, Taivo Rõkk, Zdzisław Śliwa Abstract: Defence strategies of smaller NATO states represent interesting source of information about defence policies of this pool of countries. Definition of what constitutes “small state” is discussed in first step. In second step, this study compares 10 selected NATO countries Defence Strategies in terms of identified risks and threats, future military capabilities to counter threats, processes of drafting defence papers, level of details and approving authorities. Outlining these indicators and characteristics provide useful overview for future draft of National defence strategies within countries of similar size. Abstrakt: Obranné strategie malých států NATO představují důležitý zdroj infor- mací o obranné politice. Definice “malého státu” je však nejasná a její zpřesnění představuje první část článku. Ve druhé části pak text srov- nává Obranné strategie deseti vybraných malých států NATO z pohledu hrozeb, budoucích vojenských schopností, procesu tvorby dokumentů, úrovně detailu a úrovně, na které je dokument schvalován. Přehledné se- řazení těchto poznatků pak potenciálně může sloužit jako vhodný základ a inspirace při tvorbě obranných strategií menších států. Key words: Defence; strategy; strategic documents; small states; military capabilities; NATO. Klíčová slova: Obranná strategie; koncepční dokumenty; malý stat; vojenské schopnos- ti; NATO. 23 Vojenské rozhledy č. 4/2020 Defence strategies of the smaller NATO states INTRODUCTION The re-emergence of the use of military power in the Eastern Europe after annexation of Crimea has again created a dilemma of making choices within defence policy of small states. -

Towards the Kalmar Union
S P E C I A L I Z E D A G E N C I E S TOWARDS THE KALMAR UNION Dear Delegates, Welcome to the 31st Annual North American Model United Nations 2016 at the University of Toronto! On behalf of all of the staff at NAMUN, we welcome you to the Specialized Agency branch of the conference. I, and the rest of the committee staff are thrilled to have you be a delegate in Scandinavia during the High Middle Ages, taking on this challenging yet fascinating topic on the futures of the three Scandinavian Kingdoms in a time of despair, poverty, dependence and competitiveness. This will truly be a new committee experience, as you must really delve into the history of these Kingdoms and figure out how to cooperate with each other without sending everyone into their demise. To begin, in the Towards the Kalmar Union Specialized Agency, delegates will represent influential characters from Denmark, Norway and Sweden, which include prominent knights, monarchs, nobles, and important religious figures who dominate the political, military and economic scenes of their respective Kingdoms. The impending issues that will be discussed at the meeting in Kalmar, Sweden include the future of the Danish and Norwegian crowns after the death of the sole heir to the thrones, Olaf II. Here, two distant relatives to Valdemar IV have a claim to the throne and delegates will need to decide who will succeed to the throne. The second order of business is to discuss the growing German presence in Sweden, especially in major economic cities. -

Norway: Defence 2008
Norwegian Defence 2008 Norwegian Defence 2008 2 CONTENT NORWEGIAN SECURITY And DEFEncE POLICY 4 1. Security Policy Objectives 5 Defence Policy Objectives 5 2. Defence Tasks 6 3. Areas of Government Focus 7 4. International Cooperation 8 UN 8 NATO 9 EU 10 Nordic cooperation 11 5. National Cooperation 12 DEFEncE STRUCTURE And AcTIVITIES 14 1. Constitutional Division of Responsibility in Norway 15 2. The Strategic Leadership of the Armed Forces 15 The Ministry Of Defence 16 3. The Defence Agencies 17 The Norwegian Armed Forces 17 4. The Norwegian Armed Forces 18 5. The Service Branches 19 The Norwegian Army 19 The Royal Norwegian Navy 20 Royal Norwegian Air Force 21 Home Guard 22 6. Personnel Policy 23 7. National Service 23 8. Materiel and Investments 24 Overview of Forces Engaged in International Operations 25 SUppLEMENt – THE FACTS 26 1. The Defence Budget 27 2. International Operations 27 3. Ranks and Insignia 28 4. Non-Governmental Organisations 29 5. Addresses 32 Norwegian Security and Defence Policy 4 1. SECURITY POLICY OBJECTIVES The principal objective of Norwegian security policy is to safeguard and promote national security policy interests. This is best achieved by contributing to peace, security and stability both in areas adjacent to Norway and in the wider world. Nationally Norway must be in a position to uphold its sovereignty and sove- reign rights and to exercise authority in order to safeguard our interests. At the same time, the progress of globalisation means that geo- graphical distance is no longer a determining factor for potential threats to our security. -

EL Education Core Practices
EL Education Core Practices A Vision for Improving Schools EL Education is a comprehensive school reform and school development model for elementary, middle, and high schools. The Core Practice Benchmarks describe EL Education in practice: what teachers, students, school leaders, families, and other partners do in fully implemented EL Education schools. The five core practices—learning expeditions, active pedagogy, school culture and character, leadership and school improvement, and structures—work in concert and support one another to promote high achievement through active learning, character growth, and teamwork. The Core Practice Benchmarks serve several purposes. They provide a comprehensive overview of the EL Education model, a planning guide for school leaders and teachers, a framework for designing professional development, and a tool for evaluating implementation. Each of the five core practices is comprised of a series of benchmarks. Each benchmark describes a particular area of practice and is organized by lettered components and numbered descriptors. A Different Approach to Teaching and Learning In EL Education schools… Learning is active. Students are scientists, urban planners, historians, and activists, investigating real community problems and collaborating with peers to develop creative, actionable solutions. Learning is challenging. Students at all levels are pushed and supported to do more than they think they can. Excellence is expected in the quality of their work and thinking. Learning is meaningful. Students apply their skills and knowledge to real-world issues and problems and make positive change in their communities. They see the relevance of their learning and are motivated by understanding that learning has purpose. Learning is public. -
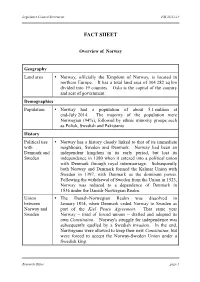
Fact Sheet on "Overview of Norway"
Legislative Council Secretariat FSC21/13-14 FACT SHEET Overview of Norway Geography Land area Norway, officially the Kingdom of Norway, is located in northern Europe. It has a total land area of 304 282 sq km divided into 19 counties. Oslo is the capital of the country and seat of government. Demographics Population Norway had a population of about 5.1 million at end-July 2014. The majority of the population were Norwegian (94%), followed by ethnic minority groups such as Polish, Swedish and Pakistanis. History Political ties Norway has a history closely linked to that of its immediate with neighbours, Sweden and Denmark. Norway had been an Denmark and independent kingdom in its early period, but lost its Sweden independence in 1380 when it entered into a political union with Denmark through royal intermarriage. Subsequently both Norway and Denmark formed the Kalmar Union with Sweden in 1397, with Denmark as the dominant power. Following the withdrawal of Sweden from the Union in 1523, Norway was reduced to a dependence of Denmark in 1536 under the Danish-Norwegian Realm. Union The Danish-Norwegian Realm was dissolved in between January 1814, when Denmark ceded Norway to Sweden as Norway and part of the Kiel Peace Agreement. That same year Sweden Norway – tired of forced unions – drafted and adopted its own Constitution. Norway's struggle for independence was subsequently quelled by a Swedish invasion. In the end, Norwegians were allowed to keep their new Constitution, but were forced to accept the Norway-Sweden Union under a Swedish king. Research Office page 1 Legislative Council Secretariat FSC21/13-14 History (cont'd) Independence The Sweden-Norway Union was dissolved in 1905, after the of Norway Norwegians voted overwhelmingly for independence in a national referendum. -

NORSOF Military Assistance Capability Development
Calhoun: The NPS Institutional Archive Theses and Dissertations Thesis and Dissertation Collection 2016-09 NORSOF military assistance capability development Hedenstrom, Andreas Monterey, California: Naval Postgraduate School http://hdl.handle.net/10945/50557 NAVAL POSTGRADUATE SCHOOL MONTEREY, CALIFORNIA DEFENSE ANALYSIS CAPSTONE PROJECT REPORT NORSOF MILITARY ASSISTANCE CAPABILITY DEVELOPMENT by Andreas Hedenstrom Marius Kristiansen September 2016 Capstone Advisor: Anna Simons Second Reader: George Lober Approved for public release. Distribution is unlimited. THIS PAGE INTENTIONALLY LEFT BLANK REPORT DOCUMENTATION PAGE Form Approved OMB No. 0704–0188 Public reporting burden for this collection of information is estimated to average 1 hour per response, including the time for reviewing instruction, searching existing data sources, gathering and maintaining the data needed, and completing and reviewing the collection of information. Send comments regarding this burden estimate or any other aspect of this collection of information, including suggestions for reducing this burden, to Washington headquarters Services, Directorate for Information Operations and Reports, 1215 Jefferson Davis Highway, Suite 1204, Arlington, VA 22202-4302, and to the Office of Management and Budget, Paperwork Reduction Project (0704-0188) Washington, DC 20503. 1. AGENCY USE ONLY 2. REPORT DATE 3. REPORT TYPE AND DATES COVERED (Leave blank) September 2016 Capstone project report 4. TITLE AND SUBTITLE 5. FUNDING NUMBERS NORSOF MILITARY ASSISTANCE CAPABILITY DEVELOPMENT 6. AUTHOR(S) Andreas Hedenstrom and Marius Kristiansen 7. PERFORMING ORGANIZATION NAME(S) AND ADDRESS(ES) 8. PERFORMING Naval Postgraduate School ORGANIZATION REPORT Monterey, CA 93943-5000 NUMBER 9. SPONSORING /MONITORING AGENCY NAME(S) AND 10. SPONSORING / ADDRESS(ES) MONITORING AGENCY Norwegian Special Operations Command (NORSOCOM), Oslo, Norway. -

The Rise and Decline of the Operational Level of War in Norway Halvor Johansen Operations
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by FHS Brage DEFENCE AND SECURITY STUDIES STUDIES SECURITY AND DEFENCE DEFENCE AND SECURITY STUDIES DEFENCE AND SECURITY STUDIES 2 2009 The rise and decline of the Operational Level of War in Halvor Johansen Norway The rise and decline of Once the hub of Norwegian defence have been addressed mainly by using planning, the Norwegian opera- technological or political science tional level plays a less signifi cant approaches. By adding social theory 2009 2 the Operational Level of role today. e operational level is to the perspectives this book also the link between the strategic and highlights the importance of civil- War in Norway tactical levels, adapting political and military relations and popular politi- strategic ends to feasible plans and cal support as a base of legitimacy Johansen Halvor Norway in War of Level Operational the of decline and rise The operations. is book looks at vari- for building and main taining mili- ous questions regarding the develop- tary institutions. Although the book ment of the operational level. How looks specifi cally at a development were the key institutions built up? specifi c to Norway, it also describes an And which events made them less sig- international trend experienced by a nifi cant? T raditionally, these questions number of military organisations. Lieutenant Colonel Halvor Johansen holds an MA in military studies from the Norwegian Defence University College (2007). He gradu- ated from the Norwegian Army Military Academy in 1993 and has had a variety of command and staff assignments. -

The Challenges and Dynamics of Alliance Policies: Norway, NATO and the High North Wrenn Yennie Lindgren & Nina Græger
7 The Challenges and Dynamics of Alliance Policies: Norway, NATO and the High North Wrenn Yennie Lindgren & Nina Græger This chapter sets out to discuss two major framework conditions for Norwegian foreign, security and defence policy: North Atlantic Treaty Organization (NATO) and the High North.1 Having to address increasingly heterogeneous security concerns and agendas, how do alliances shape their members’ foreign, security and defence policies? And how do the specific challenges related to the High North, such as Russia and other states’ policy agendas, form Norwegian responses and policies? In answering these questions, we aim to explore the framework conditions in a contemporary and historical context. Apart from contributing to the literature on Norway and NATO, we endeavour to add value to the general understanding of small states’ foreign and security policy enablers and constraints.2 1 The term ‘High North’ (nordområdene) often appears in Norwegian Government documents and is used interchangeably with ‘Arctic’. It does not refer solely to Norwegian territory, but is rather a broad concept that attempts to capture developments in the wider circumpolar area. See Jonas Gahr Støre, ‘The High North and the Arctic: The Norwegian Perspective’, Arctic Herald, Moskva, no. 2, Jun. 2012, www.regjeringen.no/no/aktuelt/nord_arktis/id685072/. 2 Christine Ingebritsen, ‘Norm Entrepreneurs: Scandinavia’s Role in World Politics’, in Christine Ingebritsen, Iver Neumann & Sieglinde Gstohl (eds), Small States in International Relations, Reykjavik: University of Iceland Press, 2006, pp. 273–85; Anders Wivel, Clive Archer & Alyson JK Bailes, ‘Setting the Scene: Small States in International Security’, in Clive Archer, Alyson JK Bailes & Anders Wivel (eds), Small States and International Security: Europe and Beyond, London: Routledge, 2014, pp. -

Serial Pinboarding in Contemporary Television
Serial Pinboarding in Contemporary Television Anne Ganzert Serial Pinboarding in Contemporary Television Anne Ganzert Serial Pinboarding in Contemporary Television Anne Ganzert University of Konstanz Konstanz, Germany ISBN 978-3-030-35271-4 ISBN 978-3-030-35272-1 (eBook) https://doi.org/10.1007/978-3-030-35272-1 © The Editor(s) (if applicable) and The Author(s), under exclusive licence to Springer Nature Switzerland AG 2020 This work is subject to copyright. All rights are solely and exclusively licensed by the Publisher, whether the whole or part of the material is concerned, specifically the rights of translation, reprinting, reuse of illustrations, recitation, broadcasting, reproduction on microfilms or in any other physical way, and transmission or information storage and retrieval, electronic adaptation, computer software, or by similar or dissimilar methodology now known or hereafter developed. The use of general descriptive names, registered names, trademarks, service marks, etc. in this publication does not imply, even in the absence of a specific statement, that such names are exempt from the relevant protective laws and regulations and therefore free for general use. The publisher, the authors and the editors are safe to assume that the advice and information in this book are believed to be true and accurate at the date of publication. Neither the pub- lisher nor the authors or the editors give a warranty, expressed or implied, with respect to the material contained herein or for any errors or omissions that may have been made. The publisher remains neutral with regard to jurisdictional claims in published maps and institu- tional affiliations.