Cluing in to Bittorrent
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Lab 5: Bittorrent Client Implementation
Lab 5: BitTorrent Client Implementation Due: Nov. 30th at 11:59 PM Milestone: Nov. 19th during Lab Overview In this lab, you and your lab parterner will develop a basic BitTorrent client that can, at minimal, exchange a file between multiple peers, and at best, function as a full feature BitTorrent Client. The programming in this assignment will be in C requiring standard sockets, and thus you will not need to have root access. You should be able to develop your code on any CS lab machine or your personal machine, but all code will be tested on the CS lab. Deliverable Your submission should minimally include the following programs and files: • REDME • Makefile • bencode.c|h • bt lib.c|h • bt setup.c|h • bt client • client trace.[n].log • sample torrent.torrent Your README file should contain a short header containing your name, username, and the assignment title. The README should additionally contain a short description of your code, tasks accomplished, and how to compile, execute, and interpret the output of your programs. Your README should also contain a list of all submitted files and code and the functionality implemented in different code files. This is a large assignment, and this will greatly aid in grading. As always, if there are any short answer questions in this lab write-up, you should provide well marked answers in the README, as well as indicate that you’ve completed any of the extra credit (so that I don’t forget to grade it). Milestones The entire assignment will be submitted and graded, but your group will also hold a milestone meeting to receive feedback on your current implementation. -

A Decentralized Cloud Storage Network Framework
Storj: A Decentralized Cloud Storage Network Framework Storj Labs, Inc. October 30, 2018 v3.0 https://github.com/storj/whitepaper 2 Copyright © 2018 Storj Labs, Inc. and Subsidiaries This work is licensed under a Creative Commons Attribution-ShareAlike 3.0 license (CC BY-SA 3.0). All product names, logos, and brands used or cited in this document are property of their respective own- ers. All company, product, and service names used herein are for identification purposes only. Use of these names, logos, and brands does not imply endorsement. Contents 0.1 Abstract 6 0.2 Contributors 6 1 Introduction ...................................................7 2 Storj design constraints .......................................9 2.1 Security and privacy 9 2.2 Decentralization 9 2.3 Marketplace and economics 10 2.4 Amazon S3 compatibility 12 2.5 Durability, device failure, and churn 12 2.6 Latency 13 2.7 Bandwidth 14 2.8 Object size 15 2.9 Byzantine fault tolerance 15 2.10 Coordination avoidance 16 3 Framework ................................................... 18 3.1 Framework overview 18 3.2 Storage nodes 19 3.3 Peer-to-peer communication and discovery 19 3.4 Redundancy 19 3.5 Metadata 23 3.6 Encryption 24 3.7 Audits and reputation 25 3.8 Data repair 25 3.9 Payments 26 4 4 Concrete implementation .................................... 27 4.1 Definitions 27 4.2 Peer classes 30 4.3 Storage node 31 4.4 Node identity 32 4.5 Peer-to-peer communication 33 4.6 Node discovery 33 4.7 Redundancy 35 4.8 Structured file storage 36 4.9 Metadata 39 4.10 Satellite 41 4.11 Encryption 42 4.12 Authorization 43 4.13 Audits 44 4.14 Data repair 45 4.15 Storage node reputation 47 4.16 Payments 49 4.17 Bandwidth allocation 50 4.18 Satellite reputation 53 4.19 Garbage collection 53 4.20 Uplink 54 4.21 Quality control and branding 55 5 Walkthroughs ............................................... -

Replication Strategies for Streaming Media
“replication-strategies” — 2007/4/24 — 10:56 — page 1 — #1 Research Report No. 2007:03 Replication Strategies for Streaming Media David Erman Department of Telecommunication Systems, School of Engineering, Blekinge Institute of Technology, S–371 79 Karlskrona, Sweden “replication-strategies” — 2007/4/24 — 10:56 — page 2 — #2 °c 2007 by David Erman. All rights reserved. Blekinge Institute of Technology Research Report No. 2007:03 ISSN 1103-1581 Published 2007. Printed by Kaserntryckeriet AB. Karlskrona 2007, Sweden. This publication was typeset using LATEX. “replication-strategies” — 2007/4/24 — 10:56 — page i — #3 Abstract Large-scale, real-time multimedia distribution over the Internet has been the subject of research for a substantial amount of time. A large number of mechanisms, policies, methods and schemes have been proposed for media coding, scheduling and distribution. Internet Protocol (IP) multicast was expected to be the primary transport mechanism for this, though it was never deployed to the expected extent. Recent developments in overlay networks has reactualized the research on multicast, with the consequence that many of the previous mechanisms and schemes are being re-evaluated. This report provides a brief overview of several important techniques for media broad- casting and stream merging, as well as a discussion of traditional IP multicast and overlay multicast. Additionally, we present a proposal for a new distribution system, based on the broadcast and stream merging algorithms in the BitTorrent distribution and repli- cation system. “replication-strategies” — 2007/4/24 — 10:56 — page ii — #4 ii “replication-strategies” — 2007/4/24 — 10:56 — page iii — #5 CONTENTS Contents 1 Introduction 1 1.1 Motivation . -
Bittorrent Files Hace Stopped Downloading
bittorrent files hace stopped downloading Why Some Torrents Don’t Download? A torrent that doesn’t start downloading or one that suddenly stops can be very frustrating. You check your Internet connection, the cables, and everything looks good. So what can be the reasons for those torrents that don’t seem to work? Some Torrents Don’t Download. The main reason behind a torrent file that doesn’t even start downloading is the lack of seeders and peers. In other words, there is no one seeding that file, meaning there’s no place where you can download it from. That’s why it’s very important that you have a look at the number of seeders and peers every time you start a new download. Seeders are the users who already finished downloading and are only sharing. The peers are the ones like you, the ones who are downloading and uploading at the same time. Some Files Suddenly Stop Downloading. This is another common scenario. We’ve all been there when a torrent stops at some moment, such as 99%. That usually happens when there are only peers, but no seeders . If you think about it, it makes total sense. The peers have many parts of the torrent in common, and they will share those between them. But because there are zero seeders, no one has the entire file , and everyone will share the same parts and stop in the same percentage point. A Dead Torrent. Both of the situations we just saw are what users in the community call a “dead torrent”. -

Improving Fairness in Peer-To-Peer Networks by Separating the Role of Seeders in Network Infrastructures
Turkish Journal of Electrical Engineering & Computer Sciences Turk J Elec Eng & Comp Sci (2016) 24: 2255 { 2266 http://journals.tubitak.gov.tr/elektrik/ ⃝c TUB¨ ITAK_ Research Article doi:10.3906/elk-1402-304 Improving fairness in peer-to-peer networks by separating the role of seeders in network infrastructures Alireza NAGHIZADEH∗, Reza EBRAHIMI ATANI Department of Computer Engineering, Faculty of Engineering, University of Guilan, Rasht, Iran Received: 27.02.2014 • Accepted/Published Online: 08.07.2014 • Final Version: 15.04.2016 Abstract:Fairness is one of the most important challenges that should be considered as a priority when designing a P2P file-sharing network. An unfair P2P network may attract free-riders, frustrate the majority of users, and consequently shorten the longevity of files. When BitTorrent protocol was first introduced, by suggesting new algorithms like tit-for- tat or rarest-first and combining them with methods like choking and unchoking, it pushed fairness one step forward. However, BitTorrent did not bring a plenary solution and has its own shortcomings. For instance, neither this protocol nor other P2P protocols that we are aware of precisely indicate how seeders should be treated in their networks. Most of the time they dictate that seeders upload as much as possible. With this approach, seeders can easily be abused by free-riders. It gets even worse when we realize that for lack of a good infrastructure a lawful user may become a free-rider unknowingly. The purpose of this paper is to address this problem by suggesting a novel and universal method that can be implemented in current P2P networks. -

Sok: Tools for Game Theoretic Models of Security for Cryptocurrencies
SoK: Tools for Game Theoretic Models of Security for Cryptocurrencies Sarah Azouvi Alexander Hicks Protocol Labs University College London University College London Abstract form of mining rewards, suggesting that they could be prop- erly aligned and avoid traditional failures. Unfortunately, Cryptocurrencies have garnered much attention in recent many attacks related to incentives have nonetheless been years, both from the academic community and industry. One found for many cryptocurrencies [45, 46, 103], due to the interesting aspect of cryptocurrencies is their explicit consid- use of lacking models. While many papers aim to consider eration of incentives at the protocol level, which has motivated both standard security and game theoretic guarantees, the vast a large body of work, yet many open problems still exist and majority end up considering them separately despite their current systems rarely deal with incentive related problems relation in practice. well. This issue arises due to the gap between Cryptography Here, we consider the ways in which models in Cryptog- and Distributed Systems security, which deals with traditional raphy and Distributed Systems (DS) can explicitly consider security problems that ignore the explicit consideration of in- game theoretic properties and incorporated into a system, centives, and Game Theory, which deals best with situations looking at requirements based on existing cryptocurrencies. involving incentives. With this work, we offer a systemati- zation of the work that relates to this problem, considering papers that blend Game Theory with Cryptography or Dis- Methodology tributed systems. This gives an overview of the available tools, and we look at their (potential) use in practice, in the context As we are covering a topic that incorporates many different of existing blockchain based systems that have been proposed fields coming up with an extensive list of papers would have or implemented. -

Blockchain and The
NOTES ACKNOWLEDGMENTS INDEX Notes Introduction 1. The manifesto dates back to 1988. See Timothy May, “The Crypto Anarchist Manifesto” (1992), https:// www . activism . net / cypherpunk / crypto - anarchy . html. 2. Ibid. 3. Ibid. 4. Ibid. 5. Ibid. 6. Timothy May, “Crypto Anarchy and Virtual Communities” (1994), http:// groups . csail . mit . edu / mac / classes / 6 . 805 / articles / crypto / cypherpunks / may - virtual - comm . html. 7. Ibid. 8. For example, as we wi ll describe in more detail in Chapter 1, the Bitcoin blockchain is currently stored on over 6,000 computers in eighty- nine jurisdictions. See “Global Bitcoin Node Distribution,” Bitnodes, 21 . co, https:// bitnodes . 21 . co / . Another large blockchain- based network, Ethereum, has over 12,000 nodes, also scattered across the globe. See Ethernodes, https:// www . ethernodes . org / network / 1. 9. See note 8. 10. Some blockchains are not publicly accessible (for more on this, see Chapter 1). These blockchains are referred to as “private blockchains” and are not the focus of this book. 11. See Chapter 1. 12. The Eu ro pean Securities and Market Authority, “Discussion Paper: The Dis- tributed Ledger Technology Applied to Securities Markets,” ESMA / 2016 / 773, June 2, 2016: at 17, https:// www . esma . europa . eu / sites / default / files / library / 2016 - 773 _ dp _ dlt . pdf. 213 214 NOTES TO PAGES 5–13 13. The phenomena of order without law also has been described in other con- texts, most notably by Robert Ellickson in his seminal work Order without Law (Cambridge, MA: Harvard University Press, 1994). 14. Joel Reidenberg has used the term “lex informatica” to describe rules imple- mented by centralized operators online. -

Proofs of Replication Are Also Relevant in the Private-Verifier Setting of Proofs of Data Replication
PoReps: Proofs of Space on Useful Data Ben Fisch Stanford University, Protocol Labs Abstract A proof-of-replication (PoRep) is an interactive proof system in which a prover defends a publicly verifiable claim that it is dedicating unique resources to storing one or more retrievable replicas of a data file. In this sense a PoRep is both a proof of space (PoS) and a proof of retrievability (PoR). This paper establishes a foundation for PoReps, exploring both their capabilities and their limitations. While PoReps may unconditionally demonstrate possession of data, they fundamentally cannot guarantee that the data is stored redundantly. Furthermore, as PoReps are proofs of space, they must rely either on rational time/space tradeoffs or timing bounds on the online prover's runtime. We introduce a rational security notion for PoReps called -rational replication based on the notion of an -Nash equilibrium, which captures the property that a server does not gain any significant advantage by storing its data in any other (non-redundant) format. We apply our definitions to formally analyze two recently proposed PoRep constructions based on verifiable delay functions and depth robust graphs. Lastly, we reflect on a notable application of PoReps|its unique suitability as a Nakamoto consensus mechanism that replaces proof-of-work with PoReps on real data, simultaneously incentivizing and subsidizing the cost of file storage. 1 Introduction A proof-of-replication (PoRep) builds on the two prior concepts of proofs-of-retrievability (PoR) [30] and proofs-of-space (PoS) [24]. In the former a prover demonstrates that it can retrieve a file and in the latter the prover demonstrates that it is using some minimum amount of space to store information. -

P2P File Sharing P2P File Sharing
P2P File Sharing P2P file sharing Alice chooses one of the peers, Bob. File is copied from Bob’s PC to Example Alice’s notebook: HTTP Alice runs P2P client While Alice downloads, other application on her notebook users uploading from Alice. computer Alice’s peer is both a Web client Intermittently connects to and a transient Web server. Internet; gets new IP address All peers are servers = highly for each connection scalable! Asks for “Hey Jude” Application displays other peers that have copy of Hey Jude. P2P: centralized directory (Napster’s Approach) Bob centralized directory server original “Napster” design 1 1) when peer connects, it peers 1 informs central server: IP address 1 3 content 2 1 2) Alice queries for “Hey Jude” 3) Alice requests file from Alice Bob P2P: problems with centralized directory file transfer is Single point of failure decentralized, but locating content is Performance highly decentralized bottleneck Copyright infringement Query flooding: Gnutella overlay network: graph edge between peer X fully distributed and Y if there’s a TCP no central server connection public domain all active peers and protocol edges is overlay net many Gnutella clients Edge is not a physical implementing protocol link Given peer will typically be connected with < 10 overlay neighbors Gnutella: protocol Ì File transfer: Query message HTTP sent over existing TCP connections Query Ì peers forward QueryHit Query message Ì QueryHit sent over reverse Query path QueryHit Scalability: limited scope flooding Gnutella: Peer joining 1. Joining peer X must find some other peer in Gnutella network: use list of candidate peers 2. -
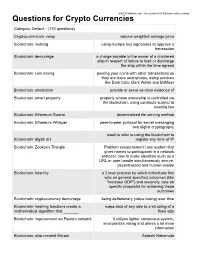
Questions for Crypto Currencies
www.YoYoBrain.com - Accelerators for Memory and Learning Questions for Crypto Currencies Category: Default - (170 questions) Cryptocurrencies: vwap volume weighted average price Blockchain: multisig using multiple key signatures to approve a transaction Blockchain: demurrage a charge payable to the owner of a chartered ship in respect of failure to load or discharge the ship within the time agreed Blockchain: coin mixing pooling your coins with other transactions so they are more anonymous, using services like Dark Coin, Dark Wallet and BitMixer Blockchain: attestation provide or serve as clear evidence of Blockchain: smart property property whose ownership is controlled via the blockchain, using contracts subject to existing law Blockchain: Ethereum Swarm decentralized file serving method Blockchain: Ethereum Whisper peer-to-peer protocol for secret messaging and digital cryptography used to refer to using the blockchain to Blockchain: digital art register any form of IP Blockchain: Zookos's Triangle Problem encountered in any system that gives names to participants in a network protocol: how to make identities such as a URL or user handle simultaneously secure, decentralized and human-usable Blockchain: futarchy a 2 level process by which individuals first vote on general specified outcomes (like "increase GDP") and secondly, vote on specific proposals for achieving those outcomes Blockchain: cryptocurrency demurrage being deflationary (value losing) over time Blockchain: hashing functions create a maps data of any size to a bit string -

Compsci 514: Computer Networks Lecture 21-2: from Bittorrent to Bittyrant Problem Statement
CompSci 514: Computer Networks Lecture 21-2: From BitTorrent to BitTyrant Problem Statement ... Server • One-to-many content distribution – Millions of clients downloading from the same server Evolving Solutions • Observation: duplicate copies of data are sent • Solutions – IP multicast – End system multicast – Content distribution networks e.g. Akamai – P2P cooperative content distribution • Bittorrent etc. IP multicast • End systems join a multicast group • Routers set up a multicast tree • Packets are duplicated and forwarded to multiple next hops at routers • Multicast pros and cons End system multicast • End systems rather than routers organize into a tree, forward and duplicate packets • Pros and cons Content distribution networks • Akamai – Works well but expensive, requires infrastructure support Peer-to-Peer Cooperative Content Distribution u Use the client’s uplink bandwidth u New problem: incentives for cooperation or how to motivate clients to upload The Gnutella approach u All nodes are true peers u A peer is the publisher, the uploader and the downloader. u No single point of failure. u Efficiency and scalability issue: u File searches span across a large number of nodes generating lots of traffic. u Integrity, i.e.content pollution issue: u Anyone can claim that he publishes valid content u No guarantee of quality of objects u Incentive issue: u No incentives for cooperation (free-riding in Gnutella) Outline u Problem of Content Distribution u The BitTorrent approach u BitTyrant BitTorrent overview Tracker 1 2 3 Leecher A Seeder Leecher C Leecher B u File is divided into chunks (e.g. 256KB) uShA1 hashes of all the pieces are included in the .torrent file for integrity check uA chunk is divided into sub-pieces to improve efficiency u Seeders have all chunks of the file u Leechers have some or no chunks of the file BitTorrent overview Tracker 1 2 3 Leecher A Seeder Leecher C Leecher B u File is divided into chunks (e.g. -

Exploiting Bittorrent for Fun (But Not Profit)
Exploiting BitTorrent For Fun (But Not Profit) Nikitas Liogkas, Robert Nelson, Eddie Kohler, and Lixia Zhang University of California, Los Angeles fnikitas, rlnelson, kohler, [email protected] ABSTRACT the file can be downloaded from different peers. A meta- This paper assesses BitTorrent’s robustness against selfish peers, data file is associated with every download. This file con- who try to download more than their fair share by abusing existing tains information necessary for the download process, in- protocol mechanisms. We design and implement three selfish-peer cluding the number of pieces and hashes for all the pieces; exploits and evaluate their effectiveness on public and private tor- the hashes are used by peers to verify that a piece has been rents. In practice, BitTorrent appears quite robust against this kind received correctly. This metadata file is typically created by of exploit: selfish peers can sometimes obtain more bandwidth, and the content provider, who must also launch at least one client honest peers’ download rates suffer slightly in consequence, but we offering the entire file for download. In order to join the observe no considerable degradation of the system’s quality of ser- download process, a client retrieves the metadata file out of vice. We identify private-torrent scenarios in which a selfish peer band, usually either from a well-known website or by email. could benefit more significantly at the expense of honest peers, and It then contacts the tracker, a centralized component that discuss the BitTorrent protocol mechanisms that lead to robustness by rendering these scenarios infeasible. keeps track of all the peers participating in the download.