Government Hacking
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Electronic Communications Surveillance
Electronic Communications Surveillance LAUREN REGAN “I think you’re misunderstanding the perceived problem here, Mr. President. No one is saying you broke any laws. We’re just saying it’s a little bit weird that you didn’t have to.”—John Oliver on The Daily Show1 The government is collecting information on millions of citizens. Phone, Internet, and email habits, credit card and bank records—vir- tually all information that is communicated electronically is subject to the watchful eye of the state. The government is even building a nifty, 1.5 million square foot facility in Utah to house all of this data.2 With the recent exposure of the NSA’s PRISM program by whistleblower Edward Snowden, many people—especially activists—are wondering: How much privacy do we actually have? Well, as far as electronic pri- vacy, the short answer is: None. None at all. There are a few ways to protect yourself, but ultimately, nothing in electronic communications is absolutely protected. In the United States, surveillance of electronic communications is governed primarily by the Electronic Communications Privacy Act of 1986 (ECPA), which is an extension of the 1968 Federal Wiretap act (also called “Title III”) and the Foreign Intelligence Surveillance Act (FISA). Other legislation, such as the USA PATRIOT Act and the Communications Assistance for Law Enforcement Act (CALEA), sup- plement both the ECPA and FISA. The ECPA is divided into three broad areas: wiretaps and “electronic eavesdropping,” stored messages, and pen registers and trap-and-trace devices. Each degree of surveillance requires a particular burden that the government must meet in order to engage in the surveillance. -

Summary of U.S. Foreign Intelligence Surveillance Law, Practice, Remedies, and Oversight
___________________________ SUMMARY OF U.S. FOREIGN INTELLIGENCE SURVEILLANCE LAW, PRACTICE, REMEDIES, AND OVERSIGHT ASHLEY GORSKI AMERICAN CIVIL LIBERTIES UNION FOUNDATION AUGUST 30, 2018 _________________________________ TABLE OF CONTENTS QUALIFICATIONS AS AN EXPERT ............................................................................................. iii INTRODUCTION ......................................................................................................................... 1 I. U.S. Surveillance Law and Practice ................................................................................... 2 A. Legal Framework ......................................................................................................... 3 1. Presidential Power to Conduct Foreign Intelligence Surveillance ....................... 3 2. The Expansion of U.S. Government Surveillance .................................................. 4 B. The Foreign Intelligence Surveillance Act of 1978 ..................................................... 5 1. Traditional FISA: Individual Orders ..................................................................... 6 2. Bulk Searches Under Traditional FISA ................................................................. 7 C. Section 702 of the Foreign Intelligence Surveillance Act ........................................... 8 D. How The U.S. Government Uses Section 702 in Practice ......................................... 12 1. Data Collection: PRISM and Upstream Surveillance ........................................ -

Limitless Surveillance at the Fda: Pro- Tecting the Rights of Federal Whistle- Blowers
LIMITLESS SURVEILLANCE AT THE FDA: PRO- TECTING THE RIGHTS OF FEDERAL WHISTLE- BLOWERS HEARING BEFORE THE COMMITTEE ON OVERSIGHT AND GOVERNMENT REFORM HOUSE OF REPRESENTATIVES ONE HUNDRED THIRTEENTH CONGRESS SECOND SESSION FEBRUARY 26, 2014 Serial No. 113–88 Printed for the use of the Committee on Oversight and Government Reform ( Available via the World Wide Web: http://www.fdsys.gov http://www.house.gov/reform U.S. GOVERNMENT PRINTING OFFICE 87–176 PDF WASHINGTON : 2014 For sale by the Superintendent of Documents, U.S. Government Printing Office Internet: bookstore.gpo.gov Phone: toll free (866) 512–1800; DC area (202) 512–1800 Fax: (202) 512–2104 Mail: Stop IDCC, Washington, DC 20402–0001 VerDate Aug 31 2005 11:40 Mar 31, 2014 Jkt 000000 PO 00000 Frm 00001 Fmt 5011 Sfmt 5011 C:\DOCS\87176.TXT APRIL COMMITTEE ON OVERSIGHT AND GOVERNMENT REFORM DARRELL E. ISSA, California, Chairman JOHN L. MICA, Florida ELIJAH E. CUMMINGS, Maryland, Ranking MICHAEL R. TURNER, Ohio Minority Member JOHN J. DUNCAN, JR., Tennessee CAROLYN B. MALONEY, New York PATRICK T. MCHENRY, North Carolina ELEANOR HOLMES NORTON, District of JIM JORDAN, Ohio Columbia JASON CHAFFETZ, Utah JOHN F. TIERNEY, Massachusetts TIM WALBERG, Michigan WM. LACY CLAY, Missouri JAMES LANKFORD, Oklahoma STEPHEN F. LYNCH, Massachusetts JUSTIN AMASH, Michigan JIM COOPER, Tennessee PAUL A. GOSAR, Arizona GERALD E. CONNOLLY, Virginia PATRICK MEEHAN, Pennsylvania JACKIE SPEIER, California SCOTT DESJARLAIS, Tennessee MATTHEW A. CARTWRIGHT, Pennsylvania TREY GOWDY, South Carolina TAMMY DUCKWORTH, Illinois BLAKE FARENTHOLD, Texas ROBIN L. KELLY, Illinois DOC HASTINGS, Washington DANNY K. DAVIS, Illinois CYNTHIA M. LUMMIS, Wyoming PETER WELCH, Vermont ROB WOODALL, Georgia TONY CARDENAS, California THOMAS MASSIE, Kentucky STEVEN A. -

FBI's Carnivore: How Federal Agents May Be Viewing Your Personal E-Mail and Why There Is Nothing You Can Do About It
The FBI's Carnivore: How Federal Agents May Be Viewing Your Personal E-Mail and Why There Is Nothing You Can Do About It PETER J. GEORGITON* Much controversy has arisen over the FBI's proposal to use an e-mail and Internet surveillanceprogram, named "Carnivore," to assist its law enforcement efforts on the Information Superhighway. In this note, the authorexamines how Carnivoreoperates and its implicationsfor individuals 'privacy rights under the Fourth Amendment and the Electronic Communications Privacy Act of 1986 (ECPA). The author concludes that the current state of constitutional and statutory law governing electronicsurveillance indicates that the FBI can utilize Carnivore to conduct a wide range of intrusive searches with little or no legal justification. Carnivore'sability to retrieve more than mere e-mail messages of suspects, the FBI's checkered past on privacy issues, and the lack ofjudicial oversight make the potentialfor abuse of Carnivoregreat. As a result, Congress must take a hard look at both the ECPA and Carnivore to prevent law enforcement agenciesfrom using Carnivore to peer into our personal e-mails and Internet usage. Whether he wrote DOWN WITH BIG BROTHER, or whether he refrainedfrom writing it, made no difference.... The Thought Police would get him just the same. He had committed-would still have committed, even ifhe had never set pen to paper-the essential crime that contained all others in itself Thoughtcrime, they called it. Thoughtcrime was not a thing that could be concealedforever. You might dodge successfully for a while, even for years, but sooner or laterthey were bound to get you. -

Independent Technical Review of the Carnivore System Final Report
Contract No. 00-C-0328 IITRI CR-030-216 Independent Technical Review of the Carnivore System Final Report 8 December 2000 Contract No. 00-C-0328 IITRI CR-030-216 Independent Review of the Carnivore System Final Report Prepared by: Stephen P. Smith J. Allen Crider Henry H. Perritt, Jr. Mengfen Shyong Harold Krent Larry L. Reynolds Stephen Mencik 8 December 2000 IIT Research Institute Suite 400 8100 Corporate Drive Lanham, Maryland 20785-2231 301-731-8894 FAX 301-731-0253 IITRI CR-030-216 CONTENTS Executive Summary.................................................................................................................. vii ES.1 Introduction................................................................................................................... vii ES.2 Scope............................................................................................................................. vii ES.3 Approach....................................................................................................................... viii ES.4 Observations ................................................................................................................. viii ES.5 Conclusions................................................................................................................... xii ES.6 Recommendations......................................................................................................... xiv Section 1 Introduction 1.1 Purpose......................................................................................................................... -

Nor'easter News Volume 2 Issue 5
Established 2007 N ...........R'EASTER NEWS Make a Dif Setting the Re ference, Be a cord Straight Mentor on Housing BY ANDREW FREDETTE BY MICHAEL CAMPINELL Nor'easter Staff Nor'easter Staff Have you ever wondered Right after the hous what it would be like to have a ing selection for the 2009 - 2010 mentor when you where growing school year happened, rumors up? Wonder what the experience starting spreading like wildfire. might do for you and the experi This article is to help set those ru ence you might gain? Growing mors straight. Information in this up is a part of life that not ev article was received from Jennifer eryone wants to do. But there are Deburro-Jones, the Director oJ ways to revert to your child hood Residential Life at UNE. She and and feel like a kid again. UNE is I have spoke on several occasions running a mentor program with about the many different aspects the College Community Men of housing at UNE and she has toring Program. also sent me answers to specific The program consists of 55 questions about the housing se mentors right now who are all lection process and what is hap UNE students, and the group of TY GOWEN, NOR'EASTER NEWS pening next year. BUSH CENTER: George H.W. and Barbara Bush address UNE at the dedication ceremony on October 3, 2008. children they work with are any One of the first rumors is that where from kindergarten all the housing selection numbers are way to 8th grade. The age of the International Center not actually random. -

Congressional Correspondence
People Record 7006012 for The Honorable Peter T. King Help # ID Opened � WF Code Assigned To Template Due Date Priority Status 1 885995 11/3/2010 ESLIAISON4 (b)(6) ESEC Workflow 11/10/2010 9 CLOSED FEMA Draft Due to ESEC: 11/10/2010 ESEC Case Number (ESEC Use Only): 10-9970 To: Secretary Document Date: 10/25/2010 *Received Date: 11/03/2010 *Attachment: Yes Significant Correspondence (ESEC Use Only): Yes *Summary of Document: Write in support of the application submitted by the (b)(4) for $7,710,089 under the Staffing for Adequate Fire and Emergency Response grant program. *Category: Congressional *Type: Congressional - Substantive Issue *Action to be Taken: Assistant Secretary OLA Signature Status: Action: *Lead Component: FEMA *Signed By (ESEC Use Only): Component Reply Direct and cc: *Date Response Signed: 11/02/2010 Action Completed: 11/04/2010 *Complete on Time: Yes Attachments: 10-9970rcuri 10.25.10.pdf Roles: The Honorable Michael Arcuri(Primary, Sender), The Honorable Timothy H. Bishop(Sender) 2 884816 10/22/2010 ESLIAISON4 (b)(6) ESEC Workflow 11/5/2010 9 OPEN FEMA Reply Direct Final Due Date: 11/05/2010 ESEC Case Number (ESEC Use Only): 10-9776 To: Secretary Mode: Fax Document Date: 10/20/2010 *Received Date: 10/22/2010 *Attachment: Yes Significant Correspondence (ESEC Use Only): No *Summary of Document: Requests an Urban Area Security Initiative designation for seven southern San Joaquin Valley Counties. *Category: Congressional *Type: Congressional - Substantive Issue *Action to be Taken: Component Reply Direct and Cc: Status: -

Introduction Points
Introduction Points Ahmia.fi - Clearnet search engine for Tor Hidden Services (allows you to add new sites to its database) TORLINKS Directory for .onion sites, moderated. Core.onion - Simple onion bootstrapping Deepsearch - Another search engine. DuckDuckGo - A Hidden Service that searches the clearnet. TORCH - Tor Search Engine. Claims to index around 1.1 Million pages. Welcome, We've been expecting you! - Links to basic encryption guides. Onion Mail - SMTP/IMAP/POP3. ***@onionmail.in address. URSSMail - Anonymous and, most important, SECURE! Located in 3 different servers from across the globe. Hidden Wiki Mirror - Good mirror of the Hidden Wiki, in the case of downtime. Where's pedophilia? I WANT IT! Keep calm and see this. Enter at your own risk. Site with gore content is well below. Discover it! Financial Services Currencies, banks, money markets, clearing houses, exchangers. The Green Machine Forum type marketplace for CCs, Paypals, etc.... Some very good vendors here!!!! Paypal-Coins - Buy a paypal account and receive the balance in your bitcoin wallet. Acrimonious2 - Oldest escrowprovider in onionland. BitBond - 5% return per week on Bitcoin Bonds. OnionBC Anonymous Bitcoin eWallet, mixing service and Escrow system. Nice site with many features. The PaypalDome Live Paypal accounts with good balances - buy some, and fix your financial situation for awhile. EasyCoin - Bitcoin Wallet with free Bitcoin Mixer. WeBuyBitcoins - Sell your Bitcoins for Cash (USD), ACH, WU/MG, LR, PayPal and more. Cheap Euros - 20€ Counterfeit bills. Unbeatable prices!! OnionWallet - Anonymous Bitcoin Wallet and Bitcoin Laundry. BestPal BestPal is your Best Pal, if you need money fast. Sells stolen PP accounts. -

GLOBAL CENSORSHIP Shifting Modes, Persisting Paradigms
ACCESS TO KNOWLEDGE RESEARCH GLOBAL CENSORSHIP Shifting Modes, Persisting Paradigms edited by Pranesh Prakash Nagla Rizk Carlos Affonso Souza GLOBAL CENSORSHIP Shifting Modes, Persisting Paradigms edited by Pranesh Pra ash Nag!a Ri" Car!os Affonso So$"a ACCESS %O KNO'LE(GE RESEARCH SERIES COPYRIGHT PAGE © 2015 Information Society Project, Yale Law School; Access to Knowle !e for "e#elo$ment %entre, American Uni#ersity, %airo; an Instituto de Technolo!ia & Socie a e do Rio+ (his wor, is $'-lishe s'-ject to a %reati#e %ommons Attri-'tion./on%ommercial 0%%.1Y./%2 3+0 In. ternational P'-lic Licence+ %o$yri!ht in each cha$ter of this -oo, -elon!s to its res$ecti#e a'thor0s2+ Yo' are enco'ra!e to re$ro 'ce, share, an a a$t this wor,, in whole or in part, incl' in! in the form of creat . in! translations, as lon! as yo' attri-'te the wor, an the a$$ro$riate a'thor0s2, or, if for the whole -oo,, the e itors+ Te4t of the licence is a#aila-le at <https677creati#ecommons+or!7licenses7-y.nc73+07le!alco e8+ 9or $ermission to $'-lish commercial #ersions of s'ch cha$ter on a stan .alone -asis, $lease contact the a'thor, or the Information Society Project at Yale Law School for assistance in contactin! the a'thor+ 9ront co#er ima!e6 :"oc'ments sei;e from the U+S+ <m-assy in (ehran=, a $'-lic omain wor, create by em$loyees of the Central Intelli!ence A!ency / em-assy of the &nite States of America in Tehran, de$ict. -
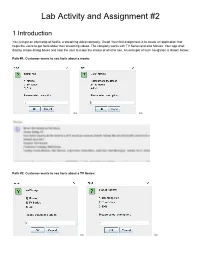
Lab Activity and Assignment #2
Lab Activity and Assignment #2 1 Introduction You just got an internship at Netfliz, a streaming video company. Great! Your first assignment is to create an application that helps the users to get facts about their streaming videos. The company works with TV Series and also Movies. Your app shall display simple dialog boxes and help the user to make the choice of what to see. An example of such navigation is shown below: Path #1: Customer wants to see facts about a movie: >> >> Path #2: Customer wants to see facts about a TV Series: >> >> >> >> Your app shall read the facts about a Movie or a TV Show from text files (in some other course you will learn how to retrieve this information from a database). They are provided at the end of this document. As part of your lab, you should be creating all the classes up to Section 3 (inclusive). As part of your lab you should be creating the main Netfliz App and making sure that your code does as shown in the figures above. The Assignment is due on March 8th. By doing this activity, you should be practicing the concept and application of the following Java OOP concepts Class Fields Class Methods Getter methods Setter methods encapsulation Lists String class Split methods Reading text Files Scanner class toString method Override superclass methods Scanner Class JOptionPane Super-class sub-class Inheritance polymorphism Class Object Class Private methods Public methods FOR loops WHILE Loops Aggregation Constructors Extending Super StringBuilder Variables IF statements User Input And much more.. -

Patrol Guide § 212-72
EXHIBIT K AOR307 An Investigation of NYPD’s Compliance with Rules Governing Investigations of Political Activity New York City Department of Investigation Office of the Inspector General for the NYPD (OIG-NYPD) Mark G. Peters Commissioner Philip K. Eure Inspector General for the NYPD August 23, 2016 AOR308 AN INVESTIGATION OF NYPD’S COMPLIANCE WITH RULES GOVERNING AUGUST 2016 INVESTIGATIONS OF POLITICAL ACTIVITY Table of Contents Overview ............................................................................................................................... 1 Executive Summary ............................................................................................................... 3 Introduction ........................................................................................................................ 11 I. NYPD Investigations of Political Activity: Handschu and Patrol Guide § 212-72 ....... 11 II. OIG-NYPD Investigation .............................................................................................. 12 Methodology and Access ..................................................................................................... 13 I. Treatment of Sensitive Information ............................................................................ 13 II. Compliance Criteria ..................................................................................................... 13 III. Scope and Sampling .................................................................................................... 14 -

Help I Am an Investigative Journalist in 2017
Help! I am an Investigative Journalist in 2017 Whistleblowers Australia Annual Conference 2016-11-20 About me • Information security professional Gabor Szathmari • Privacy, free speech and open gov’t advocate @gszathmari • CryptoParty organiser • CryptoAUSTRALIA founder (coming soon) Agenda Investigative journalism: • Why should we care? • Threats and abuses • Surveillance techniques • What can the reporters do? Why should we care about investigative journalism? Investigative journalism • Cornerstone of democracy • Social control over gov’t and private sector • When the formal channels fail to address the problem • Relies on information sources Manning Snowden Tyler Shultz Paul Stevenson Benjamin Koh Threats and abuses against investigative journalism Threats • Lack of data (opaque gov’t) • Journalists are imprisoned for doing their jobs • Sources are afraid to speak out Journalists’ Privilege • Evidence Amendment (Journalists’ Privilege) Act 2011 • Telecommunications (Interception and Access) Amendment (Data Retention) Act 2015 Recent Abuses • The Guardian: Federal police admit seeking access to reporter's metadata without warrant ! • The Intercept: Secret Rules Makes it Pretty Easy for the FBI to Spy on Journalists " • CBC News: La Presse columnist says he was put under police surveillance as part of 'attempt to intimidate’ # Surveillance techniques Brief History of Interception First cases: • Postal Service - Black Chambers 1700s • Telegraph - American Civil War 1860s • Telephone - 1890s • Short wave radio -1940s / 50s • Satellite (international calls) - ECHELON 1970s Recent Programs (2000s - ) • Text messages, mobile phone - DISHFIRE, DCSNET, Stingray • Internet - Carnivore, NarusInsight, Tempora • Services (e.g. Google, Yahoo) - PRISM, MUSCULAR • Metadata: MYSTIC, ADVISE, FAIRVIEW, STORMBREW • Data visualisation: XKEYSCORE, BOUNDLESSINFORMANT • End user device exploitation: HAVOK, FOXACID So how I can defend myself? Data Protection 101 •Encrypt sensitive data* in transit •Encrypt sensitive data* at rest * Documents, text messages, voice calls etc.