IRIX® 6.5.16 Update Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

ROADS and BRIDGES: the UNSEEN LABOR BEHIND OUR DIGITAL INFRASTRUCTURE Preface
Roads and Bridges:The Unseen Labor Behind Our Digital Infrastructure WRITTEN BY Nadia Eghbal 2 Open up your phone. Your social media, your news, your medical records, your bank: they are all using free and public code. Contents 3 Table of Contents 4 Preface 58 Challenges Facing Digital Infrastructure 5 Foreword 59 Open source’s complicated relationship with money 8 Executive Summary 66 Why digital infrastructure support 11 Introduction problems are accelerating 77 The hidden costs of ignoring infrastructure 18 History and Background of Digital Infrastructure 89 Sustaining Digital Infrastructure 19 How software gets built 90 Business models for digital infrastructure 23 How not charging for software transformed society 97 Finding a sponsor or donor for an infrastructure project 29 A brief history of free and public software and the people who made it 106 Why is it so hard to fund these projects? 109 Institutional efforts to support digital infrastructure 37 How The Current System Works 38 What is digital infrastructure, and how 124 Opportunities Ahead does it get built? 125 Developing effective support strategies 46 How are digital infrastructure projects managed and supported? 127 Priming the landscape 136 The crossroads we face 53 Why do people keep contributing to these projects, when they’re not getting paid for it? 139 Appendix 140 Glossary 142 Acknowledgements ROADS AND BRIDGES: THE UNSEEN LABOR BEHIND OUR DIGITAL INFRASTRUCTURE Preface Our modern society—everything from hospitals to stock markets to newspapers to social media—runs on software. But take a closer look, and you’ll find that the tools we use to build software are buckling under demand. -

An Automated Binary Security Update System for Freebsd
An Automated Binary Security Update System for FreeBSD Colin Percival Computing Lab, Oxford University [email protected] Abstract that a large number of people find the task of applying security patches and rebuilding affected programs to be difficult and/or confusing. Given that releases are on av- With the present trend towards increased reliance upon erage several months – and several security holes – old computer systems, the provision and prompt application by the time they are installed, the possibility arises that of security patches is becoming vital. Developers of all a new user will find his system compromised before he operating systems must generally be applauded for their has a chance to bring it up to date. success in this area; systems administrators, however, are often found lacking. Furthermore, there are some circumstances where build- ing from source is undesirable. Some embedded sys- Anecdotal evidence suggests that for FreeBSD much of tems might lack sufficient disk space to store the entire the difficulty arises out of the need to recompile from the source and object trees; some system administrators re- source code after applying security patches. Many peo- move part or all of the build toolchain in an (arguably ple, after spending years using closed-source point-and- misguided) attempt to thwart any attempt to build a click operating systems, find the concept of recompiling rootkit; and the purveyors of application-specific ‘toast- software to be entirely foreign, and even veteran users ers’ might very likely wish to keep the complexity of of open source software are often less than prompt about building from source entirely hidden from their users. -

IE 5.5 and Netscape 4.75 - Why Upgrade? ..Page 1
In This Issue . IE 5.5 and Netscape 4.75 - Why Upgrade? ..page 1 WindowsME for Home Computing ..…..…..page 1 Critical Updates are Essential ……..……….page 1 Win 95/98 Web Browser Upgrade.…………page 2 Permanent LRC Stations…………...……….page 2 cc:Mail is Retiring ……..…………..………..page 2 The newsletter for IPFW computer users Information Technology Services October 2000 Courses & Resources…………….……….….page 2 IE 5.5 and Netscape for Home 4.75 - Why Upgrade? Computing Campus surfers should update their browsers to the Microsoft recently released its upgrade to Windows 98 latest versions of Netscape and Internet Explorer (IE). for home computing — Windows Millennium (WindowsMe). Windows users may do so by the following instructions on Follett's IPFW Bookstore is now offering the CD to students, page 2. Macintosh users may obtain the instructions for faculty, and staff as part of IU's licensing agreement with creating an alias for either or both programs from the Help Microsoft. Is the upgrade for you? Windows Millennium Desk (e-mail: [email protected]). includes: Very basic digital media editing tools Why upgrade? In general, obtaining the latest 4 IE 5.5 (also downloadable for Windows 98) version of your favorite browser helps ensure that you have 4 4 Media Player 7 (also downloadable for Windows 98) the most capable and secure browser for today's Web If you have no compelling need for the above features environment. Specifically, the newest and most significant or if you take the time to do wnload IE 5.5 and/or Media Player 7 features of each include: for Windows 98, you may want to skip this upgrade. -

Znetlive SSL Compatible Applications, Platforms & Operating
ZNetLive SSL Compatible Applications, Platforms & Operating Systems Certificate Authority Root Apple MAC OS 9.0+ (circa 2002), includes 10.5.X and 10.6.X Future proof at 2048 bit, embedded in all Microsoft Windows XP, Vista, 7 and 8 (all devices and browsers and capable of upgrading versions inc 32/64 bit) weak encryption to a strong one is the most reliable Certificate Authority Root-GlobalSign. It is very important to ensure a flawless interaction of your online solutions with Default API Support within Hosting Control customers making connection with your web Panels server, reading emails, trusting your e- Ubersmith documents or running your code. Every WHMCS standard machine that uses trust of Public Key Infrastructure (PKI), e.g. S/MIME, SSL/TLS, Document Signing and Code Signing, has GlobalSign’s Root Certification present in it. Email Clients (S/MIME) ZNetLive’s SSL Certificates authenticated by GlobalSign have 2048 bit strength throughout Mulberry Mail complete Digital Certificate portfolio and Microsoft Outlook 99+ comply with recommendations of National Microsoft Entourage (OS/X) Institute of Standards and Technology (NIST) Qualcomm Eudora 6.2+ according to which all cryptographic keys Mozilla Thunderbird 1.0+ should be 2048 bit strength from 2011 onwards. Mail.app Anything weaker than 2048 bit encryption is Lotus Notes (6+) considered insecure. Because of this, the Netscape Communicator 4.51+ Certification Authorities and Browsers insists The Bat that all the EV SSL Certificates should be 2048 Apple Mail bit encryption. -

Netscape 6.2.3 Software for Solaris Operating Environment
What’s New in Netscape 6.2 Netscape 6.2 builds on the successful release of Netscape 6.1 and allows you to do more online with power, efficiency and safety. New is this release are: Support for the latest operating systems ¨ BETTER INTEGRATION WITH WINDOWS XP q Netscape 6.2 is now only one click away within the Windows XP Start menu if you choose Netscape as your default browser and mail applications. Also, you can view the number of incoming email messages you have from your Windows XP login screen. ¨ FULL SUPPORT FOR MACINTOSH OS X Other enhancements Netscape 6.2 offers a more seamless experience between Netscape Mail and other applications on the Windows platform. For example, you can now easily send documents from within Microsoft Word, Excel or Power Point without leaving that application. Simply choose File, “Send To” to invoke the Netscape Mail client to send the document. What follows is a more comprehensive list of the enhancements delivered in Netscape 6.1 CONFIDENTIAL UNTIL AUGUST 8, 2001 Netscape 6.1 Highlights PR Contact: Catherine Corre – (650) 937-4046 CONFIDENTIAL UNTIL AUGUST 8, 2001 Netscape Communications Corporation ("Netscape") and its licensors retain all ownership rights to this document (the "Document"). Use of the Document is governed by applicable copyright law. Netscape may revise this Document from time to time without notice. THIS DOCUMENT IS PROVIDED "AS IS" WITHOUT WARRANTY OF ANY KIND. IN NO EVENT SHALL NETSCAPE BE LIABLE FOR INDIRECT, SPECIAL, INCIDENTAL, OR CONSEQUENTIAL DAMAGES OF ANY KIND ARISING FROM ANY ERROR IN THIS DOCUMENT, INCLUDING WITHOUT LIMITATION ANY LOSS OR INTERRUPTION OF BUSINESS, PROFITS, USE OR DATA. -

Twenty Years of Berkeley Unix : from AT&T-Owned to Freely
Twenty Years of Berkeley Unix : From AT&T-Owned to Freely Redistributable Marshall Kirk McKusick Early History Ken Thompson and Dennis Ritchie presented the first Unix paper at the Symposium on Operating Systems Principles at Purdue University in November 1973. Professor Bob Fabry, of the University of California at Berkeley, was in attendance and immediately became interested in obtaining a copy of the system to experiment with at Berkeley. At the time, Berkeley had only large mainframe computer systems doing batch processing, so the first order of business was to get a PDP-11/45 suitable for running with the then-current Version 4 of Unix. The Computer Science Department at Berkeley, together with the Mathematics Department and the Statistics Department, were able to jointly purchase a PDP-11/45. In January 1974, a Version 4 tape was delivered and Unix was installed by graduate student Keith Standiford. Although Ken Thompson at Purdue was not involved in the installation at Berkeley as he had been for most systems up to that time, his expertise was soon needed to determine the cause of several strange system crashes. Because Berkeley had only a 300-baud acoustic-coupled modem without auto answer capability, Thompson would call Standiford in the machine room and have him insert the phone into the modem; in this way Thompson was able to remotely debug crash dumps from New Jersey. Many of the crashes were caused by the disk controller's inability to reliably do overlapped seeks, contrary to the documentation. Berkeley's 11/45 was among the first systems that Thompson had encountered that had two disks on the same controller! Thompson's remote debugging was the first example of the cooperation that sprang up between Berkeley and Bell Labs. -

Spybot - Search & Destroy Can Detect and Remove Spyware of Different Kinds from Your Computer
Description Spybot - Search & Destroy can detect and remove spyware of different kinds from your computer. Spyware is a relatively new kind of threat that common anti-virus applications do not cover yet. If you see new toolbars in your Internet Explorer that you didn't intentionally install, if your browser crashes, or if you browser start page has changed without your knowing, you most probably have spyware. But even if you don't see anything, you may be infected, because more and more spyware is emerging that is silently tracking your surfing behaviour to create a marketing profile of you that will be sold to advertisement companies. Spybot-S&D; is free, so there's no harm in trying to see if something snooped into your computer, too :) Spybot-S&D; can also clean usage tracks, an interesting function if you share your computer with other users and don't want them to see what you worked on. And for professional users, it allows to fix some registry inconsistencies and offers some extended reporting features. License Spybot-S&D; comes under the Dedication Public License. Requirements Microsoft Windows 95, 98, ME, NT, 2000 or XP (32 and 64 bit), 2003, Vista. Compatible with bootable PE disks (e.g. BartPE) and Wine. Minimum of 10 MB free hard disk space, more recommended for updates and backups. Usage We recommend that you continue by reading the tutorial next. © 2000-2008 Safer Networking Ltd. All rights reserved. I. Freeware First of all, the reasons why Spybot-S&D; is free: I.a. Dedication Spybot-S&D; is dedicated to the most wonderful girl on earth :) I.b. -
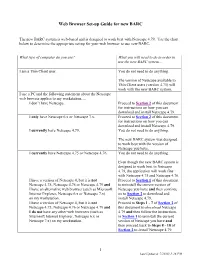
Web Browser Set-Up Guide for New BARC
Web Browser Set-up Guide for new BARC The new BARC system is web-based and is designed to work best with Netscape 4.79. Use the chart below to determine the appropriate set-up for your web browser to use new BARC. What type of computer do you use? What you will need to do in order to use the new BARC system… I am a Thin Client user. You do not need to do anything. The version of Netscape available to Thin Client users (version 4.75) will work with the new BARC system. I use a PC and the following statement about the Netscape web browser applies to my workstation…. I don’t have Netscape. Proceed to Section 2 of this document for instructions on how you can download and install Netscape 4.79. I only have Netscape 6.x or Netscape 7.x. Proceed to Section 2 of this document for instructions on how you can download and install Netscape 4.79. I currently have Netscape 4.79. You do not need to do anything. The new BARC system was designed to work best with the version of Netscape you have. I currently have Netscape 4.75 or Netscape 4.76. You do not need to do anything. Even though the new BARC system is designed to work best in Netscape 4.79, the application will work fine with Netscape 4.75 and Netscape 4.76. I have a version of Netscape 4, but it is not Proceed to Section 1 of this document Netscape 4.75, Netscape 4.76 or Netscape 4.79 and to uninstall the current version of I have an alternative web browser (such as Microsoft Netscape you have and then continue Internet Explorer, Netscape 6.x or Netscape 7.x) on to Section 2 to download and on my workstation. -

Why Websites Can Change Without Warning
Why Websites Can Change Without Warning WHY WOULD MY WEBSITE LOOK DIFFERENT WITHOUT NOTICE? HISTORY: Your website is a series of files & databases. Websites used to be “static” because there were only a few ways to view them. Now we have a complex system, and telling your webmaster what device, operating system and browser is crucial, here’s why: TERMINOLOGY: You have a desktop or mobile “device”. Desktop computers and mobile devices have “operating systems” which are software. To see your website, you’ll pull up a “browser” which is also software, to surf the Internet. Your website is a series of files that needs to be 100% compatible with all devices, operating systems and browsers. Your website is built on WordPress and gets a weekly check up (sometimes more often) to see if any changes have occured. Your site could also be attacked with bad files, links, spam, comments and other annoying internet pests! Or other components will suddenly need updating which is nothing out of the ordinary. WHAT DOES IT LOOK LIKE IF SOMETHING HAS CHANGED? Any update to the following can make your website look differently: There are 85 operating systems (OS) that can update (without warning). And any of the most popular roughly 7 browsers also update regularly which can affect your site visually and other ways. (Lists below) Now, with an OS or browser update, your site’s 18 website components likely will need updating too. Once website updates are implemented, there are currently about 21 mobile devices, and 141 desktop devices that need to be viewed for compatibility. -

Open Source Software Licenses: Perspectives of the End User and the Software Developer
White Paper: Open Source Software Licenses: Perspectives of the End User and the Software Developer By: Paul H. Arne Morris, Manning & Martin, L.L.P. Copyright © 2004 Morris, Manning & Martin, L.L.P. All rights reserved Table of Contents History of Open Source .........................................................................................................................2 Open Source Licenses Generally ..........................................................................................................3 Copyright Issues .........................................................................................................................3 Contract Considerations..............................................................................................................4 Limitation of Liability Clause.....................................................................................................5 Other Implied Warranties ...........................................................................................................6 UCITA ........................................................................................................................................6 Parties to License........................................................................................................................6 Specific Open Source Licenses..............................................................................................................7 GNU General Public License (GPL) ..........................................................................................7 -

Open Source Software: a History David Bretthauer University of Connecticut, [email protected]
University of Connecticut OpenCommons@UConn Published Works UConn Library 12-26-2001 Open Source Software: A History David Bretthauer University of Connecticut, [email protected] Follow this and additional works at: https://opencommons.uconn.edu/libr_pubs Part of the OS and Networks Commons Recommended Citation Bretthauer, David, "Open Source Software: A History" (2001). Published Works. 7. https://opencommons.uconn.edu/libr_pubs/7 Open Source Software: A History —page 1 Open Source Software: A History by David Bretthauer Network Services Librarian, University of Connecticut Open Source Software: A History —page 2 Abstract: In the 30 years from 1970 -2000, open source software began as an assumption without a name or a clear alternative. It has evolved into a s ophisticated movement which has produced some of the most stable and widely used software packages ever produced. This paper traces the evolution of three operating systems: GNU, BSD, and Linux, as well as the communities which have evolved with these syst ems and some of the commonly -used software packages developed using the open source model. It also discusses some of the major figures in open source software, and defines both “free software” and “open source software.” Open Source Software: A History —page 1 Since 1998, the open source softw are movement has become a revolution in software development. However, the “revolution” in this rapidly changing field can actually trace its roots back at least 30 years. Open source software represents a different model of software distribution that wi th which many are familiar. Typically in the PC era, computer software has been sold only as a finished product, otherwise called a “pre - compiled binary” which is installed on a user’s computer by copying files to appropriate directories or folders. -

Building and Installing Software Packages for Linux Building and Installing Software Packages for Linux
Building and Installing Software Packages for Linux Building and Installing Software Packages for Linux Table of Contents Building and Installing Software Packages for Linux.....................................................................................1 Mendel Cooper −−− http://personal.riverusers.com/~thegrendel/...........................................................1 1.Introduction...........................................................................................................................................1 2.Unpacking the Files..............................................................................................................................1 3.Using Make...........................................................................................................................................1 4.Prepackaged Binaries............................................................................................................................1 5.Termcap and Terminfo Issues...............................................................................................................1 6.Backward Compatibility With a.out Binaries.......................................................................................1 7.Troubleshooting....................................................................................................................................2 8.Final Steps.............................................................................................................................................2