Assurance Activity Report for Samsung Electronics Co., Ltd.Samsung Galaxy Devices on Android 11 - Spring
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
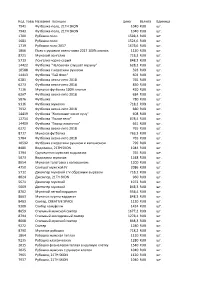
Код Товараназвание Позиции Цена Валюта Единица Измерения 7941 Футболка-Поло, 21Th Skon 1040 Rub Шт
Код_товараНазвание_позиции Цена Валюта Единица_измерения 7941 Футболка-поло, 21TH SKON 1040 RUB шт. 7943 Футболка-поло, 21TH SKON 1040 RUB шт. 1700 Рубашка поло 1598,4 RUB шт. 1681 Рубашка поло 1524,6 RUB шт. 1719 Рубашка поло 2017 1678,6 RUB шт. 1866 Поло с рукавом осень-зима 2017 100% хлопок 1120 RUB шт. 8721 Мужской лонгслив 718,2 RUB шт. 5713 Лонгслив черно-серый 848,3 RUB шт. 14422 Футболка "Человечек слушает музыку" 628,2 RUB шт. 10588 Футболка с коротким рукавом 593 RUB шт. 14413 Футболка "Гай Фокс" 603 RUB шт. 6281 Футболка весна-лето 2018 765 RUB шт. 6273 Футболка весна-лето 2018 850 RUB шт. 7116 Мужская футболка 100% хлопок 420 RUB шт. 6267 Футболка весна-лето 2018 684 RUB шт. 5876 Футболка 780 RUB шт. 9316 Футболка мужская 718,2 RUB шт. 7932 Футболка весна-лето 2018 880 RUB шт. 14419 Футболка "Космонавт косит луну" 608 RUB шт. 12714 Футболка "Голое тело" 878,4 RUB шт. 14409 Футболка "Город-лампочки" 661 RUB шт. 6272 Футболка весна-лето 2018 765 RUB шт. 8717 Мужская футболка 763,3 RUB шт. 5784 Футболка весна-лето 2018 765 RUB шт. 10592 Футболка с коротким рукавом и капюшоном 799 RUB шт. 8480 Водолазка, 21TH SKON 1044 RUB шт. 3794 Однотонная мужская водолазка 765 RUB шт. 5673 Водолазка мужская 1248 RUB шт. 8654 Мужская толстовка с капюшоном 1200 RUB шт. 4750 Свитшот мужской IV 2086 RUB шт. 5712 Джемпер мужской с V-образным вырезом 718,2 RUB шт. 8024 Джемпер, 21TH SKON 960 RUB шт. 5671 Джемпер мужской 1072 RUB шт. -

Bab Iii Metodologi Penelitian
BAB III METODOLOGI PENELITIAN A. Tujuan Penelitian Berdasarkan masalah-masalah yang telah peneliti rumuskan, maka tujuan penelitian ini adalah untuk mendapatkan pengetahuan yang benar (sahih / valid) dan dapat dipercaya (reliabel) mengenai: 1. Hubungan antara fitur produk dengan keputusan pembelian 2. Hubungan antara harga dengan keputusan pembelian 3. Hubungan antara fitur produk dan harga dengan keputusan pembelian. B. Tempat dan Waktu Penelitian 1. Tempat Penelitian Penelitian ini dilaksanakan di Fakultas Ekonomi Universitas Negeri Jakarta yang beralamat di Jalan Rawamangun Muka, Jakarta 13220. Tempat tersebut menarik bagi peneliti dikarenakan sebagian besar mahasiswa Fakultas Ekonomi Universitas Negeri Jakarta adalah pengguna smartphone Samsung Galaxy J series dan didalamnya terdapat masalah, dimana hal ini akan memudahkan peneliti selama melakukan penelitian. 2. Waktu Penelitian Waktu penelitian dilaksanakan sejak bulan Februari 2018 – Juli 2018. Waktu tersebut merupakan waktu yang tepat untuk melaksanakan penelitian karena jadwal perkuliahan peneliti sudah tidak padat dalam jangka waktu tersebut dan dirasa cukup untuk peneliti mendapatkan data guna menunjang kebutuhan penelitian. 41 42 C. Metode Penelitian 1. Metode Metode penelitian yang digunakan adalah metode survei, dengan pendekatan korelasional, yaitu untuk mengetahui tingkat hubungan antar variabel yang sedang diteliti yaitu variabel bebas dengan variabel terikat. Variabel bebas dalam penelitian ini adalah fitur produk dan harga sedangkan variabel terikatnya adalah keputusan pembelian. Jenis dan sumber data yang digunakan dalam penelitian ini adalah data primer untuk masing-masing variabel bebas dan variabel terikat yang berasal dari penyebaran angket (kuesioner). Angket ini merupakan suatu daftar pertanyaan tentang topik tertentu yang diberikan kepada subjek, baik secara individual atau kelompok, untuk mendapatkan informasi mengenai fitur produk, harga, dan keputusan pembelian smartphone Samsung Galaxy J series yang diperoleh dari mahasiswa Fakultas Ekonomi di Universitas Negeri Jakarta. -

Samsung Galaxy J7 J5 Leaked
Samsung Galaxy J7 J5 Leaked. Samsung Galaxy J7 J5 Leaked. 1 / 4 2 / 4 A partir da próxima semana, a nova série Samsung Galaxy J vai chegar às lojas portuguesas. São sem dúvida equipamentos interessantes e .... The Samsung Galaxy J5 (2017) edition is nearing its launch and had recently ... Today, we receive some Samsung Galaxy J5 2017 image leaks as well. ... Next articleSamsung Galaxy J7 (2016) started receiving April security ... 1. samsung galaxy leaked 2. samsung galaxy s11 leaked 3. samsung galaxy s21 leaked After several leaks, the Samsung Galaxy J7 (2016) and Galaxy J5 (2016) have finally been made official. Both devices are now listed on the South Korean ... samsung galaxy leaked samsung galaxy leaked, samsung galaxy s5 unlock code leaked, samsung galaxy s11 leaked, samsung galaxy s20 leaked, samsung galaxy s21 leaked, samsung galaxy note 20 leaked, samsung galaxy s7 leaked, leaked samsung galaxy s9, samsung galaxy note leaked, samsung galaxy note 7 leaked Soccer Manager 2020 – Top Football Management Game 1.0.8 Apk for android The Galaxy J7 (2017) to feature a 5.5” and the Galaxy J5 (2017) 5.2” display. Both device will be running on the latest Android 7.0 Nougat with .... Galaxy J5 (2016) and Galaxy J7 (2016) Specs and Images Leaked. By ... Of those devices, the Samsung Galaxy J5 (2016) and Galaxy J7 (2016) have already been ... It comes with the same camera setup as the J5 (2016). Datadog launches Watchdog to help you monitor your cloud apps So you think you can Cook TAP residents face off in cooking competition samsung galaxy s11 leaked 3 / 4 Advanced SystemCare 7 Ultimate Serial Keys are Here ! Samsung will be releasing two devices to add to its Galaxy J low-range smartphone series - the Galaxy J5 and the Galaxy J7: according to ... -

PENGARUH INOVASI, HARGA, DAN CITRA MEREK TERHADAP KEPUTUSAN PEMBELIAN PRODUK HANDPHONE SAMSUNG Studi Kasus Pada Mahasiswa/I Universitas Sanata Dharma
PLAGIAT MERUPAKAN TINDAKAN TIDAK TERPUJI PENGARUH INOVASI, HARGA, DAN CITRA MEREK TERHADAP KEPUTUSAN PEMBELIAN PRODUK HANDPHONE SAMSUNG Studi Kasus pada Mahasiswa/i Universitas Sanata Dharma Proposal Penelitian Diajukan dalam Rangka Menulis Skiripsi Program Studi Manajemen, Jurusan Manajemen Fakultas Ekonomi, Universitas Sanata Dharma Oleh : Martinus Yogas Pranoto NIM : 142214139 PROGRAM STUDI MANAJEMEN JURUSAN MANAJEMEN FAKULTAS EKONOMI UNIVERSITAS SANATA DHARMA YOGYAKARTA 2018 PLAGIAT MERUPAKAN TINDAKAN TIDAK TERPUJI PLAGIAT MERUPAKAN TINDAKAN TIDAK TERPUJI PLAGIAT MERUPAKAN TINDAKAN TIDAK TERPUJI MOTTO Kerahkan hati, pikiran, dan jiwamu ke dalam aksimu yang paling kecil sekalipun. Inilah rahasia kesuksesan. (Swami Sivananda) We will never know the real answer, before you try (Darwin Scot) Skripsi ini saya persembahkan untuk: Tuhan Yesus Kristus, atas berkat dan kasih-Nya Papa, Mama, dan keluarga, untuk seluruh kasih sayang dan dukungan baik moral dan materiil yang tak terbatas Sahabat-sahabatku tersayang atas hiburan, semangat, dan dukungan Almamater tercinta Universitas Sanata Dharma Yogyakarta iv PLAGIAT MERUPAKAN TINDAKAN TIDAK TERPUJI UNIVERSITAS SANATA DHARMA FAKULTAS EKONOMI JURUSAN MANAJEMEN-PROGRAM STUDI MANAJEMEN PERNYATAAN KEASLIAN KARYA TULIS Saya yang bertanda tangan di bawah ini, dengan ini menyatakan bahwa Skripsi dengan judul: PENGARUH INOVASI, HARGA DAN CITRA MEREK TERHADAP KEPUTUSAN PEMBELIAN PRODUK HANDPHONE SAMSUNG (Studi Kasus pada Mahasiswa/i Universitas Sanata Dharma Yogyakarta) dan diajukan untuk diuji pada tanggal -

Daily Dossier 4Th January 2018 Outlook
Daily Dossier 4th January 2018 Outlook Nifty ended 0.59% up at 10504.80. Daylong lackluster session followed Nifty Intraday Chart by aggressive buying in metal space led the index towards ending the session nearer to day’s high. It ended with a bullish candle, which implies Nifty may strengthen further towards 10550. Hence 10400, as discussed so many times, may continue to act as the base for the bulls. Midway support is placed around 10440. Upside resistances are placed around 10510 and 10550. Open positional calls- On the Nifty hourly chart; it closed just below a very short-term downward trend line resistance. Success- LUPIN (CMP- 878.15)- 10 trading sessions Positional buy call was given around 880-875 price zone for the TGT of 905 & 915. SL- below 855. (1 ful closing above both 50 and 100 hourly EMA is a positive indication. Breaking out immediate resistance trading sessions left). 10510 may unfold immediate rise towards 10550. BHEL (CMP- 100.75)- BTST Positional buy call was given around 100 for the TGT of 104. SL- Below 98.00. (1 trading sessions left). CASTROL (CMP- 191.45)- T+5 Trading sessions Positional buy call was Nifty patterns on multiple time frames show, 10400 continues to act as the base support for the bench- given around 193-192 for the TGT of 196 & 199. SL- Below 190. (3 trading mark index and today it ended on a bullish note. Further, Nifty breaking out 10550 is a possibility only sessions left). when it breaks out 10510. NALCO (CMP- 88.05)- 10 Trading Sessions Positional buy call was given around 86.50-86.00 for the TGT of 90 & 93. -

Android Supported Devices
Android Supported Devices Mobile Track Call Notifications Call Notifications Text Notifications Music Control Make Model OS Required Requires Google Play Requires OS 4.3+ Requires OS 4.3+ Requires OS 4.3+ Requires OS 4.4+ Services (Charge, Charge HR) (Surge) (Surge) (Surge) Samsung Galaxy S3 — ✓ ✓ ✓ — Galaxy S3 Mini (excluding Samsung — — “Value Edition” GT-i8200) ✓ ✓ ✓ Samsung Galaxy S4 — ✓ ✓ ✓ ✓ Samsung Galaxy S4 mini — ✓ ✓ ✓ ✓ Samsung Galaxy S4 Active — ✓ ✓ ✓ ✓ Samsung Galaxy S4 Zoom — ✓ ✓ ✓ ✓ Samsung Galaxy S5 — ✓ ✓ ✓ ✓ Samsung Galaxy S5 Mini — ✓ ✓ ✓ ✓ Samsung Galaxy S6 — ✓ ✓ ✓ ✓ Samsung Galaxy S6 Edge — ✓ ✓ ✓ ✓ Samsung Galaxy Note II — ✓ ✓ ✓ ✓ Samsung Galaxy Note II Duos — ✓ ✓ ✓ ✓ Samsung Galaxy Young 2 Duos — ✓ ✓ ✓ ✓ Samsung Galaxy Note III — ✓ ✓ ✓ ✓ Samsung Galaxy Note III Round — ✓ ✓ ✓ ✓ Samsung Galaxy Note 4 — ✓ ✓ ✓ ✓ Samsung Galaxy Note Edge — ✓ ✓ ✓ ✓ Samsung Galaxy Note 8.0 — ✓ ✓ ✓ ✓ Samsung Galaxy Note 10.1 — ✓ ✓ ✓ ✓ Samsung Galaxy Rugby Pro — ✓ ✓ ✓ ✓ Samsung Galaxy Mega — ✓ ✓ ✓ ✓ Samsung Galaxy S5 Active — ✓ ✓ ✓ ✓ Samsung Galaxy S5 Sport — ✓ ✓ ✓ ✓ Fitbit | Android Supported Devices Page 1 of 7 Android Supported Devices Mobile Track Call Notifications Call Notifications Text Notifications Music Control Make Model OS Required Requires Google Play Requires OS 4.3+ Requires OS 4.3+ Requires OS 4.3+ Requires OS 4.4+ Services (Charge, Charge HR) (Surge) (Surge) (Surge) Samsung Galaxy S3 Neo — ✓ ✓ ✓ — Samsung Galaxy S3 Slim — ✓ ✓ ✓ — Samsung Galaxy Ace Style — ✓ ✓ ✓ ✓ Samsung Galaxy Tab 3 — ✓ ✓ ✓ ✓ Samsung Galaxy Tab S — ✓ ✓ ✓ ✓ -

SHORT TAKES Compiled By: Ruchika Goel [email protected]
INDUSTRY | SHORT TAKES Compiled By: Ruchika Goel [email protected] Samsung Expands J Series Portfolio with Galaxy J7 and Galaxy J5 2016 edition amsung India announced the introduced a host of locally developed innovations launch of the 2016 editions of as part of their ‘Make for India’ initiative. This in- its popular Galaxy J7 and Gal- cludes a cost-effective 4G experience with the axy J5 smartphones, offering innovative Ultra Data Saving (UDS) mode. consumers more choices in Samsung India also launched an industry first Sthe J series, which is currently India’s larg- S Bike Mode, a dedicated bike mode that lets est selling smartphone range. consumers ‘ride tension free’ while encouraging The 2016 editions of Galaxy J7 and responsible riding. This was based on the insight Galaxy J5 better the previous benchmark that two-wheeler riders receive a lot of unim- set by the 2015 editions and elevate the portant calls and notifications while riding. The consumer experience to the next level. A S Bike Mode’s urgent call alert system notifies new design language with a stylish metal callers through an automated answering ma- frame and an upgraded display with an chine that the user is riding and is unavailable ergonomic height-to-width ratio are key to take calls. However, callers have the option changes from the predecessors. The to press 1 in case the call is urgent. As a safety smartphones’ performances have also feature, the in-built motion lock ensures that the been enhanced by incorporating better rider has to come to a halt before they can an- memory specifications. -

Samsung Expands J Series Portfolio with Galaxy J7 and Galaxy J5 2016
INDUSTRY | SHORT TAKES Compiled By: Ruchika Goel [email protected] Samsung Expands J Series Portfolio with Galaxy J7 and Galaxy J5 2016 edition amsung India announced the introduced a host of locally developed innovations launch of the 2016 editions of as part of their ‘Make for India’ initiative. This in- its popular Galaxy J7 and Gal- cludes a cost-effective 4G experience with the axy J5 smartphones, offering innovative Ultra Data Saving (UDS) mode. consumers more choices in Samsung India also launched an industry first Sthe J series, which is currently India’s larg- S Bike Mode, a dedicated bike mode that lets est selling smartphone range. consumers ‘ride tension free’ while encouraging The 2016 editions of Galaxy J7 and responsible riding. This was based on the insight Galaxy J5 better the previous benchmark that two-wheeler riders receive a lot of unim- set by the 2015 editions and elevate the portant calls and notifications while riding. The consumer experience to the next level. A S Bike Mode’s urgent call alert system notifies new design language with a stylish metal callers through an automated answering ma- frame and an upgraded display with an chine that the user is riding and is unavailable ergonomic height-to-width ratio are key to take calls. However, callers have the option changes from the predecessors. The to press 1 in case the call is urgent. As a safety smartphones’ performances have also feature, the in-built motion lock ensures that the been enhanced by incorporating better rider has to come to a halt before they can an- memory specifications. -

Global Android Smartphone Market: Strategy Recommendations
LAB University of Applied Sciences Faculty of Business Unit Degree Programme in International Business, Lappeenranta Nikolai Sedov Global Android Smartphone Market: Strategy Recommendations Thesis 2020 Abstract Nikolai Sedov Global Android Smartphone Market: Strategy Recommendations, 55 pages LAB University of Applied Sciences International Business, Lappeenranta Thesis 2020 Instructor: Jaani Väisänen, LAB University of Applied Sciences (Senior Lec- turer) The purpose of the research is to provide recommendations on business strate- gies for participants of the global Android smartphone market. The recommendations were developed through a descriptive and exploratory re- search of various related topics – first, the market was overviewed in general, then, products, pricing and general strategies of the case companies were ana- lysed. The main theoretical concepts used were David Aaker’s market analysis dimensions, Wiley Encyclopaedia of Management’s market competition spec- trum, part of the 4P “Marketing Mix”, Joel Dean’s “Pricing Policies for New Prod- ucts” and Porter’s Generic Strategies. The information was obtained from sec- ondary sources. The conclusion chapter presents an overview of the market, products, pricing, and strategies of the case market leader companies. From there, some general recommendations for other market participants and potential new entrants are provided. Keywords: Smartphone, Android, Market 2 Table of Contents 1 Introduction ................................................................................................. -

Smartphone Camera Module Comparison 2020 Vol 2: Focus on Samsung | Sample 1 Table of Contents
REVERSE COSTING® – STRUCTURAL, PROCESS & COST REPORT Samsung Camera Module Comparison 2020 Vol 2 Focus on Samsung SP20505 - Imaging report by Alok BHARTI, Elena BARBARINI Physical analysis done by Nicolas RADUFE August 2020 – Sample 22 bd Benoni Goullin +33 2 40 18 09 16 [email protected] www.systemplus.fr 44200 NANTES - FRANCE ©2020 by System Plus Consulting | SP20505 – Smartphone Camera Module Comparison 2020 Vol 2: Focus on Samsung | Sample 1 Table of Contents Overview / Introduction 5 Cost Comparison 88 o Executive Summary o CIS Die Cost Comparison o Reverse Costing Methodology o Front Facing o Glossary o Rear Facing Company Profile & Supply Chain 9 o Total CIS Die Price o SEMCO o Players & Market Forecast o CM Cost Comparison Physical Comparison 17 o Front Facing o Camera Module Overview o Rear Facing o Summary of the Physical Analysis o Total CM Price o Samsung Galaxy S20 Ultra Detailed Physical Analysis 110 o Samsung Galaxy S10 Plus o Samsung Galaxy S20 Ultra 5G o Samsung Galaxy 9 Plus ✓ Front Camera o Samsung Galaxy S8 ✓ Rear Camera o o Samsung Galaxy S7 Samsung galaxy S10+ ✓ Dual Front Camera o Summary Table ✓ Rear Camera o Samsung Galaxy A Series o Samsung galaxy S9 o Samsung Galaxy J Series ✓ Front Camera o Samsung Galaxy Note Series ✓ Rear Camera Physical Evolution 54 o Samsung galaxy S8 o Display Evolution ✓ Front Camera o Samsung Front Camera Evolution ✓ Rear Camera o Samsung Rear Camera Evolution o Samsung galaxy S7 o Samsung pixel technology ✓ Front Camera ✓ Rear Camera o Bonding & Stacking evolution Feedbacks 231 SystemPlus Consulting services 233 ©2020 by System Plus Consulting | SP20505 – Smartphone Camera Module Comparison 2020 Vol 2: Focus on Samsung | Sample 2 Executive Summary Overview / Introduction o Executive Summary The smartphone CMOS image sensor(CIS) has grown very rapidly over the past years. -
Instructions on How to Connect Your Mobile Phone Via Bluetooth® Using the Pairing Feature of the Mercedes-Benz Hands-Free System
Instructions on how to connect your mobile phone via Bluetooth® using the pairing feature of the Mercedes-Benz hands-free system. (All examples shown are using the COMAND system) For a connection between your mobile phone and your Mercedes-Benz hands-free system to be successful, Bluetooth® must be turned on in your mobile phone. Please make sure to also read the operating and pairing instructions of the mobile phone. Please follow the steps below to connect your mobile phone Samsung Galaxy S4 Active with the mobile phone application of your Mercedes-Benz hands-free system using Bluetooth®. Step 1 (to be performed on your Samsung Galaxy S4 Active) From the main screen of your mobile phone, 1. Push the "Applications" button and then find the “Settings” App 2. Select "Settings" 3. Select the option "Bluetooth" 4. Select the option to turn on Bluetooth® 5. Make your Samsung Galaxy S4 Active visible by selecting its name at the top of the screen or by selecting "Make phone visible". Please note that your mobile phone will be visible now for 120 seconds. During this time the pairing process must be started on the Mercedes-Benz hands-free system. Step 2 To get to the telephone screen of your Mercedes-Benz hands-free system press the “TEL” key on the radio or select "Phone". Page 1 of 4 Step 3 Select the application "Connect Dev." located in the lower left corner. Step 4 Select the "Search for Phone from Vehicle" function. Step 5 Select the "Start Search" function. Step 6 The system will now search for any Bluetooth® compatible phones. -
PENGARUH KESADARAN MEREK, PERSEPSI KUALITAS, DAN ASOSIASI MEREK TERHADAP KEPUTUSAN PEMBELIAN HANDPHONE SAMSUNG (Studi Kasus Maha
PENGARUH KESADARAN MEREK, PERSEPSI KUALITAS, DAN ASOSIASI MEREK TERHADAP KEPUTUSAN PEMBELIAN HANDPHONE SAMSUNG (Studi Kasus Mahasiswa Program Studi Pendidikan Ekonomi STKIP PGRI Sumatera Barat) JURNAL Oleh: VIKA YULIA SARI 12090078 PROGRAM STUDI PENDIDIKAN EKONOMI SEKOLAH TINGGI KEGURUAN DAN ILMU PENDIDIKAN (STKIP) PGRI SUMATERA BARAT 2017 HALAMAN PENGESAHAN JURNAL PENGARUH KESADARAN MEREK PERSEPSI KUALITAS, DAN ASOSIASI MEREK TERHADAP KEPUTUSAN PEMBELIAN HANDPHONE SAMSUNG (Studi Kasus Mahasiswa Program Studi Pendidikan Ekonomi STKIP PGRI Sumatera Barat) Nama Vika Yulia Sari NPM t2090078 Program Studi Pendidikan Ekonomi Institusi Sekolah Tinggi Keguruan dan Ilmu Pendidikan (STKIP) PGRI Sumatera Barat Padang, Februari 2017 Disetujui Oleh, Pembimbing I (Dessyt Gumanti, M.Pd.E ) marni, M.Pd) PENGARUH KESADARAN MEREK, PERSEPSI KUALITAS, DAN ASOSIASI MEREK TERHADAP KEPUTUSAN PEMBELIAN HANDPHONE SAMSUNG (Studi Kasus Mahasiswa Program Studi Pendidikan Ekonomi STKIP PGRI Sumatera Barat) Oleh: Vika Yulia Sari1, Dessyta Gumanti, M.Pd.E2, Sumarni, M.Pd3 Mahasiswa program studi pendidikan ekonomi STKIP PGRI Sumatera Barat Dosen STKIP PGRI Sumatera Barat Email : [email protected] ABSTRAK Penelitian ini bertujuan untuk menganalisis: 1) Sejauh mana pengaruh kesadaran merek terhadap keputusan pembelian handphone Samsung. 2) Sejauh mana pengaruh persepsi kualitas terhadap keputusan pembelian handphone Samsung. 3) Sejauh mana pengaruh asosiasi merek terhadap keputusan pembelian handphone Samsung. Hasil penelitian menunjukkan bahwa: 1) Kesadaran merek berpengaruh positif dan signifikan terhadap keputusan pembelian handphone Samsung. Dimana diperoleh nilai koefisien jalur sebesar 0,267 dan thitung sebesar 5,026 > ttabel sebesar 1,654 dengan nilai signifikan 0,000 < 0,05. 2) Persepsi kualitas berpengaruh positif dan signifikan terhadap keputusan pembelian handphone Samsung. Dimana diperoleh nilai koefisien jalur sebesar 0,345 dan thitung sebesar 7,690 > ttabel sebesar 1,654 dengan nilai signifikan 0,000 < 0,05.