Understanding Web Design Overview
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Origins of the Underline As Visual Representation of the Hyperlink on the Web: a Case Study in Skeuomorphism
The Origins of the Underline as Visual Representation of the Hyperlink on the Web: A Case Study in Skeuomorphism The Harvard community has made this article openly available. Please share how this access benefits you. Your story matters Citation Romano, John J. 2016. The Origins of the Underline as Visual Representation of the Hyperlink on the Web: A Case Study in Skeuomorphism. Master's thesis, Harvard Extension School. Citable link http://nrs.harvard.edu/urn-3:HUL.InstRepos:33797379 Terms of Use This article was downloaded from Harvard University’s DASH repository, and is made available under the terms and conditions applicable to Other Posted Material, as set forth at http:// nrs.harvard.edu/urn-3:HUL.InstRepos:dash.current.terms-of- use#LAA The Origins of the Underline as Visual Representation of the Hyperlink on the Web: A Case Study in Skeuomorphism John J Romano A Thesis in the Field of Visual Arts for the Degree of Master of Liberal Arts in Extension Studies Harvard University November 2016 Abstract This thesis investigates the process by which the underline came to be used as the default signifier of hyperlinks on the World Wide Web. Created in 1990 by Tim Berners- Lee, the web quickly became the most used hypertext system in the world, and most browsers default to indicating hyperlinks with an underline. To answer the question of why the underline was chosen over competing demarcation techniques, the thesis applies the methods of history of technology and sociology of technology. Before the invention of the web, the underline–also known as the vinculum–was used in many contexts in writing systems; collecting entities together to form a whole and ascribing additional meaning to the content. -

Cache Files Detect and Eliminate Privacy Threats
Award-Winning Privacy Software for OS X Every time you surf the web or use your computer, bits of Recover Disk Space data containing sensitive information are left behind that Over time, the files generated by web browsers can start could compromise your privacy. PrivacyScan provides to take up a large amount of space on your hard drive, protection by scanning for these threats and offers negatively impacting your computer’s performance. multiple removal options to securely erase them from PrivacyScan can locate and removes these space hogs, your system. freeing up valuable disk space and giving your system a speed boost in the process. PrivacyScan can seek and destroy internet files used for tracking your online whereabouts, including browsing history, cache files, cookies, search history, and more. Secure File Shredding Additionally, PrivacyScan can eliminate Flash Cookies, PrivacyScan utilizes advanced secure delete algorithms which are normally hidden away on your system. that meet and exceed US Department of Defense recommendations to ensure complete removal of Privacy Threat: Cookies sensitive data. Cookies can be used to track your usage of websites, determining which pages you visited and the length Intuitive Interface of time you spent on each page. Advertisers can use PrivacyScan’s award-winning design makes it easy to cookies to track you across multiple sites, building up track down privacy threats that exist on your system and a “profile” of who you are based on your web browsing quickly eliminate them. An integrated setup assistant and habits. tip system provide help every step of the way to make file cleaning a breeze. -

Previewserver-All Oses
USER DOCUMENTATION Preview Server – Voyager 8.0.0 CONFIDENTIAL INFORMATION The information herein is the property of Ex Libris Ltd. or its affiliates and any misuse or abuse will result in economic loss. DO NOT COPY UNLESS YOU HAVE BEEN GIVEN SPECIFIC WRITTEN AUTHORIZATION FROM EX LIBRIS LTD. This document is provided for limited and restricted purposes in accordance with a binding contract with Ex Libris Ltd. or an affiliate. The information herein includes trade secrets and is confidential. DISCLAIMER The information in this document will be subject to periodic change and updating. Please confirm that you have the most current documentation. There are no warranties of any kind, express or implied, provided in this documentation, other than those expressly agreed upon in the applicable Ex Libris contract. Any references in this document to non-Ex Libris Web sites are provided for convenience only and do not in any manner serve as an endorsement of those Web sites. The materials at those Web sites are not part of the materials for this Ex Libris product and Ex Libris has no liability for materials on those Web sites. Table of Contents 1 Introduction ...........................................................................................................................................................5 2 Preview Server Requirements .............................................................................................................................6 2.1 Browser Requirements ..................................................................................................................................6 -
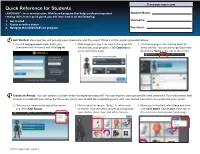
Quick Reference for Students LANGUAGE!® Live Is an Interactive, Web-Based Program That Helps You Learn Important Student Name: Reading Skills
ll.voyagersopris.com Quick Reference for Students LANGUAGE!® Live is an interactive, Web-based program that helps you learn important Student Name: reading skills. In this quick guide, you will learn how to do the following: 1. Get Started Username: 2. Create an online avatar 3. Navigate the LANGUAGE! Live program Password: Get Started. Your teacher will provide your Username and Password. Write it in the spaces provided above. 1. Go to ll.voyagersopris.com. Enter your 2. After logging in, you’ll see your training update 3. Your home page is the starting point for Username and Password, and click Log In! which tracks your progress. Click Continue to every activity. You can always get back here go to your home page. by clicking Home at the top of the screen. Create an Avatar. You can create a custom avatar to represent yourself. You can express your personality and creativity! Your classmates and teacher can identify you online by the avatar you have created. By completing each unit, you unlock new items to customize your avatar. 1. Click on your name at the top of the screen 2. Click on the first square, “Body,” to select male 3. When you’re finished, select Save and then and select Edit Avatar. or female. Click the other squares to personalize click Save Outfit. Click Home at the top of your clothes, shoes, hair, and other features. the screen to return to your home page. ©2015 Voyager Sopris Learning Quick Reference for Students Getting Started in LANGUAGE!® Live Navigate LANGUAGE! Live Your Home Page Lessons Sight Words Scorecard Click on Scorecard from the Class button at the top of the screen, and you can see When you click the blue button, or click When you click Play Sight Words (green your progress report. -

Apple Has Built a Solution Into Every Mac
Overview Mac OS X iPhone iPod + iTunes Resources Vision Mac OS X solutions VoiceOver from third parties. Browse the wide variety of To make it easier for the blind and those with low-vision to use a accessibility solutions supported computer, Apple has built a solution into every Mac. Called VoiceOver, by Mac OS X. Learn more it’s reliable, simple to learn, and enjoyable to use. In Depth Device Support Application Support Downloads VoiceOver Application Support VoiceOver. A unique solution for the vision-impaired. Every new Mac comes with Mac OS X and VoiceOver installed and includes a variety of accessible More than 50 reasons to use applications. You can also purchase additional Apple and third-party applications to use with VoiceOver. VoiceOver. Learn more While this page lists a few of the most popular applications, many more are available. If you use an application with VoiceOver that’s not on this list, and you would like to have it added, send email to [email protected]. Unlike traditional screen readers, VoiceOver is integrated into the operating system, so you can start using new accessible applications right away. You don’t need to buy an update to VoiceOver, install a new copy, or add the application to a “white list.” Moreover, VoiceOver commands work the same way in every application, so once you learn how to use them, you’ll be able to apply what you know to any accessible application. Apple provides developers with a Cocoa framework that contains common, reusable application components (such as menus, text fields, buttons, and sliders), so developers don’t have to re-create these elements each time they write a new application. -

Legislators of Cyberspace: an Analysis of the Role Of
SHAPING CODE Jay P. Kesan* & Rajiv C. Shah** I. INTRODUCTION ............................................................................................................................ 4 II. THE CASE STUDIES: THE DEVELOPMENT OF CODE WITHIN INSTITUTIONS.............................. 13 A. World Wide Web......................................................................................................... 14 1. Libwww............................................................................................................ 14 2. NCSA Mosaic .................................................................................................. 16 B. Cookies ........................................................................................................................ 21 1. Netscape’s Cookies .......................................................................................... 21 2. The IETF’s Standard for Cookies .................................................................... 24 C. Platform for Internet Content Selection....................................................................... 28 D. Apache......................................................................................................................... 34 III. LEGISLATIVE BODIES: SOCIETAL INSTITUTIONS THAT DEVELOP CODE ................................. 37 A. Universities.................................................................................................................. 38 B. Firms........................................................................................................................... -

T1, U-2 and L1 Transmitters™ Software V3.06 April 22, 2014
™ Air Integrated Dive Computer User Manual ™ Air Integrated Dive Computer Software v1.18 Ultrasonic software v1.11 And T1, U-2 and L1 Transmitters™ Software v3.06 April 22, 2014 Liquivision Products, Inc -1- Manual 1.6; Lynx 1.18; US 1.11; U-2 3.06 ™ Air Integrated Dive Computer User Manual CONTENTS IMPORTANT NOTICES ............................................................................................................................... 8 Definitions ..................................................................................................................................................... 9 User Agreement and Warranty ....................................................................................................................... 9 User Manual .................................................................................................................................................. 9 Liquivision Limitation of Liability ............................................................................................................... 10 Trademark Notice ........................................................................................................................................ 10 Patent Notice ............................................................................................................................................... 10 CE ............................................................................................................................................................... 10 LYNX -

Personalizing Voyager Using Browser Extensions
University of Kentucky UKnowledge Library Presentations University of Kentucky Libraries 5-8-2015 Personalizing Voyager Using Browser Extensions Kathryn Lybarger University of Kentucky, [email protected] Right click to open a feedback form in a new tab to let us know how this document benefits oy u. Follow this and additional works at: https://uknowledge.uky.edu/libraries_present Part of the Cataloging and Metadata Commons Repository Citation Lybarger, Kathryn, "Personalizing Voyager Using Browser Extensions" (2015). Library Presentations. 128. https://uknowledge.uky.edu/libraries_present/128 This Presentation is brought to you for free and open access by the University of Kentucky Libraries at UKnowledge. It has been accepted for inclusion in Library Presentations by an authorized administrator of UKnowledge. For more information, please contact [email protected]. Personalizing Voyager using Browser Extensions Kathryn Lybarger @zemkat ELUNA 2015 #eluna2015 May 8, 2015 Personalizing Voyager As an institution, we have a fair amount of power over how Voyager’s OPAC looks Colors and fonts Which fields are searchable What displays in search results What displays in full record view … (anything really) Must find a balance Provide good access to most of our patrons Don’t clutter the interface needlessly But how about… Personalizing for particular groups of patrons? Personalizing for staff needs? Doing so quickly? Even temporarily? Web browser extensions Custom search bars Extensions Bookmarklets User scripts Browser -

World-Wide Web Proxies
World-Wide Web Proxies Ari Luotonen, CERN Kevin Altis, Intel April 1994 Abstract 1.0 Introduction A WWW proxy server, proxy for short, provides access to The primary use of proxies is to allow access to the Web the Web for people on closed subnets who can only access from within a firewall (Fig. 1). A proxy is a special HTTP the Internet through a firewall machine. The hypertext [HTTP] server that typically runs on a firewall machine. server developed at CERN, cern_httpd, is capable of run- The proxy waits for a request from inside the firewall, for- ning as a proxy, providing seamless external access to wards the request to the remote server outside the firewall, HTTP, Gopher, WAIS and FTP. reads the response and then sends it back to the client. cern_httpd has had gateway features for a long time, but In the usual case, the same proxy is used by all the clients only this spring they were extended to support all the within a given subnet. This makes it possible for the proxy methods in the HTTP protocol used by WWW clients. Cli- to do efficient caching of documents that are requested by ents don’t lose any functionality by going through a proxy, a number of clients. except special processing they may have done for non- native Web protocols such as Gopher and FTP. The ability to cache documents also makes proxies attrac- tive to those not inside a firewall. Setting up a proxy server A brand new feature is caching performed by the proxy, is easy, and the most popular Web client programs already resulting in shorter response times after the first document have proxy support built in. -

Discontinued Browsers List
Discontinued Browsers List Look back into history at the fallen windows of yesteryear. Welcome to the dead pool. We include both officially discontinued, as well as those that have not updated. If you are interested in browsers that still work, try our big browser list. All links open in new windows. 1. Abaco (discontinued) http://lab-fgb.com/abaco 2. Acoo (last updated 2009) http://www.acoobrowser.com 3. Amaya (discontinued 2013) https://www.w3.org/Amaya 4. AOL Explorer (discontinued 2006) https://www.aol.com 5. AMosaic (discontinued in 2006) No website 6. Arachne (last updated 2013) http://www.glennmcc.org 7. Arena (discontinued in 1998) https://www.w3.org/Arena 8. Ariadna (discontinued in 1998) http://www.ariadna.ru 9. Arora (discontinued in 2011) https://github.com/Arora/arora 10. AWeb (last updated 2001) http://www.amitrix.com/aweb.html 11. Baidu (discontinued 2019) https://liulanqi.baidu.com 12. Beamrise (last updated 2014) http://www.sien.com 13. Beonex Communicator (discontinued in 2004) https://www.beonex.com 14. BlackHawk (last updated 2015) http://www.netgate.sk/blackhawk 15. Bolt (discontinued 2011) No website 16. Browse3d (last updated 2005) http://www.browse3d.com 17. Browzar (last updated 2013) http://www.browzar.com 18. Camino (discontinued in 2013) http://caminobrowser.org 19. Classilla (last updated 2014) https://www.floodgap.com/software/classilla 20. CometBird (discontinued 2015) http://www.cometbird.com 21. Conkeror (last updated 2016) http://conkeror.org 22. Crazy Browser (last updated 2013) No website 23. Deepnet Explorer (discontinued in 2006) http://www.deepnetexplorer.com 24. Enigma (last updated 2012) No website 25. -
![Web Technologies [R18a0517] Lecture Notes](https://docslib.b-cdn.net/cover/1694/web-technologies-r18a0517-lecture-notes-831694.webp)
Web Technologies [R18a0517] Lecture Notes
WEB TECHNOLOGIES [R18A0517] LECTURE NOTES B.TECH III YEAR – II SEM(R18) (2020-21) DEPARTMENT OF COMPUTER SCIENCE AND ENGINEERING MALLA REDDY COLLEGE OF ENGINEERING & TECHNOLOGY (Autonomous Institution – UGC, Govt. of India) Recognized under 2(f) and 12 (B) of UGC ACT 1956 (Affiliated to JNTUH, Hyderabad, Approved by AICTE - Accredited by NBA & NAAC – ‘A’ Grade - ISO 9001:2015 Certified) Maisammaguda, Dhulapally (Post Via. Hakimpet), Secunderabad – 500100, Telangana State, India III Year B. Tech. CSE –II Sem L T/P/D C 4 1/- / - 3 (R18A0517) WEB TECHNOLOGIES Objectives: Giving the students the insights of the Internet programming and how to design and implement complete applications over the web. It covers the notions of Web servers and Web Application Servers, Design Methodologies with concentration on Object-Oriented concepts, Client-Side Programming, Server-Side Programming, Active Server Pages, Database Connectivity to web applications, Adding Dynamic content to web applications, Programming Common Gateway Interfaces, Programming the User Interface for the web applications. UNIT I: Web Basics and Overview: Introduction to Internet, World Wide Web, Web Browsers, URL, MIME, HTTP, Web Programmers Tool box. HTML Common tags: List, Tables, images, forms, frames, Basics of CSS and types of CSS. Client-Side Programming (Java Script): Introduction to Java Script, declaring variables, functions, Event handlers (onclick, onsubmit, etc.,) and Form Validation. UNIT II: Server-Side Programming (PHP): Declaring Variables, Data types, Operators, Control structures, Functions, Reading data from web form controls like text buttons, radio buttons, list, etc., Handling File Uploads, Handling Sessions & Cookies. Introduction to XML: Document type definition, XML Schemas, Document Object model, Presenting XML , Introduction to XHTML, Using XML Processors: DOM and SAX. -

Tutorial URL Manager Pro Tutorial
Tutorial URL Manager Pro Tutorial Version 3.3 Summer 2004 WWW http://www.url-manager.com Email mailto:[email protected] Copyright © 2004 Alco Blom All Rights Reserved - 1 - Tutorial Installation Requirements URL Manager Pro 3.3 requires Mac OS X 10.2 or higher. On Mac OS X 10.1 you can use URL Manager Pro 3.1.1. URL Manager Pro 2.8 is still available for Mac OS 8 users. The bundle size of URL Manager Pro 3.3 is around 8 MB, including this user manual and localizations for English, Japanese, German, French, Spanish and Italian, which are all included in the default package. Installing Installation is very easy, just move URL Manager Pro into the Applications folder. To start using URL Manager Pro, simply double-click the application icon. Optional: You may want to install the Add Bookmark Contextual Menu Item plug-in. The Add Bookmark plug-in can be installed using the URLs tab of the Preferences Window of URL Manager Pro. The plug-in will then be copied to: ~/Library/Contextual Menu Items/ Where ~ is the customary Unix shorthand to indicate the user's home directory. For more information, go to the Add Bookmark Web page or the Contextual Menu Item section in the Special Features chapter. The Bookmark Menu Extra While URL Manager Pro is running, it automatically adds the Bookmark Menu Extra to the menu bar. With the Bookmark Menu Extra you have access to your bookmarks from within any application, including your web browser. The Bookmark Menu Extra is located in the right part of your menu bar (see below).