Tutorial URL Manager Pro Tutorial
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Origins of the Underline As Visual Representation of the Hyperlink on the Web: a Case Study in Skeuomorphism
The Origins of the Underline as Visual Representation of the Hyperlink on the Web: A Case Study in Skeuomorphism The Harvard community has made this article openly available. Please share how this access benefits you. Your story matters Citation Romano, John J. 2016. The Origins of the Underline as Visual Representation of the Hyperlink on the Web: A Case Study in Skeuomorphism. Master's thesis, Harvard Extension School. Citable link http://nrs.harvard.edu/urn-3:HUL.InstRepos:33797379 Terms of Use This article was downloaded from Harvard University’s DASH repository, and is made available under the terms and conditions applicable to Other Posted Material, as set forth at http:// nrs.harvard.edu/urn-3:HUL.InstRepos:dash.current.terms-of- use#LAA The Origins of the Underline as Visual Representation of the Hyperlink on the Web: A Case Study in Skeuomorphism John J Romano A Thesis in the Field of Visual Arts for the Degree of Master of Liberal Arts in Extension Studies Harvard University November 2016 Abstract This thesis investigates the process by which the underline came to be used as the default signifier of hyperlinks on the World Wide Web. Created in 1990 by Tim Berners- Lee, the web quickly became the most used hypertext system in the world, and most browsers default to indicating hyperlinks with an underline. To answer the question of why the underline was chosen over competing demarcation techniques, the thesis applies the methods of history of technology and sociology of technology. Before the invention of the web, the underline–also known as the vinculum–was used in many contexts in writing systems; collecting entities together to form a whole and ascribing additional meaning to the content. -

Cache Files Detect and Eliminate Privacy Threats
Award-Winning Privacy Software for OS X Every time you surf the web or use your computer, bits of Recover Disk Space data containing sensitive information are left behind that Over time, the files generated by web browsers can start could compromise your privacy. PrivacyScan provides to take up a large amount of space on your hard drive, protection by scanning for these threats and offers negatively impacting your computer’s performance. multiple removal options to securely erase them from PrivacyScan can locate and removes these space hogs, your system. freeing up valuable disk space and giving your system a speed boost in the process. PrivacyScan can seek and destroy internet files used for tracking your online whereabouts, including browsing history, cache files, cookies, search history, and more. Secure File Shredding Additionally, PrivacyScan can eliminate Flash Cookies, PrivacyScan utilizes advanced secure delete algorithms which are normally hidden away on your system. that meet and exceed US Department of Defense recommendations to ensure complete removal of Privacy Threat: Cookies sensitive data. Cookies can be used to track your usage of websites, determining which pages you visited and the length Intuitive Interface of time you spent on each page. Advertisers can use PrivacyScan’s award-winning design makes it easy to cookies to track you across multiple sites, building up track down privacy threats that exist on your system and a “profile” of who you are based on your web browsing quickly eliminate them. An integrated setup assistant and habits. tip system provide help every step of the way to make file cleaning a breeze. -

Podcast Presentation
3/18/2009 Today’s Goals Podcasts: Understanding, 1. What is a podcast? Creating, and Deploying them 2. How do I get podcasts? 3. How do I play podcasts? 4. Why should I care about podcasts for Dr. Rick Jerz ediducation? 5. How do I produce my own audio podcasts? [email protected] 6. How do I deliver (deploy) my own podcasts? www.rjerz.com 1 © 2009 rjerz.com 2 © 2009 rjerz.com Demos 1) What is a Podcast? • It must be nothing, since the “podcast” is not in my dictionary. • It is something only children do. • It has something to do with fishing. • It is a radio talk show. • It a music file. • It is a TV program. • It is a lecture. 3 © 2009 rjerz.com 4 © 2009 rjerz.com Podcast Definition1 Rick’s Podcast Definition • Podcasting is a new format for distributing A method of obtaining (subscribing) audio and video content via the Internet. Actually, podcasting is just multimedia computer files (episodes), usually content enclosed into an RSS file. audio (mp3) or video (m4v), from a • RSS means Really Simple Syndication. RSS is a catalog (RSS feed, XML) on the special format based on XML. In fact, RSS Internet (website), and having them feeds are XML files containing data according to the RSS specification, and usually located automatically delivered to your on a website. computer and then to your iPod (or • XML: an HTML‐like file for handling data. other multimedia player) • HTML: Hyper Text Markup Language 1 ‐ http://www.rss‐specification.com/sitemap.htm 5 © 2009 rjerz.com 6 © 2009 rjerz.com 1 3/18/2009 2) How do I get podcasts? iTunes: An Aggregator -

Kemble Z3 Ephemera Collection
http://oac.cdlib.org/findaid/ark:/13030/c818377r No online items Kemble Ephemera Collection Z3 Finding aid prepared by Jaime Henderson California Historical Society 678 Mission Street San Francisco, CA, 94105-4014 (415) 357-1848 [email protected] 2013 Kemble Ephemera Collection Z3 Kemble Z3 1 Title: Kemble Z3 Ephemera Collection Date (inclusive): 1802-2013 Date (bulk): 1900-1970 Collection Identifier: Kemble Z3 Extent: 185 boxes, 19 oversize boxes, 4 oversize folder (137 linear feet) Repository: California Historical Society 678 Mission Street San Francisco, CA 94105 415-357-1848 [email protected] URL: http://www.californiahistoricalsociety.org Location of Materials: Collection is stored onsite. Language of Materials: Collection materials are primarily in English. Abstract: The collection comprises a wide variety of ephemera pertaining to printing practice, culture, and history in the Western Hemisphere. Dating from 1802 to 2013, the collection includes ephemera created by or relating to booksellers, printers, lithographers, stationers, engravers, publishers, type designers, book designers, bookbinders, artists, illustrators, typographers, librarians, newspaper editors, and book collectors; bookselling and bookstores, including new, used, rare and antiquarian books; printing, printing presses, printing history, and printing equipment and supplies; lithography; type and type-founding; bookbinding; newspaper publishing; and graphic design. Types of ephemera include advertisements, announcements, annual reports, brochures, clippings, invitations, trade catalogs, newspapers, programs, promotional materials, prospectuses, broadsides, greeting cards, bookmarks, fliers, business cards, pamphlets, newsletters, price lists, bookplates, periodicals, posters, receipts, obituaries, direct mail advertising, book catalogs, and type specimens. Materials printed by members of Moxon Chappel, a San Francisco-area group of private press printers, are extensive. Access Collection is open for research. -

QUICK GUIDE How to Download a Digital Publication to View Offline from the BC Publications Subscription Library
QUICK GUIDE how to download a digital publication to view offline from the BC Publications subscription library INTERNET EXPLORER, P2 FIREFOX, P4 GOOGLE CHROME, P6 INTERNET EXPLORER STEP 1 Begin with opening the publication from the “My Publications” page. Now select the “Save to browser” button in the top right corner Once completed the following message will appear. Select the “Close” button Quick Guide 2 To find out how to display the “favorites bar” go to Page 8 STEP 2: ADD TO FAVORITES Bookmark the URL by selecting the “Add to Favorites” option. The “Add to Favorite” dialogue box will From the top Menu select the “Favorites”, then from the drop down appear and users may change the favorite name within the Name field at this time. select the “Add to Favorites” option or select the Favorites icon. Next select the “Add” button. The “Add to Favorite” dialogue Anytime the workstation is offline (not connected to the internet) this link within the Favorites will provide the user access to the bookmarked offline copy. To access this link launch Internet Explorer, Open list of Favorites and select the title as originally saved. Quick Guide 3 STEP 1 FIREFOX Now select the “Save to browser” Begin with opening the publication from the “My Publications” page button in the top right corner The browser will begin saving and the following box will appear. Once completed the following message will appear. Select the “Close” button Quick Guide 4 To find out how to display the “favorites bar” go to Page 9 STEP 2: BOOKMARK THE URL Bookmark the URL by selecting the “Bookmark this page” button. -

View Managing Devices and Corporate Data On
Overview Managing Devices & Corporate Data on iOS Overview Overview Contents Businesses everywhere are empowering their employees with iPhone and iPad. Overview Management Basics The key to a successful mobile strategy is balancing IT control with user Separating Work and enablement. By personalizing iOS devices with their own apps and content, Personal Data users take greater ownership and responsibility, leading to higher levels of Flexible Management Options engagement and increased productivity. This is enabled by Apple’s management Summary framework, which provides smart ways to manage corporate data and apps discretely, seamlessly separating work data from personal data. Additionally, users understand how their devices are being managed and trust that their privacy is protected. This document offers guidance on how essential IT control can be achieved while at the same time keeping users enabled with the best tools for their job. It complements the iOS Deployment Reference, a comprehensive online technical reference for deploying and managing iOS devices in your enterprise. To refer to the iOS Deployment Reference, visit help.apple.com/deployment/ios. Managing Devices and Corporate Data on iOS July 2018 2 Management Basics Management Basics With iOS, you can streamline iPhone and iPad deployments using a range of built-in techniques that allow you to simplify account setup, configure policies, distribute apps, and apply device restrictions remotely. Our simple framework With Apple’s unified management framework in iOS, macOS, tvOS, IT can configure and update settings, deploy applications, monitor compliance, query devices, and remotely wipe or lock devices. The framework supports both corporate-owned and user-owned as well as personally-owned devices. -

Apple Has Built a Solution Into Every Mac
Overview Mac OS X iPhone iPod + iTunes Resources Vision Mac OS X solutions VoiceOver from third parties. Browse the wide variety of To make it easier for the blind and those with low-vision to use a accessibility solutions supported computer, Apple has built a solution into every Mac. Called VoiceOver, by Mac OS X. Learn more it’s reliable, simple to learn, and enjoyable to use. In Depth Device Support Application Support Downloads VoiceOver Application Support VoiceOver. A unique solution for the vision-impaired. Every new Mac comes with Mac OS X and VoiceOver installed and includes a variety of accessible More than 50 reasons to use applications. You can also purchase additional Apple and third-party applications to use with VoiceOver. VoiceOver. Learn more While this page lists a few of the most popular applications, many more are available. If you use an application with VoiceOver that’s not on this list, and you would like to have it added, send email to [email protected]. Unlike traditional screen readers, VoiceOver is integrated into the operating system, so you can start using new accessible applications right away. You don’t need to buy an update to VoiceOver, install a new copy, or add the application to a “white list.” Moreover, VoiceOver commands work the same way in every application, so once you learn how to use them, you’ll be able to apply what you know to any accessible application. Apple provides developers with a Cocoa framework that contains common, reusable application components (such as menus, text fields, buttons, and sliders), so developers don’t have to re-create these elements each time they write a new application. -

HTTP Cookie - Wikipedia, the Free Encyclopedia 14/05/2014
HTTP cookie - Wikipedia, the free encyclopedia 14/05/2014 Create account Log in Article Talk Read Edit View history Search HTTP cookie From Wikipedia, the free encyclopedia Navigation A cookie, also known as an HTTP cookie, web cookie, or browser HTTP Main page cookie, is a small piece of data sent from a website and stored in a Persistence · Compression · HTTPS · Contents user's web browser while the user is browsing that website. Every time Request methods Featured content the user loads the website, the browser sends the cookie back to the OPTIONS · GET · HEAD · POST · PUT · Current events server to notify the website of the user's previous activity.[1] Cookies DELETE · TRACE · CONNECT · PATCH · Random article Donate to Wikipedia were designed to be a reliable mechanism for websites to remember Header fields Wikimedia Shop stateful information (such as items in a shopping cart) or to record the Cookie · ETag · Location · HTTP referer · DNT user's browsing activity (including clicking particular buttons, logging in, · X-Forwarded-For · Interaction or recording which pages were visited by the user as far back as months Status codes or years ago). 301 Moved Permanently · 302 Found · Help 303 See Other · 403 Forbidden · About Wikipedia Although cookies cannot carry viruses, and cannot install malware on 404 Not Found · [2] Community portal the host computer, tracking cookies and especially third-party v · t · e · Recent changes tracking cookies are commonly used as ways to compile long-term Contact page records of individuals' browsing histories—a potential privacy concern that prompted European[3] and U.S. -

Legal-Process Guidelines for Law Enforcement
Legal Process Guidelines Government & Law Enforcement within the United States These guidelines are provided for use by government and law enforcement agencies within the United States when seeking information from Apple Inc. (“Apple”) about customers of Apple’s devices, products and services. Apple will update these Guidelines as necessary. All other requests for information regarding Apple customers, including customer questions about information disclosure, should be directed to https://www.apple.com/privacy/contact/. These Guidelines do not apply to requests made by government and law enforcement agencies outside the United States to Apple’s relevant local entities. For government and law enforcement information requests, Apple complies with the laws pertaining to global entities that control our data and we provide details as legally required. For all requests from government and law enforcement agencies within the United States for content, with the exception of emergency circumstances (defined in the Electronic Communications Privacy Act 1986, as amended), Apple will only provide content in response to a search issued upon a showing of probable cause, or customer consent. All requests from government and law enforcement agencies outside of the United States for content, with the exception of emergency circumstances (defined below in Emergency Requests), must comply with applicable laws, including the United States Electronic Communications Privacy Act (ECPA). A request under a Mutual Legal Assistance Treaty or the Clarifying Lawful Overseas Use of Data Act (“CLOUD Act”) is in compliance with ECPA. Apple will provide customer content, as it exists in the customer’s account, only in response to such legally valid process. -

Chapter 1. Origins of Mac OS X
1 Chapter 1. Origins of Mac OS X "Most ideas come from previous ideas." Alan Curtis Kay The Mac OS X operating system represents a rather successful coming together of paradigms, ideologies, and technologies that have often resisted each other in the past. A good example is the cordial relationship that exists between the command-line and graphical interfaces in Mac OS X. The system is a result of the trials and tribulations of Apple and NeXT, as well as their user and developer communities. Mac OS X exemplifies how a capable system can result from the direct or indirect efforts of corporations, academic and research communities, the Open Source and Free Software movements, and, of course, individuals. Apple has been around since 1976, and many accounts of its history have been told. If the story of Apple as a company is fascinating, so is the technical history of Apple's operating systems. In this chapter,[1] we will trace the history of Mac OS X, discussing several technologies whose confluence eventually led to the modern-day Apple operating system. [1] This book's accompanying web site (www.osxbook.com) provides a more detailed technical history of all of Apple's operating systems. 1 2 2 1 1.1. Apple's Quest for the[2] Operating System [2] Whereas the word "the" is used here to designate prominence and desirability, it is an interesting coincidence that "THE" was the name of a multiprogramming system described by Edsger W. Dijkstra in a 1968 paper. It was March 1988. The Macintosh had been around for four years. -

Tips and Tricks for OS X Lion 10.7 Introduction
Mac Information Tips and Tricks for OS X Lion 10.7 Introduction: Lion was introduced in the middle of 2011 and came with lots of changes such as Mission Control and Launchpad. However here are a list of smaller changes, ones which you may never have noticed... 1/ Put your contact info on the login screen Lion now allows you to place a personal message with your contact information on the login screen which may be useful if your laptop is lost or stolen. To enable the feature, go to your Security & Privacy in System Preferences, click on the General tab and click on the padlock in the lower left corner to unlock your settings. Then tick the box labeled "Show a message when the screen is locked”. Click on the “Set Lock Message...” button and type in the message which you would like to appear on your login screen. 2/ Always Display Scroll Bars Under Lion, scroll bars on the side have been reduced in importance. In the past, users dragged the scroll bar or used the arrows under the scroll bar. to navigate a document or window. With the advent of trackpads these scroll bars are now just an indication of your position on a page. Under Lion the scroll bars fade out after a few seconds unless you change a setting. In System Preferences, click on the General section, and then choose the “Always” option. 3/ Turn Off Restore Windows Lion also brought in a “restore windows” feature which means that windows which are open when you quit an app re-open the next time you choose that app. -
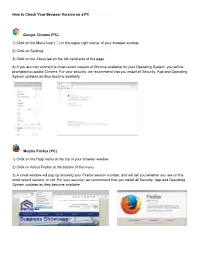
How to Check Your Browser Version on a PC
How to Check Your Browser Version on a PC Google Chrome (PC) 1) Click on the Menu Icon ( ) in the upper right corner of your browser window. 2) Click on Settings 3) Click on the About tab on the left-hand side of the page. 4) If you are not running the most recent version of Chrome available for your Operating System, you will be prompted to update Chrome. For your security, we recommend that you install all Security, App and Operating System updates as they become available. Mozilla Firefox (PC) 1) Click on the Help menu at the top of your browser window. 2) Click on About Firefox at the bottom of the menu. 3) A small window will pop up showing your Firefox version number, and will tell you whether you are on the most recent version, or not. For your security, we recommend that you install all Security, App and Operating System updates as they become available. Internet Explorer (PC) 1) Click on the Gear Icon at the top of your browser window. 2) Click on the About Internet Explorer option. 3) A window will pop up showing you your Internet Explorer version. 4) If you are using Internet Explorer 9 or 10, you will need to make sure that you have TLS 1.2 enabled by: A) Clicking on the Gear Icon again. B) Click on Internet Options. C) Click on the Advanced Tab and scroll down to the option titled “Use TLS 1.2”. (This should be found at the bottome of the list of options.) The box next to this should be checked.