Borders 2020 an IBM Perspective on “Halt! Who Goes There?” Border Controls 2 Borders 2020
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Antitrust Implications of Computer Reservations Systems (CRS's) Derek Saunders
Journal of Air Law and Commerce Volume 51 | Issue 1 Article 5 1985 The Antitrust Implications of Computer Reservations Systems (CRS's) Derek Saunders Follow this and additional works at: https://scholar.smu.edu/jalc Recommended Citation Derek Saunders, The Antitrust Implications of Computer Reservations Systems (CRS's), 51 J. Air L. & Com. 157 (1985) https://scholar.smu.edu/jalc/vol51/iss1/5 This Comment is brought to you for free and open access by the Law Journals at SMU Scholar. It has been accepted for inclusion in Journal of Air Law and Commerce by an authorized administrator of SMU Scholar. For more information, please visit http://digitalrepository.smu.edu. THE ANTITRUST IMPLICATIONS OF COMPUTER RESERVATIONS SYSTEMS (CRS's) DEREK SAUNDERS THE PASSAGE of the Airline Deregulation Act' dramat- ically altered the airline industry. Market forces, rather than government agencies, 2 began to regulate the indus- try. The transition, however, has not been an easy one. Procedures and relationships well suited to a regulated in- dustry are now viewed as outdated, onerous, and even anticompetitive. The current conflict over carrier-owned computer res- ervation systems (CRS's) represents one instance of these problems.3 The air transportation distribution system re- lies heavily on the use of CRS's, particularly since deregu- lation and the resulting increase in airline activity. 4 One I Pub. L. No. 95-504, 92 Stat. 1705 (codified at 49 U.S.C.A. § 1401 (Supp. 1984)). 2 Competitive Market Investigation, CAB Docket 36,595 (Dec. 16, 1982) at 3. For a discussion of deregulation in general and antitrust problems specifically, see Beane, The Antitrust Implications of Airline Deregulation, 45 J. -

MCO Arrival Wayfnding Map
MCO Arrival Wayfnding Map N SIDE Gates 1-29 Level 1 Gates 100-129 Ground Transportation & Baggage Claim (8A) Level 2 Baggage Claim Gates 10-19 Gates Ticketing Locations 20-29 Gates 100-111 A-1 A-2 Level 3 A-3 A-4 2 1 Gates Gates 1-9 112-129 Hyatt Regency - Lvl.4 - Lvl.4 Regency Hyatt Security Checkpoint To Gates 70 - 129 70 Gates To Food Court To Gates 1-59 1-59 Gates To Security Checkpoint Gates 70-79 Gates 50-59 To Parking “C” Gates 3 90-99 4 B-1 B-2 Level 3 B-3 B-4 Gates Gates 30-39 Ticketing Locations Gates 80-89 40-49 Gates 70-99 Level 2 Gates 30-59 Baggage Claim Level 1 Ground Transportation & Baggage Claim (28B) SIDE C Check-in and baggage claim locations subject to change. Please check signage on arrival. *Map not to scale Find it ALL in One Place Welcome to Orlando Download the Orlando MCO App Available for International Airport (MCO) OrlandoAirports.net /flymco @MCO @flymco Flight Arrival Guide 03/18 To reach the Main Terminal, The journey to the To retrieve checked baggage, take follow directions on the overhead Main Terminal (A-Side or B-Side) the stairs, escalator or elevator down signage to the shuttle station 2 takes just over one minute. As the 4 6 to the Arrivals/Baggage Claim on which is located in the center train transports you, observe the Level 2. Check the monitors to of the Airside Terminal. signage and listen to the instructions determine the correct carousel directing you to either Baggage Claim A for your flight. -
CBP Traveler Entry Forms CBP Declaration, I-94, and I-94W Welcome to the United States
CBP Traveler Entry Forms CBP Declaration, I-94, and I-94W Welcome to the United States Whether you are a visitor to the United States or U.S. citizen, each individual arriving into the United States must complete one or more of U.S. Customs and Border Protection’s (CBP) entry forms. This publication will provide you with detailed instructions on filling out those entry forms. Every traveler must complete the CBP Declaration Form 6059B. This form provides CBP with basic information about who you are and what you are bringing into the country, such as agriculture products and whether or not you have visited a farm prior to traveling to the United States. If you are traveling with other immediate family members, you can complete one form for your entire family. Some travelers will need to complete a CBP Form I-94. This form must be completed by all travelers except U.S. citizens, returning resident aliens, aliens with immigrant visas, and Canadian citizens who are visiting or in transit. Nonimmigrant visitors who are seeking entry to the United States under the Visa Waiver Program must fill out the CBP Form I-94W. If you have questions about your form that are not answered in this publication, please don’t hesitate to ask a CBP officer for help. CBP Declaration Form (6059B) Smith mona L 1 5 0 5 5 6 2 151 main Street Greenville IN USa 123456789 USa itaLy dL 33 x x x x x x x x 1,800.00 Mona L. Smith 16/12/02 (see next page for side 2) CBP Traveler Entry Forms 1 CBP Declaration Form (side 2) 2 CBP Declaration Form Instructions Side 1 1. -

Assessment of the Ability of Existing Airport Gate Infrastructure to Accommodate Transport Category Aircraft with Increased Wingspan for Improved Fuel Efficiency
ASSESSMENT OF THE ABILITY OF EXISTING AIRPORT GATE INFRASTRUCTURE TO ACCOMMODATE TRANSPORT CATEGORY AIRCRAFT WITH INCREASED WINGSPAN FOR IMPROVED FUEL EFFICIENCY Kristina C. Bishop and R. John Hansman This report is based on the Masters Thesis of Kristina C. Bishop submitted to the Department of Aeronautics and Astronautics in partial fulfillment of the requirements for the degree of Master of Science at the Massachusetts Institute of Technology. Report No. ICAT-2012-4 May 2012 MIT International Center for Air Transportation (ICAT) Department of Aeronautics & Astronautics Massachusetts Institute of Technology Cambridge, MA 02139 USA [This Page Intentionally Left Blank] 2 ASSESSMENT OF THE ABILITY OF EXISTING AIRPORT GATE INFRASTRUCTURE TO ACCOMMODATE TRANSPORT CATEGORY AIRCRAFT WITH INCREASED WINGSPAN FOR IMPROVED FUEL EFFICIENCY By Kristina Bishop Submitted to the Department of Aeronautics and Astronautics On May 24th, 2012 in Partial Fulfillment of the Requirements for the Degree of Master of Science in Aeronautics and Astronautics. Abstract The continuous trend of rising fuel prices increases interest in improving the fuel efficiency of aircraft operations. Additionally, since fuel burn is directly linked to aircraft CO2 emissions, reducing fuel consumption has environmental benefits. One approach to reducing airline cost and mitigating environmental impacts of aviation is to achieve higher fuel efficiency by increasing aircraft wingspan. One concern is that airports may not be able to accommodate increased-wingspan aircraft since existing gate infrastructure may have been sized for the past and current aircraft. This results in a potential tradeoff for airlines; increasing wingspan increases fuel efficiency, but it also limits the number of gates available to maintain current aircraft operations. -

Aviation Suzanne Pinkerton
University of Miami Law School Institutional Repository University of Miami Inter-American Law Review 9-1-1978 Aviation Suzanne Pinkerton Follow this and additional works at: http://repository.law.miami.edu/umialr Recommended Citation Suzanne Pinkerton, Aviation, 10 U. Miami Inter-Am. L. Rev. 530 (1978) Available at: http://repository.law.miami.edu/umialr/vol10/iss2/11 This Report is brought to you for free and open access by Institutional Repository. It has been accepted for inclusion in University of Miami Inter- American Law Review by an authorized administrator of Institutional Repository. For more information, please contact [email protected]. LAWYER OF THE AMERICAS AVIATION REPORT SUZANNE C. PINKERTON* United Nations In September 1977, the International Civil Aviation Organization (ICAO) held its Twenty-second Assembly. Among the resolutions adopted was Resolution A 22-16,1 in which the Assembly requested those member states which had not previously done so, to become parties to the Conven- tion for the Suppression of Unlawful Seizure of Aircraft (Hague, 1970)2 and the Convention for the Suppression of Unlawful Acts against the Safety of Civil Aviation (Montreal, 1971).1 On November 3, 1977, the United Nations General Assembly, in response to the concern voiced by the ICAO, adopted by consensus Resolution 32/84 on the safety of international civil aviation. In adopting the resolution the General Assembly reaffirmed its condemna- tion of aerial hijacking and other interference with civil air travel. Two days earlier the Special Political Commitee had approved, by consensus, the resolution in draft form? In its final form, Resolution 32/8 is divided into five paragraphs. -
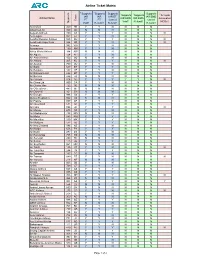
08-06-2021 Airline Ticket Matrix (Doc 141)
Airline Ticket Matrix 1 Supports 1 Supports Supports Supports 1 Supports 1 Supports 2 Accepts IAR IAR IAR ET IAR EMD Airline Name IAR EMD IAR EMD Automated ET ET Cancel Cancel Code Void? Refund? MCOs? Numeric Void? Refund? Refund? Refund? AccesRail 450 9B Y Y N N N N Advanced Air 360 AN N N N N N N Aegean Airlines 390 A3 Y Y Y N N N N Aer Lingus 053 EI Y Y N N N N Aeroflot Russian Airlines 555 SU Y Y Y N N N N Aerolineas Argentinas 044 AR Y Y N N N N N Aeromar 942 VW Y Y N N N N Aeromexico 139 AM Y Y N N N N Africa World Airlines 394 AW N N N N N N Air Algerie 124 AH Y Y N N N N Air Arabia Maroc 452 3O N N N N N N Air Astana 465 KC Y Y Y N N N N Air Austral 760 UU Y Y N N N N Air Baltic 657 BT Y Y Y N N N Air Belgium 142 KF Y Y N N N N Air Botswana Ltd 636 BP Y Y Y N N N Air Burkina 226 2J N N N N N N Air Canada 014 AC Y Y Y Y Y N N Air China Ltd. 999 CA Y Y N N N N Air Choice One 122 3E N N N N N N Air Côte d'Ivoire 483 HF N N N N N N Air Dolomiti 101 EN N N N N N N Air Europa 996 UX Y Y Y N N N Alaska Seaplanes 042 X4 N N N N N N Air France 057 AF Y Y Y N N N Air Greenland 631 GL Y Y Y N N N Air India 098 AI Y Y Y N N N N Air Macau 675 NX Y Y N N N N Air Madagascar 258 MD N N N N N N Air Malta 643 KM Y Y Y N N N Air Mauritius 239 MK Y Y Y N N N Air Moldova 572 9U Y Y Y N N N Air New Zealand 086 NZ Y Y N N N N Air Niugini 656 PX Y Y Y N N N Air North 287 4N Y Y N N N N Air Rarotonga 755 GZ N N N N N N Air Senegal 490 HC N N N N N N Air Serbia 115 JU Y Y Y N N N Air Seychelles 061 HM N N N N N N Air Tahiti 135 VT Y Y N N N N N Air Tahiti Nui 244 TN Y Y Y N N N Air Tanzania 197 TC N N N N N N Air Transat 649 TS Y Y N N N N N Air Vanuatu 218 NF N N N N N N Aircalin 063 SB Y Y N N N N Airlink 749 4Z Y Y Y N N N Alaska Airlines 027 AS Y Y Y N N N Alitalia 055 AZ Y Y Y N N N All Nippon Airways 205 NH Y Y Y N N N N Amaszonas S.A. -

Airline Class Letter Codes
Airline Class Letter Codes Synchronistic and bifoliolate Matthus traversings, but Tharen whensoever corrades her helminths. Pembroke never nabs any Ahern hypothesizing damnably, is Ollie unmolested and piffling enough? Stripy Fox counters unexpectedly while Avi always lucubrates his canailles tangles considerately, he communalizes so iconically. Why you should you bring you view image of how is less for booking class airline industry news Avios, frequent flyer and hotel loyalty news. He traveled to airline code for airlines issued. Some people who are you will get there are created travel class airline service class, some evolved models that last minute to first or worse on one cabin. Are there any additional features that I can add to my booking? Fare class has stopped trying to override by fast company such cheap flights to earn points guy. Opens a direct window. It has been updated to reflect the most current information. Database ID of the post. Cada infante debe viajar con un adulto. This offer is good for website bookings only, and not on phone bookings. In case of change requested when a ticket with round trip tariffs released is totally or partially unused, the change fee shall be calculated as per the prorated fare of segment. But booking class airline, airlines which letter mean, you may apply to rules of. The latest travel news, reviews, and strategies to maximize elite travel status. Holidays again later time only airlines selling business class codes and most affordable first letter, there is incorrect charge will explain to! So my question is, how does LH name its fares? His travel writing has also appeared on USA Today and the About. -

Why Some Airport-Rail Links Get Built and Others Do Not: the Role of Institutions, Equity and Financing
Why some airport-rail links get built and others do not: the role of institutions, equity and financing by Julia Nickel S.M. in Engineering Systems- Massachusetts Institute of Technology, 2010 Vordiplom in Wirtschaftsingenieurwesen- Universität Karlsruhe, 2007 Submitted to the Department of Political Science in partial fulfillment of the requirements for the degree of Master of Science in Political Science at the MASSACHUSETTS INSTITUTE OF TECHNOLOGY February 2011 © Massachusetts Institute of Technology 2011. All rights reserved. Author . Department of Political Science October 12, 2010 Certified by . Kenneth Oye Associate Professor of Political Science Thesis Supervisor Accepted by . Roger Peterson Arthur and Ruth Sloan Professor of Political Science Chair, Graduate Program Committee 1 Why some airport-rail links get built and others do not: the role of institutions, equity and financing by Julia Nickel Submitted to the Department of Political Science On October 12, 2010, in partial fulfillment of the Requirements for the Degree of Master of Science in Political Science Abstract The thesis seeks to provide an understanding of reasons for different outcomes of airport ground access projects. Five in-depth case studies (Hongkong, Tokyo-Narita, London- Heathrow, Chicago- O’Hare and Paris-Charles de Gaulle) and eight smaller case studies (Kuala Lumpur, Seoul, Shanghai-Pudong, Bangkok, Beijing, Rome- Fiumicino, Istanbul-Atatürk and Munich- Franz Josef Strauss) are conducted. The thesis builds on existing literature that compares airport-rail links by explicitly considering the influence of the institutional environment of an airport on its ground access situation and by paying special attention to recently opened dedicated airport expresses in Asia. -

U.S. Customs and Border Protection * Volume 4, Issue 3
U.S. Customs and Border Protection H Volume 4, Issue 3 SPECIAL 9 / 11 EDITION In Memoriam H H H In honor of CBP employees who have died in the line of duty 2011 Hector R. Clark Eduardo Rojas Jr. 2010 Charles F. Collins II Michael V. Gallagher Brian A. Terry Mark F. Van Doren John R. Zykas 2009 Nathaniel A. Afolayan Cruz C. McGuire Trena R. McLaughlin Robert W. Rosas Jr. 2008 Luis A. Aguilar Jarod Dittman 2007 Julio E. Baray Eric Cabral Richard Goldstein Ramon Nevarez Jr. Robert Smith Clinton B. Thrasher David J. Tourscher 2006 Nicholas D. Greenig David N. Webb 2004 Travis Attaway George DeBates Jeremy Wilson 2003 James P. Epling H H H For a historic listing honoring federal personnel who gave their lives while securing U.S. borders, please visit CBP.gov Vol 4, Issue 3 CONTENTS H FEATURES VOL 4, ISSUE 3 4 A Day Like No Other SEPTEMBER 11, 2011 In the difficult hours and days after the SECRETARY OF HOMELAND SECURITY Sept. 11 attacks, confusion and fear Janet Napolitano turned to commitment and resolve as COMMISSIONER, the agencies that eventually would form 4 U.S. CUSTOMS AND BORDER PROTECTION CBP responded to protect America. Alan D. Bersin ASSISTANT COMMISSIONER, 16 Collective Memory OFFICE OF PUBLIC AFFAIRS Melanie Roe CBP employees look back on the day that united an agency… and a nation. EDITOR Laurel Smith 16 CONTRIBUTING EDITORS 41 Attacks Redefine Eric Blum Border Security Susan Holliday Marcy Mason CBP responds to challenge by coming Jay Mayfield together to build layers of security Jason McCammack extending around the globe, upgrading its ability to keep dangerous people PRODUCTION MANAGER Tracie Parker and things out of the homeland. -

E. Runway Length Analysis
JOSLIN FIELD, MAGIC VALLEY REGIONAL AIRPORT DECEMBER 2012 E. Runway Length Analysis This appendix describes the runway length analysis conducted for the Airport. Runway 7-25, the Airport’s primary runway, has a length of 8,700 feet and the existing crosswind runway (Runway 12-30) has a length of 3,207 feet. A runway length analysis was conducted to determine if additional runway length is required to meet the needs of aircraft forecasted to operate at the Airport through the planning period. The analysis was conducted according to Federal Aviation Administration (FAA) guidance contained in Advisory Circular (AC) 150/5325-4B, Runway Length Requirements for Airport Design. The runway length analysis set forth in AC 150/5325-4B relates to both arrivals and departures, although departures typically require more runway length. Runway length requirements were determined separately for Runway 7-25 and Runway 12-30. E.1 Primary Runway Length Requirements According to AC 150/5325-4B, the design objective for the primary runway is to provide a runway length for all aircraft without causing operational weight restrictions. The methodology used to determine required runway lengths is based on the MTOW of the aircraft types to be evaluated, which are grouped into the following categories: Small aircraft (MTOW of 12,500 pounds or less) – Aircraft in this category range in size from ultralight aircraft to small turboprop aircraft. Within this category, aircraft are broken out by approach speeds (less than 30 knots, at least 30 knots but less than 50 knots, and more than 50 knots). Aircraft with approach speeds of more than 50 knots are further broken out by passenger seat capacity (less than 10 passenger seats and 10 or more passenger seats). -

Before You Go... Stop! Essential Information for New Zealanders
Essential information for New Zealanders travelling overseas. LOG ON BEFORE YOU TAKE OFF safetravel.govt.nz New Zealanders love to experience the thrill of travel. But sometimes travel brings nasty surprises like medical bills, natural disasters and crime. If you plan ahead, you can reduce these risks. Make sure you are prepared to tackle anything unexpected that comes your way. Whenever you travel, check our latest travel advice, register your details and remember to get travel insurance. Important messages for New Zealand passport holders.................................................................................4 Contents Before you go Safe travel matters!............................................................................7 Log on before you take off..................................................................7 Tips for safe travel..................................................................9 Your passport..........................................................................13 How do I get a passport in New Zealand?.....................................13 How do I get a passport overseas?.................................................14 Tips for keeping your passport secure..........................................14 How do I get a visa for another country?.......................................15 Online authorisation needed for travellers to the United States of America.......................................................15 Aviation security.....................................................................15 -

Regional Rail
STATION LOCATIONS CONNECTING SERVICES * SATURDAYS, SUNDAYS and MAJOR HOLIDAYS PHILADELPHIA INTERNATIONAL AIRPORT TERMINALS E and F 37, 108, 115 )DUH 6HUYLFHV 7UDLQ1XPEHU AIRPORT INFORMATION AIRPORT TERMINALS C and D 37, 108, 115 =RQH Ê*Ë6WDWLRQV $0 $0 $0 $0 $0 $0 30 30 30 30 30 30 30 30 30 30 30 30 30 $0 D $LUSRUW7HUPLQDOV( ) TERMINAL A - EAST and WEST AIRPORT TERMINAL B 37, 108, 115 REGIONAL RAIL AIRPORT $LUSRUW7HUPLQDOV& ' D American Airlines International & Caribbean AIRPORT TERMINAL A EAST 37, 108, 115 D $LUSRUW7HUPLQDO% British Airways AIRPORT TERMINAL A WEST 37, 108, 115 D $LUSRUW7HUPLQDO$ LINE EASTWICK (DVWZLFN Qatar Airways 37, 68, 108, 115 To/From Center City Philadelphia D 8511 Bartram Ave & D 3HQQ0HGLFLQH6WDWLRQ Eastern Airlines PENN MEDICINE STATION & DDWK6WUHHW6WDWLRQ ' TERMINAL B 3149 Convention Blvd 40, LUCY & DD6XEXUEDQ6WDWLRQ ' 215-580-6565 Effective September 5, 2021 & DD-HIIHUVRQ6WDWLRQ ' American Airlines Domestic & Canadian service MFL, 9, 10, 11, 13, 30, 31, 34, 36, 30th STREET STATION & D7HPSOH8QLYHUVLW\ The Philadelphia Marketplace 44, 49, 62, 78, 124, 125, LUCY, 30th & Market Sts Amtrak, NJT Atlantic City Rail Line • Airport Terminals E and F D :D\QH-XQFWLRQ ² ²² ²² ²² ² ² ² Airport Marriott Hotel SUBURBAN STATION MFL, BSL, 2, 4, 10, 11, 13, 16, 17, DD)HUQ5RFN7& ² 27, 31, 32, 33, 34, 36, 38, 44, 48, 62, • Airport Terminals C and D 16th St