Modelling Coastal Vulnerability
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The AP Mineral Development Corporation Limited
The A.P. Mineral Development Corporation Limited (A State Government Undertaking) E-TENDER FOR Working of Ball Clay mining lease over an extent of 34.41 Acres in Dwarakatirumala (V) & (M) near Bhimadole, West Godavari Dist. A.P. on Raising-Cum-Sale Contract basis The A.P. Mineral Development Corporation Limited (A State Government Undertaking) 294/ 1D, Tadigadapa to Enikepadu 100 ft. Road, Kanuru Village, Penamaluru Mandal , Vijayawada - 521137, Andhra Pradesh Tel: +91 866 2429999, Fax: +91 866 2429977 Nodal Officer Sri T. Nathaniel, Deputy General Manager (Geology) Contact: +91-866-2429999 Email id: [email protected] Tender No.: APMDC/ GEO-6/BC-RCSC/DTM Dated: 01st April, 2020 Tender Document Fee: INR 10,000/- + 18% GST (Non-Refundable) (Indian Ten thousand only + 18% GST) Note: The Tender Document Fee is non-refundable and non-transferable. All tender related payments to be made online only. DD’s are not accepted. Hard copy submission of documents not required 1 Notice Inviting Tender The A.P. Mineral Development Corporation Limited 294/ 1D, Tadigadapa to Enikepadu 100 ft. Road, Kanuru Village, Penamaluru Mandal , Vijayawada - 521137, Andhra Pradesh Tel: +91 866 2429999, Fax: +91 866 2429977 E-Mail: [email protected] E- Tender for Working of Ball Clay mining lease over an extent of 34.41 Acres in Dwarakatirumala (V) & (M) near Bhimadole, West Godavari Dist. A.P. on Raising-Cum- Sale Contract basis Tender No: APMDC/ GEO-6/BC-RCSC/DTM dated 01.04.2020 APMDC, a fully owned undertaking of the Govt. of Andhra Pradesh, invites tenders from reputed Agencies/Contractors for Working of Ball Clay mining lease over an extent of 34.41 Acres in Dwarakatirumala (V) & (M) near Bhimadole, West Godavari Dist. -

East Godavari and West Godavari Districts Andhra Pradesh
कᴂ द्रीय भूमि जल बो셍ड जल संसाधन, नदी विकास और गंगा संरक्षण विभाग, जल श啍ति मंत्रालय भारि सरकार Central Ground Water Board Department of Water Resources, River Development and Ganga Rejuvenation, Ministry of Jal Shakti Government of India AQUIFER MAPPING AND MANAGEMENT OF GROUND WATER RESOURCES EAST GODAVARI AND WEST GODAVARI DISTRICT, ANDHRA PRADESH दक्षक्षणी क्षेत्र, हैदराबाद Southern Region, Hyderabad REPORT ON AQUIFER MAPPING AND MANAGEMENT PLAN OF GODAVARI DELTAIC AREA PARTS OF EAST GODAVARI AND WEST GODAVARI DISTRICTS ANDHRA PRADESH CONTENTS P.No Area at a Glance 1 INTRODUCTION 1 – 10 Study Area Climate and Rainfall Drainage Geomorphology Soils Land Use, Irrigation & Cropping Pattern Previous Work 2 DATA COLLECTION AND GENERATION 11- 30 Geology Hydrogeology Ground Water Levels Ground Water Quality 3 DATA INTERPRETATION, INTEGRATION AND AQUIFER 31 – 38 MAPPING 4 GROUND WATER RESOURCES 39 – 43 5 GROUND WATER RELATED ISSUES 44 – 49 6 MANAGEMENT PLAN 50 – 52 7 SUM UP 53 – 54 Figures 1 Location and Administrative Divisions 2 2 Normal Rainfall Map 3 3 Drainage Map 5 4 Geomorphological Map 6 5 Topographic Elevation Map 7 6 Shoreline Development 7 7 Pedological Map 8 8 Land Use Pattern and Principal Crops 9 9 Area Irrigated by Different Sources 10 10 Geological Map 13 11 Geological (Schematic) Cross Section 13 12 Geological Cross Section 14 13 Schematic Map of Depth to Sand Stone 14 14 Hydrogeological Map 16 15 Depth to Water Level - Pre-Monsoon (2016) 17 16 Depth to Water Level - Post-Monsoon (2016) 17 17 Water Table Elevation Map 18 18 -

UFO Digital Cinema THEATRE COMPANY WEB S.No
UFO Digital Cinema THEATRE COMPANY WEB S.No. THEATRE_NAME ADDRESS CITY ACTIVE DISTRICT STATE SEATING CODE NAME CODE 1 TH1011 Maheshwari 70Mm Cinema Road,4-2-198/2/3, Adilabad 500401 Adilabad Y Adilabad ANDHRA PRADESH UFO 698 2649 2 TH1012 Sri Venkataramana 70Mm Sirpur Kagzahnagar, Adilabad - 504296 Kagaznagar Y Adilabad ANDHRA PRADESH UFO 878 514 3 TH1013 Mayuri Theatre Mancherial, Adilabad, Mancherial - 504209, AP Mancherial Y Adilabad ANDHRA PRADESH UFO 354 1350 4 TH1014 Noor Jahan Picture Palace (Vempalli) Main Road, Vempalli, Pin- 516329, Andhar Pradesh Vempalli Y Adilabad ANDHRA PRADESH UFO 635 4055 5 TH1015 Krishna Theatre (Kadiri) Dist. - Ananthapur, Kadiri - 515591 AP Anantapur Y Anantapur ANDHRA PRADESH UFO 371 3834 Main Road, Gorantla, Dist. - Anantapur, Pin Code - 6 TH1016 Ramakrishna Theatre (Gorantla) Anantapur Y Anantapur ANDHRA PRADESH UFO 408 3636 515231 A.P 7 TH1017 Sri Varalakshmi Picture Palace Dharmavaram-515671 Ananthapur Distict Dharmavaram Y Anantapur ANDHRA PRADESH UFO 682 2725 8 TH1018 Padmasree Theatre (Palmaner) M.B.T Road, Palmaner, Chittor. Pin-517408 Chittoor Y Chittoor ANDHRA PRADESH UFO 587 3486 9 TH1021 Sri Venkateswara Theatre Chitoor Vellore Road, Chitoor, Dist Chitoor, AP Chittoor Y Chittoor ANDHRA PRADESH UFO 584 2451 10 TH1022 Murugan Talkies Kuppam, Dist. - Chittoor, AP Kuppam Y Chittoor ANDHRA PRADESH UFO 316 3696 Nagari, Venkateshmudaliyar St., Chittoor, Pin 11 TH1023 Rajeswari Theatre Nagari Y Chittoor ANDHRA PRADESH UFO 600 1993 517590 12 TH1024 Sreenivasa Theatre Nagari, Prakasam Road, Chithoor, -

Andhra Pradesh Industrial Infrastructure Corporation Limited
Andhra Pradesh Industrial Infrastructure Corporation Limited DPR for Diversion of Forest Lands for Establishment of Industrial Parks at Dubacherla Forest Block in West Godavari District, Andhra Pradesh FINAL DETAILED PROJECT REPORT August 2015 Prepared By L&T INFRASTRUCTURE ENGINEERING LIMITED B1152201 RP008, Rev.0 L&T Infrastructure Engineering Ltd. Client: Andhra Pradesh Industrial Infrastructure Corporation Limited (APIIC) Parisramabhavanam, 5th Floor, Fateh Maidan Road, Hyderabad – 500 004 Project: DPR for Diversion of Forest Lands for Project No.: Establishment of Industrial Parks in W.G B1152201 District, AP Title: Final Detailed Project Report for Document No.: Rev.: Dubaclerla Forest Block RP008 0 This document is the property of L&T Infrastructure Engineering Ltd. (formerly File path: known as L&T-Rambøll Consulting Engineers Limited) and must not be \\hydsvr\intranet\roads & airports\02-b jobs\b1152201-gbd roads n airports 2015- passed on to any person or body not authorised by us to receive it nor be copied 2016\dpr for eluru forest lands\003-final detailed project report\002-rp008- or otherwise made use of either in full or in part by such person or body without dubacherla-final dpr\002-rp008-dubacherla-final dpr.docx our prior permission in writing. Notes: Revision Details: LPN 0 14.08.2015 First Submission SJV TKSS KRM KRM Init. Sign. Init. Sign. Init. Sign. Rev. Date Details Prepared Checked Approved Table of Contents DPR for Diversion of Forest Lands for Establishment of Industrial Parks in W.G District, AP B1152201 Final -

S.No Ht No S Name Mob Number Address DISTRICT Course Name Inst Name
S.No ht_no s_name mob_number Address DISTRICT course_name inst_name Vijaya Nagesh Institute of H, No: 1-5, (po&m) Diploma in Medical Medical Sciences (Denduluru V V Gopala Krishna Denduluru, ,Dt: Lab Technician Development Society Instute) , 1 0904035-S Basava 1111111111 West Godavari.,A.P West Godavari (Two Years) Course Denduluru , West Godavari H, No: 24 C-12/30, R M S Colony,,Etigattu, 34th Division, Eluru Diploma in Medical Padinjaraveedu ( P & M),,West Lab Technician Andhra Medical College , 2 1002020 Sowmya 7396343535 Godavari Dist. West Godavari (Two Years) Course Visakhapatnam , Visakhapatnam D No 2-129, Kesavaram Vill ,Ganapavaram ( Diploma in Medical Raghava Institute of Medical M),West Godavari Lab Technician Sciences (DMLT) , Kakinada , East 3 1003101 Rayala Rajesh 9603489196 Dist., A.P West Godavari (Two Years) Course Godavari Dist, A.P. Plat No: 103, Sajapuram, ,Harichandra Diploma in Towers, Phase- Opthalmic GSL Ophthalmic Assistant Course 2,(po&m) Tuni,,Dt: Assistant (Two , Rajanagaram Mandal , East 4 917014 Gorley Madhuri 9705404402 West Godavari. West Godavari Years) Course Godavari Dist, A.P. Page 1 S.No ht_no s_name mob_number Address DISTRICT course_name inst_name D No 5-124, Brahminstreet,Ach Diploma in anta(P&M), West Perfusion Swatantra Para Medical Satishkumar Godavari - Technician (Two Institutions , Rajahmundry , East 5 1103115 Banda 9959208202 534123,A.P West Godavari Years) Course Godavari Dist, A.P. Kovvali(v),Dendulur Diploma in Medical u(m),West Lab Technician Sri Sai DMLT Institution , 6 905053 Baby Andugula -

LIST of FARMS REGISTERED in WEST GODAVARI DISTRICT * Valid for 5 Years from the Date of Issue
LIST OF FARMS REGISTERED IN WEST GODAVARI DISTRICT * Valid for 5 Years from the Date of Issue. Address Farm Address S.No. Registration No. Name Father's / Husband's name Survey Number Issue date * Village / P.O. Mandal District Mandal Revenue Village Kalidindi Venkata 6-129, Indira Nagar, Bhimavaram Bhimavaram Mandal- West Godavari 1 AP-II-2008(02369) Subba Raju Shri . Narsa Raju China-Amiram Mandal 534204 District Bhimavaram Vempa 22, 24, 270 10.06.2008 Mantena Venkata Palakoderu Mandal - West Godavari 292, 294/1, 294/2, 294/6, 2 AP-II-2008(02370) Prahaladha Raju Shri . Narasimha Raju No 2-1, Korukollu 534209 District Palakoderu Korukollu 299/2, 294/3, 293/4 10.06.2008 363/1,3, 366/1, 337/4, Gottumukkala Shri .V.V.S.S.S.Bala Palakoderu Mandal- West Godavari 365/2, 366/3, 4, 5, 336/1, 3 AP-II-2008(02371) Vineetha Kumari Krishnam Raju Korukollu 534209 District Palakoderu Korukollu 364/2 10.06.2008 363/4, 1,2, 366/5, 365/1, Mantena Venkata Palakoderu Mandal- West Godavari 2,3, 366/2,3, 365/3, 4 AP-II-2008(02372) Pathi Raju Shri. Ramabadra Raju Korukollu 534209 District Palakoderu Korukollu 336/2 10.06.2008 298/1, 298/3, 299/1, Mantena Sudeer Palakoderu Mandal- West Godavari 299/2, 298/3A, B, C, 5 AP-II-2008(02373) Kumar Shri. Narayana Raju Korukollu 534209 District Palakoderu Korukollu 298/2 10.06.2008 Mantena Palakoderu Mandal- West Godavari 343, 360/3, 360/1, 360/4, 6 AP-II-2008(02374) Venkatapathi Raju Shri. -

Poll Res-31.Pmd
Poll Res. 40 (1) : 189-193 (2021) Copyright © EM International ISSN 0257–8050 SEASONAL VARIATION OF DRINKING WATER SOURCES AND CONTOUR MAPS - IN THE UPLAND AREA OF THE WEST GODAVARI DISTRICT, AP, INDIA C.A. JYOTHIRMAYEE1, SR SHOWRILU2, K. SREELATHA3 AND A. NIRMALA JYOTHSNA4 1 Department of Chemistry, 2, 3 & 4Department of Physics, Ch SD St Theresa’s College for Women (A), Eluru, A.P., India (Received 22 June, 2020; accepted 31 July, 2020) ABSTRACT Water plays an essential role in human life. WHO reports that approximately 36% of urban and 65% of rural Indian were without access to safe drinking water. It must be noted that a regular chemical analysis must be done to ensure that the quality of water in this area is not contaminated. Ground Water quality plays an important role in groundwater protection and quality conservation; hence it is very much important to assess the groundwater quality not only for its present use but also a potential source of water for future consumption. Ground water is highly valuable source of water because of its unique properties which may not be possessed by surface water. The chemical quality tests may be difficult to interpret the groundwater quality for the whole region. Therefore, the quality tests results of groundwater can be represented by a variety of graphic techniques developed to display and detect the major chemical constituents. The contour maps are also useful to show the isograms of equally chemical, biological contaminants concentrations with physical parameters. Contour maps are extremely useful for various research areas. This technique could give a more regular gradient of the groundwater table than other methods. -
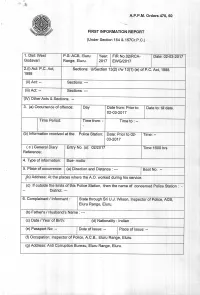
2.Cr. No.2-RCA-17
A.P.P.M. Orders 470,50 I FIRST INFORMATION REPORT (Under Section 154 & 1S7Cr.P.C.) 1. Dist: West P.S: ACB, Eluru Year: FIR No.02lRCA- Date: 02-03-2017 Godavari Range, Eluru. 2017 EWGt2017 2.(i) Act: P.C. Act, Sections: U/Section 13(2) r/w 13(1) 1ey oinC. nct, tOaa 1 988 (ii) Act: - Sections: -- (iii) Act: Sections, I =- -- (lV) OtherActs & Sections: -- 3. (a) Occurrence of offence: Day Date from: Prior to Date to: till date. 02-03-2017 Time Period: Time from: - Time to : -- (b) lnformation received at the Police Station: Date: Prior to 02- Time: - 03-2017 (c)General Diary Entry No. (s): A212017 Time 1600 hrs Reference: 4. Type of information: Sue- motto 5. Place of occurrence: (a) Direction and Distance :--- Beat No. - Address: At the places where the A.O. worked u(b) during his servicl_ District: -- 6. Complainant / lnformant : State through Sri U.J. Wilson, lnspector of Police, ACB, Eluru Range, Eluru. (b) Father's I Husband's Name (c) Date lYear of Birth: (d) Nationality : lndian (e) Passport No: -- Date of lssue: -- Place of lssue: - (f) Occupation: lnspector of Police, A.C.B., Eluru Range, Eluru. I ,. - 7. Details of known suspected / / unknown accused with full particulars. (Attach separate sheet if necessary): Sri Geddam Vijaya Ganesh Babu S/o Vishnumurthy, Age 55 years, Sub_Treasury Officer, Gannavaram, Krishna District. Physical features, deformities and other details of the suspect: Date/Year Height in Sex Build Complexion ldentification Marks(s) , of Birth Cms. 1. 2. 3. 4. 5. 6. Deformities / Teeth Hair Eyes Habits(s) Peculiarities Dress Habits 7, 8. -

Fairs and Festival, 4 West Godavari, Part VII
PRO. 179.4 (N) o . 7S0 .~ WEST GODAVARI CENSUS OF INDIA 1961 VOLUME II ANDHRA PRADESH PART VII - B (4) FAIRS AND FESTIV (4. West Godavari District) A: CHANDRA SEKHAR OF THE INDIAN ADMINISTRATIVE SERVICB Superintendent o.J,...J;_"UJIF. Q_wations, Andhra Pradesh Pnce: Rs .. 6.50 P. or 15 Sh. 2 d. or $ 2.34 c. ~9t{ CENSUS PUBLICATIONS, ANDHRA PRADESH . , ,! (All the Census Publications of this State bear Vol. No. II) PART I-A General Report PART J-B Report on Vital Statistics PART I-C Subsidiary Tables PART II-A General Population Tables PART II-B (i) Economic Tables [B-1 to B-IV] PART IJ-B (ii) Economic Tables fB-V to B-IXJ PART n-c Cultural and Migration Tables PART III .J Household Economic Tables PART IV-A Report on Housing and Establishments (with Subsidiary Tables) PART IV-B Housing and Establishment Tables PART V-A Special Tables for Scheduled Castes and Scheduled Tribes PART V-B Ethnographic Notes on Scheduled Castes and Scheduled Tribes PART VI Village Survey MonogTaphs (46) PART VII-A (1) ~ Handicrafts Survey Reports (Selected Crafts) PART VII-A (2) PART VII-B (1 to 20), .. Fairs and Festivals (Separate Book for each District) PART VIII-A Administration Report-Enumeration I ~ (Not for sale) PART VIII-B Administration Report-Tabulation .J PART IX State Atlas PART X Special Report on Hyderabad City District Census Handbooks (Separate Volume for each District) ! I, f Plate I: Sri Venkateswaraswamv-Dwaraka Thirumala. Eluru Taluk - Courtesy : Commissioner. H.R.&C .E . (Admn.) Dept., A . -

Ground Water Brochure West Godavari District, Andhra Pradesh (Aap- 2012-13)
For Official Use Only CENTRAL GROUND WATER BOARD MINISTRY OF WATER RESOURCES GOVERNMENT OF INDIA GROUND WATER BROCHURE WEST GODAVARI DISTRICT, ANDHRA PRADESH (AAP- 2012-13) SOUTHERN REGION HYDERABAD September 2013 CENTRAL GROUND WATER BOARD MINISTRY OF WATER RESOURCES GOVERNMENT OF INDIA GROUND WATER BROCHURE WEST GODAVARI DISTRICT, ANDHRA PRADESH (AAP 2012-13) By Dr. P. N. RAO SCIENTIST-D SOUTHERN REGION BHUJAL BHAWAN GSI Post, NH-IV, Faridabad, Bandlaguda Haryana, India Hyderabad – 500 068 Te: 0129-2419074 Tel: 040-24225201 Fax: 0129-2412524, 2413050 Fax: 040-24225202 Gram: Bhumijal Email: [email protected] GROUND WATER BROCHURE WEST GODAVARI DISTRICT, ANDHRA PRADESH (AAP 2012-13) CONTENTS DISTRICT AT A GLANCE 1.0 INTRODUCTION 2.0 RAINFALL & CLIMATE 3.0 GEOMORPHOLOGY & SOIL TYPES 4.0 GROUND WATER SCENARIO 4.1 Hydrogeology 4.2 Ground Water Resources 4.3 Ground Water Quality 4.4 Status of ground water development 5.0 GROUND WATER MANAGEMENT STRATEGY 5.1 Ground Water Development 5.2 Water Conservation & Artificial Recharge 5.3 Ground Water Related issues & Problems 6.0 GROUND WATER RELATED PROBLEMS & ISSUES 7.0 GROUND WATER QUALITY 8.0 AWARENESS & TRAINING ACTIVITY 9.0 RECOMMENDATIONS FIGURES: 1.0 Administrative divisions, Drainage, location of exploratory wells, West Godavari district, Andhra Pradesh. 2.0 Hydrogeology, West Godavari district 3.0 Panel Diagram showing disposition of geological formations 4.0 Geological cross section 5.0 Depth to water level- Premonsoon (May, 2012) and post-monsoon (Nov, 2012). 6.0 Hydrographs of select -

Standing Committee of National Board for Wildlife
STANDING COMMITTEE OF NATIONAL BOARD FOR WILDLIFE TWENTY SECOND MEETING 25 th APRIL 2011 AGENDA NOTES GOVERNMENT OF INDIA MINISTRY OF ENVIRONMENT AND FORESTS INDEX SL. NO AGENDA ITEM PAGE NO. 1. Agenda Item No.1: Confirmation of the Minutes of meeting of the Standing 3 Committee of National Board for Wildlife held on 24th January 2011. 2. Agenda Item No.2: Action taken report on the recommendations of 21 st 4 Meeting of the Standing Committee of National Board for Wildlife held on 24 th January 2011 3 Agenda Item No. 3: 3.1 Report of the Expert Committee on Conservation of Kolleru Lake Sanctuary 3.2 Delegation of the powers of the State Board for Wildlife to the Chairman in case of Strategic Border Roads 3.3 Agenda item proposed by Shri. Biswajit Mohanty, Member, NBWL 4 Agenda Item No. 4: 4.1 Proposals for diversion of PAs 4.2 Proposals for taking up activities within 10 Kms from the boundaries of Protected Areas 5 Agenda Item No.5. Any other item with the permission of the Chair ********************* AGENDA NOTES FOR THE TWENTY SECOND MEETING OF THE STANDING COMMITTEE OF NATIONAL BOARD FOR WILD LIFE Date: 25 th April 2011 Venue: Paryavaran Bhawan, New Delhi. AGENDA ITEM NO.1 Confirmation of the minutes of the 21 st Meeting of Standing Committee of National Board for Wildlife held on 24 th January 2011 . The minutes of the 21 st Meeting of Standing Committee of NBWL, held on 24.01.2011 were circulated to the members on 07.02.2011. -

Regional Divisions of India a Cartographic Analysis, Vol-II, Series-I
CENSUS OF INDIA REGIONAL DIVISIONS OF INDIA -A CARTOGRAPHIC ANALYSIS OCCASIONAL PAPERS SFRIES-l VOLUME-II ANDHRA PRADESH Planning & Supervision B.K. ROY. M·A., Pb. D. Deputy Registrar General (Map) General Direction & Editing VJJAY S. VERMA of the Indian A dministrative Service Registrar General & Census Commissio:t;ler, India 2-A, Mansingh Road, New Delhi Maps included in this volume are based upon Survey of India map with the permission of the Surveyor General of India, The boundary of Megbalaya sbown on tbe map of India is as interpreted from the North eastern areas (Reorganisation) Act. 1971. but has yet to be verified (applicable to India map only). The territorial waters of India extend into the sea to a distance of twelve nautical mi1~s measured from the appropriate base line. © Government of (ndia Copyright 1988. ~ if:;rr ';fT~ "'f fq~r-l10001 HOME MINISTER INDIA NEW DELHI-110001 Oct. 26, 1988 FOREWORD Experience has taught us that planning bas to be related the situation in the field in order to better respond to local aspirations and for better utilization of local resources. A lot of planning has, of necessity, to be for larger areas, encompassing an agglomeration of adminis trative units. Even such macro planning has. in order to be realistic, to be cognisant of the realities at the micro level. Correspondingly. such plans for bigger areas and involving larger outlays have also to be administ~red from a suitably higb threshold of administrative authority and by a wide network: of administrative hierarchy. Nevertheless. there is a whole corpus of activities which can be and are, in fact, better planned, conducted and financed at the lower or local levels.