Certified Ethical Hacker (CEH) Cert Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

A the Hacker
A The Hacker Madame Curie once said “En science, nous devons nous int´eresser aux choses, non aux personnes [In science, we should be interested in things, not in people].” Things, however, have since changed, and today we have to be interested not just in the facts of computer security and crime, but in the people who perpetrate these acts. Hence this discussion of hackers. Over the centuries, the term “hacker” has referred to various activities. We are familiar with usages such as “a carpenter hacking wood with an ax” and “a butcher hacking meat with a cleaver,” but it seems that the modern, computer-related form of this term originated in the many pranks and practi- cal jokes perpetrated by students at MIT in the 1960s. As an example of the many meanings assigned to this term, see [Schneier 04] which, among much other information, explains why Galileo was a hacker but Aristotle wasn’t. A hack is a person lacking talent or ability, as in a “hack writer.” Hack as a verb is used in contexts such as “hack the media,” “hack your brain,” and “hack your reputation.” Recently, it has also come to mean either a kludge, or the opposite of a kludge, as in a clever or elegant solution to a difficult problem. A hack also means a simple but often inelegant solution or technique. The following tentative definitions are quoted from the jargon file ([jargon 04], edited by Eric S. Raymond): 1. A person who enjoys exploring the details of programmable systems and how to stretch their capabilities, as opposed to most users, who prefer to learn only the minimum necessary. -
Network Forensic Tools Sidebar
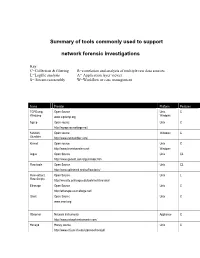
Summary of tools commonly used to support network forensic investigations Key: C=Collection & filtering R=correlation and analysis of multiple raw data sources L=Logfile analysis A= Application layer viewer S= Stream reassembly W=Workflow or case management Name Provider Platform Features TCPDump, Open Source Unix, C Windump www.tcpdump.org Windows Ngrep Open source Unix C http://ngrep.sourceforge.net/ Network Open source Windows C Stumbler http://www.netstumbler.com/ Kismet Open source Unix C http://www.kismetwireless.net Windows Argus Open Source Unix CL http://www.qosient.com/argus/index.htm Flow-tools Open Source Unix CL http://www.splintered.net/sw/flow-tools/ Flow-extract, Open Source Unix L Flow Scripts http://security.uchicago.edu/tools/net-forensics/ Etherape Open Source Unix C http://etherape.sourceforge.net/ Snort Open Source Unix C www.snort.org Observer Network Instruments Appliance C http://www.networkinstruments.com/ Honeyd Honey source Unix C http://www.citi.umich.edu/u/provos/honeyd/ Ethereal Open Source Windows CLS www.Ethereal.com Unix Etherpeek Wild Packets, Inc. Windows CLS www.wildpackets.com SecureNet Intrusion Inc. Windows with CS http://www.intrusion.com collector appliance FLAG Open Source Unix L Forensic and http://www.dsd.gov.au/library/software/flag/ Log Analysis GUI ACID Analysis Console for Intrusion Databases Unix L http://www.andrew.cmu.edu/~rdanyliw/snort/snortacid.html Shadow http://www.nswc.navy.mil/ISSEC/CID/index.html Unix LS DeepNines and http://www.deepnines.com/sleuth9.html Unix CSR Sleuth9 Infinistream -

Guide to Computer Forensics and Investigations Fourth Edition
Guide to Computer Forensics and Investigations Fourth Edition Chapter 11 Virtual Machines, Network Forensics, and Live Acquisitions Objectives • Describe primary concerns in conducting forensic examinations of virtual machines • Describe the importance of network forensics • Explain standard procedures for performing a live acquisition • Explain standard procedures for network forensics • Describe the use of network tools Guide to Computer Forensics and Investigations 2 Virtual Machines Overview • Virtual machines are important in today’s networks. • Investigators must know how to detect a virtual machine installed on a host, acquire an image of a virtual machine, and use virtual machines to examine malware. Virtual Machines Overview (cont.) • Check whether virtual machines are loaded on a host computer. • Check Registry for clues that virtual machines have been installed or uninstalled. Network Forensics Overview • Network forensics – Systematic tracking of incoming and outgoing traffic • To ascertain how an attack was carried out or how an event occurred on a network • Intruders leave trail behind • Determine the cause of the abnormal traffic – Internal bug – Attackers Guide to Computer Forensics and Investigations 5 Securing a Network • Layered network defense strategy – Sets up layers of protection to hide the most valuable data at the innermost part of the network • Defense in depth (DiD) – Similar approach developed by the NSA – Modes of protection • People • Technology • Operations Guide to Computer Forensics and Investigations -

Intelligent Malware Detection Using File-To-File Relations and Enhancing Its Security Against Adversarial Attacks
Graduate Theses, Dissertations, and Problem Reports 2019 Intelligent Malware Detection Using File-to-file Relations and Enhancing its Security against Adversarial Attacks Lingwei Chen [email protected] Follow this and additional works at: https://researchrepository.wvu.edu/etd Part of the Information Security Commons Recommended Citation Chen, Lingwei, "Intelligent Malware Detection Using File-to-file Relations and Enhancing its Security against Adversarial Attacks" (2019). Graduate Theses, Dissertations, and Problem Reports. 3844. https://researchrepository.wvu.edu/etd/3844 This Dissertation is protected by copyright and/or related rights. It has been brought to you by the The Research Repository @ WVU with permission from the rights-holder(s). You are free to use this Dissertation in any way that is permitted by the copyright and related rights legislation that applies to your use. For other uses you must obtain permission from the rights-holder(s) directly, unless additional rights are indicated by a Creative Commons license in the record and/ or on the work itself. This Dissertation has been accepted for inclusion in WVU Graduate Theses, Dissertations, and Problem Reports collection by an authorized administrator of The Research Repository @ WVU. For more information, please contact [email protected]. Intelligent Malware Detection Using File-to-file Relations and Enhancing its Security against Adversarial Attacks Lingwei Chen Dissertation submitted to the Benjamin M. Statler College of Engineering and Mineral Resources at West Virginia University in partial fulfillment of the requirements for the degree of Doctor of Philosophy in Computer Science Yanfang Ye, Ph.D., Committee Chairperson Donald Adjeroh, Ph.D. Elaine M. -
![Reversing Malware [Based on Material from the Textbook]](https://docslib.b-cdn.net/cover/8924/reversing-malware-based-on-material-from-the-textbook-1438924.webp)
Reversing Malware [Based on Material from the Textbook]
SoftWindows 11/23/05 Reversing Malware [based on material from the textbook] Reverse Engineering (Reversing Malware) © SERG What is Malware? • Malware (malicious software) is any program that works against the interest of the system’s user or owner. • Question: Is a program that spies on the web browsing habits of the employees of a company considered malware? • What if the CEO authorized the installation of the spying program? Reverse Engineering (Reversing Malware) © SERG Reversing Malware • Revering is the strongest weapon we have against the creators of malware. • Antivirus researchers engage in reversing in order to: – analyze the latest malware, – determine how dangerous the malware is, – learn the weaknesses of malware so that effective antivirus programs can be developed. Reverse Engineering (Reversing Malware) © SERG Distributed Objects 1 SoftWindows 11/23/05 Uses of Malware • Why do people develop and deploy malware? – Financial gain – Psychological urges and childish desires to “beat the system”. – Access private data – … Reverse Engineering (Reversing Malware) © SERG Typical Purposes of Malware • Backdoor access: – Attacker gains unlimited access to the machine. • Denial-of-service (DoS) attacks: – Infect a huge number of machines to try simultaneously to connect to a target server in hope of overwhelming it and making it crash. • Vandalism: – E.g., defacing a web site. • Resource Theft: – E.g., stealing other user’s computing and network resources, such as using your neighbors’ Wireless Network. • Information Theft: – E.g., stealing other user’s credit card numbers. Reverse Engineering (Reversing Malware) © SERG Types of Malware • Viruses • Worms • Trojan Horses • Backdoors • Mobile code • Adware • Sticky software Reverse Engineering (Reversing Malware) © SERG Distributed Objects 2 SoftWindows 11/23/05 Viruses • Viruses are self-replicating programs that usually have a malicious intent. -

Wireless Networking in the Developing World
Wireless Networking in the Developing World Second Edition A practical guide to planning and building low-cost telecommunications infrastructure Wireless Networking in the Developing World For more information about this project, visit us online at http://wndw.net/ First edition, January 2006 Second edition, December 2007 Many designations used by manufacturers and vendors to distinguish their products are claimed as trademarks. Where those designations appear in this book, and the authors were aware of a trademark claim, the designations have been printed in all caps or initial caps. All other trademarks are property of their respective owners. The authors and publisher have taken due care in preparation of this book, but make no expressed or implied warranty of any kind and assume no responsibility for errors or omissions. No liability is assumed for incidental or consequential damages in connection with or arising out of the use of the information contained herein. © 2007 Hacker Friendly LLC, http://hackerfriendly.com/ This work is released under the Creative Commons Attribution-ShareAlike 3.0 license. For more details regarding your rights to use and redistribute this work, see http://creativecommons.org/licenses/by-sa/3.0/ Contents Where to Begin 1 Purpose of this book........................................................................................................................... 2 Fitting wireless into your existing network.......................................................................................... 3 Wireless -

Leveraging Advanced Linux Debugging Techniques for Malware Hunting
Beyond Whitelisting: Fileless Attacks Against Linux Shlomi Boutnaru ./whomai • Currently: − CTO & Co-Founder, Rezilion • Previous: − Chief Technologist Cybersecurity, PayPal − CTO & Co-Founder, CyActive − Acquired by PayPal (2015) Fileless Malware - Definition “… a variant of computer related malicious software that exists exclusively as a computer memory-based artifact i.e. in RAM. It does not write any part of its activity to the computer's hard drive meaning that it's very resistant to existing Anti-computer forensic strategies that incorporate file-based whitelisting, signature detection, hardware verification, pattern-analysis, time-stamping, etc., and leaves very little by way of evidence that could be used by digital forensic investigators to identify illegitimate activity. As malware of this type is designed to work in-memory, its longevity on the system exists only until the system is rebooted…” https://en.wikipedia.org/wiki/Fileless_malware In the News… https://www.techradar.com/news/why-fileless-malware-is-the-biggest-new-threat-to-your-business https://securelist.com/fileless-attacks-against-enterprise-networks/77403/ https://threatpost.com/threatlist-ransomware-attacks-down-fileless-malware-up-in-2018/136962/ And More… Statistics https://www.barkly.com/ponemon-2018-endpoint-security-statistics-trends “…77% of attacks that successfully compromised organizations in 2017 utilized fileless techniques…” https://blog.barkly.com/2018-cybersecurity-statistics A third of all attacks are projected to utilize fileless techniques in 2018. -

Use Style: Paper Title
COMPARATIVE ANALYSIS OF PACKET SNIFFERS : A STUDY Jyoti Senior Engineer, Bharat Electronics Limited (India) ABSTRACT Today everything is being centralized through a common dedicated network to ease its use, make it more user friendly and increase its efficiency. The size of these centric networks is also increasing rapidly. So the management, maintenance and monitoring of these networks is important to keep network smooth and improve economic efficiency. Packet sniffing or packet analysis is the process of capturing data passed over the local network and looking for any information that may be useful. There is a wide variety of packet sniffers available in the market that can be exploited for this purpose. This paper focuses on the basics of packet sniffer, its working principle and a comparative study of various packet sniffers. Keywords: Packet Capture; Packet Sniffer; network monitoring; wireshark; NIC I INTRODUCTION A packet sniffer is a program that can see all of the information passing over the network it is connected to. As data steams back and forth on the network the program looks at it or „sniffs‟ each packet. A packet is a part of a message that has been broken up. Packet analysis can help us understand network characteristics, learn who is on network, determine who or what is utilizing available bandwidth, identify peak network usage times, identify possible attacks or malicious activity, and find unsecured and bloated applications[1]. II WORKING There are two modes in which a network interface of a machine work i.e Promiscuous and Non-promiscuous. Promiscuous mode in one in which the NIC of the machine can take over all packets and a frame it receives on network, namely this machine (involving its software) is sniffer. -

Deeppanda Paging Dr. Smith Melissa L. Markey, Esq
DeepPanda Paging Dr. Smith Melissa L. Markey, Esq. Hall, Render, Killian, Heath & Lyman, PC 1512 Larimer Street Suite 300 Denver CO 80202 248-310-4876 1 A Brief Introduction… Data Breaches © Hall, Render, Killian, Heath & Lyman, P.C. The Threats Ransomware Identity Theft Business Email Cyberstalking Compromise Fraud, Extortion, Phishing/Whaling/ etc. Vishing/Pharming DDoS attacks Spoofing Social Engineering Botnets Fileless Attacks Malware Medjacking Logic Bombs Dronejacking Trojans, Worms, Viruses The Players FBI/Cyber Action Teams Department of Justice DoD/DCIS Secret Service Electronic Crimes Task Force US Postal Inspection Service Internet Safety Enforcement Team AG State Police Local Police Interpol FTC ATF Internet Crime Complaint Center Is This Real? How real is the threat of cybercrime against a healthcare provider? Sometimes the healthcare provider is the target Healthcare providers are a treasure-trove of ID theft information Celebrity patients, public health emergencies… all are fodder for the media Healthcare has all the best data Sometimes the healthcare provider is just collateral damage Lots of computers to be taken over by a botnet Because it's there… Hospital as a Target Israeli Hospital Hacked Infections Shut Down Services A Reader’s Comment: “…It's the computer system that has a virus not the doctor. The patient knows what time their appointment's for and may already have arranged to take time off work. The doctor knows what time they have a clinic…..” “…a hospital should not be totally dependent on functioning IT systems. It sounds like the decision of an administrator totally divorced from any perception of patients' circumstances…” It’s More Than The EMR… It’s More Than The EMR… Hospitals as Collateral Damage Health care as a target: A piece of critical infrastructure Not an Effective Security Stance Motivations Data Breaches © Hall, Render, Killian, Heath & Lyman, P.C. -

Linux Viruses by Aaron Grothe March 18, 2009
Linux Virus Writing: A How To Linux Viruses by Aaron Grothe March 18, 2009 1 Disclaimer #1 ■ This presentation will give some hints about how to write very simple viruses and other malware that run under the GNU/Linux and other operating systems. ■ As part of this we'll be looking at several example viruses which can be dangerous to do 2 Disclaimer #2 ■ This talk is based on my opinions and experiences and nothing else. It does not reflect the views or opinions of any place I work or organization that I may be a part of. 3 Reactions The following is the rough breakdown of Reactions when I announced the talk broke down as follows ■ Wow! Couldn't you get Bob McCoy to Talk? - 50% ■ Linux doesn't have viruses. Duh!!! - 30% ■ Meow - 20% 4 What is a Computer Virus? ■ One classic definition is a self-reproducing program that requires user interaction to propagate It is not by the classic definition able to propagate to remote systems without human interaction. 5 First Linux Virus??? ■ Staog – 1996 Staog appears to have been the first public seen virus ■ Bliss – 1996/Early 1997 Bliss was the first “popular” virus. It got quite a bit of press. The source code to bliss is still available in the comp.security.unix archives Both of these needed specific versions of libraries/kernels etc. So they were version specific and neither runs on a modern system anymore 6 Linux Doesn't Have Viruses ■ This must be true. Everybody says this!!! ■ A lot of Linux distros don't install any anti-virus ■ People switch to Linux at work to avoid anti-virus programs 7 -

Computer Virus Tutorial
Computer Virus Tutorial Computer Virus Tutorial License Copyright 1996-2005, Computer Knowledge. All Rights Reserved The Computer Knowledge Virus Tutorial is a copyright product of Computer Knowledge. It also contains copyrighted material from others (used with permission). Please honor the copyrights. Read the tutorial, learn from the tutorial, download and run the PDF version of the tutorial on your computer, link to the tutorial. But, please don't copy it and claim it as your own in whole or part. The PDF version of the Computer Knowledge Virus Tutorial is NOT in the public domain. It is copyrighted by Computer Knowledge and it and all accompanying materials are protected by United States copyright law and also by international treaty provisions. The tutorial requires no payment of license fees for its use as an educational tool. If you are paying to use the tutorial please advise Computer Knowledge (PO Box 5818,www.co-bw.com Santa Maria, CA 93456 USA). Please provide contact information for those charging the fee; even a distribution fee. License for Distribution of the PDF Version No royalties are required for distribution. No fees may be charged for distribution of the tutorial. You may not use, copy, rent, lease, sell, modify, decompile, disassemble, otherwise reverse engineer, or transfer the licensed program except as provided in this agreement. Any such unauthorized use shall result in immediate and automatic termination of this license. In no case may this product be bundled with hardware or other software without written permission from Computer Knowledge (PO Box 5818, Santa Maria, CA 93456 USA). -

Cyber-Crimes: a Practical Approach to the Application of Federal Computer Crime Laws Eric J
Santa Clara High Technology Law Journal Volume 16 | Issue 2 Article 1 January 2000 Cyber-Crimes: A Practical Approach to the Application of Federal Computer Crime Laws Eric J. Sinrod William P. Reilly Follow this and additional works at: http://digitalcommons.law.scu.edu/chtlj Part of the Law Commons Recommended Citation Eric J. Sinrod and William P. Reilly, Cyber-Crimes: A Practical Approach to the Application of Federal Computer Crime Laws, 16 Santa Clara High Tech. L.J. 177 (2000). Available at: http://digitalcommons.law.scu.edu/chtlj/vol16/iss2/1 This Article is brought to you for free and open access by the Journals at Santa Clara Law Digital Commons. It has been accepted for inclusion in Santa Clara High Technology Law Journal by an authorized administrator of Santa Clara Law Digital Commons. For more information, please contact [email protected]. ARTICLES CYBER-CRIMES: A PRACTICAL APPROACH TO THE APPLICATION OF FEDERAL COMPUTER CRIME LAWS Eric J. Sinrod' and William P. Reilly" TABLE OF CONTENTS I. Introduction ................................................................................178 II. Background ................................................................................ 180 A. The State of the Law ................................................................... 180 B. The Perpetrators-Hackers and Crackers ..................................... 181 1. H ackers ................................................................................... 181 2. Crackers .................................................................................