Creating Trust in Critical Network Infrastructures: Korean Case Study
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Recommendation on Making Broadband Affordable in Asia
Pro-poor. Pro-market. Recommendation on Making Broadband Affordable in Asia Abu Saeed Khan Senior Policy Fellow, LIRNEasia January 2014 Please direct all correspondence to: abu[at]lirneasia[dot]net LIRNE asia , 12, Balcombe Place, Colombo 00800, Sri Lanka v: +94 (0)11 267 1160 | f: +94 (0)11 267 5212 | [email protected] Pro-poor. Pro-market. Table of Contents 1. Background .................................................................................................................................................. 4 2. Submarine cables ......................................................................................................................................... 6 2.1 Transatlantic - U.S.A. to Europe: ................................................................................................................... 6 2.2 Europe demystifies infrastructure: ................................................................................................................ 7 2.3 Transpacific route between U.S.A. and Asia: ................................................................................................ 8 2.3.1 Singapore: .................................................................................................................................................. 9 2.3.2: Hong Kong: ............................................................................................................................................. 10 3. Internet gets centralized in Asia ............................................................................................................ -

2 April 1993
1------------..:....---=-- --~"- ;..:."-..:..::- ::..--=.--::..::.-- ::..:- -.:..:.... :.:.: - ::.:...- -=-==-=-=====-- April 2 1993 PM gets engaged ramatic jump in\- -HIV cases CHRISTOF MALETSKY A TOTAL of 51 per cent of the 4 4 10 HIV cases recorded in Namibia over a seven-year pcriod were reported in 1992 alone, showing a dramalic increase, according 10 fi gures just released by the PRIME MinistltT Hage Ministry of Health and Social Services. Geingob will formally HIV cases among children under five years old announce his engage have shot up by 140 per cent in one year, while ment tomorrow. See overall the incident ra te for 1992 shows a startling s tor~.. page J jump - up to 146 per 100 000 people compared 10 >-;:======:::; 0,3 per 100 000 in 1986. I The. HIV Infection Repon for 1992 fCveals that HIT your the most cases oCHrY infection for anyone month during the seven-year period (1986 - 1992), were weekend reported in December 1992 with 253 cac;es. There has also beel.l an increase of L28 pe r cen! in style. in HIV infections in the group of people aged 45 Don't MISS years and above. FUllher, 54 per cent of the cases were male, 44 your free per cent female and two per cent unknown. HIV infection increased by 62,6 percent from Weekender 1991101992 and the incident rate for HIV infec in today's tion for 1992 was 146 per 100 000 people, a Namiblan! Continued on page 2 Lu COMPION ph ~.ceutic~ l s Law firm pleaded for COMPION PHABMACY TEl (061) 229260 Andt' Compion (B.Phann.) FAX: (06!) 231161 3.4.93 WHOLE LEG OF release of Ananias A pharmacist available 24 hours per day for medication. -
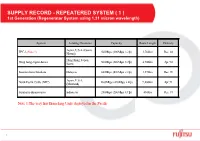
SUPPLY RECORD - REPEATERED SYSTEM ( 1 ) 1St Generation (Regenerator System Using 1.31 Micron Wavelength)
SUPPLY RECORD - REPEATERED SYSTEM ( 1 ) 1st Generation (Regenerator System using 1.31 micron wavelength) System Landing Countries Capacity Route Length Delivery Japan, U.S.A. (Guam, TPC-3 (Note 1) 560Mbps (280Mbps x 2fp) 3,760km Dec. 88 Hawaii) Hong Kong, Japan, Hong Kong-Japan-Korea 560Mbps (280Mbps x 2fp) 4,700km Apr. 90 Korea Kuantan-Kota Kinabaru Malaysia 840Mbps (420Mbps x 2fp) 1,570km Dec. 90 Japan, U.S.A. North Pacific Cable (NPC) 1680Mbps (420Mbps x 4fp) 9,400km Apr. 91 (Mainland) Surabaya-Banjarmasin Indonesia 280Mbps (280Mbps x 1fp) 410km Dec. 91 N. ote 1:The very first Branching Units deployed in the Pacific 1 SUPPLY RECORD - REPEATERED SYSTEM ( 2 ) 2nd Generation (Regenerator System using 1.55 micron wavelength) System Landing Sites Capacity Route Length Delivery UK-Germany No.5 (Note 2) UK, Germany 3.6Gbps (1.8Gbps x 2fp) 500km Oct. 91 Brunei-Singapore Brunei, Singapore 1120Mbps (560Mbps x 2fp) 1500km Nov. 91 Brunei, Malaysia, Brunei-Malaysia-Philippines (BMP) 1120Mbps (560Mbps x 2fp) 1500km Jan. 92 Philippines Japan, U.S.A. TPC-4 1680Mbps (560Mbps x 3fp) 5000km Oct. 92 (Mainland) Japan, Hong Kong, APC Taiwan, Malaysia, 1680Mbps (560Mbps x 3fp) 7600km Aug. 93 Singapore Malaysia-Thailand Malaysia, Thailand 1120Mbps (560Mbps x 2fp) 1500km Aug. 94 (incl. Petchaburi-Sri Racha) Russia-Japan-Korea (RJK) Russia, Japan, Korea 1120Mbps (560Mbps x 2fp) 1700km Nov. 94 Thailand, Vietnam, Thailand-Vietnam-Hong Kong (T-V-H) 1120Mbps (560Mbps x 2fp) 3400km Nov. 95 Hong Kong N. ote 2: The very first giga bit submarine cable system in the world 2 SUPPLY RECORD - REPEATERED SYSTEM ( 3 ) 3rd Generation (Optical Amplifier System) System Landing Sites Capacity Route Length Delivery Malaysia Domestic (Southern Link) Malaysia 10Gbps (5Gbps x 2fp) 2,300km Jul. -

Interim Report on the Asian Telecom Connectivity Market
Asian Telecom Connectivity Market: Executive Summary (Research conducted 2005) The following is a summary of the findings of the Telecommunications Research Project University of Hong Kong NOTE1 The original research was undertaken for a private client in 2005 and the detailed report and recommendations are therefore not publicly available, but the following Executive Summary was made available at the time to companies who provided information and their opinions. In respect of demand and supply, the research goes beyond the data and analysis provided by TeleGeography (an industry benchmark publication) by estimating various rates of growth of demand against estimates of capacity lit and capacity used, thereby projecting various dates of capacity exhaustion. Unity Cable Since this research the 10,000 km Unity Cable connecting Japan and the USA has been announced (2008) consisting of carriers SingTel, Bharti- Airtel and KDDI, together with Internet companies Google, Pacnet and Global Transit (subsidiary of Malaysian network exchange company, AIMS). 1 This Executive Summary also appears as Appendix 2 in John Ure (ed.) Telecommunications Development in Asia, HKU Press, April 2008 1 Asian Telecom Connectivity Market: Executive Summary2 Between June and August 2005, the Telecommunications Research Project (TRP) at the University of Hong Kong undertook an extensive look at the regional bandwidth market. The research study was undertaken with intent to understand both the supply (and pricing) and demand sides of the equation, based upon feedback direct from carriers and experts, on the one hand, and from those directly purchasing bandwidth on the other. It quickly became apparent that the supply and demand of bandwidth represent two distinct stories which, not only are not necessarily in alignment (obvious enough to anyone who has been watching the market over the last 10 years), but are at times quite seriously disconnected in their fundamental drivers. -

KDDI Global ICT Brochure
https://global.kddi.com KDDI-Global Networks and IT Solutions Networking, Colocation, System Integration around the world BUILDING YOUR BUSINESS TOGETHER KDDI solutions are at the cutting-edge in all fields of information and communications KDDI, a Fortune Global 500 company, is one of Asia’s largest telecommunications providers, with approximately US$48 billion in annual revenue and a proven track record extending over many years and around the world. We deliver all-round services, from mobile phones to fixed-line communications, making us your one-stop solution provider for telecommunications and IT environments. The high praise and trust enjoyed by our TELEHOUSE data centers positioned around the world have kept us at the forefront of service and quality. Since our establishment in 1953, we have expanded our presence into 28 countries and 60 cities, with over 100 offices around the world supporting the success of our international customers through our high quality services. KDDI’s mobile telephone brand “au” has achieved significant market share in Japan, one of the world’s most comprehensive KDDI Quick Facts communications markets. KDDI’s relationship with over 600 carriers worldwide enables us to provide high-quality international network services in over 190 countries. Our exciting ventures, built on extensive experience, include investment in the “South-East Asia Japan 2 Cable”, which connects 11 locations in 9 countries and territories in Asia. Moreover, as the world moves toward the age of IoT and 5G, KDDI is taking steps to promote IoT business, such as connected cars, support for companies engaged in global business, and the creation of new value for our society. -

Broadband Infrastructure in the ASEAN-9 Region
BroadbandBroadband InfrastructureInfrastructure inin thethe ASEANASEAN‐‐99 RegionRegion Markets,Markets, Infrastructure,Infrastructure, MissingMissing Links,Links, andand PolicyPolicy OptionsOptions forfor EnhancingEnhancing CrossCross‐‐BorderBorder ConnectivityConnectivity Michael Ruddy Director of International Research Terabit Consulting www.terabitconsulting.com PartPart 1:1: BackgroundBackground andand MethodologyMethodology www.terabitconsulting.com ProjectProject ScopeScope Between late‐2012 and mid‐2013, Terabit Consulting performed a detailed analysis of broadband infrastructure and markets in the 9 largest member countries of ASEAN: – Cambodia – Indonesia – Lao PDR – Malaysia – Myanmar – Philippines – Singapore – Thailand – Vietnam www.terabitconsulting.com ScopeScope (cont(cont’’d.)d.) • The data and analysis for each country included: Telecommunications market overview and analysis of competitiveness Regulation and government intervention Fixed‐line telephony market Mobile telephony market Internet and broadband market Consumer broadband pricing Evaluation of domestic network connectivity International Internet bandwidth International capacity pricing Historical and forecasted total international bandwidth Evaluation of international network connectivity including terrestrial fiber, undersea fiber, and satellite Evaluation of trans‐border network development and identification of missing links www.terabitconsulting.com SourcesSources ofof DataData • Terabit Consulting has completed dozens of demand studies for -

Taiwan Earthquake Fiber Cuts: a Service Provider View
Taiwan Earthquake Fiber Cuts: a Service Provider View Sylvie LaPerrière, Director Peering & Commercial Operations nanog39 – Toronto, Canada – 2007/02/05 www.vsnlinternational.com Taiwan Earthquake fiber cuts: a service provider view Building a backbone from USA to Asia 2006 Asian Backbone | The reconstruction year Earthquake off Taiwan on Dec 26, 2006 The damage(s) Repairing subsea cables Current Situation Lessons for the future www.vsnlinternational.com Page 2 USA to Asia Backbones | Transpac & Intra Asia Cable Systems China-US | Japan-US | PC-1 | TGN-P Combined with Source Flag 2006 APCN-2 C2C EAC FNAL www.vsnlinternational.com Page 3 2006 Spotlight on Asia | Expansion Add Geographies Singapore (2 sites) Tokyo Consolidate presence Hong Kong Upgrade Bandwidth on all Segments Manila Sydney Planning and Design Musts Subsea cables diversity Always favour low latency (RTD …) Improve POP meshing intra-Asia www.vsnlinternational.com Page 4 AS6453 Asia Backbone | Physical Routes Diversity TransPac: C-US | J-US | TGN-P TOKYO Intra-Asia: EAC FNAL | APCN | APCN-2 FLAG FNAL | EAC | SMW-3 Shima EAC J-US HONG KONG EAC LONDON APCN-2 TGN-P APCN-2 Pusan MUMBAI SMW-4 J-US Chongming KUALA APCN-2 PALO ALTO LUMPUR Fangshan MUMBAI CH-US APCN-2 SMW-3 Shantou TIC APCN SMW-3 CH-US LOS ANGELES EAC SINGAPORE APCN-2 EAC LEGEND EXISTING MANILLA IN PROGRESS www.vsnlinternational.com As of December 26 th , 2006 Page 5 South East Asia Cable Systems – FNAL & APCN-2 TOKYO EAC FLAG FNAL Shima EAC J-US HONG KONG EAC LONDON APCN-2 TGN-P APCN-2 Pusan MUMBAI -

DOC-367222A1.Pdf
PUBLIC NOTICE FEDERAL COMMUNICATIONS COMMISSION 445 12th STREET S.W. WASHINGTON D.C. 20554 News media information 202-418-0500 Internet: http://www.fcc.gov (or ftp.fcc.gov) TTY (202) 418-2555 Report No. SCL-00284NS Wednesday September 30, 2020 Non-Streamlined Submarine Cable Landing License Applications Accepted For Filing Unless otherwise specified, the following procedures apply to the applications listed below: The applications listed below have been found, upon initial review, to be acceptable for filing. Pursuant to the Submarine Cable Landing License Act, 47 U.S.C. §§ 34-39, and Executive Order No. 10530, reprinted as amended in 3 U.S.C. § 301, each applicant seeks: (a) the grant of a cable landing licensee; (b) the modification of a cable landing license; and/or (c) the assignment or transfer of control of an interest in a submarine cable landing license. These applications are not subject to the streamlined processing procedures set forth in Section 1.767 of the Commission's rules, 47 CFR § 1.767. Filings relating to this application must be received within 14 days of this notice. Ex parte communications between outside parties and Commission staff concerning these applications are permitted subject to the Commission's rules for "permit-but-disclose proceedings." See 47 C.F.R. § 1.1206. These applications are being coordinated with the Department of State and other Executive Branch agencies pursuant to section 1.767(b) of the Commission's rules, 47 C.F.R. §1.767(b), and consistent with procedures established with the Department of State. See Review of Commission Consideration of Applications under the Cable Landing License Act, IB Docket No. -

Joufsofu!Lpsfb
Attachment 5 XIJUF!QBQFS! JOUFSOFU!LPSFB As the leading agency for national informatization, the National Computerization Agency provides policies and state of the art technology that will guide us to the successful construction of e-Korea. For more than ten the people of National Computerization Agency(NCA) have kept helping the public and private sector to make the best of new and exciting opportunities brought by information and communication technology all over the country. N ational Computerization Age n cy Ministry of Inform ation and Communication XIJUF!QBQFS! JOUFSOFU!LPSFB As the leading agency for national informatization, the National Computerization Agency provides policies and state of the art technology that will guide us to the successful construction of e-Korea. For more than ten the people of National Computerization Agency(NCA) have kept helping the public and private sector to make the best of new and exciting opportunities brought by information and communication technology all over the country. Message From the Minister Korea has established a world-class information and communication infrastructure thanks to the joint efforts of the government and private sectors to build an IT powerhouse during the 1990s. Korea's leading infrastructure in the information and communication sector has enabled Korea to achieve unprecedented developments in all areas including political, economic, social and cultural spheres. As of the end of 2003, 11.18 million households - more than 73% of the total number of households - subscribed to broadband Internet and 29.22 million people - 66% of the total population - had access to the Internet. According to the "ITU 2003 Internet Report," Korea ranks first in terms of broadband Internet penetration rate, has the third largest population of Internet users, and has the fourth highest PC penetration rate in the world. -

Asia-America Gateway (AAG) Cable Network, South Lantau
210mm_FO-English_4194.ai 10/5/2007 11:01:15 AM Asia-America Gateway (AAG) Cable Network, South Lantau PROJECT PROFILE October 2007 TABLE OF CONTENTS 1. Basic Information.....................................................................................................................1 1.1 Project Title........................................................................................................................1 1.2 Purpose and Nature of the Project ....................................................................................1 1.3 Name of Project Proponent ...............................................................................................1 1.4 Location and Scale of Project............................................................................................1 1.5 Cable Route Selection Process.........................................................................................2 1.6 Designated Projects to be Covered by the Project Profile.................................................2 1.7 Name and Telephone Number of Contact Person.............................................................2 2. Outline of Planning, Implementation Programme & Features of Environment..................3 2.1 Project Planning and Implementation................................................................................3 2.2 Programme........................................................................................................................5 2.3 Major Elements of the Surrounding Environment..............................................................6 -

Internet Traffic Expansion Submarine Cable
ntt.com Internet traffic expansion submarine cable May, 2017 NTT Communications Corporation Kohei Kitade Transform your business, transcend expectations with our technologically advanced solutions. Copyright © NTT Communications Corporation. All rights reserved. 1 1. About NTT Copyright © NTT Communications Corporation. All rights reserved. 2 1-1.Introduction of NTT group One of the world’s largest ICT companies (Consolidated revenue of approximately 11.5 trillion JPY) 100% 100% 100% 100% 54.2% 66.2% Long distance & international System and Regional communication, Managed ICT Application Mobile communications ICT Solutions infrastructure integration communications Results for FY2015*1 NTT Europe Operating Revenues : JPY 1,319.1B NTT Com Group Employees*2 NTT America Total : Approx. 21,700 NTT Singapore Global Deployment*2 Ø Offices in 43 countries/regions, 120 cities Other Overseas Subsidiaries Ø Global Network Service in 196 countries/regions Ø Global Tier-1 IP backbone provider, one of the largest in Asia Ø Over 140*3 data centers, strong increase in Asia/US/Europe *In FY2015 *1 Ended on March 31, 2016 *2 As of the end of March 2016 *3 Including planned DC Copyright © NTT Communications Corporation. All rights reserved. 3 1-2. Introduction of NTT Communications Enhance capabilities to fulfill Global Cloud Vision through M&A activities Service Area EMEA US APAC Managed ICT Managed Security Cloud-based Applications Data Center/ Cloud Network / VoIP Copyright © NTT Communications Corporation. All rights reserved. 4 2. Cable expansion over the globe Copyright © NTT Communications Corporation. All rights reserved. 5 2-1. Global Cable systems overview Currently operating 8.7Tbps* of communication cables in total across the globe * Terabit per sec Total Capacity of US – Japan: Total Capacity of 2.4Tbps Asia – Japan: 4.5Tbps * As of June 2016 Copyright © NTT Communications Corporation. -

Maximising Availability of International Connectivity in the Pacific
Thematic reports ITUPublications Regulatory & market environment Maximising availability of international connectivity in the Pacific International Telecommunication Union Telecommunication Development Bureau Place des Nations CH-1211 Geneva 20 Switzerland ISBN: 978-92-61-27451-1 9 7 8 9 2 6 1 2 7 4 5 1 1 Published in Switzerland Geneva, 2018 Maximising availability of connectivity in the Pacific international Photo credits: Shutterstock Maximising availability of international connectivity in the Pacific Acknowledgements This report was prepared by International Telecommunication Union (ITU) expert Matthew O’Rourke and produced by ITU Telecommunication Development Bureau (BDT) in partnership with the Pacific Islands Telecommunications Association and with support from the Government of Australia through Department of Communications and the Arts. ITU would like to acknowledge the information contributed by John Hibbard, Paul McCann, Maui Sanford and delegates from the Pacific island telecommunication ministries, regulators and operators for their contributions to the content of this report. The designations employed and presentation of material in this publication, including maps, do not imply the expression of any opinion whatsoever on the part of ITU concerning the legal status of any country, territory, city or area, or concerning the delimitations of its frontiers or boundaries. ISBN 978-92-61-27441-2 (Paper version) 978-92-61-27451-1 (Electronic version) 978-92-61-27461-0 (EPUB version) 978-92-61-27471-9 (Mobi version) Please consider