Level One Benchmark Windows NT 4.0 Operating Systems V1.0.5
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Since Sliced Bread?
Douglas A. Hamilton WINDOWS NT NT: The Greatest Thing Since Sliced Bread? T'S OFFICIAL. Windows unlike OS/2, is not the only product in the family. Right around the corner is the NT is finally out of the Chicago technology that Microsoft will be using in DOS 7.0 and Windows 4.0. Earli oven. The pricing has est betas for software developers are I scheduled for early fall and products been set and delivery dates based on it should be out in 1994. Chicago is a rewrite of the same Win32 have been promised. Those API (application programming interface) seen on NT. Compared with NT, it leaves promises (back in May) out the security (how many of us need government-certified C2 security on our were that the base system personal machines?), portability to RISC processors and the OS/2 character-mode would ship within 60 days and POSIX subsystems. And it wouldn't surprise me if Unicode support were trimmed out or if the networking were and the Advanced Server version would ship 30 days unbundled. What Chicago leaves in is 32- bit flat virtual memory, preemptive multi later. So there's every chance that by the time you read tasking, threads, pipes and semaphores all the really good stuff in Win32. That be this, there'll be piles of Windows NT packages at your comes Windows 4.0. Subtract the graphi cal user interface and you get DOS 7.0. local computer store. Is there anyone left who wonders why developers are so excited about NT? It's After a false rumor that Microsoft might price NT at not just because NT is expected to do ex tremely well. -

System Requirements for LWC Connect to Learning
System Requirements for LWC Connect to Learning Run the Adobe Connect Diagnostic to see if you meet the Flash, connection, and add-in minimum requirements https://na3cps.adobeconnect.com/common/help/en/support/meeting_test.htm MINIMUM COMPUTER SYSTEM REQUIREMENTS: Windows • 1.4GHz Intel® Pentium® 4 or faster processor (or equivalent) for Microsoft® Windows® XP, Windows 7 or Windows 8 • Windows 8.1 (32-bit/64-bit), Windows 8 (32-bit/64-bit), Windows 7 (32-bit/64-bit), Windows XP • 512MB of RAM (1GB recommended) for Windows XP, Windows 7 or Windows 8 • Microsoft Internet Explorer 8, 9, 10, 11; Mozilla Firefox; Google Chrome • Adobe® Flash® Player 11.2+ Mac OS • 1.83GHz Intel Core™ Duo or faster processor • 512MB of RAM (1GB recommended) • Mac OS X 10.7.4, 10.8, 10.9 • Mozilla Firefox; Apple Safari; Google Chrome • Adobe Flash Player 11.2+ Linux • Ubuntu 12.04; Red Hat Enterprise Linux 6; OpenSuSE 12.2 • No Add-in support for Linux. Users on Linux can attend meetings in the browser. • Mozilla Firefox • Adobe Flash Player 11.2+ Mobile • Apple supported devices: iPhone 5S, iPhone 5, iPhone 4S, iPad with Retina display, iPad 3, iPad 2, iPad mini, and iPod touch (4th & 5th generations) • Apple supported OS versions summary: iOS 6 and higher • Android supported devices: Motorola DROID RAZR MAXX, Motorola Atrix, Motorola Xoom, Samsung Galaxy Tab 2 10.1, Samsung Galaxy S3 & S4, Nexus 7 tablet • Android supported OS versions summary: 2.3.4 and higher 1 ADDITIONAL REQUIREMENTS • Latest version of Adobe Flash Player installed o Download latest version at http://get.adobe.com/flashplayer/ . -

Adobe Introduction to Scripting
ADOBE® INTRODUCTION TO SCRIPTING © Copyright 2007 Adobe Systems Incorporated. All rights reserved. Adobe® Introduction to Scripting NOTICE: All information contained herein is the property of Adobe Systems Incorporated. No part of this publication (whether in hardcopy or electronic form) may be reproduced or transmitted, in any form or by any means, electronic, mechanical, photocopying, recording, or otherwise, without the prior written consent of Adobe Systems Incorporated. The software described in this document is furnished under license and may only be used or copied in accordance with the terms of such license. This publication and the information herein is furnished AS IS, is subject to change without notice, and should not be construed as a commitment by Adobe Systems Incorporated. Adobe Systems Incorporated assumes no responsibility or liability for any errors or inaccuracies, makes no warranty of any kind (express, implied, or statutory) with respect to this publication, and expressly disclaims any and all warranties of merchantability, fitness for particular purposes, and non-infringement of third-party rights. Any references to company names in sample templates are for demonstration purposes only and are not intended to refer to any actual organization. Adobe®, the Adobe logo, Illustrator®, InDesign®, and Photoshop® are either registered trademarks or trademarks of Adobe Systems Incorporated in the United States and/or other countries. Apple®, Mac OS®, and Macintosh® are trademarks of Apple Computer, Inc., registered in the United States and other countries. Microsoft®, and Windows® are either registered trademarks or trademarks of Microsoft Corporation in the United States and other countries. JavaScriptTM and all Java-related marks are trademarks or registered trademarks of Sun Microsystems, Inc. -

Windows NT Architecture Previous Screen Gilbert Held Payoff Windows NT Is a Sophisticated Operating System for Workstations and Network Servers
50-30-19 Windows NT Architecture Previous screen Gilbert Held Payoff Windows NT is a sophisticated operating system for workstations and network servers. This article helps network managers to understand the communications capability of workstations and servers running on Windows NT, and data base administrators to determine the suitability of this platform for a structured query language (SQL) data base server. Introduction Windows NT is a 32-bit, preemptive multitasking operating system that includes comprehensive networking capabilities and several levels of security. Microsoft markets two version of Windows NT: one for workstations—appropriately named Windows NT Workstation—and a second for servers—Windows NT Server. This article, which describes the workings of the NT architecture, collectively references both versions as Windows NT when information is applicable to both versions of the operating system. Similarly, it references a specific version of the operating system when the information presented is specific to either Windows NT Workstation or Windows NT Server. Architecture Windows NT consists of nine basic modules. The relationship of those modules to one another, as well as to the hardware platform on which the operating system runs, is illustrated in Exhibit 1. Windows NT Core Modules Hardware Abstraction Layer The hardware abstraction layer (HAL) is located directly above the hardware on which Windows NT operates. HAL actually represents a software module developed by hardware manufacturers that is bundled into Windows NT to allow it to operate on a specific hardware platform, such as Intel X86, DEC Alpha, or IBM PowerPC. HAL hides the specifics of the hardware platform from the rest of the operating system and represents the lowest level of Windows NT. -

Feature Description
NTLM Feature Description UPDATED: 19 March 2021 NTLM Copyright Notices Copyright © 2002-2021 Kemp Technologies, Inc. All rights reserved. Kemp Technologies and the Kemp Technologies logo are registered trademarks of Kemp Technologies, Inc. Kemp Technologies, Inc. reserves all ownership rights for the LoadMaster and Kemp 360 product line including software and documentation. Used, under license, U.S. Patent Nos. 6,473,802, 6,374,300, 8,392,563, 8,103,770, 7,831,712, 7,606,912, 7,346,695, 7,287,084 and 6,970,933 kemp.ax 2 Copyright 2002-2021, Kemp Technologies, All Rights Reserved NTLM Table of Contents 1 Introduction 4 1.1 Document Purpose 6 1.2 Intended Audience 6 1.3 Related Firmware Version 6 2 Configure NTLM Authentication 7 2.1 Configure Internet Options on the Client Machine 7 2.2 Configure the LoadMaster 11 2.2.1 Enable NTLM Proxy Mode 13 2.2.2 Configure the Server Side SSO Domain 13 2.2.3 Configure the Client Side SSO Domain 15 2.2.4 Configure the Virtual Service 15 2.3 Configure Firefox to Allow NTLM (if needed) 17 2.4 Troubleshooting 18 References 19 Last Updated Date 20 kemp.ax 3 Copyright 2002-2021, Kemp Technologies, All Rights Reserved NTLM 1 Introduction 1 Introduction NT LAN Manager (NTLM) is a Windows Challenge/Response authentication protocol that is often used on networks that include systems running the Windows operating system and Active Directory. Kerberos authentication adds greater security than NTLM systems on a network and provides Windows-based systems with an integrated single sign-on (SSO) mechanism. -
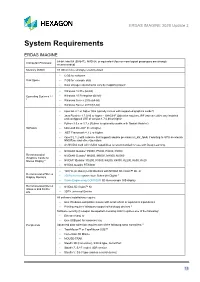
ERDAS IMAGINE 2020 Update 3
ERDAS IMAGINE 2020 Update 3 System Requirements ERDAS IMAGINE 64-bit: Intel 64 (EM64T), AMD 64, or equivalent (four or more logical processors are strongly Computer/ Processor recommended) Memory (RAM) 16 GB or more strongly recommended • 6 GB for software Disk Space • 7 GB for example data • Data storage requirements vary by mapping project1 • Windows 10 Pro (64-bit) Operating Systems 2, 3, • Windows 10 Enterprise (64-bit) 4 • Windows Server 2016 (64-bit) • Windows Server 2019 (64-bit) • OpenGL 2.1 or higher (this typically comes with supported graphics cards 5) • Java Runtime 1.7.0.80 or higher - IMAGINE Objective requires JRE and can utilize any installed and configured JRE of version 1.7.0.80 or higher • Python 3.6.x or 3.7.x (Python is optionally usable with Spatial Modeler) Software • Microsoft DirectX® 9c or higher • .NET Framework 4.7.2 or higher • OpenCL 1.2 with a device that supports double precision (cl_khr_fp64) if wanting to GPU accelerate NNDiffuse and other Operators • An NVIDIA card with CUDA capabilities is recommended for use with Deep Learning. • NVIDIA® Quadro® P6000, P5000, P4000, P2000 Recommended • NVIDIA® Quadro® M6000, M5000, M4000, M2000 Graphics Cards for Stereo Display 6 • NVIDIA® Quadro® K5200, K5000, K4200, K4000, K2200, K600, K420 • NVIDIA Quadro RTX4000 • 120 Hz (or above) LCD Monitors with NVIDIA 3D Vision™ Kit, or Recommended Stereo • 3D PluraView system from Schneider Digital 7 Display Monitors • Vision Engineering CONTOUR 3D stereoscopic GIS display Recommended Stereo • NVIDIA 3D Vision™ Kit Glasses -

Installing the IPM Client on Windows NT
CHAPTER 6 Installing the IPM Client on Windows NT IPM supports running only the IPM client software on a Windows NT system. However, you can run the IPM client on Windows NT with an IPM server that resides on a different operating system platform such as Sun Solaris. The IPM client software can be installed from the CD-ROM or it can be downloaded for installation using the IPM server’s web server. This chapter provides the following information about installing the IPM client software on Windows NT: • Requirements for the IPM Client on Windows NT on page 6-2 • Installing the IPM Client on Windows NT from the CD-ROM on page 6-3 • Installing the IPM Client on Windows NT Using the Web Server on page 6-4 • Verifying the IPM Client Installation on Windows NT on page 6-6 • Modifying the IPM Client Configuration on Windows NT on page 6-7 • Uninstalling the IPM Client on Windows NT on page 6-10 Installing the IPM Client on Windows NT 6-1 Requirements for the IPM Client on Windows NT Requirements for the IPM Client on Windows NT The following hardware and software is required to install the IPM client on a Windows NT system: • Windows NT version 4.0 with Service Pack 3 Note IPM software release 2.0 has not been tested with Windows NT Service Pack 4. • 64 MB RAM minimum (128 MB recommended) • 30 MB hard disk space Before you install the IPM client on a workstation running Windows NT, you should know the following information: • IPM server port number for the Naming server (the default is 44342) • Name of the host where the IPM server software is installed Tips The IPM server port number is obtained using the pkgparam -v CSCOcwbS | grep OSAGENT_PORT command on the Solaris server system. -

Vbscript Programmer’S Reference Third Edition
VBScript Programmer’s Reference Third Edition Adrian Kingsley-Hughes Kathie Kingsley-Hughes Daniel Read Wiley Publishing, Inc. ffirs.indd iii 8/28/07 9:41:21 AM ffirs.indd vi 8/28/07 9:41:22 AM VBScript Programmer’s Reference Third Edition Introduction . xxv Chapter 1: A Quick Introduction to Programming . 1 Chapter 2: What VBScript Is — and Isn’t! . 31 Chapter 3: Data Types . 45 Chapter 4: Variables and Procedures . 83 Chapter 5: Control of Flow . 109 Chapter 6: Error Handling and Debugging . 129 Chapter 7: The Scripting Runtime Objects . 183 Chapter 8: Classes in VBScript (Writing Your Own COM Objects) . 209 Chapter 9: Regular Expressions . 233 Chapter 10: Client-Side Web Scripting . 261 Chapter 11: Windows Sidebars and Gadgets . 287 Chapter 12: Task Scheduler Scripting . 309 Chapter 13: PowerShell . 345 Chapter 14: Super-Charged Client-Side Scripting . 375 Chapter 15: Windows Script Host . 405 Chapter 16: Windows Script Components . 465 Chapter 17: Script Encoding . 489 Chapter 18: Remote Scripting . 509 Chapter 19: HTML Applications . 517 Chapter 20: Server-Side Web Scripting . 535 Chapter 21: Adding VBScript to Your VB and .NET Applications . 569 (Continued) ffirs.indd i 8/28/07 9:41:21 AM Appendix A: VBScript Functions and Keywords . 603 Appendix B: Variable Naming Convention . 675 Appendix C: Coding Conventions . 677 Appendix D: Visual Basic Constants Supported in VBScript . 681 Appendix E: VBScript Error Codes and the Err Object . 687 Appendix F: The Scripting Runtime Library Object Reference . 703 Appendix G: The Windows Script Host Object Model . 715 Appendix H: Regular Expressions . 723 Appendix I: The Variant Subtypes . -

Flashboot User Manual
FlashBoot User Manual © 2015 Mikhail Kupchik Contents 3 Table of Contents Foreword 0 Part I Introduction 5 1 Product................................................................................................................................... Overview 5 2 Why USB................................................................................................................................... Flash Disks? 5 3 Why FlashBoot?................................................................................................................................... 6 4 System................................................................................................................................... Requirements 7 5 Limitations................................................................................................................................... of Demo Version 8 6 Demo Version................................................................................................................................... -> Full Version 8 7 Support................................................................................................................................... & Feedback 8 Part II CD/DVD to USB conversions 9 1 Install ...................................................................................................................................full Win8/8.1/10 -> USB [BIOS mode] 9 2 Install................................................................................................................................... full -

Understanding the Windows SMB NTLM Authentication Weak Nonce Vulnerability
Understanding the Windows SMB NTLM Authentication Weak Nonce Vulnerability Hernan Ochoa Agustin Azubel [email protected] [email protected] Understanding the Windows SMB NTLM Authentication Weak Nonce Vulnerability Presentation goals: ‣ Describe the vulnerability in detail ‣ Explain & demonstrate exploitation • Three different exploitation methods ‣ Clear up misconceptions ‣ Determine vulnerability scope, severity and impact ‣ Share Conclusions BlackHat USA 2010 Understanding the Windows SMB NTLM Authentication Weak Nonce Vulnerability Vulnerability Information ‣ Flaws in Windows’ implementation of NTLM - attackers can access SMB service as authorized user - leads to read/write access to files, SMB shared resources in general and remote code execution ‣ Published February 2010 ‣ CVE-2010-0231, BID 38085 ‣ Advisory with Exploit Code: • http://www.hexale.org/advisories/OCHOA-2010-0209.txt ‣ Addressed by MS10-012 BlackHat USA 2010 Understanding the Windows SMB NTLM Authentication Weak Nonce Vulnerability Why talk about this vulnerability? ‣ Major 14-year old vulnerability affecting Windows Authentication Mechanism! - Basically, all Windows versions were affected (NT4, 2000, XP, 2003, Vista, 2008, 7) - Windows NT 4 released in ∼1996 - Windows NT 3.1 released in ∼1993 (∼17 years ago) - All this time, we assumed it was working correctly.. but it wasn’t... - Flew under the radar... BlackHat USA 2010 Understanding the Windows SMB NTLM Authentication Weak Nonce Vulnerability Why talk about this vulnerability? ‣ Interesting vulnerability, not your common buffer overflow - Issues in the Pseudo-Random Number Generator (PRNG) - Challenge-response protocol implementation issues - Replay attacks - Attack to predict challenges is interesting BlackHat USA 2010 Understanding the Windows SMB NTLM Authentication Weak Nonce Vulnerability Why talk about this vulnerability? ‣ There’s a lesson to be learned.. -
![Chapter 15-70-411FINAL[1]](https://docslib.b-cdn.net/cover/6294/chapter-15-70-411final-1-646294.webp)
Chapter 15-70-411FINAL[1]
Lesson 15: Configuring Service Authentication MOAC 70-411: Administering Windows Server 2012 Overview • Exam Objective 5.1: Configure Service Authentication • Configuring Service Authentication • Managing Service Accounts © 2013 John Wiley & Sons, Inc. 2 Configuring Service Authentication Lesson 15: Configuring Service Authentication © 2013 John Wiley & Sons, Inc. 3 Authentication • Authentication is the act of confirming the identity of a user or system and is an essential part used in authorization when the user or system tries to access a server or network resource. • Two types of authentication that Windows supports are NT LAN Manager (NTLM) and Kerberos. • Kerberos is the default authentication protocol for domain computers. • NTLM is the default authentication protocol for Windows NT, standalone computers that are not part of a domain, and situations in which you authenticate to a server using an IP address. © 2013 John Wiley & Sons, Inc. 4 Understanding NTLM Authentication • NT LAN Manager (NTLM) is a suite of Microsoft security protocols that provides authentication, integrity, and confidentiality to users. • NTLM is an integrated single sign-on mechanism. • NTLM uses a challenge-response mechanism for authentication in which clients are able to prove their identities without sending a password to the server. © 2013 John Wiley & Sons, Inc. 5 Managing Kerberos Kerberos: • Is a computer network authentication protocol, which allows hosts to prove their identity over a non-secure network in a secure manner. • Can provide mutual authentication -

Windows 95 & NT
Windows 95 & NT Configuration Help By Marc Goetschalckx Version 1.48, September 19, 1999 Copyright 1995-1999 Marc Goetschalckx. All rights reserved Version 1.48, September 19, 1999 Marc Goetschalckx 4031 Bradbury Drive Marietta, GA 30062-6165 tel. (770) 565-3370 fax. (770) 578-6148 Contents Chapter 1. System Files 1 MSDOS.SYS..............................................................................................................................1 WIN.COM..................................................................................................................................2 Chapter 2. Windows Installation 5 Setup (Windows 95 only)...........................................................................................................5 Internet Services Manager (Windows NT Only)........................................................................6 Dial-Up Networking and Scripting Tool....................................................................................6 Direct Cable Connection ..........................................................................................................16 Fax............................................................................................................................................17 Using Device Drivers of Previous Versions.............................................................................18 Identifying Windows Versions.................................................................................................18 User Manager (NT Only) .........................................................................................................19