Understanding the Windows SMB NTLM Authentication Weak Nonce Vulnerability
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Windows 7 Operating Guide
Welcome to Windows 7 1 1 You told us what you wanted. We listened. This Windows® 7 Product Guide highlights the new and improved features that will help deliver the one thing you said you wanted the most: Your PC, simplified. 3 3 Contents INTRODUCTION TO WINDOWS 7 6 DESIGNING WINDOWS 7 8 Market Trends that Inspired Windows 7 9 WINDOWS 7 EDITIONS 10 Windows 7 Starter 11 Windows 7 Home Basic 11 Windows 7 Home Premium 12 Windows 7 Professional 12 Windows 7 Enterprise / Windows 7 Ultimate 13 Windows Anytime Upgrade 14 Microsoft Desktop Optimization Pack 14 Windows 7 Editions Comparison 15 GETTING STARTED WITH WINDOWS 7 16 Upgrading a PC to Windows 7 16 WHAT’S NEW IN WINDOWS 7 20 Top Features for You 20 Top Features for IT Professionals 22 Application and Device Compatibility 23 WINDOWS 7 FOR YOU 24 WINDOWS 7 FOR YOU: SIMPLIFIES EVERYDAY TASKS 28 Simple to Navigate 28 Easier to Find Things 35 Easy to Browse the Web 38 Easy to Connect PCs and Manage Devices 41 Easy to Communicate and Share 47 WINDOWS 7 FOR YOU: WORKS THE WAY YOU WANT 50 Speed, Reliability, and Responsiveness 50 More Secure 55 Compatible with You 62 Better Troubleshooting and Problem Solving 66 WINDOWS 7 FOR YOU: MAKES NEW THINGS POSSIBLE 70 Media the Way You Want It 70 Work Anywhere 81 New Ways to Engage 84 INTRODUCTION TO WINDOWS 7 6 WINDOWS 7 FOR IT PROFESSIONALS 88 DESIGNING WINDOWS 7 8 WINDOWS 7 FOR IT PROFESSIONALS: Market Trends that Inspired Windows 7 9 MAKE PEOPLE PRODUCTIVE ANYWHERE 92 WINDOWS 7 EDITIONS 10 Remove Barriers to Information 92 Windows 7 Starter 11 Access -

Introduction to Windows 7
[Not for Circulation] Introduction to Windows 7 This document provides a basic overview of the new and enhanced features of Windows 7 as well as instructions for how to request an upgrade. Windows 7 at UIS Windows 7 is Microsoft’s latest operating system. Beginning in the fall of 2010, UIS will upgrade all classroom and lab PCs to Windows 7. Any new PC that is ordered will automatically come installed with Windows 7. To request an upgrade, contact the Technology Support Center (TSC) at 217/206-6000 or [email protected]. The TSC will evaluate your machine to see if it’s capable of running Windows 7. (Your computer needs a dual core processor and at least 2 GB of RAM.) Please note that University licensing does NOT cover distribution of Windows 7 for personally owned computers. However, it is available for a discounted price via the WebStore at http://webstore.illinois.edu. What to Consider Before Upgrading There is no direct upgrade path from Windows XP to Windows 7. Therefore, the TSC will take your computer, save your files, and install Windows 7 on a clean hard drive. Please budget a couple days for this process. In some cases, you may have older devices that will not work with Windows 7. While many vendors are providing and will continue to provide drivers for their hardware, in some cases, printers, scanners, and other devices that are more than 5 years old may have issues running on Windows 7. To check the compatibility of your devices with Windows 7, visit the Microsoft Windows 7 Compatibility Center at http://www.microsoft.com/windows/compatibility/windows-7/en-us/default.aspx. -
Performing a Windows 7 Upgrade from Windows Vista
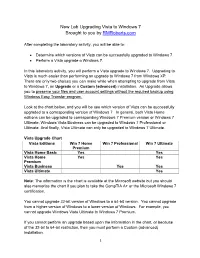
New Lab Upgrading Vista to Windows 7 Brought to you by RMRoberts.com After completing the laboratory activity, you will be able to: Determine which versions of Vista can be successfully upgraded to Windows 7. Perform a Vista upgrade o Windows 7. In this laboratory activity, you will perform a Vista upgrade to Windows 7. Upgrading to Vista is much easier than performing an upgrade to Windows 7 from Windows XP. There are only two choices you can make while when attempting to upgrade from Vista to Windows 7, an Upgrade or a Custom (advanced) installation. An Upgrade allows you to preserve your files and user account settings without the required backup using Windows Easy Transfer program. Look at the chart below, and you will be see which version of Vista can be successfully upgraded to a corresponding version of Windows 7. In general, both Vista Home editions can be upgraded to corresponding Windows 7 Premium version or Windows 7 Ultimate. Windows Vista Business can be upgraded to Windows 7 Professional or Ultimate. And finally, Vista Ultimate can only be upgraded to Windows 7 Ultimate. Vista Upgrade Chart Vista Editions Win 7 Home Win 7 Professional Win 7 Ultimate Premium Vista Home Basic Yes Yes Vista Home Yes Yes Premium Vista Business Yes Yes Vista Ultimate Yes Note: The information is the chart is available at the Microsoft website but you should also memorize the chart if you plan to take the CompTIA A+ or the Microsoft Windows 7 certification. You cannot upgrade 32-bit version of Windows to a 64-bit version. -
Intel® HD Graphics 5300 12 4.4 2.0 Yes Yes
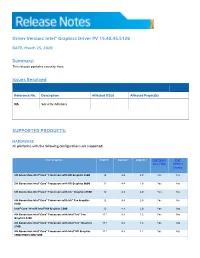
Driver Version: Intel® Graphics Driver PV 15.40.45.5126 DATE: March 25, 2020 Summary: This release contains security fixes. Issues Resolved Reference No. Description Affected OS(s) Affected Project(s) NA Security Advisory SUPPORTED PRODUCTS: HARDWARE All platforms with the following configurations are supported: Intel® Graphics1 DirectX*2 OpenGL* OpenCL* Intel® Quick Intel® Sync Video Wireless Display 5th Generation Intel® Core™ Processors with HD Graphics 5500 12 4.4 2.0 Yes Yes 5th Generation Intel® Core™ Processors with HD Graphics 6000 12 4.4 2.0 Yes Yes 5th Generation Intel® Core™ Processors with Iris™ Graphics 6100 12 4.4 2.0 Yes Yes 5th Generation Intel® Core™ Processors with Iris™ Pro Graphics 12 4.4 2.0 Yes Yes 6200 Intel® Core™ M with Intel® HD Graphics 5300 12 4.4 2.0 Yes Yes 4th Generation Intel® Core™ Processors with Intel® Iris™ Pro 11.1 4.3 1.2 Yes Yes Graphics 5200 4th Generation Intel® Core™ Processors with Intel® Iris™ Graphics 11.1 4.3 1.2 Yes Yes 5100 4th Generation Intel® Core™ Processors with Intel® HD Graphics 11.1 4.3 1.2 Yes Yes 5000/4600/4400/4200 Intel® Pentium® and Celeron® Processors with Intel® HD Graphics 11.1 4.3 1.2 Yes Yes based on 4th and 5th Generation Intel® Core™ Pentium®, Celeron®, and Atom™ processors based on Braswell and 12 4.3 2.0 Yes Yes CherryTrail. SOFTWARE On 4th Generation Intel Core processors and related Pentium/Celeron: • Microsoft Windows 10® 64-bit, 32-bit* *32-bit support is limited to particular SKU’s. -

Feature Description
NTLM Feature Description UPDATED: 19 March 2021 NTLM Copyright Notices Copyright © 2002-2021 Kemp Technologies, Inc. All rights reserved. Kemp Technologies and the Kemp Technologies logo are registered trademarks of Kemp Technologies, Inc. Kemp Technologies, Inc. reserves all ownership rights for the LoadMaster and Kemp 360 product line including software and documentation. Used, under license, U.S. Patent Nos. 6,473,802, 6,374,300, 8,392,563, 8,103,770, 7,831,712, 7,606,912, 7,346,695, 7,287,084 and 6,970,933 kemp.ax 2 Copyright 2002-2021, Kemp Technologies, All Rights Reserved NTLM Table of Contents 1 Introduction 4 1.1 Document Purpose 6 1.2 Intended Audience 6 1.3 Related Firmware Version 6 2 Configure NTLM Authentication 7 2.1 Configure Internet Options on the Client Machine 7 2.2 Configure the LoadMaster 11 2.2.1 Enable NTLM Proxy Mode 13 2.2.2 Configure the Server Side SSO Domain 13 2.2.3 Configure the Client Side SSO Domain 15 2.2.4 Configure the Virtual Service 15 2.3 Configure Firefox to Allow NTLM (if needed) 17 2.4 Troubleshooting 18 References 19 Last Updated Date 20 kemp.ax 3 Copyright 2002-2021, Kemp Technologies, All Rights Reserved NTLM 1 Introduction 1 Introduction NT LAN Manager (NTLM) is a Windows Challenge/Response authentication protocol that is often used on networks that include systems running the Windows operating system and Active Directory. Kerberos authentication adds greater security than NTLM systems on a network and provides Windows-based systems with an integrated single sign-on (SSO) mechanism. -

Students,Faculty & Staff Guide for Windows 7
iM Students,Faculty & Staff Guide for Windows 7 Prepared by Information Technology Division Lehman College, CUNY March 22, 2014 This document was originally prepared by Dickinson College. It was modified and adapted for use at Lehman College with the permission of Dickinson College. Introduction to Windows 7 Table of Contents Windows 7 Taskbar ...................................................................................................................................... 2 Show Desktop ............................................................................................................................................... 2 Start Menu..................................................................................................................................................... 3 Pin ................................................................................................................................................................. 4 Jump Lists ..................................................................................................................................................... 4 Snap .............................................................................................................................................................. 5 Windows Search ........................................................................................................................................... 6 Library (the new My Documents area & more) ........................................................................................... -
![Chapter 15-70-411FINAL[1]](https://docslib.b-cdn.net/cover/6294/chapter-15-70-411final-1-646294.webp)
Chapter 15-70-411FINAL[1]
Lesson 15: Configuring Service Authentication MOAC 70-411: Administering Windows Server 2012 Overview • Exam Objective 5.1: Configure Service Authentication • Configuring Service Authentication • Managing Service Accounts © 2013 John Wiley & Sons, Inc. 2 Configuring Service Authentication Lesson 15: Configuring Service Authentication © 2013 John Wiley & Sons, Inc. 3 Authentication • Authentication is the act of confirming the identity of a user or system and is an essential part used in authorization when the user or system tries to access a server or network resource. • Two types of authentication that Windows supports are NT LAN Manager (NTLM) and Kerberos. • Kerberos is the default authentication protocol for domain computers. • NTLM is the default authentication protocol for Windows NT, standalone computers that are not part of a domain, and situations in which you authenticate to a server using an IP address. © 2013 John Wiley & Sons, Inc. 4 Understanding NTLM Authentication • NT LAN Manager (NTLM) is a suite of Microsoft security protocols that provides authentication, integrity, and confidentiality to users. • NTLM is an integrated single sign-on mechanism. • NTLM uses a challenge-response mechanism for authentication in which clients are able to prove their identities without sending a password to the server. © 2013 John Wiley & Sons, Inc. 5 Managing Kerberos Kerberos: • Is a computer network authentication protocol, which allows hosts to prove their identity over a non-secure network in a secure manner. • Can provide mutual authentication -

Level One Benchmark Windows NT 4.0 Operating Systems V1.0.5
Level One Benchmark Windows NT 4.0 Operating Systems V1.0.5 Copyright 2003, The Center for Internet Security www.cisecurity.org Page 2 of 32 Terms of Use Agreement Background. CIS provides benchmarks, scoring tools, software, data, information, suggestions, ideas, and other services and materials from the CIS website or elsewhere (“Products”) as a public service to Internet users worldwide. Recommendations contained in the Products (“Recommendations”) result from a consensus-building process that involves many security experts and are generally generic in nature. The Recommendations are intended to provide helpful information to organizations attempting to evaluate or improve the security of their networks, systems and devices. Proper use of the Recommendations requires careful analysis and adaptation to specific user requirements. The Recommendations are not in any way intended to be a “quick fix” for anyone’s information security needs. No representations, warranties and covenants. CIS makes no representations, warranties or covenants whatsoever as to (i) the positive or negative effect of the Products or the Recommendations on the operation or the security of any particular network, computer system, network device, software, hardware, or any component of any of the foregoing or (ii) the accuracy, reliability, timeliness or completeness of any Product or Recommendation. CIS is providing the Products and the Recommendations “as is” and “as available” without representations, warranties or covenants of any kind. User agreements. By using the Products and/or the Recommendations, I and/or my organization (“we”) agree and acknowledge that: 1. No network, system, device, hardware, software or component can be made fully secure; 2. -

Microsoft Windows 7 Has Reached Its End of Life Your Critical Operations Are at Risk of Costly Downtime Or Outage
— INDUSTRIAL AUTOMATION Microsoft Windows 7 has reached its End of Life Your critical operations are at risk of costly downtime or outage Beginning January 14, 2020, Microsoft will no longer support Windows 7, Windows Server 2008 and 2008 R2. As a result, many ABB products and services will be impacted. To keep your systems secure, you must invest in a plan to upgrade your control systems. Know what “End of Life” means Understand how it impacts you “End of Life” means Microsoft will discontinue all If you choose to continue using Windows 7, Windows support and will no longer provide software or Server 2008 and 2008 R2 even after support is security updates for Windows 7, Windows Server 2008 discontinued, the operating system will still work. and 2008 R2. The Windows 7 “End of Life” is similar to However, running unsupported operating systems that of previous Microsoft operating systems. will make ABB control systems vulnerable to cyber The lifecycle begins when a product is released and threats. Microsoft will no longer provide technical ends when it’s no longer supported. Knowing key support, software updates and security updates dates in this lifecycle helps you make informed needed to keep your systems secure. Purchasing and decisions about when to update, upgrade or make supporting replacement Windows 7 Workstations other changes to your software. and 2008 Server hardware will become challenging, and affected ABB distributed control systems software will move to the Limited Lifecycle Phase. Version End of support Comments Microsoft -

Upgrading to Windows 7
Upgrading to Windows 7 Windows 7 was designed to upgrade from Windows Vista and not from Windows XP. Additionally, Microsoft will only allow the following upgrade path to Vista users: • Windows Vista Home Premium to Windows 7 Home Premium • Windows Vista Business to Windows 7 Professional • Windows Vista Enterprise to Windows 7 Enterprise • Windows Vista Ultimate to Windows 7 Ultimate ***Any other upgrade path from Vista to Windows 7 will require a clean install*** ***Any upgrade from Windows XP to Windows 7 will require a clean install*** Before proceeding with an installation of Windows 7, you are strongly advised to run Windows 7 Upgrade Advisor. Windows 7 Upgrade Advisor will check the compatibility of your computer with Windows 7 and alert you to any issues that you should address before installing Windows 7. The download is available at http://www.microsoft.com/windows/windows‐7/get/upgrade‐advisor.aspx. 1. From the Microsoft website click on Download the Windows Upgrade Advisor Beta. 2. Click Download and then click Run. 3. A window will display that says “Do you want to run this software?” Click Run. 4. On the Setup Wizard screen, click Next. 5. Click I accept the license terms and click Next. 6. Click Install. When installation is complete, click Close. 7. When you see the screen below, click Start Check. 8. Windows Upgrade Advisor will start checking compatibility. 9. Once the scan is complete, Upgrade Advisor will display any issues that you should be aware of. 10. Click Close to exit Windows Upgrade Advisor. You will be unable to do an in-place upgrade in the following situations: 1. -

Windows 7 Winload OS Loader (Winload.Exe) Security Policy for FIPS 140-2 Validation
Winload OS Loader (winload.exe) Security Policy Windows 7 Winload OS Loader (winload.exe) Security Policy For FIPS 140-2 Validation v 4.3 08/31/11 1 INTRODUCTION .................................................................................................................. 2 1.1 Cryptographic Boundary for WINLOAD.EXE .............................................................................. 2 2 SECURITY POLICY .............................................................................................................. 2 2.1 WINLOAD.EXE Security Policy ..................................................................................................... 2 3 WINLOAD.EXE PORTS AND INTERFACES ....................................................................... 4 3.1 Control Input Interface ................................................................................................................. 4 3.2 Status Output Interface ................................................................................................................ 4 3.3 Data Output Interface ................................................................................................................... 5 3.4 Data Input Interface ...................................................................................................................... 5 4 SPECIFICATION OF ROLES ............................................................................................... 5 4.1 Maintenance Roles ........................................................................................................................ -

Windows Poster 20-12-2013 V3
Microsoft® Discover the Open Specifications technical documents you need for your interoperability solutions. To obtain these technical documents, go to the Open Specifications Interactive Tiles: open specifications poster © 2012-2014 Microsoft Corporation. All rights reserved. http://msdn.microsoft.com/openspecifications/jj128107 Component Object Model (COM+) Technical Documentation Technical Documentation Presentation Layer Services Technical Documentation Component Object Model Plus (COM+) Event System Protocol Active Directory Protocols Overview Open Data Protocol (OData) Transport Layer Security (TLS) Profile Windows System Overview Component Object Model Plus (COM+) Protocol Active Directory Lightweight Directory Services Schema WCF-Based Encrypted Server Administration and Notification Protocol Session Layer Services Windows Protocols Overview Component Object Model Plus (COM+) Queued Components Protocol Active Directory Schema Attributes A-L Distributed Component Object Model (DCOM) Remote Protocol Windows Overview Application Component Object Model Plus (COM+) Remote Administration Protocol Directory Active Directory Schema Attributes M General HomeGroup Protocol Supplemental Shared Abstract Data Model Elements Component Object Model Plus (COM+) Tracker Service Protocol Active Directory Schema Attributes N-Z Peer Name Resolution Protocol (PNRP) Version 4.0 Windows Data Types Services General Application Services Services Active Directory Schema Classes Services Peer-to-Peer Graphing Protocol Documents Windows Error Codes ASP.NET