System Requirements for LWC Connect to Learning
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
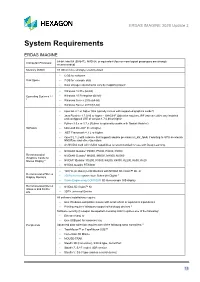
ERDAS IMAGINE 2020 Update 3
ERDAS IMAGINE 2020 Update 3 System Requirements ERDAS IMAGINE 64-bit: Intel 64 (EM64T), AMD 64, or equivalent (four or more logical processors are strongly Computer/ Processor recommended) Memory (RAM) 16 GB or more strongly recommended • 6 GB for software Disk Space • 7 GB for example data • Data storage requirements vary by mapping project1 • Windows 10 Pro (64-bit) Operating Systems 2, 3, • Windows 10 Enterprise (64-bit) 4 • Windows Server 2016 (64-bit) • Windows Server 2019 (64-bit) • OpenGL 2.1 or higher (this typically comes with supported graphics cards 5) • Java Runtime 1.7.0.80 or higher - IMAGINE Objective requires JRE and can utilize any installed and configured JRE of version 1.7.0.80 or higher • Python 3.6.x or 3.7.x (Python is optionally usable with Spatial Modeler) Software • Microsoft DirectX® 9c or higher • .NET Framework 4.7.2 or higher • OpenCL 1.2 with a device that supports double precision (cl_khr_fp64) if wanting to GPU accelerate NNDiffuse and other Operators • An NVIDIA card with CUDA capabilities is recommended for use with Deep Learning. • NVIDIA® Quadro® P6000, P5000, P4000, P2000 Recommended • NVIDIA® Quadro® M6000, M5000, M4000, M2000 Graphics Cards for Stereo Display 6 • NVIDIA® Quadro® K5200, K5000, K4200, K4000, K2200, K600, K420 • NVIDIA Quadro RTX4000 • 120 Hz (or above) LCD Monitors with NVIDIA 3D Vision™ Kit, or Recommended Stereo • 3D PluraView system from Schneider Digital 7 Display Monitors • Vision Engineering CONTOUR 3D stereoscopic GIS display Recommended Stereo • NVIDIA 3D Vision™ Kit Glasses -

Supported Server-Side Configuration
Server and hosting requirements Supported server-side configuration Supported operating systems: Windows 7 Service Pack 1 (32bit or 64bit) Windows 8 or 8.1 (32bit or 64bit) Windows 10 (32bit or 64bit) Windows Server versions: 2008 R2 Service Pack 1, 2012, 2012 R2 We recommend that you install the following components on the computer where you want to run Kentico. If you do not install these components on your computer before installing Kentico, the Installer is capable of downloading and installing them or their suitable alternatives on its own (except for the Visual Studio built-in server). In such cases, your computer must be connected to the Internet. Microsoft .NET Framework 4.5 or 4.6. Microsoft Internet Information Services (see the table below) or Visual Studio 2012/2013/2015 built-in web server. Microsoft SQL Server 2008 R2, 2012, 2014 (including the free SQL Server Express Edition 2008 R2/2012/2014). The collation set for the SQL server must be case-insensitive. Internet Information Services overview The following table lists instructions on how to install different versions of IIS on different operating systems. Internet Information Services version Operating system Details and installation instructions IIS 7.0 Windows Vista not supported Windows Server 2008 IIS 7.5 Windows 7 SP1 IIS 7 Installation and Deployment Windows Server 2008 R2 SP1 IIS 8.0 Windows 8 Installing IIS on Windows Server 2012 Windows Server 2012 IIS 8.5 Windows 8.1 Installing IIS 8.5 Windows Server 2012 R2 IIS 10 Windows 10 Same process as IIS 8+ For the Kentico -

Models Step 1: Identify Which Version of the Windows Phone Operating
Nokia Lumia – All Models (Excluding models 710 and 800) Step 1: Identify which version of the Windows Phone operating system is installed on your phone: 1. Go to your App list. 2. From there, tap “Settings” > “About” > “More info”. 3. The “Software” section indicates which version of the Windows Phone operating system is in use. a. If your phone is currently running Windows Phone 7, proceed to page 2 for instructions on how to wipe your device. b. If your phone is currently running Windows Phone 8, 8.1, or 10, proceed to page 3 for instructions on how to wipe your device. ______________________________________________________________________________ Nokia Lumia - Tous les modèles (À l'exclusion des modèles 710 et 800) Étape 1: Déterminer la version du système d'exploitation Windows Phone installée sur votre téléphone: 1. Accédez à votre liste d’applications. 2. Presse « Paramètres » > « À propos » > « Plus d'info ». 3. La section « Logiciel » indique le nom de la version du système d'exploitation Windows Phone. a. Si votre téléphone utilise actuellement Windows Phone 7, aller à la page 2 pour obtenir des instructions sur la façon de réinitialiser votre téléphone. b. Si votre téléphone utilise actuellement Windows Phone 8, 8.1, ou 10, aller à la page 4 pour obtenir des instructions sur la façon de réinitialiser votre téléphone. Nokia Lumia (Windows 7.5) Model Numbers: 610, 900 The following instruction will give you all the information you need to remove your personal information from your phone. Before recycling your device please also remember to: The account for the device has been fully paid and service has been deactivated. -

Flashboot User Manual
FlashBoot User Manual © 2015 Mikhail Kupchik Contents 3 Table of Contents Foreword 0 Part I Introduction 5 1 Product................................................................................................................................... Overview 5 2 Why USB................................................................................................................................... Flash Disks? 5 3 Why FlashBoot?................................................................................................................................... 6 4 System................................................................................................................................... Requirements 7 5 Limitations................................................................................................................................... of Demo Version 8 6 Demo Version................................................................................................................................... -> Full Version 8 7 Support................................................................................................................................... & Feedback 8 Part II CD/DVD to USB conversions 9 1 Install ...................................................................................................................................full Win8/8.1/10 -> USB [BIOS mode] 9 2 Install................................................................................................................................... full -

Level One Benchmark Windows NT 4.0 Operating Systems V1.0.5
Level One Benchmark Windows NT 4.0 Operating Systems V1.0.5 Copyright 2003, The Center for Internet Security www.cisecurity.org Page 2 of 32 Terms of Use Agreement Background. CIS provides benchmarks, scoring tools, software, data, information, suggestions, ideas, and other services and materials from the CIS website or elsewhere (“Products”) as a public service to Internet users worldwide. Recommendations contained in the Products (“Recommendations”) result from a consensus-building process that involves many security experts and are generally generic in nature. The Recommendations are intended to provide helpful information to organizations attempting to evaluate or improve the security of their networks, systems and devices. Proper use of the Recommendations requires careful analysis and adaptation to specific user requirements. The Recommendations are not in any way intended to be a “quick fix” for anyone’s information security needs. No representations, warranties and covenants. CIS makes no representations, warranties or covenants whatsoever as to (i) the positive or negative effect of the Products or the Recommendations on the operation or the security of any particular network, computer system, network device, software, hardware, or any component of any of the foregoing or (ii) the accuracy, reliability, timeliness or completeness of any Product or Recommendation. CIS is providing the Products and the Recommendations “as is” and “as available” without representations, warranties or covenants of any kind. User agreements. By using the Products and/or the Recommendations, I and/or my organization (“we”) agree and acknowledge that: 1. No network, system, device, hardware, software or component can be made fully secure; 2. -

Lumia with Windows 10 Mobile User Guide
User Guide Lumia with Windows 10 Mobile Issue 1.1 EN-US About this user guide This guide is the user guide for your software release. Important: For important information on the safe use of your device and battery, read “For your safety” and “Product and safety info” in the printed or in-device user guide, or at www.microsoft.com/mobile/support before you take the device into use. To find out how to get started with your new device, read the printed user guide. For the online user guidance, videos, even more information, and troubleshooting help, go to support.microsoft.com, and browse to the instructions for Windows phones. You can also check out the support videos at www.youtube.com/lumiasupport. Moreover, there's a user guide in your phone – it's always with you, available when needed. To find answers to your questions and to get helpful tips, tap Lumia Help+Tips. If you’re new to Lumia, check out the section for new users. For info on Microsoft Privacy Statement, go to aka.ms/privacy. © 2016 Microsoft Mobile. All rights reserved. 2 User Guide Lumia with Windows 10 Mobile Contents For your safety 5 People & messaging 64 Get started 6 Calls 64 Turn the phone on 6 Contacts 68 Lock the keys and screen 7 Social networks 73 Charge your phone 7 Messages 74 Your first Lumia? 10 Email 78 Learn more about your phone 10 Camera 83 Set up your phone 10 Open your camera quickly 83 Update your apps 11 Camera basics 83 Explore your tiles, apps, and settings 12 Advanced photography 86 Navigate inside an app 14 Photos and videos 88 Use the touch screen -
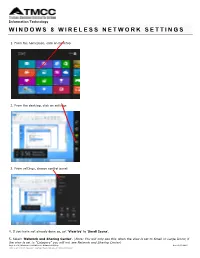
Windows 8 Wireless Network Settings
Information Technology WINDOWS 8 WIRELESS NETWORK SETTINGS 1. From the homepage, click on Desktop 2. From the desktop, click on settings 3. From settings, choose control panel 4. If you have not already done so, set ‘View by’ to ‘Small Icons’. 5. Select ‘Network and Sharing Center’. (Note: You will only see this when the view is set to Small or Large Icons; if the view is set to “Category” you will not see Network and Sharing Center) Page 1 of 6; Windows 8 OS Wireless Network Settings Rev.: 2/5/2013 TMCC is an EEO/AA institution. See http://eeo.tmcc.edu for more information. 6. Click ‘Set up a new connection or network’. 7. Click ‘Manually connect to a wireless network’. Then click ‘Next’. 8. Fill in the appropriate Network name: a. For Students: TMCC-Student b. For Staff: TMCC-Admin Security 9. Select ‘WPA2-Enterprise’ from the security type drop-down box. 10. Select ‘AES’ from the encryption type drop-down box. 11. Leave the Security key field blank. 12. Make sure ‘Connect even if the network is not broadcasting’ box is checked. 13. Below is an example of what is should look like for students: 14. Click ‘Next’. 15. Click ‘Change connection settings’ 16. Make sure both 'Connect automatically when this network is in range' and 'Connect even if the network is not broadcasting its name (SSID)' are selected. Page 2 of 6; Windows 8 OS Wireless Network Settings Rev.: 2/5/2013 TMCC is an EEO/AA institution. See http://eeo.tmcc.edu for more information. -
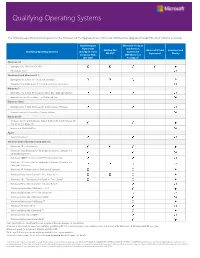
Qualifying Operating Systems
Qualifying Operating Systems The following operating systems qualify for the Windows 10 Pro Upgrade and/or Windows 10 Enterprise Upgrade through Microsoft Volume Licensing. New Enterprise Microsoft Products Agreement and Services Existing EA/ Microsoft Cloud Academic and Qualifying Operating Systems (EA)/Open Value Agreement OV-CW2 Agreement Charity Company-Wide (MPSA)/Select (OV-CW)1 Plus/Open3 Windows 10 4 Enterprise (N, KN) , Pro (N, KN) Education, Home Windows 8 and Windows 8.1 Enterprise (N, K, KN), Pro (N, K, KN, diskless) Windows 8 and Windows 8.1 (including Single Language) Windows 7 Enterprise (N, K, KN), Professional (N, K, KN, diskless), Ultimate Home Premium, Home Basic, or Starter Edition Windows Vista Enterprise (N, K, KN), Business (N, K, KN, Blade), Ultimate Home Premium, Home Basic, Starter Edition Windows XP Professional (N, K, KN, Blade), Tablet Edition (N, K, KN, Blade), XP Pro N, XP Pro Blade PC Home and Starter Edition Apple Apple Macintosh Windows Embedded Operating Systems Windows 10 IoT Enterprise Windows Vista Business for Embedded Systems, Ultimate for Embedded Systems Windows 2000 Professional for Embedded Systems Windows 7 Professional for Embedded Systems, Ultimate for Embedded Systems Windows XP Professional for Embedded Systems Windows Embedded 8 and 8.1 Pro, Industry Pro Windows 10 IoT Enterprise for Retail or Thin Clients5 5 Windows Embedded 8 and 8.1 Industry Retail Windows Embedded POSReady 7 Pro5 5 Windows Embedded for Point of Service Windows Embedded POSReady 20095 5 Windows Embedded POSReady 7 5 Windows XP Embedded Windows Embedded Standard 75 5 Windows Embedded 2009 5 Windows Embedded 8 Standard 1Also applicable to Qualified Devices acquired through merger or acquisition. -

Windows 10: Considered Harmful
Windows 10: Considered Harmful 26 August, 2016 Last Updated: 25 September 2016 Previously I made a series of articles against Windows 10, consisting of basic explanation, open letters, and even a long-winded chance.org petition. However, I have come to realize that these various things could be better as one page rather than fragments across my website. On this page I hope to explain why the Windows 10 system is evil and also include why Windows as a whole is Considered Harmful . Sources to unreferenced items in this article can be found in the various resource links on the bottom of the page. Information can also be found in the photographs shown and with a simple web search. The primary reason against the Windows 10 system is an obvious one. The system is designed to be a system that data-mines the user. This is proven time and time again. Using a tool such as wireshark, one can clearly see that it makes encrypted connections to a variety of Microsoft servers. This uses a very weak RSA encryption that can be broken in under a minute. When a user successfully decrypted the encrypted data, he simply converted the decrypted ``.bin'' extension to ``.png'' and opened them. The image files were screen- shots of him installing the RSA decryptor tool. This was in a VM and was a fresh install. In addition to this, another user in Australia also monitored the odd connection but did not decrypt it. He noticed this when he opened a photograph in the Windows Photo App. -

Introduction to Windows 8
[Not for Circulation] Introduction to Windows 8 Windows 8 is a completely redesigned operating system developed from the ground up with touchscreen use in mind as well as near instant-on capabilities that enable a Windows 8 PC to load and start up in a matter of seconds rather than in minutes. Windows 8 Vocabulary Apps - "App" is another word for program. In Windows 8 , some apps come built-in to Windows, and there are even more available in the Windows Store. Live Tiles – Interactive apps that take advantage of Internet access to provide real-time updates. Hot Corners - The corners on your screen are hot corners and give you access to different Windows features. Charms Bar - Contains a set of buttons and commands that control the application you are currently using, as well as provide options for system settings. The Charms bar includes many of the features previously available from the Start button. Metro-style - New layout of Windows 8 with tiles and apps instead of the standard desktop with a Start button. Mobile - Windows 8 is designed for mobile devices, such as tablets. You can also sign into your Windows 8 screen anywhere using your Live ID, and your customized settings travel with you. Touch-centric – Touch is a key element in Windows 8; however, a traditional mouse and keyboard can be used as well. Speed Bump - The small gap between groups of tiles. Speed bumps can be added to create new groups. Where Do I Find: Shut down - Move your mouse to the upper right corner of the screen, and move your mouse down until you see your charms appear. -

Tapani Havia
Tapani Havia Microsoft Windows Server 2012 Centrally Managed Basic Services for Microsoft Windows 8 Clients Helsinki Metropolia University of Applied Sciences Bachelor of Engineering Information Technology Bachelor’s Thesis 14th May 2013 PREFACE This Bachelor’s Thesis is the outcome of my professional knowledge of the Microsoft Windows Server 2012 centrally managed basic services. I wish to thank my instructors Kari Järvi and Jonita Martelius for their invaluable help and support while writing the study. Last but not least I wish to thank my wife Mia Havia for her endless patience while writing the study. Espoo, May 14, 2013 Tapani Havia Abstract Author(s) Tapani Havia Title Microsoft Windows Server 2012 Number of Pages 153 pages + 10 appendices Date 14th May 2013 Degree Bachelor of Engineering Degree Program Information Technology Specialization option Data Networks Instructor(s) Kari Järvi, Principal Lecturer Microsoft published the latest operating system versions; Windows Server 2012 and Windows 8 last autumn. It was the correct time to create a test environment and test how basic services and their centralized remote management could be done nowadays. The purpose was to come up with as versatile an environment as possible which any person interested in the topic could do and continue to the desired direction. The initial plan was to create the test environment in one computer virtually. The environment was done with redundancy of basic services without Network Load Balancing or Failover Clustering features. Finally, the environment within the framework of the study included 11 virtual servers and three virtual workstations. For the host computer’s operating system was chosen the Windows Server 2012 Datacenter edition and the needed hypervisor software was chosen between Microsoft Hyper-V and VMware Workstation 9, the environment was done with VMware. -

Bakalarska Prace-Petrpekny.Pdf
Západočeská univerzita v Plzni Fakulta filozofická Bakalářská práce Kauza PRISM Petr Pěkný Plzeň 2015 Západočeská univerzita v Plzni Fakulta filozofická Katedra politologie a mezinárodních vztahů Studijní program Mezinárodní teritoriální studia Studijní obor Mezinárodní vztahy – britská a americká studia Bakalářská práce Kauza PRISM Petr Pěkný Vedoucí práce: doc. PhDr. Přemysl Rosůlek, Ph.D. Katedra politologie a mezinárodních vztahů Fakulta filozofická Západočeské univerzity v Plzni Plzeň 2015 Prohlašuji, ţe jsem práci zpracoval samostatně a pouţil jen uvedených pramenů a literatury. Plzeň, duben 2015 ……………………… Chtěl bych poděkovat vedoucímu své bakalářské práce doc. PhDr. Přemyslu Rosůlkovi, Ph.D. za odborné vedení, věcné připomínky, za pomoc a rady při jejím zpracováním. Obsah SEZNAM POUŢITÝCH ZKRATEK .................................................... 1 ÚVOD ......................................................................................... 1 2 INTERNETOVÉ SOUKROMÍ ...................................................... 4 2.1 Soukromí na internetu v digitální éře......................................... 4 2.1.1 Sociální sítě .......................................................................... 5 2.2 Potencionální hrozby ohroţující internetové soukromí ........... 5 2.2.1 Zadní vrátka v hardwaru a softwaru ..................................... 6 2.3 Technologie a soukromí .............................................................. 7 2.3.1 Cloud Computing .................................................................