Installing the IPM Client on Windows NT
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Since Sliced Bread?
Douglas A. Hamilton WINDOWS NT NT: The Greatest Thing Since Sliced Bread? T'S OFFICIAL. Windows unlike OS/2, is not the only product in the family. Right around the corner is the NT is finally out of the Chicago technology that Microsoft will be using in DOS 7.0 and Windows 4.0. Earli oven. The pricing has est betas for software developers are I scheduled for early fall and products been set and delivery dates based on it should be out in 1994. Chicago is a rewrite of the same Win32 have been promised. Those API (application programming interface) seen on NT. Compared with NT, it leaves promises (back in May) out the security (how many of us need government-certified C2 security on our were that the base system personal machines?), portability to RISC processors and the OS/2 character-mode would ship within 60 days and POSIX subsystems. And it wouldn't surprise me if Unicode support were trimmed out or if the networking were and the Advanced Server version would ship 30 days unbundled. What Chicago leaves in is 32- bit flat virtual memory, preemptive multi later. So there's every chance that by the time you read tasking, threads, pipes and semaphores all the really good stuff in Win32. That be this, there'll be piles of Windows NT packages at your comes Windows 4.0. Subtract the graphi cal user interface and you get DOS 7.0. local computer store. Is there anyone left who wonders why developers are so excited about NT? It's After a false rumor that Microsoft might price NT at not just because NT is expected to do ex tremely well. -

Windows NT Architecture Previous Screen Gilbert Held Payoff Windows NT Is a Sophisticated Operating System for Workstations and Network Servers
50-30-19 Windows NT Architecture Previous screen Gilbert Held Payoff Windows NT is a sophisticated operating system for workstations and network servers. This article helps network managers to understand the communications capability of workstations and servers running on Windows NT, and data base administrators to determine the suitability of this platform for a structured query language (SQL) data base server. Introduction Windows NT is a 32-bit, preemptive multitasking operating system that includes comprehensive networking capabilities and several levels of security. Microsoft markets two version of Windows NT: one for workstations—appropriately named Windows NT Workstation—and a second for servers—Windows NT Server. This article, which describes the workings of the NT architecture, collectively references both versions as Windows NT when information is applicable to both versions of the operating system. Similarly, it references a specific version of the operating system when the information presented is specific to either Windows NT Workstation or Windows NT Server. Architecture Windows NT consists of nine basic modules. The relationship of those modules to one another, as well as to the hardware platform on which the operating system runs, is illustrated in Exhibit 1. Windows NT Core Modules Hardware Abstraction Layer The hardware abstraction layer (HAL) is located directly above the hardware on which Windows NT operates. HAL actually represents a software module developed by hardware manufacturers that is bundled into Windows NT to allow it to operate on a specific hardware platform, such as Intel X86, DEC Alpha, or IBM PowerPC. HAL hides the specifics of the hardware platform from the rest of the operating system and represents the lowest level of Windows NT. -

Level One Benchmark Windows NT 4.0 Operating Systems V1.0.5
Level One Benchmark Windows NT 4.0 Operating Systems V1.0.5 Copyright 2003, The Center for Internet Security www.cisecurity.org Page 2 of 32 Terms of Use Agreement Background. CIS provides benchmarks, scoring tools, software, data, information, suggestions, ideas, and other services and materials from the CIS website or elsewhere (“Products”) as a public service to Internet users worldwide. Recommendations contained in the Products (“Recommendations”) result from a consensus-building process that involves many security experts and are generally generic in nature. The Recommendations are intended to provide helpful information to organizations attempting to evaluate or improve the security of their networks, systems and devices. Proper use of the Recommendations requires careful analysis and adaptation to specific user requirements. The Recommendations are not in any way intended to be a “quick fix” for anyone’s information security needs. No representations, warranties and covenants. CIS makes no representations, warranties or covenants whatsoever as to (i) the positive or negative effect of the Products or the Recommendations on the operation or the security of any particular network, computer system, network device, software, hardware, or any component of any of the foregoing or (ii) the accuracy, reliability, timeliness or completeness of any Product or Recommendation. CIS is providing the Products and the Recommendations “as is” and “as available” without representations, warranties or covenants of any kind. User agreements. By using the Products and/or the Recommendations, I and/or my organization (“we”) agree and acknowledge that: 1. No network, system, device, hardware, software or component can be made fully secure; 2. -

Windows 95 & NT
Windows 95 & NT Configuration Help By Marc Goetschalckx Version 1.48, September 19, 1999 Copyright 1995-1999 Marc Goetschalckx. All rights reserved Version 1.48, September 19, 1999 Marc Goetschalckx 4031 Bradbury Drive Marietta, GA 30062-6165 tel. (770) 565-3370 fax. (770) 578-6148 Contents Chapter 1. System Files 1 MSDOS.SYS..............................................................................................................................1 WIN.COM..................................................................................................................................2 Chapter 2. Windows Installation 5 Setup (Windows 95 only)...........................................................................................................5 Internet Services Manager (Windows NT Only)........................................................................6 Dial-Up Networking and Scripting Tool....................................................................................6 Direct Cable Connection ..........................................................................................................16 Fax............................................................................................................................................17 Using Device Drivers of Previous Versions.............................................................................18 Identifying Windows Versions.................................................................................................18 User Manager (NT Only) .........................................................................................................19 -

Windows 10: Considered Harmful
Windows 10: Considered Harmful 26 August, 2016 Last Updated: 25 September 2016 Previously I made a series of articles against Windows 10, consisting of basic explanation, open letters, and even a long-winded chance.org petition. However, I have come to realize that these various things could be better as one page rather than fragments across my website. On this page I hope to explain why the Windows 10 system is evil and also include why Windows as a whole is Considered Harmful . Sources to unreferenced items in this article can be found in the various resource links on the bottom of the page. Information can also be found in the photographs shown and with a simple web search. The primary reason against the Windows 10 system is an obvious one. The system is designed to be a system that data-mines the user. This is proven time and time again. Using a tool such as wireshark, one can clearly see that it makes encrypted connections to a variety of Microsoft servers. This uses a very weak RSA encryption that can be broken in under a minute. When a user successfully decrypted the encrypted data, he simply converted the decrypted ``.bin'' extension to ``.png'' and opened them. The image files were screen- shots of him installing the RSA decryptor tool. This was in a VM and was a fresh install. In addition to this, another user in Australia also monitored the odd connection but did not decrypt it. He noticed this when he opened a photograph in the Windows Photo App. -

What Is Windows NT
What is Windows NT Windows NT is worked out on the base OS/2 NT. OS/2 is developed by Microsoft and IBM together. It has Microsoft OS/2 NT and IBM OS/2 two types. The two firms part on bad terms after cooperation. IBM continues to provide OS/2 version but Microsoft renames its OS/2 NT Wndows NT. That is the first generation of Windows NT 3.1. Windows NT is pure 32-bit operating system. It employs advanced NT core technology. NT stands for New Technology. --Source from http://www.powerdatarecovery.com/data-recovery/windows-nt.html Microsoft Windows NT (Network Termination) is a kind of operating system developed by Microsoft. Microsoft hires a few staffs from Digital Equipment Corporation to develop this new system. Many features of this system have showed the early conceptions with VMS, RSX-11, and DEC. Windows NT is the operating system for the workstation, networkserver, and large computer. It can also be used as PC operating system. It has a close relationship with communication services and provides file print service. It can run client/server applications, and it has built-in Internet/Intranet function. It is gradually becoming the standard platform of enterprise network. This article mainly introduces Wondows NT Server4.0. Features 1. 32-bit operating system. Multiple guide function. It is compatible with other operating systems. 2. It realizes the "preemptive" multitask and multithreading operation. 3. It uses SMP technology and supports multi-CPU system. 4. It supports CISC (such as Intel system) and RISC (such as Power PC, R440) and all kinds of hardware platform. -

An Introduction to Windows Operating System
EINAR KROGH AN INTRODUCTION TO WINDOWS OPERATING SYSTEM Download free eBooks at bookboon.com 2 An Introduction to Windows Operating System 2nd edition © 2017 Einar Krogh & bookboon.com ISBN 978-87-403-1935-4 Peer review by Høgskolelektor Lars Vidar Magnusson, Høgskolen i Østfold Download free eBooks at bookboon.com 3 AN INTRODUCTION TO WINDOWS OPERATING SYSTEM CONTENTS CONTENTS Introduction 9 1 About Windows history 10 1.1 MS-DOS 10 1.2 The first versions of Windows 11 1.3 Windows NT 12 1.4 Windows versions based on Windows NT 13 1.5 Windows Server 15 1.6 Control Questions 17 2 The tasks of an operating system 18 2.1 About the construction of computers 19 2.2 Central tasks for an operating system 20 2.3 Control Questions 22 �e Graduate Programme I joined MITAS because for Engineers and Geoscientists I wanted real responsibili� www.discovermitas.comMaersk.com/Mitas �e Graduate Programme I joined MITAS because for Engineers and Geoscientists I wanted real responsibili� Maersk.com/Mitas Month 16 I wwasas a construction Month 16 supervisorI wwasas in a construction the North Sea supervisor in advising and the North Sea Real work helpinghe foremen advising and IInternationalnternationaal opportunities ��reeree wworkoro placements solves Real work problems helpinghe foremen IInternationalnternationaal opportunities ��reeree wworkoro placements solves problems Download free eBooks at bookboon.com Click on the ad to read more 4 AN INTRODUCTION TO WINDOWS OPERATING SYSTEM CONTENTS 3 Some concepts and terms of the Windows operating system 23 3.1 -

Windows Vista Short History of Windows
Windows Vista The good and bad behind the hype Short History of Windows • 1983 - Bill Gates announces Microsoft will begin work on an OS with a Graphical User Interface. • 1984 - Apple airs a 30 sec commercial during the super bowl announcing the release of the Macintosh, the first (successful) GUI based computer. • 1985 - Windows 1.0 was first released in Nov. The release was considered a flop. • 1990 - Windows 3.0 is released with a substantial upgrade to the interface over Windows 1 and 2. This is the first commercially successful version of Windows. • 1993 - Windows NT 3.1 is released and is the first Microsoft OS not based in DOS. Microsoft would release separate versions of NT along with their DOS counterparts untill Windows XP • 1995 - Windows 95 is released as the first native 32 bit OS. Microsoft originally wanted to merge the NT and DOS platforms but due to backward compatibility issues and lacking hardware support of NT, Microsoft left NT out. 1 Short History of Windows • 1998 - Windows 98 is released. Microsoft integrates its web browser in the GUI and file manager. This opens up the floodgates for hackers to use the internet to infiltrate an entire computer or network. This move to integrate IE in to windows prompts a flood of anti-trust lawsuits from the US and several countries. Some cases are still active today. • 2000 - Windows 2000 is released. As with Windows 95, Microsoft planed Windows 2000 to be the bridge between the NT and DOS based OS’s, but was unsuccessful in that regard due to compatibility issues. -

Windows NT/SAM User Authentica- Tion and Titan FTP Server Instructions for Configuring Titan FTP Server to Leverage Windows NT/SAM for User Authentica- Tion
2018 Windows NT/SAM User Authentica- tion and Titan FTP Server Instructions for configuring Titan FTP Server to leverage Windows NT/SAM for user authentica- tion. QuickStart Guide © 2018 South River Technologies, Inc. All Rights Reserved Configuring Windows NT/SAM for User Authentication Configuring Windows NT/SAM for User Authentication The following instructions will help you to set up Titan FTP for user authentication with Microsoft Windows NT Security Accounts Manager (SAM). If you need additional assistance, the Titan FTP User Guide is avail- able online at http://www.southrivertech.com/product-support/titan-ftp-server/, and the knowledge base can be found at http://srthelpdesk.com/. Creating a Dedicated Windows User Account To use Windows NT/SAM (Security Accounts Manager) for user authentication with Titan FTP, a special Windows User Account must be created, which will be dedicated to Titan. Please see the Appendix for instructions on how to create a special Windows User Account for use with Titan FTP. The Titan Service will use this account to authenticate FTP clients connecting to the system; FTP clients will not use this account to connect to the server. This account will have permissions not usually available to other Windows User accounts. To use this account, the Titan Service will need to be modified. Configuring the Titan Administrator Use the following steps to configure a new server to utilize Windows NT/SAM as the user authentication engine. 1. Run the Titan Administration Utility and start the New Server Wizard. 2. Walk through the Server Wizard, selecting the desired options, until you reach the User Authenti- cation Database page. -

5686E Installation Map English.Fm
Installation Step Five: Install the Modem Drivers Congratulations. You have successfully completed the installation procedure. Please register your 56K Faxmodem at www.usr.com/productreg/. Windows Vista, XP and 2000 Step One: Prepare for Installation Windows NT 4.0 56K Faxmodem You must be logged in as an administrator in order to properly install the new 1. Uninstall all other modems that are installed on your computer. For instructions, modem. You must be logged in as an administrator in order to properly install the new refer to the documentation for your previous modem. When you turn your computer on, Windows automatically detects the modem and modem. 2. Unplug all telephone and power cords connected to your previous modem(s). installs a generic driver. You will need to update it with the USRobotics driver to sup- When you turn your computer on, Windows automatically detects the modem and 3. Shut down your computer and power it off. port full V.92 features and the additional software tools for your modem. installs a generic driver. You will need to update it with the USRobotics driver to sup- port full V.92 features and the additional software tools for your modem. 4. Locate the serial port on the back of your computer. To find the serial port, look 1. Insert the USRobotics Installation CD-ROM to install the for a port labeled COM, MODEM, RS-232, , or SERIAL. Do not use the USRobotics driver. 1. Insert the USRobotics Installation CD-ROM to install the AUX, GAME, LPT, or PARALLEL ports. If the CD doesn't start automatically, start it manually as follows: USRobotics driver. -
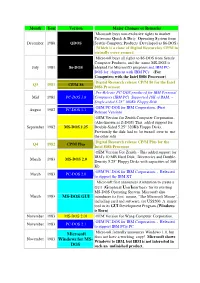
Microsoft Windows for MS
Month Year Version Major Changes or Remarks Microsoft buys non-exclusive rights to market Pattersons Quick & Dirty Operating System from December 1980 QDOS Seattle Computer Products (Developed as 86-DOS) (Which is a clone of Digital Researches C P/M in virtually every respect) Microsoft buys all rights to 86-DOS from Seattle Computer Products, and the name MS-DOS is July 1981 86-DOS adopted for Microsoft's purposes and IBM PC- DOS for shipment with IBM PCs (For Computers with the Intel 8086 Processor) Digital Research release CP/M 86 for the Intel Q3 1981 CP/M 86 8086 Processer Pre-Release PC-DOS produced for IBM Personal Mid 1981 PC-DOS 1.0 Computers (IBM PC) Supported 16K of RAM, ~ Single-sided 5.25" 160Kb Floppy Disk OEM PC-DOS for IBM Corporation. (First August 1982 PC-DOS 1.1 Release Version) OEM Version for Zenith Computer Corporation.. (Also known as Z-DOS) This added support for September 1982 MS-DOS 1.25 Double-Sided 5.25" 320Kb Floppy Disks. Previously the disk had to be turned over to use the other side Digital Research release CP/M Plus for the Q4 1982 CP/M Plus Intel 8086 Processer OEM Version For Zenith - This added support for IBM's 10 MB Hard Disk, Directories and Double- March 1983 MS-DOS 2.0 Density 5.25" Floppy Disks with capacities of 360 Kb OEM PC-DOS for IBM Corporation. - Released March 1983 PC-DOS 2.0 to support the IBM XT Microsoft first announces it intention to create a GUI (Graphical User Interface) for its existing MS-DOS Operating System. -

CIS Microsoft Windows Server 2012 Benchmarkv1.0.0
CIS Microsoft Windows Server 2012 Benchmarkv1.0.0 01-31-2013 The CIS Security Benchmarks division provides consensus-oriented information security products, services, tools, metrics, suggestions, and recommendations (the “SB Products”) as a public service to Internet users worldwide. Downloading or using SB Products in any way signifies and confirms your acceptance of and your binding agreement to these CIS Security Benchmarks Terms of Use. CIS SECURITY BENCHMARKS TERMS OF USE BOTH CIS SECURITY BENCHMARKS DIVISION MEMBERS AND NON-MEMBERS MAY: Download, install, and use each of the SB Products on a single computer, and/or Print one or more copies of any SB Product that is in a .txt, .pdf, .doc, .mcw, or .rtf format, but only if each such copy is printed in its entirety and is kept intact, including without limitation the text of these CIS Security Benchmarks Terms of Use. UNDER THE FOLLOWING TERMS AND CONDITIONS: SB Products Provided As Is. CIS is providing the SB Products “as is” and “as available” without: (1) any representations, warranties, or covenants of any kind whatsoever (including the absence of any warranty regarding: (a) the effect or lack of effect of any SB Product on the operation or the security of any network, system, software, hardware, or any component of any of them, and (b) the accuracy, utility, reliability, timeliness, or completeness of any SB Product); or (2) the responsibility to make or notify you of any corrections, updates, upgrades, or fixes. Intellectual Property and Rights Reserved. You are not acquiring any title or ownership rights in or to any SB Product, and full title and all ownership rights to the SB Products remain the exclusive property of CIS.