A Report for the BBC I
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

In the Name of God
In The Name Of God Heidarali Korangi Father's Name: Abbas ID number: 1210 Birthdate: 1970 December 3 National Code: 1287952917 Mobile: 09121138859 Phone: (+98) 21 86037407 Email: [email protected] [email protected] Educational background: Ph.D. student in Business Intelligence at Islamic Azad University, Najafabad Branch, 2016 MSc in Information Technology from Islamic Azad University, Prof. Hassabi Tafresh Branch, 2016 GPA 46/19 Bachelor of Computer Engineering Software Aberdeen Virtual College US 2008 GPA 18/50 Positions: Executive secretary of specialized scientific network seminars Designer of four-choice software security lesson questions at Tehran Office of Education and Research, 2013 ، Teaching some short -term courses such as ”E-Organization ، E-Government ، E-Commerce ، E-Learning ”ECSA ، OWASP ،CHFI ،ISMS ، CEH & Network and Information Security Postgraduate research student in 2015 at Prof. Hassabi Tafresh Islamic Azad University PhD elected student in Information Technology in Islamic Azad University of Najafabad , Iran, with a grade point average of 19/33 Jobs: Vice President of Advanced Technology Complex Shahid-Alamol-Hoda. Head of Information Security Department of West Asia Scientific Network CEO Of a Knowledge-Based corporation called Tosun Information Technology Strategists Specialties: Linux-Java-JEE—Postgre SQL-MySQL-Spring- Hibernate-CEH-ECSA-ISMS-OWASP- CHFI- Maven-CREST-PHP-C#.Net-CCNA-CCNP-PWK-SharePoint Server and etc. Past Careers: Member of the Board of Directors of Pasteur Company -

Blogging Iran – a Case Study of Iranian English Language Weblogs
UNIVERSITY OF OSLO FACULTY OF SOCIAL SCIENCES TIK Centre for technology, innovation and culture P.O. BOX 1108 Blindern N-0317 OSLO Norway http://www.tik.uio.no ESST The European Inter-University Association on Society, Science and Technology http://www.esst.uio.no The ESST MA Blogging Iran – A Case Study of Iranian English Language Weblogs Peder Are Nøstvold Jensen University of Oslo Nature and Culture 2004 24.819 Words 1 Supervisor for this Master thesis has been Professor Terje Rasmussen from the Department of Media and Communication, the University of Oslo, Norway. I would also like to thank Elisabeth Staksrud from Statens Filmtilsyn for valuable information, and for pointing me to the Nordic Institute for Asian Studies (NIAS) in Copenhagen, Denmark, who were kind enough to offer me a scholarship and the opportunity to use their library. James Gomez was generous enough to send me his excellent new book Asian Cyberactivism for free. Last, but not least, I have to thank Mr. Hossein Derakhshan for spending some of his time giving me information and granting me an interview. Without him, and the other Iranian webloggers described here, this Master thesis would not have been possible. 2 Chapter outline of thesis: 1 Motivation 2. Methodology 3. The Internet and censorship 4. Background on Internet censorship in several countries 4.1 The case of China 4.2 The case of Singapore 4.3 Burma 5. The situation in Iran – Politics and censorship 6. Weblogs 6.1 About weblogs 6.2 Iranian weblogs 6.3 About description of weblogs 7. Weblogs – case studies 7.1 Weblogs by Insiders, Iranians in Iran 7.1.1 Additional weblogs by Insiders 7.2 Weblogs by Outsiders, Iranians in exile 7.3 Summary, and conclusion about weblog findings 8. -

Data Collection Survey on Tourism and Cultural Heritage in the Islamic Republic of Iran Final Report
THE ISLAMIC REPUBLIC OF IRAN IRANIAN CULTURAL HERITAGE, HANDICRAFTS AND TOURISM ORGANIZATION (ICHTO) DATA COLLECTION SURVEY ON TOURISM AND CULTURAL HERITAGE IN THE ISLAMIC REPUBLIC OF IRAN FINAL REPORT FEBRUARY 2018 JAPAN INTERNATIONAL COOPERATION AGENCY (JICA) HOKKAIDO UNIVERSITY JTB CORPORATE SALES INC. INGÉROSEC CORPORATION RECS INTERNATIONAL INC. 7R JR 18-006 JAPAN INTERNATIONAL COOPERATION AGENCY (JICA) DATA COLLECTION SURVEY ON TOURISM AND CULTURAL HERITAGE IN THE ISLAMIC REPUBLIC OF IRAN FINAL REPORT TABLE OF CONTENTS Abbreviations ............................................................................................................................ v Maps ........................................................................................................................................ vi Photos (The 1st Field Survey) ................................................................................................. vii Photos (The 2nd Field Survey) ............................................................................................... viii Photos (The 3rd Field Survey) .................................................................................................. ix List of Figures and Tables ........................................................................................................ x 1. Outline of the Survey ....................................................................................................... 1 (1) Background and Objectives ..................................................................................... -

Download Being the Number of Sent Packets That Were Acknowledged As Received
Dimming the Internet Detecting Throttling as a Mechanism of Censorship in Iran Collin Anderson? [email protected] Abstract. In the days immediately following the contested June 2009 Presidential election, Iranians attempting to reach news content and so- cial media platforms were subject to unprecedented levels of the degra- dation, blocking and jamming of communications channels. Rather than shut down networks, which would draw attention and controversy, the government was rumored to have slowed connection speeds to rates that would render the Internet nearly unusable, especially for the consump- tion and distribution of multimedia content. Since, political upheavals elsewhere have been associated with headlines such as \High usage slows down Internet in Bahrain" and \Syrian Internet slows during Friday protests once again," with further rumors linking poor connectivity with political instability in Myanmar and Tibet. For governments threatened by public expression, the throttling of Internet connectivity appears to be an increasingly preferred and less detectable method of stifling the free flow of information. In order to assess this perceived trend and begin to create systems of accountability and transparency on such practices, we attempt to outline an initial strategy for utilizing a ubiquitious set of network measurements as a monitoring service, then apply such method- ology to shed light on the recent history of censorship in Iran. Keywords: censorship, national Internet, Iran, throttling, M-Lab 1 Introduction "Prison is like, there's no bandwidth." - Eric Schmidt1 The primary purpose of this paper is to assess the validity of claims that the international connectivity of information networks used by the Iranian public has been subject to substantial throttling based on a historical and correlated set of open measurements of network performance. -

Mapping Iran Online
University of Pennsylvania ScholarlyCommons Center for Global Communication Studies Iran Media Program (CGCS) 2-2012 National Web Studies: Mapping Iran Online Richard Rogers Esther Weltevrede Sabine Niederer Erik Borra Follow this and additional works at: https://repository.upenn.edu/iranmediaprogram Part of the Communication Commons, and the International and Area Studies Commons Recommended Citation Rogers, Richard; Weltevrede, Esther; Niederer, Sabine; and Borra, Erik. (2012). National Web Studies: Mapping Iran Online. Iran Media Program. Retrieved from https://repository.upenn.edu/iranmediaprogram/2 This paper is posted at ScholarlyCommons. https://repository.upenn.edu/iranmediaprogram/2 For more information, please contact [email protected]. National Web Studies: Mapping Iran Online Abstract This work offers an approach to conceptualizing, demarcating and analyzing a national web. Instead of defining a priori the types of websites to be included in a national web, the approach put forward here makes use of web devices (platforms and engines) that purport to provide (ranked) lists of URLs relevant to a particular country. Once gathered in such a manner, the websites are studied for their properties, following certain of the common measures (such as responsiveness and page age), and repurposing them to speak in terms of the health of a national web: Are sites lively, or neglected? The case study in question is Iran, which is special for the degree of Internet censorship undertaken by the state. Despite the widespread censorship, we have found a highly responsive Iranian web. We also report on the relationship between blockage, responsiveness and freshness, i.e., whether blocked sites are still up, and also whether they have been recently updated. -
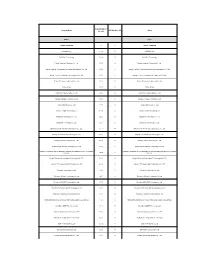
Stand Number/ ﻧﺎم ﺷﺮﮐﺖ ﺳﺎﻟﻦ /Company Name Hall Number ﺷﻤﺎره ﻏﺮﻓﻪ
Stand Number/ ﻧﺎم ﺷﺮﮐﺖ ﺳﺎﻟﻦ /Company Name Hall Number ﺷﻤﺎره ﻏﺮﻓﻪ ﺳﺎﻟﻦ Hall 5 5 CHINA - PAVILION 5 5 CHINA - PAVILION ACE Marketing 5.2.4 5 ACE Marketing B&C Fiber Technology 5.2.19 5 B&C Fiber Technology Beijing Huahuan Electronics Co., Ltd. 5.1.51 5 Beijing Huahuan Electronics Co., Ltd. Beijing HuaXing Cutting-edge Technology Development Co., Ltd. 5.1.48 5 Beijing HuaXing Cutting-edge Technology Development Co., Ltd. Beijing Telesea Technologies Development Co., Ltd. 5.1.16 5 Beijing Telesea Technologies Development Co., Ltd. Deviser Electronics Instrument Co., Ltd. 5.2.8 5 Deviser Electronics Instrument Co., Ltd. Fasten Group 5.2.23 5 Fasten Group Hangzhou Putianle Cable Co., Ltd. 5.1.21 5 Hangzhou Putianle Cable Co., Ltd. Jiangsu Changyue Trading Co., Ltd. 5.1.45 5 Jiangsu Changyue Trading Co., Ltd. Jiangsu Diyi Group Co., Ltd 5.1.49 5 Jiangsu Diyi Group Co., Ltd Jiangsu Hengxin Technology Co. 5.1.56 5 Jiangsu Hengxin Technology Co. Kingsignal Technology Co., Ltd. 5.2.21 5 Kingsignal Technology Co., Ltd. Lanbowan Technology Co. Ltd. 5.1.17 5 Lanbowan Technology Co. Ltd. Mobi Antenna Technologies (Shenzhen) Co., Ltd. 5.1.27 5 Mobi Antenna Technologies (Shenzhen) Co., Ltd. Nanjing Hedot Network Technology Co., Ltd. 5.1.18 5 Nanjing Hedot Network Technology Co., Ltd. Nanjing Huamai Technology Co., Ltd. 5.1.52 5 Nanjing Huamai Technology Co., Ltd. Ningbo Longtu Network Technology Co., Ltd. 5.1.15 5 Ningbo Longtu Network Technology Co., Ltd. NINGBO LONGXING TELECOMMUNICATIONS EQUIPMENT MANUFACTURING NINGBO LONGXING TELECOMMUNICATIONS EQUIPMENT MANUFACTURING 5.2.22 5 CO.,LTD. -

22. 0.3. 200 S- Kurzfassung Der Dissertation
Die approbierte Originalversion dieser Dissertation ist an der Hauptbibliothek der Technischen Universität Wien aufgestellt (http://www.ub.tuwien.ac.at). The approved original version of this thesis is available at the main library of the Vienna University of Technology (http://www.ub.tuwien.ac.at/englweb/). DISSERTATION Auswirkungen moderner Technologien auf die kulturelle Entwicklung der iranischen Gesellschaft Ausgeführt zum Zwecke der Erlangung des akademischen Grades eines Doktors der technischen Wissenschaften unter der Leitung von Univ. Professor Dr. phil. Wolfgang Hofkirchner E187 Institut für. Gestaltungs- und Wirkungsforschung eingereicht an der Technischen Universität Wien Fakultät für Technische Naturwissenschaften und Informatik .e von Dip!.- Ing. Seyed-Mohsen Ekssir-Monfared i 8026512 Brigittenauer Lände 156 - 158 / 6 /20, 1200 - Wien \ I Wien, am 22. 0.3. 200 S- Kurzfassung der Dissertation Kurzfassung der Dissertation Der Iran, der im Laufe der Jahrtausende immer als Drehscheibe der aufeinanderprallenden verschiedenen Kulturen und Gebräuche gedient hat, erfährt einen großen sozialen und kulturellen Umbruch. Im Informationszeitalter und im Zuge des Globalisierungsprozesses, in welchem die Welt mehr denn je zusammenrückt und die Bezugnahme der Kulturen intensiver geworden ist, sind die Auswirkungen "fremder" Kulturen auf die "eigene" und umgekehrt stärker denn je. Die Welt ist in der Tat "kleiner" und "überschau barer" geworden. Allerdings: je enger die Welt zusammenrückt und die Homogenisierung und Verwestlichung, insbesondere Amerikanisierung der Kulturen durch die technologische Entwicklung und den • verbreiteten Einsatz neuer I&K-Technologien vorangetrieben wird, verstärkt sich auf der anderen Seite eine Kraft zu Dezentralismus, Inhomogenität sowie eine Tendenz zur Rückkehr zu lokalen kulturellen Werten. Auf der anderen Seite ist es der Fundamentalismus und die Rückkehr zu den Traditionen und dem religiösen Glauben, die keine Affinität mit dem Leben im 21. -

The Relationship of Supportive Roles with Mental Health and Satisfaction with Life in Female Household Heads: a Structural Equations Model
The Relationship of Supportive Roles With Mental Health and Satisfaction With Life in Female Household Heads: A Structural Equations Model Nooshin Shadabi Alborz University of Medical Sciences, Karaj, IRAN Sara Esmaelzadeh – Saeieh Alborz University of Medical Sciences, Karaj, IRAN Mostafa Qorbani Alborz University of Medical Sciences, Karaj, IRAN Touran Bahrami Babaheidari Alborz University of Medical Sciences, Karaj, IRAN Zohreh Mahmoodi ( [email protected] ) Alborz University of Medical Sciences, Karaj, IRAN Research Article Keywords: Female Household Heads, Supportive Roles, Satisfaction with Life, Mental Health, Structural Equations Posted Date: December 30th, 2020 DOI: https://doi.org/10.21203/rs.3.rs-129599/v1 License: This work is licensed under a Creative Commons Attribution 4.0 International License. Read Full License Page 1/15 Abstract Background: Female household heads are faced with many more problems than men due to their multiple concurrent roles. The present study was conducted to determine the relationship of supportive roles with mental health and satisfaction with life in female household heads using a structural equations model. Methods: The present descriptive-analytical study was conducted on 286 eligible female household heads in Karaj, Iran, in 2020, who were selected by convenience sampling. Data were collected using VAX social support, the perceived social support scale, the general health questionnaire (GHQ), and the satisfaction with life questionnaire plus a socio-demographic checklist, and were analyzed in SPSS-16 and Lisrel-8.8. Results: The participants’ mean age was 43.1±1.7 years. According to the path analysis results, satisfaction with life had the highest direct positive relationship with perceived social support (B=0.33) and the highest indirect positive relationship with age (B=0.13) and the highest direct and indirect positive relationship with education and social support (B=0.13). -

Hardware, Hand Tools & Metal Products
• Hardware, Hand Tools & Metal Products Alloy Products Measuring Equipments Aluminum Products Mechanical, Hydraulic & Pneumatic Tools Bolts, Nuts, Screws Metal Angles, Bars, Rods & Beams Brass Tools & Dimensions Metal Tools & Parts Coils Molds & Dies Copper Products Pipes & Tubes, Fittings, Couplings Diamond Tools Profiles Die / Casting Tools Pumps Fasteners Rivets, Blind Rivets, Nails Flanges, Strainers Shear & Cutting Tools Forging Parts Springs Gardening Tools Steel Products Hand Tools Valves & Faucets Hardeware Vibration Systems Industrial Parts & Tools Washers Ingots, Slabs Welding Equipments Jigs, Fixtures Wire Brushes Locks, Keys, Handles, Hinges Wire Nettings, Barbed Wires LPG Cylinders & Regulators Misc. Reference:Iran Tpo Exporters Data Bank , Exemplary Exporters Directory Iran trade yellowpages , iran export directory www.tpo.ir A ABOHAVA CO, L TO AEROSPACE INDUSTRIES AKBAR I METAL MELTING CO Head Office: Underground FI.,No.25, East Head Office: 1st FL, No. 81 East 146th St, ORGANIZATION Garmsar St. South Shiraz St, Tehran Head Office: Langari St, Nobonyad Sq Tehranpars 1st Sq., 1654636453, Tehran AB HAYAT KERMAN CO Tel: (+98-21) 88034874-5 19575. Tehran Tel: (+98-21) 77861521, 7777749 Head Office: No 12, Corner of Farahanipour Alley, Fax: (+98-21) 88051330 Tel: (+98-21) 22945466-7, 23022231 Fax: (+98-21) 7775302 Yousef Abad St, 14336, Tehran Email: [email protected] Fax: (+98-21) 22945629 Factory: (+98-232) 4772022-3 Tel: (+98-21) 88553701 URL: www.abohava.com Email: [email protected] Email: [email protected] Fax: (+98-21) 88711051 MD: Shambayati MD: Ahmad Vahid URL: www.akbarimetalmelt.com Factory: (+98-341) 3318940 Activity: Waterpumps [I] Activity: Industrial Parts. Industnal Molds, MD: Ali Asghar Akbari Email: [email protected] Home Appliances, Automotive Parts, Engines Activity: Steel Grinding [M] URL: www.ab-hayat.com [M-E-I] MD: Hossain Mohammadi Nasr Abadi ABRAHAN PIPE CO Activity: Polyethylene Fittings. -

Violations Against Ethnic and Religious Minorities in Iran
Rights Denied: Violations against ethnic and religious minorities in Iran © Ceasefire Centre for Civilian Rights, Centre for Supporters of Human Rights and Minority Rights Group International, March 2018. This report has been produced with the financial assistance of the European Union. The contents of this report are the sole responsibility of the publishers and can under no circumstances be regarded as reflecting the position of the European Union. Cover photo: A Kurdish man at Hawraman-at Takht, Iranian Kurdistan, Iran. © Roberto Cornacchia / Alamy Stock Photo Ceasefire Centre for Civilian Rights The Ceasefire Centre for Civilian Rights is a new initiative to develop ‘civilian-led monitoring’ of violations of international humanitarian law or human rights, to pursue legal and political accountability for those responsible for such violations, and to develop the practice of civilian rights. The Ceasefire Centre for Civilian Rights is registered as a charity and a company limited by guarantee under English law; charity no: 1160083, company no: 9069133. Centre for Supporters of Human Rights The Centre for Supporters of Human Rights (CSHR) is a non-governmental organ- isation established in the UK in 2013. Dr. Shirin Ebadi, Nobel Peace Prize Laureate 2003, is one of its founders and the chair of the Centre. CSHR's main goal is to advance human rights in the Middle East, in particular Iran. Minority Rights Group International MRG is an NGO working to secure the rights of ethnic, religious and linguistic minorities and indigenous peoples worldwide, and to promote cooperation and understanding between communities. MRG works with over 150 partner orga- nizations in nearly 50 countries. -

La Province De Teheran
LLAA PPRROOVVIINNCCEE DDEE TTEEHHEERRAANN Mai 2019 © DG Trésor Présentation La province de Téhéran, centre politique et économique de l’Iran générale Au Nord de l’Iran, localisée au pied du massif de l’Alborz dont le mont Damavand culmine à 5 671 mètres, la province de Téhéran inclut la capitale iranienne et ses Population (2016) : périphéries, à travers une organisation administrative en 16 districts. Capitale à la 13 267 367 habitants topographie contrastée, l’altitude des quartiers de Téhéran, entre 1100 et 1700 (16,6 % de la population nationale) mètres au-dessus du niveau de la mer, est bien souvent corrélée au capital économique et social des habitants1. La province bénéficie d’un climat continental Superficie : 12 981 km2 caractérisé par quatre saisons bien distinctes et par un été long et chaud. Devenue la capitale de l’Iran le 12 mars 1786 par une décision d’Agha Mohammad Khan, fondateur de la dynastie Qadjar, Téhéran est passée d’une cité d’une dizaine de milliers de résidents à une mégalopole comptant plus de 8,6 millions d’habitants. En parallèle de cette croissance démographique, le poids de la province de Téhéran dans l’économie iranienne a connu une progression continue depuis le 19ème siècle. Téhéran est le centre administratif et poumon économique du pays. Depuis fin novembre 2018, le maire de la ville est Pirouz Hanachi et depuis décembre 2018, le gouverneur de la province de Téhéran est Anoushirvan Mohseni-Bandpey (précédemment président de l’Organisation d’Etat pour la protection sociale). Plus de la moitié de la population de la province a moins de 35 ans. -

Hadi Hesab Tehran Audit Firm (Certified Public Accountants) Reg
Hadi Hesab Tehran Audit Firm (Certified Public Accountants) Reg . No.51151 Hadi Hesab Tehran (Certified public accountants) Member firm of UHY International In Iran [email protected] No : 2 , Sarv Alley , Torkamanestan Dtr, Shahid Motahari Ave. www.HadiHesab.ir Tehran , Iran Postal Code : 9366916651 SMS : 0111 88 44 Tel : +19 (29) 99 44 56 54 ( Special Line ) Fax : +19 ( 29 ) 99 44 26 66 Hadi Hesab Tehran Audit Firm (Certified Public Accountants) Reg . No.51151 Contents: Hadi Hesab in a nutshell Credentials Partners and Managers Organizational Chart Services Special customers/clients Completed projects and tasks Appendix [email protected] No : 2 , Sarv Alley , Torkamanestan Dtr, Shahid Motahari Ave. www.HadiHesab.ir Tehran , Iran Postal Code : 9366916651 SMS : 0111 88 44 Tel : +19 (29) 99 44 56 54 ( Special Line ) Fax : +19 ( 29 ) 99 44 26 66 Hadi Hesab Tehran Audit Firm (Certified Public Accountants) Reg . No.51151 Hadi Hesab in a nutshell: Hadi Hesab Tehran is an Iranian firm that delivers services in audit, consulting, financial advisory, tax and related services both at home and abroad. Located in Tehran, Hadi Hesab Tehran was founded in 2003 under reference number 51050 of the Companies Registration Office. We are a member of Iranian Association of Certified Public Accountants (IACPA). This firm has achieved grade "A" status from IACPA which represents the highest grade in quality control assessment. Ranking in the Institutes of certified public accountants in Iran (Determination of time rating) 2007 2008 2009 2010 2011 2012 2013 2014 2015 2016 2017 2018 Grade Grade Grade Grade Grade Grade Grade Grade Grade Grade Grade Grade (A) (A) (A) (A) (A) (A) (B) (A) (A) (A) (A) (A) Important Note: Additionally, according to the latest represented ranking from CPA (Situation Control Unit), this firm could get eighth degree in total 322 audit firms.