Asterisk™: the Future of Telephony ,Roadmap Asterisk.21163 Page I Tuesday, August 14, 2007 1:43 PM
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Jupyter Reference Guide
– 1 – Nicholas Bowman, Sonja Johnson-Yu, Kylie Jue Handout #15 CS 106AP August 5, 2019 Jupyter Reference Guide This handout goes over the basics of Jupyter notebooks, including how to install Jupyter, launch a notebook, and run its cells. Jupyter notebooks are a common tool used across different disciplines for exploring and displaying data, and they also make great interactive explanatory tools. Installing Jupyter To install Jupyter, run the following command inside your Terminal (replace python3 with py if you’re using a Windows device): $ python3 -m pip install jupyter Launching a notebook A Jupyter notebook is a file that ends in the extension .ipynb, which stands for “interactive Python notebook.” To launch a Python notebook after you’ve installed Jupyter, you should first navigate to the directory where your notebook is located (you’ll be there by default if you’re using the PyCharm terminal inside a project). Then run the following command inside your Terminal (if this doesn’t work, see the “Troubleshooting” section below): $ jupyter notebook This should open a window in your browser (Chrome, Firefox, Safari, Edge, etc.) that looks like Figure 1. Jupyter shows the files inside the current directory and allows you to click on any Python notebook files within that folder. Figure 1: After running the jupyter notebook command, you should see a window that lists the Python notebooks inside the current directory from which you ran the command. The picture above shows the Lecture 25 directory. – 2 – To launch a particular notebook, click on its file name. This should open a new tab with the notebook. -

Edit Bibliographic Records
OCLC Connexion Browser Guides Edit Bibliographic Records Last updated: May 2014 6565 Kilgour Place, Dublin, OH 43017-3395 www.oclc.org Revision History Date Section title Description of changes May 2014 All Updated information on how to open the diacritic window. The shortcut key is no longer available. May 2006 1. Edit record: basics Minor updates. 5. Insert diacritics Revised to update list of bar syntax character codes to reflect and special changes in character names and to add newly supported characters characters. November 2006 1. Edit record: basics Minor updates. 2. Editing Added information on guided editing for fields 541 and 583, techniques, template commonly used when cataloging archival materials. view December 2006 1. Edit record: basics Updated to add information about display of WorldCat records that contain non-Latin scripts.. May 2007 4. Validate record Revised to document change in default validation level from None to Structure. February 2012 2 Editing techniques, Series added entry fields 800, 810, 811, 830 can now be used to template view insert data from a “cited” record for a related series item. Removed “and DDC” from Control All commands. DDC numbers are no longer controlled in Connexion. April 2012 2. Editing New section on how to use the prototype OCLC Classify service. techniques, template view September 2012 All Removed all references to Pathfinder. February 2013 All Removed all references to Heritage Printed Book. April 2013 All Removed all references to Chinese Name Authority © 2014 OCLC Online Computer Library Center, Inc. 6565 Kilgour Place Dublin, OH 43017-3395 USA The following OCLC product, service and business names are trademarks or service marks of OCLC, Inc.: CatExpress, Connexion, DDC, Dewey, Dewey Decimal Classification, OCLC, WorldCat, WorldCat Resource Sharing and “The world’s libraries. -

How the Past Affects the Future: the Story of the Apostrophe1
HOW THE PAST AFFECTS THE FUTURE: THE STORY OF THE APOSTROPHE1 Christina Cavella and Robin A. Kernodle I. Introduction The apostrophe, a punctuation mark which “floats above the line, symbolizing something missing in the text” (Battistella, 1999, p. 109), has been called “an unstable feature of written English” (Gasque, 1997, p. 203), “the step-child of English orthography” (Barfoot, 1991, p. 121), and “an entirely insecure orthographic squiggle” (Barfoot, 1991, p. 133). Surely the apostrophe intends no harm; why then the controversy and apparent emotionalism surrounding it? One major motivation for investigating the apostrophe is simply because it is so often misused. A portion of the usage problem can perhaps be attributed to the chasm dividing spoken and written language, as the apostrophe was originally intended to indicate missing letters, which may or may not have actually been enunciated. To understand what has been called “the aberrant apostrophe,” (Crystal, 1995, p. 203) and the uncertainty surrounding its usage, an examination of its history is essential, for it is this “long and confused” (Crystal, 1995, p. 203) history that is partially responsible for the modern-day misuses of the apostrophe. This paper will trace the history of the apostrophe, examining the purpose(s) for which the apostrophe has been utilized in the past as well as presenting its current use. An overview of contemporary rules of usage is then included, along with specific examples of apostrophe misuse and a recommendation on how to teach apostrophe usage to non- native speakers of English. Finally, an attempt is made to predict the apostrophe’s future. -

14 * (Asterisk), 169 \ (Backslash) in Smb.Conf File, 85
,sambaIX.fm.28352 Page 385 Friday, November 19, 1999 3:40 PM Index <> (angled brackets), 14 archive files, 137 * (asterisk), 169 authentication, 19, 164–171 \ (backslash) in smb.conf file, 85 mechanisms for, 35 \\ (backslashes, two) in directories, 5 NT domain, 170 : (colon), 6 share-level option for, 192 \ (continuation character), 85 auto services option, 124 . (dot), 128, 134 automounter, support for, 35 # (hash mark), 85 awk script, 176 % (percent sign), 86 . (period), 128 B ? (question mark), 135 backup browsers ; (semicolon), 85 local master browser, 22 / (slash character), 129, 134–135 per local master browser, 23 / (slash) in shares, 116 maximum number per workgroup, 22 _ (underscore) 116 backup domain controllers (BDCs), 20 * wildcard, 177 backups, with smbtar program, 245–248 backwards compatibility elections and, 23 for filenames, 143 A Windows domains and, 20 access-control options (shares), 160–162 base directory, 40 accessing Samba server, 61 .BAT scripts, 192 accounts, 51–53 BDCs (backup domain controllers), 20 active connections, option for, 244 binary vs. source files, 32 addresses, networking option for, 106 bind interfaces only option, 106 addtosmbpass executable, 176 bindings, 71 admin users option, 161 Bindings tab, 60 AFS files, support for, 35 blocking locks option, 152 aliases b-node, 13 multiple, 29 boolean type, 90 for NetBIOS names, 107 bottlenecks, 320–328 alid users option, 161 reducing, 321–326 announce as option, 123 types of, 320 announce version option, 123 broadcast addresses, troubleshooting, 289 API -

Legacy Character Sets & Encodings
Legacy & Not-So-Legacy Character Sets & Encodings Ken Lunde CJKV Type Development Adobe Systems Incorporated bc ftp://ftp.oreilly.com/pub/examples/nutshell/cjkv/unicode/iuc15-tb1-slides.pdf Tutorial Overview dc • What is a character set? What is an encoding? • How are character sets and encodings different? • Legacy character sets. • Non-legacy character sets. • Legacy encodings. • How does Unicode fit it? • Code conversion issues. • Disclaimer: The focus of this tutorial is primarily on Asian (CJKV) issues, which tend to be complex from a character set and encoding standpoint. 15th International Unicode Conference Copyright © 1999 Adobe Systems Incorporated Terminology & Abbreviations dc • GB (China) — Stands for “Guo Biao” (国标 guóbiâo ). — Short for “Guojia Biaozhun” (国家标准 guójiâ biâozhün). — Means “National Standard.” • GB/T (China) — “T” stands for “Tui” (推 tuî ). — Short for “Tuijian” (推荐 tuîjiàn ). — “T” means “Recommended.” • CNS (Taiwan) — 中國國家標準 ( zhôngguó guójiâ biâozhün) in Chinese. — Abbreviation for “Chinese National Standard.” 15th International Unicode Conference Copyright © 1999 Adobe Systems Incorporated Terminology & Abbreviations (Cont’d) dc • GCCS (Hong Kong) — Abbreviation for “Government Chinese Character Set.” • JIS (Japan) — 日本工業規格 ( nihon kôgyô kikaku) in Japanese. — Abbreviation for “Japanese Industrial Standard.” — 〄 • KS (Korea) — 한국 공업 규격 (韓國工業規格 hangug gongeob gyugyeog) in Korean. — Abbreviation for “Korean Standard.” — ㉿ — Designation change from “C” to “X” on August 20, 1997. 15th International Unicode Conference Copyright © 1999 Adobe Systems Incorporated Terminology & Abbreviations (Cont’d) dc • TCVN (Vietnam) — Tiu Chun Vit Nam in Vietnamese. — Means “Vietnamese Standard.” • CJKV — Chinese, Japanese, Korean, and Vietnamese. 15th International Unicode Conference Copyright © 1999 Adobe Systems Incorporated What Is A Character Set? dc • A collection of characters that are intended to be used together to create meaningful text. -

The Luacode Package
The luacode package Manuel Pégourié-Gonnard <[email protected]> v1.2a 2012/01/23 Abstract Executing Lua code from within TEX with \directlua can sometimes be tricky: there is no easy way to use the percent character, counting backslashes may be hard, and Lua comments don’t work the way you expect. This package provides the \luaexec command and the luacode(*) environments to help with these problems, as well as helper macros and a debugging mode. Contents 1 Documentation1 1.1 Lua code in LATEX...................................1 1.2 Helper macros......................................3 1.3 Debugging........................................3 2 Implementation3 2.1 Preliminaries......................................4 2.2 Internal code......................................5 2.3 Public macros and environments...........................7 3 Test file 8 1 Documentation 1.1 Lua code in LATEX For an introduction to the most important gotchas of \directlua, see lualatex-doc.pdf. Before presenting the tools in this package, let me insist that the best way to manage a non- trivial piece of Lua code is probably to use an external file and source it from Lua, as explained in the cited document. \luadirect First, the exact syntax of \directlua has changed along version of LuaTEX, so this package provides a \luadirect command which is an exact synonym of \directlua except that it doesn’t have the funny, changing parts of its syntax, and benefits from the debugging facilities described below (1.3).1 The problems with \directlua (or \luadirect) are mainly with TEX special characters. Actually, things are not that bad, since most special characters do work, namely: _, ^, &, $, {, }. Three are a bit tricky but they can be managed with \string: \, # and ~. -

Trademarks 10 Things You Should Know to Protect Your Product and Business Names
Trademarks 10 things you should know to protect your product and business names 1. What is a trademark? A trademark is a brand name for a product. It can be a word, phrase, logo, design, or virtually anything that is used to identify the source of the product and distinguish it from competitors’ products. More than one trademark may be used in connection with a product; for example, COCA-COLA® and DIET COKE® are both trademarks for beverages. A trademark represents the goodwill and reputation of a product and its source. Its owner has the right to prevent others from trading on that goodwill by using the same or a similar trademark on the same or similar products in a way that is likely to cause confusion as to the source, origin, or sponsorship of the products. A service mark is like a trademark, except it is used to identify and distinguish services rather than products. For example, the “golden arches” mark shown below is a service mark for restaurant services. The terms “trademark” and “mark” are often used interchangeably to refer to either a trademark or service mark. 2. How should a mark be used? Trademarks must be used properly to maintain their value. Marks should be used as adjectives, but not as nouns or verbs. 4 | knobbe.com For example, when referring to utilizing the FACEBOOK® website, do not say that you “Facebooked” or that you were “Facebooking.” To prevent loss of trademark or service mark rights, the generic name for the product should appear after the mark, and the mark should appear visually different from the surrounding text. -

List of Approved Special Characters
List of Approved Special Characters The following list represents the Graduate Division's approved character list for display of dissertation titles in the Hooding Booklet. Please note these characters will not display when your dissertation is published on ProQuest's site. To insert a special character, simply hold the ALT key on your keyboard and enter in the corresponding code. This is only for entering in a special character for your title or your name. The abstract section has different requirements. See abstract for more details. Special Character Alt+ Description 0032 Space ! 0033 Exclamation mark '" 0034 Double quotes (or speech marks) # 0035 Number $ 0036 Dollar % 0037 Procenttecken & 0038 Ampersand '' 0039 Single quote ( 0040 Open parenthesis (or open bracket) ) 0041 Close parenthesis (or close bracket) * 0042 Asterisk + 0043 Plus , 0044 Comma ‐ 0045 Hyphen . 0046 Period, dot or full stop / 0047 Slash or divide 0 0048 Zero 1 0049 One 2 0050 Two 3 0051 Three 4 0052 Four 5 0053 Five 6 0054 Six 7 0055 Seven 8 0056 Eight 9 0057 Nine : 0058 Colon ; 0059 Semicolon < 0060 Less than (or open angled bracket) = 0061 Equals > 0062 Greater than (or close angled bracket) ? 0063 Question mark @ 0064 At symbol A 0065 Uppercase A B 0066 Uppercase B C 0067 Uppercase C D 0068 Uppercase D E 0069 Uppercase E List of Approved Special Characters F 0070 Uppercase F G 0071 Uppercase G H 0072 Uppercase H I 0073 Uppercase I J 0074 Uppercase J K 0075 Uppercase K L 0076 Uppercase L M 0077 Uppercase M N 0078 Uppercase N O 0079 Uppercase O P 0080 Uppercase -

Beginner's Guide to Asterisk
Getting Started With Open Source Telephony A Beginners Guide to Asterisk Steve Sokol Asterisk Marketing Lead, Digium Justin Hester Lead Asterisk Technical Instructor, Digium Agenda • Summary of Asterisk • Basics and Distributions • Resources • Asterisk is a toolkit • Distros are more complete • Training classes package with GUI • Digium and Asterisk • Getting started using Asterisk • AstriCon 2016 • Architecture - Linux + Asterisk • Difference between CLI and GUI • Versioning Getting Started with Asterisk Getting Started with Asterisk • Find it • Install it • Configure it What is Asterisk? An Open Source Communications Platform • Software, written in C, that you put on an ordinary operating system—transforming that system into a communications engine. Software – A communications platform A system through which communications flow, from one endpoint to another. What is Asterisk - Platform Open Source Communications Platform Software - Extensible Architecture A simple core with only a few responsibilities Module Management Reading Configuration CORE System Timing CORE Channel Management Software – Modular Architecture Modules app_dial.so • Use the native modules • Use Asterisk’s APIs to control and extend Asterisk – AMI, AGI, and ARI Preparing for Asterisk – Set up a host machine • Old physical hardware – Laptop, rackmount or tower system • Virtual machine – e.g. VirtualBox (on your Mac, Windows or Linux laptop!) www.virtualbox.org • Cloud server – e.g. www.digitalocean.com or aws.amazon.com Finding Asterisk – Choose your path ‘Source’ or ‘Plain Vanilla’ AsteriskNOW, a PBX ‘distro’. www.asterisk.org/downloads Choosing Asterisk - Source • Install a Linux operating system • Set up networking • Configure software repositories • Install Asterisk dependencies • Download and install Asterisk, DAHDI, LibPRI from provided scripts. And you will have an unconfigured, pristine, ready to configure “Asterisk Configuration Framework”. -

Appraisal Institute Trademark Usage Manual
Trademark Usage Manual for Appraisal Institute Copyright © 2020 Appraisal Institute. All rights reserved. Printed in the United States of America. No part of this publication may be reproduced, stored in a retrieval system, or transmitted in any form or by any means, electronic, mechanical, photocopy, recording or otherwise, without the prior written consent of the publisher. TRADEMARK USAGE MANUAL FOR APPRAISAL INSTITUTE Table of Contents I. Introduction 1 II. Trademarks, Service Marks, Collective Service Marks and Collective Membership Marks 1 III. Trade Names are Different from Trademarks 2 IV. Proper Trademark Usage 3 A. Always Use Trademarks as Proper Adjectives ............................................................................... 3 B. Make the Trademark Stand Out .................................................................................................... 3 C. Only One Trademark Should Appear on the Same Label or Name Plate ....................................... 4 D. Use of Appraisal Institute Trademarks ........................................................................................... 4 1. Signature Requirements and Restrictions ................................................................................ 4 2. Membership Designation Requirements and Restrictions ........................................................ 5 3. Proper Use of Letter Designations ........................................................................................... 5 4. Emblem Requirements and Restrictions ................................................................................. -
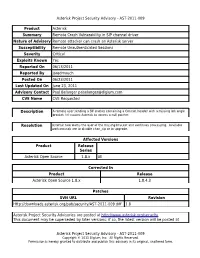
AST-2011-009 Product Asterisk Summary Remote Crash Vulnerability in SIP Channel Driver Natu
Asterisk Project Security Advisory - AST-2011-009 Product Asterisk Summary Remote Crash Vulnerability in SIP channel driver Nature of Advisory Remote attacker can crash an Asterisk server Susceptibility Remote Unauthenticated Sessions Severity Critical Exploits Known Yes Reported On 06/13/2011 Reported By jaredmauch Posted On 06/23/2011 Last Updated On June 23, 2011 Advisory Contact Paul Belanger [email protected] CVE Name CVE Requested Description A remote user sending a SIP packet containing a Contact header with a missing left angle bracket (<) causes Asterisk to access a null pointer. Resolution Asterisk now warns the user of the missing bracket and continues processing. Available workarounds are to disable chan_sip or to upgrade. Affected Versions Product Release Series Asterisk Open Source 1.8.x All Corrected In Product Release Asterisk Open Source 1.8.x 1.8.4.3 Patches SVN URL Revision Http://downloads.asterisk.org/pub/security/AST-2011-009.diff 1.8 Asterisk Project Security Advisories are posted at http://www.asterisk.org/security This document may be superseded by later versions; if so, the latest version will be posted at Asterisk Project Security Advisory - AST-2011-009 Copyright © 2011 Digium, Inc. All Rights Reserved. Permission is hereby granted to distribute and publish this advisory in its original, unaltered form. Asterisk Project Security Advisory - AST-2011-009 http://downloads.digium.com/pub/security/AST-2011-009.pdf and http://downloads.digium.com/pub/security/AST-2011-009.html Revision History Date Editor Revisions Made 06/20/2011 Kinsey Moore Initial Release Asterisk Project Security Advisory - AST-2011-009 Copyright © 2011 Digium, Inc. -

Common Intellectual Property Abbreviations and Symbols
www.oliveandolive.com 500 Memorial Street • Post Office Box 2049 • Durham, NC 27702-2049 I Phone (919)683-5514 • Fax (919)683-3781 COMMON INTELLECTUAL PROPERTY ABBREVIATIONS AND INTELLECTUAL PROPERTY SYMBOLS: The Meaning of Abbreviations and Symbols for Patents, Trademarks, Copyrights, Mask Works, and Designs Abbreviation or Meaning Symbol Patent or Pat. Indicates an invention protected by an issued United States patent. A proper patent notice contains one of these listed terms, followed by the patent number. Sometimes the letters “U.S.” are added before one of the terms, and sometimes the abbreviation “No.” or “Number” are used after one of the terms, but they are not required. The notice should appear either on the protected article or, if that is not possible, on a label affixed to it or to its packaging. For more information about patents, refer to our Learning Center article on Patents. Patent Pending or An application has been filed seeking to protect some aspect of the Pat. Pending marked invention. This designation does not mean a patent has issued. It may never issue. Reg. U.S. Pat. & Indicates a mark which has been registered with the United States TM Office or Patent & Trademark Office. The owner of such a mark has greater protection than do owners of unregistered marks. For more ® information about trademarks, refer to our Learning Center article on Trademarks, and our short article on appropriate trademark use. SM SM or Stands for “service mark” and means that someone is claiming the adjacent word or symbol as their trademark to identify the services, such as restaurant services, which they are offering.