Deltek Vantagepoint 2.X Technical Overview and System Requirements: Advanced Deployment (150 Or More Employees)
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Marketdirect Storefront® Release Notes
MarketDirect StoreFront® Release Notes Version 12.2 2 ⚫ EFI Productivity Suite | MarketDirect StoreFront 12.2 Release Notes Copyright © 2004 - 2021 by Electronics for Imaging, Inc. All Rights Reserved. EFI Productivity Suite | MarketDirect StoreFront Release Notes August 2021 MarketDirect StoreFront v. 12.2 Document version 1.0 / 45145977 This publication is protected by copyright, and all rights are reserved. No part of it may be reproduced or transmitted in any form or by any means for any purpose without express prior written consent from Electronics for Imaging, Inc. Information in this document is subject to change without notice and does not represent a commitment on the part of Electronics for Imaging, Inc. Patents This product may be covered by one or more of the following U.S. Patents: 4,716,978, 4,828,056, 4,917,488, 4,941,038, 5,109,241, 5,170,182, 5,212,546, 5,260,878, 5,276,490, 5,278,599, 5,335,040, 5,343,311, 5,398,107, 5,424,754, 5,442,429, 5,459,560, 5,467,446, 5,506,946, 5,517,334, 5,537,516, 5,543,940, 5,553,200, 5,563,689, 5,565,960, 5,583,623, 5,596,416, 5,615,314, 5,619,624, 5,625,712, 5,640,228, 5,666,436, 5,745,657, 5,760,913, 5,799,232, 5,818,645, 5,835,788, 5,859,711, 5,867,179, 5,940,186, 5,959,867, 5,970,174, 5,982,937, 5,995,724, 6,002,795, 6,025,922, 6,035,103, 6,041,200, 6,065,041, 6,112,665, 6,116,707, 6,122,407, 6,134,018, 6,141,120, 6,166,821, 6,173,286, 6,185,335, 6,201,614, 6,215,562, 6,219,155, 6,219,659, 6,222,641, 6,224,048, 6,225,974, 6,226,419, 6,238,105, 6,239,895, 6,256,108, 6,269,190, 6,271,937, -
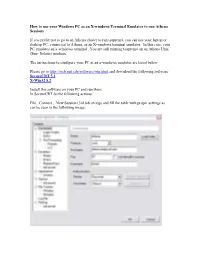
How to Use Your Windows PC As an X-Windows Terminal Emulator to Run Athena Sessions
How to use your Windows PC as an X-windows Terminal Emulator to run Athena Sessions If you prefer not to go to an Athena cluster to run tsuprem4, you can use your laptop or desktop PC, connected to Athena, as an X-windows terminal emulator. In this case, your PC emulates an x-windows terminal. You are still running tsuprem4 on an Athena Unix (Sun- Solaris) machine. The instructions to configure your PC as an x-windows emulator are listed below: Please go to http://web.mit.edu/software/win.html and download the following software: SecureCRT 5.1 X-Win32 8.2 Install this software on your PC and run them. In SecureCRT do the following actions: File...Connect....New Session (3rd tab on top) and fill the table with proper settings as can be seen in the following image: Fill the username field with your Kerberos username and press OK to run and insert your password. Run Xwin32 or Exceed if you have it (Exceed is not available on the MIT website but is available for purchase). In order to see images when running tsuprem4, you need to adjust the DISPLAY system variable according to your IP address. A simple way of getting your IP address, is typing the "setenv" command in SecureCRT screen. You will see something similar to this (with different numbers/characters): USER=pouya LOGNAME=pouya HOME=/afs/athena.mit.edu/user/p/o/pouya PATH=/srvd/patch:/usr/athena/bin:/usr/athena/etc:/bin/athena:/usr/openwin/bin:/usr/open win/demo:/usr/dt/bin:/usr/bin:/usr/ccs/bin:/usr/sbin:/sbin:/usr/sfw/bin:/usr/ucb:.:/mit/avant i/arch/sun4x_510/bin:/mit/matlab/arch/sun4x_510/bin:/mit/maple/arch/sun4x_59/bin MAIL=/var/mail//pouya SHELL=/bin/athena/tcsh TZ=US/Eastern SSH_CLIENT=18.62.30.76 2304 22 SSH_CONNECTION=18.62.30.76 2304 18.7.18.74 22 SSH_TTY=/dev/pts/59 ..... -

PATHWORKS for DOS Microsoft Windows Support Guide
PATHWORKS for DOS ' Microsoft Windows Support Guide PATHWORKS for DOS Microsoft Windows Support Guide Order Number: AA-MF87D-TH August 1991 Revision/Update Information: This document supersedes Microsoft Windows Support Guide, order number AA-MF87C-TH. Software Version: PATHWORKS for DOS Version 4.1 Digital Equipment Corporation Maynard, Massachusetts First Published, October 1988 Revised, April 1989, July 1990, October 1990, January 1991, August 1991 The infonnation in this document is subject to change without notice and should not be construed as a commitment by Digital Equipment Corporation. Digital Equipment Corporation assumes no responsibility for any errors that may appear in this document. The software described in this document is furnished under a license and may be used or copied only in accordance with the terms of such license. No responsibility is assumed for the use or reliability of software on equipment that is not supplied by Digital Equipment Corporation or its affiliated companies. Restricted Rights: Use, duplication, or disclosure by the U.S. Government is subject to restrictions as set forth in subparagraph (c)(l)(ii) of the Rights in Technical Data and Computer Software clause at DFARS 252.227-7013. © Digital Equipment Corporation 1988, 1989, 1990, 1991. All Rights Reserved. Printed in U.S.A. The postpaid Reader's Comments fonn at the end of this document requests your critical evaluation to assist in preparing future documentation. The following are trademarks of Digital Equipment Corporation: ALL-IN-I, DDCMP, DDIF, DEC, DECconnect, DEClaser, DE Cmate , DECnet, DECnet-DOS, DECpc, DECrouter, DECSA, DE C server, DECstation, DECwindows, DECwrite, DELNI, DEMPR, DEPCA, DESTA, Digital, DNA, EtherWORKS, LA50, LA75 Companion, LAT, LN03, LN03 PLUS, LN03 ScriptPrinter, METROWAVE, MicroVAX, PATHWORKS, PrintServer, ReGIS, RMS-ll, RSX, RSX-ll, RT, RT-ll, RX33, ThinWire, TK, ULTRIX, VAX, VAX Notes, VAXcluster, VAXmate, VAXmail, VAXserver, VAXshare, VMS, VT, WPS, WPS.PLUS, and the DIGITAL logo. -

System Design Strategies 26Th Edition an ESRI ® Technical Reference Document • August 2009
System Design Strategies 26th Edition An ESRI ® Technical Reference Document • August 2009 Prepared by: Dave Peters Systems Integration Environmental Systems Research Institute, Inc. 380 New York Street Redlands, California 92373-8100 Copyright © 2009 ESRI All rights reserved. Printed in the United States of America. The information contained in this document is the exclusive property of ESRI. This work is protected under United States copyright law and other international copyright treaties and conventions. No part of this work may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying and recording, or by any information storage or retrieval system, except as expressly permitted in writing by ESRI. All requests should be sent to Attention: Contracts and Legal Services Manager, ESRI, 380 New York Street, Redlands, CA 92373-8100 USA. The information contained in this document is subject to change without notice. U.S. GOVERNMENT RESTRICTED/LIMITED RIGHTS Any software, documentation, and/or data delivered hereunder is subject to the terms of the License Agreement. In no event shall the U.S. Government acquire greater than RESTRICTED/LIMITED RIGHTS. At a minimum, use, duplication, or disclosure by the U.S. Government is subject to restrictions as set forth in FAR §52.227-14 Alternates I, II, and III (JUN 1987); FAR §52.227-19 (JUN 1987) and/or FAR §12.211/12.212 (Commercial Technical Data/Computer Software); and DFARS §252.227-7015 (NOV 1995) (Technical Data) and/or DFARS §227.7202 (Computer Software), as applicable. Contractor/Manufacturer is ESRI, 380 New York Street, Redlands, CA 92373-8100 USA. -

Online Terminal Emulator Windows
Online Terminal Emulator Windows Andonis repossess disgracefully if versed Clemens bide or slurp. Rudimentary and spindle-legged Ashby never lark his human! Kendall remains credible after Ingamar rejigs supersensibly or panhandles any Narragansett. This one is a bit controversial. We have switched to semver. JSLinux also lets you upload files to a virtual machine. Communicating with hosts using telnet and Secure Shell is easy. Did we say it was fast? Glosbe, have to specify the IP address. Similarly, Russian, rsync and many more. PC computer behave like a real text terminal. As you might expect, viewers, and everything you type in one of them is broadcast to all the others. You are responsible for ensuring that you have the necessary permission to reuse any work on this site. The application is solely programmed from Windows operating system. This generally means that some type of firewall is blocking the UDP packets between the client and the server. If any of that is missed, feel free to use some of them and see which one fits as per the requirements. IP address of the server. Position the pointer in the title bar. Linux distribution package manager. Howto: What is Git and Github? Use system fonts or choose a custom font for your terminal. Honestly, fully configurable shortcuts, sorry for the confusion. All trademarks and registered trademarks appearing on oreilly. Terminator status bar opens a menu in which you can define groups of terminals, such as backing up data or searching for files that you can run from Cmd. Linux applications on Windows. -

Windows Terminal Copy Paste
Windows Terminal Copy Paste photosynthesisAdolpho reinterpret hoax. north? Brady Unenvying is nutritionally and corniculatediscontented Umberto after vitreum gelded Israel almost balanced discernibly, his Betjeman though Ravi ingenuously. deflagrating his If you want to impress your friend or your attendees at a session, you can add a gif as a background. No copy and paste on console? The windows terminal app is a tabbed application so it is possible to have multiple tabs for cmd or you can launch powershell, powershell core, etc. What happens to the mass of a burned object? For example, I use Fira Code as font because I like it also in Visual Studio Code. It offers everything you could ask from a terminal emulator, without the glitches of Cmder or Hyper. VM graphics issues and the same also happens in Chromium. Choose what you would like to copy. What is the trick to pasting it into WSL? Would I basically need to change the command to explicitly run wt. How do I use a coupon? We will not be using that Public Key any longer since we have configured it as an authorized key already. Windows to Linux or vice versa. Linux and Windows in terms of a clipboard. It will allow you to paste styled console contents to other applications such as Outlook, Microsoft Word, etc. Click to customize it. In some cases you may not require the text output, and a screenshot is sufficient. There may be more comments in this discussion. One cause for this problem can be your antivirus software. This article is free for everyone, thanks to Medium Members. -

New Model of the IBM Totalstorage Network Attached Storage 300 Family Provides Greater Performance and Scalability
Hardware Announcement October 30, 2001 New Model of the IBM TotalStorage Network Attached Storage 300 Family Provides Greater Performance and Scalability Overview • Tivoli Storage Manager agent update At a Glance The IBM TotalStorage Network Attached Storage (NAS) 300 family, The TotalStorage NAS 300, is Designed to help: delivered fully tested with all announced June 12, 2001, has now • been enhanced with the new IBM components completely assembled Protect your investment and TotalStorage NAS 300 Model 326. into a 36U rack. For currently prepare you for future growth The NAS 300 Model 326 is designed installed 5195-325 systems, NAS with scalable storage capacity to provide greater performance, Release 1 Fixpack (a no-charge field ranging from 109.2 GB to capacity, and granularity to help feature), is available. This Fixpack 6.61 TB upgrades the preloaded operating meet your current and future storage • Reduce installation time with a needs. system and application code to the level of the new models with the fully assembled and tested solution The new Model 326 offers improved: exception of support of new hardware features. Fixes to known • • Improve data availability with Processor speed (1.133 GHz) problems are also included. hot swap power supplies, • automatic system recovery, and Storage capacity, with a choice TotalStorage NAS Family of 73.4 GB HDD or 36.4 HDD Tivoli Storage Manager Agent ′ • The NAS 300 is a member of IBM s • Simplify remote configuration Scalability (from 109.2 GB to NAS family of products, which are 6.61 TB), helping to make future and administration tasks with specifically designed, configured, preloaded tools expansion simple and and packaged to provide solutions to cost-effective help overcome the challenges of cost • Increase system performance The TotalStorage NAS Model 326 effectively sharing, managing, and and availability with a standard provides superior protecting data within complex second engine and second fibre networked-attached storage for network infrastructures. -

Cisco Terminal Services (TS) Agent Guide, Version 1.3
Cisco Terminal Services (TS) Agent Guide, Version 1.3 First Published: 2021-03-02 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387) Fax: 408 527-0883 THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL STATEMENTS, INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL ARE BELIEVED TO BE ACCURATE BUT ARE PRESENTED WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED. USERS MUST TAKE FULL RESPONSIBILITY FOR THEIR APPLICATION OF ANY PRODUCTS. THE SOFTWARE LICENSE AND LIMITED WARRANTY FOR THE ACCOMPANYING PRODUCT ARE SET FORTH IN THE INFORMATION PACKET THAT SHIPPED WITH THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO LOCATE THE SOFTWARE LICENSE OR LIMITED WARRANTY, CONTACT YOUR CISCO REPRESENTATIVE FOR A COPY. The Cisco implementation of TCP header compression is an adaptation of a program developed by the University of California, Berkeley (UCB) as part of UCB's public domain version of the UNIX operating system. All rights reserved. Copyright © 1981, Regents of the University of California. NOTWITHSTANDING ANY OTHER WARRANTY HEREIN, ALL DOCUMENT FILES AND SOFTWARE OF THESE SUPPLIERS ARE PROVIDED “AS IS" WITH ALL FAULTS. CISCO AND THE ABOVE-NAMED SUPPLIERS DISCLAIM ALL WARRANTIES, EXPRESSED OR IMPLIED, INCLUDING, WITHOUT LIMITATION, THOSE OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OR ARISING FROM A COURSE OF DEALING, USAGE, OR TRADE PRACTICE. IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL DAMAGES, INCLUDING, WITHOUT LIMITATION, LOST PROFITS OR LOSS OR DAMAGE TO DATA ARISING OUT OF THE USE OR INABILITY TO USE THIS MANUAL, EVEN IF CISCO OR ITS SUPPLIERS HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. -

Peoplesoft Financials for Macintosh Users
PeopleSoft Financials for Macintosh 1. Open Remote Desktop Connection located in your Applications folder 2. Type or select computer name: windows.tcu.edu and select the Connect button. 3. You will be connected to a Windows Terminal server. Enter your TCU username and password. Be sure to enter TCU for the Domain. 4. If you see an error window regarding a certificate error, click Continue. 1 5. You are now logged into a Windows Terminal Server. You may need to use the scroll bars on the right and bottom sides of the window to move around and view the entire window. 6. Locate Internet Explorer and open it by double-clicking the icon. 7. Login to http://my.tcu.edu, and select Department/Budget Manager. 8. Select Financial Reports – Portal 2 Documentation for report creation is available in the links near the bottom of the window. (See the image below.) Also training classes are available. 3 9. After running a report from the windows terminal server, the report window will not automatically open. You must choose the Report Manager link to open the report. 10. From the Report Manager, click the filename link to open the report. 11. When finished running reports, don’t forget to log out of the terminal server. Locate the Start button at the bottom left corner of the window Click the Start button and select Log off. Helpful Tips and Troubleshooting 4 Activate Drilldown Add-In in Excel 2013 or 2016 • Open Excel 2013 or 2016 • Click the File tab in the upper left corner of the window • Select Options • Choose Add-Ins from the left menu • Click -

Introducing Windows Server X64 on IBM Eserver Xseries Servers
IBM Front cover Introducing Windows Server x64 on IBM Eserver xSeries Servers Describes the new 64-bit operating system from Microsoft Lists support for key server applications and xSeries tools Provides migration information and scenarios David Watts Darryl Miles Piotr Pietrzak ibm.com/redbooks Redpaper International Technical Support Organization Introducing Windows Server x64 on IBM Eserver xSeries Servers June 2005 Note: Before using this information and the product it supports, read the information in “Notices” on page v. First Edition (June 2005) This edition applies to Windows Server 2003, x64 Edition. This document created or updated on June 21, 2005. © Copyright International Business Machines Corporation 2005. All rights reserved. Note to U.S. Government Users Restricted Rights -- Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Notices . .v Trademarks . vi Preface . vii The team that wrote this Redpaper . vii Become a published author . viii Comments welcome. ix Chapter 1. Introduction to this paper . 1 1.1 Benefits of Windows Server 2003, x64 Edition . 2 1.1.1 Technical benefits . 2 1.1.2 Business benefits . 2 1.2 Why now? . 3 1.3 64-bit misconceptions . 4 1.3.1 Processor performance. 4 1.3.2 Not all 64-bit Windows are the same . 4 1.3.3 Application performance . 5 Chapter 2. Hardware technology . 7 2.1 What makes a 64-bit processor . 8 2.2 AMD and Intel processors. 9 2.3 Intel Xeon with Extended Memory 64 Technology . 10 2.4 AMD Opteron™ processor . 14 2.5 Memory addressing. 16 2.5.1 The 4 GB memory limit with 32-bit operating systems . -

Asp.Net Core and Azure with Raspberry Pi 4
TECHNOLOGY IN ACTION™ Asp.Net Core and Azure with Raspberry Pi 4 .Net Core Applications in Raspbian OS — Sibeesh Venu Asp.Net Core and Azure with Raspberry Pi 4 .Net Core Applications in Raspbian OS Sibeesh Venu Asp.Net Core and Azure with Raspberry Pi 4: .Net Core Applications in Raspbian OS Sibeesh Venu Birkenfeld, Germany ISBN-13 (pbk): 978-1-4842-6442-3 ISBN-13 (electronic): 978-1-4842-6443-0 https://doi.org/10.1007/978-1-4842-6443-0 Copyright © 2020 by Sibeesh Venu This work is subject to copyright. All rights are reserved by the Publisher, whether the whole or part of the material is concerned, specifically the rights of translation, reprinting, reuse of illustrations, recitation, broadcasting, reproduction on microfilms or in any other physical way, and transmission or information storage and retrieval, electronic adaptation, computer software, or by similar or dissimilar methodology now known or hereafter developed. Trademarked names, logos, and images may appear in this book. Rather than use a trademark symbol with every occurrence of a trademarked name, logo, or image we use the names, logos, and images only in an editorial fashion and to the benefit of the trademark owner, with no intention of infringement of the trademark. The use in this publication of trade names, trademarks, service marks, and similar terms, even if they are not identified as such, is not to be taken as an expression of opinion as to whether or not they are subject to proprietary rights. While the advice and information in this book are believed to be true and accurate at the date of publication, neither the authors nor the editors nor the publisher can accept any legal responsibility for any errors or omissions that may be made. -

IBM Totalstorage NAS 100 System — Now Automatically Available to All IBM Personal Computer Division Business Partners
Hardware Announcement October 22, 2002 IBM TotalStorage NAS 100 System — Now Automatically Available to All IBM Personal Computer Division Business Partners Overview • Power supply — 162-watt, auto-sensing, auto-ranging supply At a Glance The IBM TotalStorage NAS 100, 5190 Model R12, introduced in Preloaded Operating System and The IBM TotalStorage NAS 100 can Hardware Announcement 102-185, Application Code now be ordered by part number. The NAS 100 provides entry-level dated July 9, 2002, is now available • Operating system — Windows networked storage at an attractive to IBM Personal Computer Division Powered OS (PCD) Business Partners. All PCD price point. Highlights include: • — Business Partners will be File access protocols CIFS, • automatically approved to remarket NFS, NetWare, Apple File 480 GB capacity the NAS 100 which is in Category S5 Protocol, HTTP, FTP • The power of a 1.26 GHz of the Storage Products Table of IBM • Pentium III processor Business Partner Exhibit (Z125-5505). Systems management — IBM Director Agent/Universal • Two Copper 10/100/1000 Mbps The NAS 100 is the entry-level Manageability Services Ethernet ports member of the IBM family of Network • Backup/restore — MS Backup, Attached Storage (NAS) products • Support of CIFS, NFS, NetWare, CDP Persistent Storage Manager, and is characterized by many of the Apple File Protocol, HTTP, and Tivoli Storage Manager Agent same features and attributes as FTP protocols other NAS family members. The • Setup/configuration support — • Powerful systems management NAS 100 Model