Windows Terminal Copy Paste
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Marketdirect Storefront® Release Notes
MarketDirect StoreFront® Release Notes Version 12.2 2 ⚫ EFI Productivity Suite | MarketDirect StoreFront 12.2 Release Notes Copyright © 2004 - 2021 by Electronics for Imaging, Inc. All Rights Reserved. EFI Productivity Suite | MarketDirect StoreFront Release Notes August 2021 MarketDirect StoreFront v. 12.2 Document version 1.0 / 45145977 This publication is protected by copyright, and all rights are reserved. No part of it may be reproduced or transmitted in any form or by any means for any purpose without express prior written consent from Electronics for Imaging, Inc. Information in this document is subject to change without notice and does not represent a commitment on the part of Electronics for Imaging, Inc. Patents This product may be covered by one or more of the following U.S. Patents: 4,716,978, 4,828,056, 4,917,488, 4,941,038, 5,109,241, 5,170,182, 5,212,546, 5,260,878, 5,276,490, 5,278,599, 5,335,040, 5,343,311, 5,398,107, 5,424,754, 5,442,429, 5,459,560, 5,467,446, 5,506,946, 5,517,334, 5,537,516, 5,543,940, 5,553,200, 5,563,689, 5,565,960, 5,583,623, 5,596,416, 5,615,314, 5,619,624, 5,625,712, 5,640,228, 5,666,436, 5,745,657, 5,760,913, 5,799,232, 5,818,645, 5,835,788, 5,859,711, 5,867,179, 5,940,186, 5,959,867, 5,970,174, 5,982,937, 5,995,724, 6,002,795, 6,025,922, 6,035,103, 6,041,200, 6,065,041, 6,112,665, 6,116,707, 6,122,407, 6,134,018, 6,141,120, 6,166,821, 6,173,286, 6,185,335, 6,201,614, 6,215,562, 6,219,155, 6,219,659, 6,222,641, 6,224,048, 6,225,974, 6,226,419, 6,238,105, 6,239,895, 6,256,108, 6,269,190, 6,271,937, -

Ubuntu Kung Fu
Prepared exclusively for Alison Tyler Download at Boykma.Com What readers are saying about Ubuntu Kung Fu Ubuntu Kung Fu is excellent. The tips are fun and the hope of discov- ering hidden gems makes it a worthwhile task. John Southern Former editor of Linux Magazine I enjoyed Ubuntu Kung Fu and learned some new things. I would rec- ommend this book—nice tips and a lot of fun to be had. Carthik Sharma Creator of the Ubuntu Blog (http://ubuntu.wordpress.com) Wow! There are some great tips here! I have used Ubuntu since April 2005, starting with version 5.04. I found much in this book to inspire me and to teach me, and it answered lingering questions I didn’t know I had. The book is a good resource that I will gladly recommend to both newcomers and veteran users. Matthew Helmke Administrator, Ubuntu Forums Ubuntu Kung Fu is a fantastic compendium of useful, uncommon Ubuntu knowledge. Eric Hewitt Consultant, LiveLogic, LLC Prepared exclusively for Alison Tyler Download at Boykma.Com Ubuntu Kung Fu Tips, Tricks, Hints, and Hacks Keir Thomas The Pragmatic Bookshelf Raleigh, North Carolina Dallas, Texas Prepared exclusively for Alison Tyler Download at Boykma.Com Many of the designations used by manufacturers and sellers to distinguish their prod- ucts are claimed as trademarks. Where those designations appear in this book, and The Pragmatic Programmers, LLC was aware of a trademark claim, the designations have been printed in initial capital letters or in all capitals. The Pragmatic Starter Kit, The Pragmatic Programmer, Pragmatic Programming, Pragmatic Bookshelf and the linking g device are trademarks of The Pragmatic Programmers, LLC. -

Powerview Command Reference
PowerView Command Reference TRACE32 Online Help TRACE32 Directory TRACE32 Index TRACE32 Documents ...................................................................................................................... PowerView User Interface ............................................................................................................ PowerView Command Reference .............................................................................................1 History ...................................................................................................................................... 12 ABORT ...................................................................................................................................... 13 ABORT Abort driver program 13 AREA ........................................................................................................................................ 14 AREA Message windows 14 AREA.CLEAR Clear area 15 AREA.CLOSE Close output file 15 AREA.Create Create or modify message area 16 AREA.Delete Delete message area 17 AREA.List Display a detailed list off all message areas 18 AREA.OPEN Open output file 20 AREA.PIPE Redirect area to stdout 21 AREA.RESet Reset areas 21 AREA.SAVE Save AREA window contents to file 21 AREA.Select Select area 22 AREA.STDERR Redirect area to stderr 23 AREA.STDOUT Redirect area to stdout 23 AREA.view Display message area in AREA window 24 AutoSTOre .............................................................................................................................. -

Blue Coat SGOS Command Line Interface Reference, Version 4.2.3
Blue Coat® Systems ProxySG™ Command Line Interface Reference Version SGOS 4.2.3 Blue Coat ProxySG Command Line Interface Reference Contact Information Blue Coat Systems Inc. 420 North Mary Ave Sunnyvale, CA 94085-4121 http://www.bluecoat.com/support/contact.html [email protected] http://www.bluecoat.com For concerns or feedback about the documentation: [email protected] Copyright© 1999-2006 Blue Coat Systems, Inc. All rights reserved worldwide. No part of this document may be reproduced by any means nor modified, decompiled, disassembled, published or distributed, in whole or in part, or translated to any electronic medium or other means without the written consent of Blue Coat Systems, Inc. All right, title and interest in and to the Software and documentation are and shall remain the exclusive property of Blue Coat Systems, Inc. and its licensors. ProxySG™, ProxyAV™, CacheOS™, SGOS™, Spyware Interceptor™, Scope™, RA Connector™, RA Manager™, Remote Access™ are trademarks of Blue Coat Systems, Inc. and CacheFlow®, Blue Coat®, Accelerating The Internet®, WinProxy®, AccessNow®, Ositis®, Powering Internet Management®, The Ultimate Internet Sharing Solution®, Permeo®, Permeo Technologies, Inc.®, and the Permeo logo are registered trademarks of Blue Coat Systems, Inc. All other trademarks contained in this document and in the Software are the property of their respective owners. BLUE COAT SYSTEMS, INC. DISCLAIMS ALL WARRANTIES, CONDITIONS OR OTHER TERMS, EXPRESS OR IMPLIED, STATUTORY OR OTHERWISE, ON SOFTWARE AND DOCUMENTATION FURNISHED HEREUNDER INCLUDING WITHOUT LIMITATION THE WARRANTIES OF DESIGN, MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL BLUE COAT SYSTEMS, INC., ITS SUPPLIERS OR ITS LICENSORS BE LIABLE FOR ANY DAMAGES, WHETHER ARISING IN TORT, CONTRACT OR ANY OTHER LEGAL THEORY EVEN IF BLUE COAT SYSTEMS, INC. -

Your Guide to Installing and Using Coastal Explorer EXPLORING COASTAL EXPLORER Version 4
EXPLORING COASTAL EXPLORER Your guide to installing and using Coastal Explorer EXPLORING COASTAL EXPLORER Version 4 Your guide to installing and using Coastal Explorer Copyright © 2017 Rose Point Navigation Systems. All rights reserved. Rose Point Navigation Systems, Coastal Explorer, and Coastal Explorer Network are trademarks of Rose Point Navigation Systems. The names of any other companies and/or products mentioned herein may be the trademarks of their respective owners. WARNINGS: Use Coastal Explorer at your own risk. Be sure to carefully read and understand the user's manual and practice operation prior to actual use. Coastal Explorer depends on information from the Global Position System (GPS) and digital charts, both of which may contain errors. Navigators should be aware that GPS- derived positions are often of higher accuracy than the positions of charted data. Rose Point Navigation Systems does not warrant the accuracy of any information presented by Coastal Explorer. Coastal Explorer is intended to be used as a supplementary aid to navigation and must not be considered a replacement for official government charts, notices to mariners, tide and current tables, and/or other reference materials. The captain of a vessel is ultimately responsible for its safe navigation and the prudent mariner does not rely on any single source of information. The information in this manual is subject to change without notice. Rose Point Navigation Systems 18005 NE 68th Street Suite A100 Redmond, WA 98052 Phone: 425-605-0985 Fax: 425-605-1285 e-mail: [email protected] www.rosepoint.com Welcome to Coastal Explorer Thank you for choosing Coastal Explorer! If you are new to navigation software, but use a computer for anything else, you will find that Coastal Explorer works just like many other Windows applications: you create documents, edit them, save them, print them, etc. -

VNC User Guide 7 About This Guide
VNC® User Guide Version 5.3 December 2015 Trademarks RealVNC, VNC and RFB are trademarks of RealVNC Limited and are protected by trademark registrations and/or pending trademark applications in the European Union, United States of America and other jursidictions. Other trademarks are the property of their respective owners. Protected by UK patent 2481870; US patent 8760366 Copyright Copyright © RealVNC Limited, 2002-2015. All rights reserved. No part of this documentation may be reproduced in any form or by any means or be used to make any derivative work (including translation, transformation or adaptation) without explicit written consent of RealVNC. Confidentiality All information contained in this document is provided in commercial confidence for the sole purpose of use by an authorized user in conjunction with RealVNC products. The pages of this document shall not be copied, published, or disclosed wholly or in part to any party without RealVNC’s prior permission in writing, and shall be held in safe custody. These obligations shall not apply to information which is published or becomes known legitimately from some source other than RealVNC. Contact RealVNC Limited Betjeman House 104 Hills Road Cambridge CB2 1LQ United Kingdom www.realvnc.com Contents About This Guide 7 Chapter 1: Introduction 9 Principles of VNC remote control 10 Getting two computers ready to use 11 Connectivity and feature matrix 13 What to read next 17 Chapter 2: Getting Connected 19 Step 1: Ensure VNC Server is running on the host computer 20 Step 2: Start VNC -

Automated Malware Analysis Report for Oldnewexplorercfg.Exe
ID: 152305 Sample Name: OldNewExplorerCfg.exe Cookbook: default.jbs Time: 03:48:12 Date: 15/07/2019 Version: 26.0.0 Aquamarine Table of Contents Table of Contents 2 Analysis Report OldNewExplorerCfg.exe 5 Overview 5 General Information 5 Detection 5 Confidence 6 Classification 6 Analysis Advice 6 Mitre Att&ck Matrix 7 Signature Overview 7 AV Detection: 7 Spreading: 7 Networking: 7 Key, Mouse, Clipboard, Microphone and Screen Capturing: 7 DDoS: 8 System Summary: 8 Data Obfuscation: 8 Hooking and other Techniques for Hiding and Protection: 8 Malware Analysis System Evasion: 8 Anti Debugging: 8 HIPS / PFW / Operating System Protection Evasion: 8 Language, Device and Operating System Detection: 8 Behavior Graph 9 Simulations 9 Behavior and APIs 9 Antivirus and Machine Learning Detection 9 Initial Sample 9 Dropped Files 9 Unpacked PE Files 9 Domains 10 URLs 10 Yara Overview 10 Initial Sample 10 PCAP (Network Traffic) 10 Dropped Files 10 Memory Dumps 10 Unpacked PEs 10 Joe Sandbox View / Context 10 IPs 10 Domains 10 ASN 10 JA3 Fingerprints 10 Dropped Files 10 Screenshots 10 Thumbnails 11 Startup 11 Created / dropped Files 12 Domains and IPs 12 Contacted Domains 12 URLs from Memory and Binaries 12 Contacted IPs 12 Static File Info 12 General 12 File Icon 13 Static PE Info 13 General 13 Entrypoint Preview 13 Data Directories 14 Sections 14 Copyright Joe Security LLC 2019 Page 2 of 27 Resources 14 Imports 15 Version Infos 16 Possible Origin 16 Network Behavior 17 Code Manipulations 17 Statistics 17 Behavior 17 System Behavior 17 Analysis Process: -
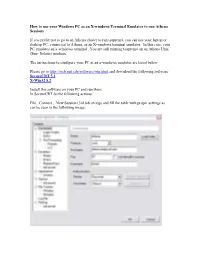
How to Use Your Windows PC As an X-Windows Terminal Emulator to Run Athena Sessions
How to use your Windows PC as an X-windows Terminal Emulator to run Athena Sessions If you prefer not to go to an Athena cluster to run tsuprem4, you can use your laptop or desktop PC, connected to Athena, as an X-windows terminal emulator. In this case, your PC emulates an x-windows terminal. You are still running tsuprem4 on an Athena Unix (Sun- Solaris) machine. The instructions to configure your PC as an x-windows emulator are listed below: Please go to http://web.mit.edu/software/win.html and download the following software: SecureCRT 5.1 X-Win32 8.2 Install this software on your PC and run them. In SecureCRT do the following actions: File...Connect....New Session (3rd tab on top) and fill the table with proper settings as can be seen in the following image: Fill the username field with your Kerberos username and press OK to run and insert your password. Run Xwin32 or Exceed if you have it (Exceed is not available on the MIT website but is available for purchase). In order to see images when running tsuprem4, you need to adjust the DISPLAY system variable according to your IP address. A simple way of getting your IP address, is typing the "setenv" command in SecureCRT screen. You will see something similar to this (with different numbers/characters): USER=pouya LOGNAME=pouya HOME=/afs/athena.mit.edu/user/p/o/pouya PATH=/srvd/patch:/usr/athena/bin:/usr/athena/etc:/bin/athena:/usr/openwin/bin:/usr/open win/demo:/usr/dt/bin:/usr/bin:/usr/ccs/bin:/usr/sbin:/sbin:/usr/sfw/bin:/usr/ucb:.:/mit/avant i/arch/sun4x_510/bin:/mit/matlab/arch/sun4x_510/bin:/mit/maple/arch/sun4x_59/bin MAIL=/var/mail//pouya SHELL=/bin/athena/tcsh TZ=US/Eastern SSH_CLIENT=18.62.30.76 2304 22 SSH_CONNECTION=18.62.30.76 2304 18.7.18.74 22 SSH_TTY=/dev/pts/59 ..... -

Implementation of Clipboard Security Using Cryptographic Techniques
International Journal of Computer Applications (0975 – 8887) Volume 86 – No 6, January 2014 Implementation of Clipboard Security using Cryptographic Techniques Gaurav Pathak Gaurav Kumar Tak Department of Computer Department of Computer Science and Engineering Science and Engineering Lovely Professional University Lovely Professional University Phagwara, India Phagwara, India ABSTRACT looking malicious content. So security to clipboard content is In the present scenario malicious authors are rapidly growing issue of concern and need to enhance the functionality of and now other than internet users they are also targeting the operating system by which we can protect our clipboard data loophole in operating system application level security. from being got watched. Transferring data between applications is common user From the study of recent papers and market reports, clipboard activity. Since data in a clipboard is freely delivered between security becomes important issue of concern in data security. arbitrary programs capable of using a format of the data, a According to the google forum [6] there is being the great simple text, a rich text, a picture, and information having a threat to the clipboard security in which they talk about particular format may be delivered between programs capable ClipNote that can monitor the system clipboard of using such information. Information delivery made and collect all clipboard entries. That ClipNote application between programs through a clipboard is undoubtedly an does not require any special permission to run. That means efficient method of properly using a multitasking function of any malware can steal passwords by just monitoring the an operating system, but as the security of important data is system clipboard in the background, which become great increasingly demanded, data transmitted between independent threat to the client’s system. -

Gotomypc® User Guide
GoToMyPC® User Guide GoToMyPC GoToMyPC Pro GoToMyPC Corporate Citrix Online 6500 Hollister Avenue • Goleta CA 93117 +1-805-690-6400 • Fax: +1-805-690-6471 © 2009 Citrix Online, LLC. All rights reserved. GoToMyPC® User Guide Contents Welcome ........................................................................................... 4 Getting Started .................................................................................. 1 System Requirements ....................................................................... 1 Notes on Installation and Feature Access ............................................. 1 Versions of GoToMyPC ...................................................................... 1 Mac Users .................................................................................... 1 Upgrade Information ......................................................................... 2 Useful GoToMyPC Terms .................................................................... 4 Features ......................................................................................... 5 Set Up a Host Computer .................................................................... 6 Create Your Account (first-time users) .............................................. 6 Set Up a Host PC ........................................................................... 7 Leaving the Host Computer Accessible................................................. 8 Managing Billing and Account Information ........................................ 9 Change Your -

PATHWORKS for DOS Microsoft Windows Support Guide
PATHWORKS for DOS ' Microsoft Windows Support Guide PATHWORKS for DOS Microsoft Windows Support Guide Order Number: AA-MF87D-TH August 1991 Revision/Update Information: This document supersedes Microsoft Windows Support Guide, order number AA-MF87C-TH. Software Version: PATHWORKS for DOS Version 4.1 Digital Equipment Corporation Maynard, Massachusetts First Published, October 1988 Revised, April 1989, July 1990, October 1990, January 1991, August 1991 The infonnation in this document is subject to change without notice and should not be construed as a commitment by Digital Equipment Corporation. Digital Equipment Corporation assumes no responsibility for any errors that may appear in this document. The software described in this document is furnished under a license and may be used or copied only in accordance with the terms of such license. No responsibility is assumed for the use or reliability of software on equipment that is not supplied by Digital Equipment Corporation or its affiliated companies. Restricted Rights: Use, duplication, or disclosure by the U.S. Government is subject to restrictions as set forth in subparagraph (c)(l)(ii) of the Rights in Technical Data and Computer Software clause at DFARS 252.227-7013. © Digital Equipment Corporation 1988, 1989, 1990, 1991. All Rights Reserved. Printed in U.S.A. The postpaid Reader's Comments fonn at the end of this document requests your critical evaluation to assist in preparing future documentation. The following are trademarks of Digital Equipment Corporation: ALL-IN-I, DDCMP, DDIF, DEC, DECconnect, DEClaser, DE Cmate , DECnet, DECnet-DOS, DECpc, DECrouter, DECSA, DE C server, DECstation, DECwindows, DECwrite, DELNI, DEMPR, DEPCA, DESTA, Digital, DNA, EtherWORKS, LA50, LA75 Companion, LAT, LN03, LN03 PLUS, LN03 ScriptPrinter, METROWAVE, MicroVAX, PATHWORKS, PrintServer, ReGIS, RMS-ll, RSX, RSX-ll, RT, RT-ll, RX33, ThinWire, TK, ULTRIX, VAX, VAX Notes, VAXcluster, VAXmate, VAXmail, VAXserver, VAXshare, VMS, VT, WPS, WPS.PLUS, and the DIGITAL logo. -

Cheatsheet V2.4.Pdf
! ! 2.4!Edition! Cross!reference!processes!with!various!lists:! Scan!a!block!of!code!in!process!or!kernel!memory! psxview! for!imported!APIs:! ! impscan!! Show!processes!in!parent/child!tree:! !!!!Hp/HHpid=PID!!!!!!!!!Process!ID!! pstree! !!!!Hb/HHbase=BASE!!!Base!address!to!scan! & !!!!Hs/HHsize=SIZE!!!!!!!Size!to!scan!from!start!of!base! Process&Information& ! ! Logs&/&Histories& Specify!–o/HHoffset=OFFSET!or!Hp/HHpid=1,2,3!! ! ! Recover!event!logs!(XP/2003):! Display!DLLs:! evtlogs!! ! ! dlllist! !!!!HS/HHsaveHevt!!!!!!!!!!!!!!!!!!!!Save!raw!event!logs! Development!build!and!wiki:! ! !!!!HD/HHdumpHdir=PATH!!!Write!to!this!directory! github.com/volatilityfoundation!! Show!command!line!arguments:! ! ! cmdline! Recover!command!history:! Download!a!stable!release:! ! cmdscan!and!consoles!! volatilityfoundation.org!! Display!details!on!VAD!allocations:! ! ! vadinfo![HHaddr]! Recover!IE!cache/Internet!history:! Read!the!book:! ! iehistory!! artofmemoryforensics.com! Dump!allocations!to!individual!files:! ! ! vaddump!HHdumpHdir=PATH![HHbase]! Show!running!services:! Development!Team!Blog:! ! svcscan!! http://volatilityHlabs.blogspot.com!! Dump!all!valid!pages!to!a!single!file:! !!!!Hv/HHverbose!!!!Show!ServiceDll!from!registry! ! memdump!HHdumpHdir=PATH! ! (Official)!Training!Contact:! ! Networking&Information& Display!open!handles:! [email protected]!! ! handles!! ! Active!info!(XP/2003):! !!!!Ht/HHobjectHtype=TYPE!!!Mutant,!File,!Key,!etc…! Follow:!@volatility! connections!and!sockets!! !!!!Hs/HHsilent!!!!!!!!!!!!!!!!!!!!!!!!!!!Hide!unnamed!handles!