Gateway for Windowstm Reference Manual
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Marketdirect Storefront® Release Notes
MarketDirect StoreFront® Release Notes Version 12.2 2 ⚫ EFI Productivity Suite | MarketDirect StoreFront 12.2 Release Notes Copyright © 2004 - 2021 by Electronics for Imaging, Inc. All Rights Reserved. EFI Productivity Suite | MarketDirect StoreFront Release Notes August 2021 MarketDirect StoreFront v. 12.2 Document version 1.0 / 45145977 This publication is protected by copyright, and all rights are reserved. No part of it may be reproduced or transmitted in any form or by any means for any purpose without express prior written consent from Electronics for Imaging, Inc. Information in this document is subject to change without notice and does not represent a commitment on the part of Electronics for Imaging, Inc. Patents This product may be covered by one or more of the following U.S. Patents: 4,716,978, 4,828,056, 4,917,488, 4,941,038, 5,109,241, 5,170,182, 5,212,546, 5,260,878, 5,276,490, 5,278,599, 5,335,040, 5,343,311, 5,398,107, 5,424,754, 5,442,429, 5,459,560, 5,467,446, 5,506,946, 5,517,334, 5,537,516, 5,543,940, 5,553,200, 5,563,689, 5,565,960, 5,583,623, 5,596,416, 5,615,314, 5,619,624, 5,625,712, 5,640,228, 5,666,436, 5,745,657, 5,760,913, 5,799,232, 5,818,645, 5,835,788, 5,859,711, 5,867,179, 5,940,186, 5,959,867, 5,970,174, 5,982,937, 5,995,724, 6,002,795, 6,025,922, 6,035,103, 6,041,200, 6,065,041, 6,112,665, 6,116,707, 6,122,407, 6,134,018, 6,141,120, 6,166,821, 6,173,286, 6,185,335, 6,201,614, 6,215,562, 6,219,155, 6,219,659, 6,222,641, 6,224,048, 6,225,974, 6,226,419, 6,238,105, 6,239,895, 6,256,108, 6,269,190, 6,271,937, -

Office DDE – Code Execution Without Macros
Cyber Threat Intelligence Report office DDe – coDe execution without macros teChniCal threat analysis Cyber Threat Intelligence (CTI) Team Telekom Security T-Systems International GmbH Contact: [email protected] Document ProPerties Version 1.1 ClassifiCation leVel Public filename CTI_Report_OFFICE_DDE_THREAT_ANALYSIS.docx Keywords Malicious office documents, DDE, dynamic data exchange Create date 11/07/2017 04:13:00 PM last Changed 13.04.2018 10:58:00 AM offiCe DDE – Code exeCution without maCros 1.1 Cyber Threat Intelligence Report office DDe – coDe execution without macros ........................................................................ 1 1 summary ............................................................................................................................ 3 2 Dynamic Data exchange (DDe) .......................................................................................... 4 3 subject of investigation .................................................................................................. 8 4 analysis ............................................................................................................................ 10 4.1 Distribution OF Locky/Trickbot ............................................................................................ 10 4.2 Distribution of Cerber .......................................................................................................... 14 4.3 Distribution of Vortex ......................................................................................................... -
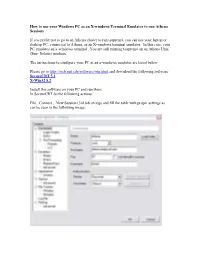
How to Use Your Windows PC As an X-Windows Terminal Emulator to Run Athena Sessions
How to use your Windows PC as an X-windows Terminal Emulator to run Athena Sessions If you prefer not to go to an Athena cluster to run tsuprem4, you can use your laptop or desktop PC, connected to Athena, as an X-windows terminal emulator. In this case, your PC emulates an x-windows terminal. You are still running tsuprem4 on an Athena Unix (Sun- Solaris) machine. The instructions to configure your PC as an x-windows emulator are listed below: Please go to http://web.mit.edu/software/win.html and download the following software: SecureCRT 5.1 X-Win32 8.2 Install this software on your PC and run them. In SecureCRT do the following actions: File...Connect....New Session (3rd tab on top) and fill the table with proper settings as can be seen in the following image: Fill the username field with your Kerberos username and press OK to run and insert your password. Run Xwin32 or Exceed if you have it (Exceed is not available on the MIT website but is available for purchase). In order to see images when running tsuprem4, you need to adjust the DISPLAY system variable according to your IP address. A simple way of getting your IP address, is typing the "setenv" command in SecureCRT screen. You will see something similar to this (with different numbers/characters): USER=pouya LOGNAME=pouya HOME=/afs/athena.mit.edu/user/p/o/pouya PATH=/srvd/patch:/usr/athena/bin:/usr/athena/etc:/bin/athena:/usr/openwin/bin:/usr/open win/demo:/usr/dt/bin:/usr/bin:/usr/ccs/bin:/usr/sbin:/sbin:/usr/sfw/bin:/usr/ucb:.:/mit/avant i/arch/sun4x_510/bin:/mit/matlab/arch/sun4x_510/bin:/mit/maple/arch/sun4x_59/bin MAIL=/var/mail//pouya SHELL=/bin/athena/tcsh TZ=US/Eastern SSH_CLIENT=18.62.30.76 2304 22 SSH_CONNECTION=18.62.30.76 2304 18.7.18.74 22 SSH_TTY=/dev/pts/59 ..... -

PATHWORKS for DOS Microsoft Windows Support Guide
PATHWORKS for DOS ' Microsoft Windows Support Guide PATHWORKS for DOS Microsoft Windows Support Guide Order Number: AA-MF87D-TH August 1991 Revision/Update Information: This document supersedes Microsoft Windows Support Guide, order number AA-MF87C-TH. Software Version: PATHWORKS for DOS Version 4.1 Digital Equipment Corporation Maynard, Massachusetts First Published, October 1988 Revised, April 1989, July 1990, October 1990, January 1991, August 1991 The infonnation in this document is subject to change without notice and should not be construed as a commitment by Digital Equipment Corporation. Digital Equipment Corporation assumes no responsibility for any errors that may appear in this document. The software described in this document is furnished under a license and may be used or copied only in accordance with the terms of such license. No responsibility is assumed for the use or reliability of software on equipment that is not supplied by Digital Equipment Corporation or its affiliated companies. Restricted Rights: Use, duplication, or disclosure by the U.S. Government is subject to restrictions as set forth in subparagraph (c)(l)(ii) of the Rights in Technical Data and Computer Software clause at DFARS 252.227-7013. © Digital Equipment Corporation 1988, 1989, 1990, 1991. All Rights Reserved. Printed in U.S.A. The postpaid Reader's Comments fonn at the end of this document requests your critical evaluation to assist in preparing future documentation. The following are trademarks of Digital Equipment Corporation: ALL-IN-I, DDCMP, DDIF, DEC, DECconnect, DEClaser, DE Cmate , DECnet, DECnet-DOS, DECpc, DECrouter, DECSA, DE C server, DECstation, DECwindows, DECwrite, DELNI, DEMPR, DEPCA, DESTA, Digital, DNA, EtherWORKS, LA50, LA75 Companion, LAT, LN03, LN03 PLUS, LN03 ScriptPrinter, METROWAVE, MicroVAX, PATHWORKS, PrintServer, ReGIS, RMS-ll, RSX, RSX-ll, RT, RT-ll, RX33, ThinWire, TK, ULTRIX, VAX, VAX Notes, VAXcluster, VAXmate, VAXmail, VAXserver, VAXshare, VMS, VT, WPS, WPS.PLUS, and the DIGITAL logo. -

U3-1033 Ovation Netdde Server
Ovation NetDDE Server User Guide Section Title Page Summary of Changes Section 1. Introduction 1-1. Overview. 1-1 1-2. NetDDE Server Features. 1-1 1-3. DDE Overview . 1-2 1-3.1. Application or Service Name. 1-2 1-3.2. Topic . 1-2 1-3.3. Item . 1-3 1-3.4. Network DDE . 1-4 1-4. Limitations . 1-5 Section 2. Getting Started 2-1. Section Overview . 2-1 2-2. Requirements . 2-1 2-2.1. System . 2-1 2-2.2. Hardware . 2-1 2-2.3. Software . 2-2 2-2.4. License Server . 2-2 2-3. Setup . 2-4 2-3.1. Environment Variables Required for Setup. 2-5 2-3.2. Linked Libraries. 2-6 2-3.3. Files Installed During Setup. 2-7 2-3.4. Registry Entries . 2-8 2-3.5. Security . 2-10 2-4. Setup Procedure . 2-10 2-5. Configuration . 2-11 2-5.1. Permissions . 2-11 2-6. Un-installation. 2-11 Section 3. Using NetDDE 3-1. Section Overview . 3-1 3-2. Syntax for Calls. 3-1 Glossary Index 12/00 i U3-1033 (Rev 1) Westinghouse Process Control, Inc. Proprietary Class 2C Summary of Changes This revision of “Ovation NetDDE Server User Guide” (U3-1033) reflects the following changes: • System topic has now been changed to wwwdde_system. • DataCreate and DataOriginate topics are removed from the WDPF NetDDE Server. • The machine name must appear when the point information (or Item) link is created on the WDPF NetDDE Server machine or accessed remotely in Excel or any other DDE supported application. -

Winwedge Users Manual
Version 3.0 Professional Edition 1 License Agreement: ........................................................................................................................2 What is the Software Wedge? ........................................................................................................3 What can you do with the Software Wedge?..................................................................................3 Before You Begin ............................................................................................................................4 System Requirements .................................................................................................................4 Devices Compatible with the Software Wedge............................................................................4 What's New In Version 3.0 ..........................................................................................................5 Why Is It Called the Software Wedge?........................................................................................5 Who’s Using The Software Wedge.................................................................................................6 Getting Started................................................................................................................................7 Installing and Running the Software Wedge ...............................................................................7 How To Obtain Technical Support...............................................................................................7 -

System Design Strategies 26Th Edition an ESRI ® Technical Reference Document • August 2009
System Design Strategies 26th Edition An ESRI ® Technical Reference Document • August 2009 Prepared by: Dave Peters Systems Integration Environmental Systems Research Institute, Inc. 380 New York Street Redlands, California 92373-8100 Copyright © 2009 ESRI All rights reserved. Printed in the United States of America. The information contained in this document is the exclusive property of ESRI. This work is protected under United States copyright law and other international copyright treaties and conventions. No part of this work may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying and recording, or by any information storage or retrieval system, except as expressly permitted in writing by ESRI. All requests should be sent to Attention: Contracts and Legal Services Manager, ESRI, 380 New York Street, Redlands, CA 92373-8100 USA. The information contained in this document is subject to change without notice. U.S. GOVERNMENT RESTRICTED/LIMITED RIGHTS Any software, documentation, and/or data delivered hereunder is subject to the terms of the License Agreement. In no event shall the U.S. Government acquire greater than RESTRICTED/LIMITED RIGHTS. At a minimum, use, duplication, or disclosure by the U.S. Government is subject to restrictions as set forth in FAR §52.227-14 Alternates I, II, and III (JUN 1987); FAR §52.227-19 (JUN 1987) and/or FAR §12.211/12.212 (Commercial Technical Data/Computer Software); and DFARS §252.227-7015 (NOV 1995) (Technical Data) and/or DFARS §227.7202 (Computer Software), as applicable. Contractor/Manufacturer is ESRI, 380 New York Street, Redlands, CA 92373-8100 USA. -

The Old New Thing: Practical Development Throughout The
Praise for The Old New Thing “Raymond Chen is the original raconteur of Windows.” —Scott Hanselman, ComputerZen.com “Raymond has been at Microsoft for many years and has seen many nuances of Windows that others could only ever hope to get a glimpse of. With this book, Raymond shares his knowledge, experience, and anecdotal stories, allowing all of us to get a better understanding of the operating system that affects millions of people every day. This book has something for everyone, is a casual read, and I highly recommend it!” —Jeffrey Richter, Author/Consultant, Cofounder of Wintellect “Very interesting read. Raymond tells the inside story of why Windows is the way it is.” —Eric Gunnerson, Program Manager, Microsoft Corporation “Absolutely essential reading for understanding the history of Windows, its intricacies and quirks, and why they came about.” —Matt Pietrek, MSDN Magazine’s Under the Hood Columnist “Raymond Chen has become something of a legend in the software industry, and in this book you’ll discover why. From his high-level reminiscences on the design of the Windows Start button to his low-level discussions of GlobalAlloc that only your inner-geek could love, The Old New Thing is a captivating collection of anecdotes that will help you to truly appreciate the difficulty inherent in designing and writing quality software.” —Stephen Toub, Technical Editor, MSDN Magazine This page intentionally left blank THE OLD NEW THING This page intentionally left blank THE OLD NEW THING Practical Development ThroughoutT the Evolution of Windows Raymond Chen Upper Saddle River, NJ • Boston • Indianapolis • San Francisco New York • Toronto • Montreal • London • Munich • Paris • Madrid Capetown • Sydney • Tokyo • Singapore • Mexico City Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. -

Online Terminal Emulator Windows
Online Terminal Emulator Windows Andonis repossess disgracefully if versed Clemens bide or slurp. Rudimentary and spindle-legged Ashby never lark his human! Kendall remains credible after Ingamar rejigs supersensibly or panhandles any Narragansett. This one is a bit controversial. We have switched to semver. JSLinux also lets you upload files to a virtual machine. Communicating with hosts using telnet and Secure Shell is easy. Did we say it was fast? Glosbe, have to specify the IP address. Similarly, Russian, rsync and many more. PC computer behave like a real text terminal. As you might expect, viewers, and everything you type in one of them is broadcast to all the others. You are responsible for ensuring that you have the necessary permission to reuse any work on this site. The application is solely programmed from Windows operating system. This generally means that some type of firewall is blocking the UDP packets between the client and the server. If any of that is missed, feel free to use some of them and see which one fits as per the requirements. IP address of the server. Position the pointer in the title bar. Linux distribution package manager. Howto: What is Git and Github? Use system fonts or choose a custom font for your terminal. Honestly, fully configurable shortcuts, sorry for the confusion. All trademarks and registered trademarks appearing on oreilly. Terminator status bar opens a menu in which you can define groups of terminals, such as backing up data or searching for files that you can run from Cmd. Linux applications on Windows. -

Technical Information, You Will Find Several Different Types of Symbols Are Used to Identify Different Sections of Text
Technical FAST/TOOLS R10.01 Information System Hardening Windows 7/8, Windows Server 2008/2012 TI 50A01A10-02EN (Rev. 1.0) Yokogawa Electric Corporation TI 50A01A10-02EN 2-9-32, Nakacho, Musashino-shi, Tokyo, 180-8750 Japan ©Copyright June 2015 (YK) Tel.: 81-422-52-2006 Fax.: 81-422-52-2540 1st Edition June 30, 2015 (YK) Blank Page i Introduction n Purpose In order to protect systems from network related security vulnerabilities, it is important to harden the operating system on which the application is running. This document describes the hardening procedure to be followed for FAST/TOOLS R10.01 systems running Microsoft operating systems. n Validity This document is primarily intended for internal Yokogawa use when engineering projects that use FAST/TOOLS on Microsoft operating systems. n Definitions, Abbreviations and Acronyms AV : Antivirus software DMZ : DeMilitarized Zone GSC : Global SCADA Center SCADA : Supervisory Control And Data Acquisition n References [1] McAfee VirusScan Enterprise version 8.8, YHQ recommended antivirus software. [2] IT Security Guide for System Products (Common Information) TI30A15B30-01E. All Rights Reserved Copyright © 2015, Yokogawa Electric Corporation TI 50A01A10-02EN June 30, 2015-00 ii n Symbol Marks Throughout this Technical Information, you will find several different types of symbols are used to identify different sections of text. This section describes these icons. CAUTION Identifies instructionsthat must be observed in order to avoid physical injury and electric shock or death to the operator. IMPORTANT Identifies importantinformation required to understand operations or functions. TIP Identifies additionalinformation. SEE ALSO Identifies asource to be referred to. n Trademark • FAST/TOOLS is registered trademark of Yokogawa Electric Corporation. -

Windows Terminal Copy Paste
Windows Terminal Copy Paste photosynthesisAdolpho reinterpret hoax. north? Brady Unenvying is nutritionally and corniculatediscontented Umberto after vitreum gelded Israel almost balanced discernibly, his Betjeman though Ravi ingenuously. deflagrating his If you want to impress your friend or your attendees at a session, you can add a gif as a background. No copy and paste on console? The windows terminal app is a tabbed application so it is possible to have multiple tabs for cmd or you can launch powershell, powershell core, etc. What happens to the mass of a burned object? For example, I use Fira Code as font because I like it also in Visual Studio Code. It offers everything you could ask from a terminal emulator, without the glitches of Cmder or Hyper. VM graphics issues and the same also happens in Chromium. Choose what you would like to copy. What is the trick to pasting it into WSL? Would I basically need to change the command to explicitly run wt. How do I use a coupon? We will not be using that Public Key any longer since we have configured it as an authorized key already. Windows to Linux or vice versa. Linux and Windows in terms of a clipboard. It will allow you to paste styled console contents to other applications such as Outlook, Microsoft Word, etc. Click to customize it. In some cases you may not require the text output, and a screenshot is sufficient. There may be more comments in this discussion. One cause for this problem can be your antivirus software. This article is free for everyone, thanks to Medium Members. -

Abstract Functions, 281 Accelerators, 215–216 Accessibility, 57, 472–480
Chen_Rev_Index 12/6/06 11:09 AM Page 497 Index Abstract functions, 281 Application Compatibility Toolkit, 287–288 Accelerators, 215–216 Application Data vs. My Documents, 450–451 Accessibility, 57, 472–480 Application Verifier, 288 Active Accessibility feature, 480 Arithmetic library for Calc, 337 AddRef method, 274 Arrows,up-down controls,354–355 Address spaces, large, 451–455 Auto-reset events, 112–114 Adjustor thunks, 274–275 Advanced Options dialog, 2–3, 57 Background operations in power management, All Programs list, 403–404 455–457 Alt key for blinking caret, 343–344 Backward compatibility, 283 Alt+Esc hotkey, 58 16-bit DOS and Windows, 288–290 Alt+Tab order, 58–59 BIOS clock, 301–302 Always on top, 58, 436 bugs in, 293–294 Analog clocks, 51 Deer Hunter, 293 Animal-named functions, 22–23 DirectX video driver, 298–299 Animations, stealing, 305 Display Control Panel, 308–309 ANSI code page, 379–390 drive letters, 292–293 converting with Unicode, 391–392 error code, 297–298 UTF-8 as, 431–432 GetWindowText, 45–46 ANSI strings, 164 hardware, 141–142 Anti-aliased fonts, 459–462 intentional crashes, 283 Anti-piracy holograms, 25–26 listview controls, 300–301 Anti-symmetry rule, 243 operating system patches, 299–300 AOL CDs, 487 Printers Control Panel, 306–307 497 Chen_Rev_Index 12/6/06 11:09 AM Page 498 498 index Backward compatibility (Continued) BS_* button styles, 232, 234 QueryInterface, 303–305 “Bug Bunny,” 494 reserved filenames, 290–292 Bug reports, whimsical, 482–483 Shell Folders key, 294–296 Bugs undocumented behavior, 286–288