Connecting to IBM I IBM I Access for Windows: Installation and Setup 7.1
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Marketdirect Storefront® Release Notes
MarketDirect StoreFront® Release Notes Version 12.2 2 ⚫ EFI Productivity Suite | MarketDirect StoreFront 12.2 Release Notes Copyright © 2004 - 2021 by Electronics for Imaging, Inc. All Rights Reserved. EFI Productivity Suite | MarketDirect StoreFront Release Notes August 2021 MarketDirect StoreFront v. 12.2 Document version 1.0 / 45145977 This publication is protected by copyright, and all rights are reserved. No part of it may be reproduced or transmitted in any form or by any means for any purpose without express prior written consent from Electronics for Imaging, Inc. Information in this document is subject to change without notice and does not represent a commitment on the part of Electronics for Imaging, Inc. Patents This product may be covered by one or more of the following U.S. Patents: 4,716,978, 4,828,056, 4,917,488, 4,941,038, 5,109,241, 5,170,182, 5,212,546, 5,260,878, 5,276,490, 5,278,599, 5,335,040, 5,343,311, 5,398,107, 5,424,754, 5,442,429, 5,459,560, 5,467,446, 5,506,946, 5,517,334, 5,537,516, 5,543,940, 5,553,200, 5,563,689, 5,565,960, 5,583,623, 5,596,416, 5,615,314, 5,619,624, 5,625,712, 5,640,228, 5,666,436, 5,745,657, 5,760,913, 5,799,232, 5,818,645, 5,835,788, 5,859,711, 5,867,179, 5,940,186, 5,959,867, 5,970,174, 5,982,937, 5,995,724, 6,002,795, 6,025,922, 6,035,103, 6,041,200, 6,065,041, 6,112,665, 6,116,707, 6,122,407, 6,134,018, 6,141,120, 6,166,821, 6,173,286, 6,185,335, 6,201,614, 6,215,562, 6,219,155, 6,219,659, 6,222,641, 6,224,048, 6,225,974, 6,226,419, 6,238,105, 6,239,895, 6,256,108, 6,269,190, 6,271,937, -

Supporting Operating System Installation | 3
cc01SupportingOperatingSystemInstallation.indd01SupportingOperatingSystemInstallation.indd PagePage 1 08/10/1408/10/14 4:334:33 PMPM martinmartin //208/WB01410/XXXXXXXXXXXXX/ch01/text_s208/WB01410/XXXXXXXXXXXXX/ch01/text_s Supporting Operating LESSON 1 System Installation 70-688 EXAM OBJECTIVE Objective 1.1 – Support operating system installation. This objective may include but is not limited to: Support Windows To Go; manage boot settings, including native virtual hard disk (VHD) and multi-boot; manage desktop images; customize a Windows installation by using Windows Preinstallation Environment (PE). LESSON HEADING EXAM OBJECTIVE Using a Troubleshooting Methodology Viewing System Information Using the Event Viewer Supporting Windows To Go Support Windows To Go Creating and Deploying a Windows To Go Workspace Drive Booting into a Windows To Go Workspace Managing Boot Settings Manage boot settings, including native virtual hard disk (VHD) and multi-boot Using BCDEdit and BCDBoot Configuring a Multi-Boot System Manage boot settings, including native virtual hard disk (VHD) and multi-boot Configuring a Native VHD Boot File Manage boot settings, including native virtual hard disk (VHD) and multi-boot Understanding VHD Formats Installing Windows 8.1 on a VHD with an Operating System Present Installing Windows 8.1 on a VHD Without an Operating SystemCOPYRIGHTED Present MATERIAL Managing Desktop Images Manage desktop images Capturing Images Modifying Images using DISM Customizing a Windows Installation by Using Windows PE Customize a Windows -

Advanced Windows SIG January 17, 2002 Disk Management Note: Material for Paragraphs 1, 2,And 3 Based on Microsoft Windows XP Inside/Out Chapter 26
Advanced Windows SIG January 17, 2002 Disk Management Note: material for paragraphs 1, 2,and 3 based on Microsoft Windows XP Inside/Out Chapter 26 If you have mastered hard-disk setup utilities from Windows 98 and Me, prepare to unlearn everything you know. Windows XP offers new capabilities and a new set of tools. 1. Definitions • Disk or hard Disk Î physical disk drive installed on computer o First hard disk drive Î Disk 0 o Second hard disk drive Î Disk 1 o Third hard disk drive Î Disk 2 • Basic Disk Î Contains one or more partitions o A partition Î A portion of a disk that functions as if it were a separate disk o A primary partition Î used for starting Windows - can not be further subdivided o An extended partition Î can be further divided into one or more logical drives each of which can be formatted separately and assigned a drive letter • Volume Î When a partition or logical drive is formatted for a particular file system (FAT, FAT32, or NTFS) and assigned a drive letter, it is called a volume Disk Management rev 1.doc Page 1 of 5 1/16/2002 D R Wright 2. Windows XP Disk Management Utility • Provides tools to manage disks, partitions, volumes and logical drives • Go to Start Î Right click My Computer Î Manage Î Disk Management • Perform the following tasks: o Check size, file system, status o Create partitions, logical drives, and volumes o Assign drive letters to hard disk volumes, removable disk drives, and CD-ROM drives o Changes usually take effect immediately and without need to reboot 3. -

Implementing Powerpc Linux on System I Platform
Front cover Implementing POWER Linux on IBM System i Platform Planning and configuring Linux servers on IBM System i platform Linux distribution on IBM System i Platform installation guide Tips to run Linux servers on IBM System i platform Yessong Johng Erwin Earley Rico Franke Vlatko Kosturjak ibm.com/redbooks International Technical Support Organization Implementing POWER Linux on IBM System i Platform February 2007 SG24-6388-01 Note: Before using this information and the product it supports, read the information in “Notices” on page vii. Second Edition (February 2007) This edition applies to i5/OS V5R4, SLES10 and RHEL4. © Copyright International Business Machines Corporation 2005, 2007. All rights reserved. Note to U.S. Government Users Restricted Rights -- Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Notices . vii Trademarks . viii Preface . ix The team that wrote this redbook. ix Become a published author . xi Comments welcome. xi Chapter 1. Introduction to Linux on System i platform . 1 1.1 Concepts and terminology . 2 1.1.1 System i platform . 2 1.1.2 Hardware management console . 4 1.1.3 Virtual Partition Manager (VPM) . 10 1.2 Brief introduction to Linux and Linux on System i platform . 12 1.2.1 Linux on System i platform . 12 1.3 Differences between existing Power5-based System i and previous System i models 13 1.3.1 Linux enhancements on Power5 / Power5+ . 14 1.4 Where to go for more information . 15 Chapter 2. Configuration planning . 17 2.1 Concepts and terminology . 18 2.1.1 Processor concepts . -

Powernet Installation and Troubleshooting Guide
PowerNet Installation and Troubleshooting Guide revision: 06-13-06-0001 PowerNet Installation and Troubleshooting Guide Table of Contents Implementation Process for PowerNet Products .......................................................3 Customer Requirements and Information Gathering .................................................4 Installation Process……................................................................................................5 Verification of the Installation ......................................................................................6 XP Soft NCU Installation ...............................................................................................7 Appendix A: Preparing Windows 2000 for PowerNet...............................................12 Appendix B: Preparing Windows NT for PowerNet..................................................14 Appendix C: Application Target Hosts ......................................................................16 Appendix D: Information on Access Points ..............................................................17 Appendix E: Mobile Unit Information.........................................................................18 Appendix F: PowerNet OpenAir Server Information ................................................19 Appendix G: PowerNet Twin Client Server Information...........................................20 Appendix H: Non-Interactive Applications User Interface .......................................21 Appendix I: Windows 2000 Telnet Interface..............................................................22 -

Windows 95 & NT
Windows 95 & NT Configuration Help By Marc Goetschalckx Version 1.48, September 19, 1999 Copyright 1995-1999 Marc Goetschalckx. All rights reserved Version 1.48, September 19, 1999 Marc Goetschalckx 4031 Bradbury Drive Marietta, GA 30062-6165 tel. (770) 565-3370 fax. (770) 578-6148 Contents Chapter 1. System Files 1 MSDOS.SYS..............................................................................................................................1 WIN.COM..................................................................................................................................2 Chapter 2. Windows Installation 5 Setup (Windows 95 only)...........................................................................................................5 Internet Services Manager (Windows NT Only)........................................................................6 Dial-Up Networking and Scripting Tool....................................................................................6 Direct Cable Connection ..........................................................................................................16 Fax............................................................................................................................................17 Using Device Drivers of Previous Versions.............................................................................18 Identifying Windows Versions.................................................................................................18 User Manager (NT Only) .........................................................................................................19 -

The New York Society Library Presents
The New York Society Library Presents: Intermediate Computers Ingrid Richter Computer Specialist & Webmaster COMPUTERS I INDEX INTRODUCTION Basic Windows Overview……………………………………………………………………… Page 03 Windows 98, ME, 2000, XP.........................................................….. Page 04 THE BASICS: My Computer........................................................................……… Page 05 Start Menu & Taskbar..........................................................……… Page 06 Control Panel.......................................................................……… Page 07 Windows Setup.....................................................................……… Page 08 FILE ORGANIZATION: Windows Explorer...................................................................... Page 09 SOFTWARE Backup..................................................................................... Page 10 DOS and file extensions………………………………………………………………………. Page 10 Calculator................................................................................. Page 11 HyperTerminal.......................................................................... Page 11 Notepad.................................................................................... Page 12 Wordpad................................................................................... Page 12 Paint......................................................................................... Page 13 TROUBLESHOOTING: Scanning Hard Drive................................................................. -
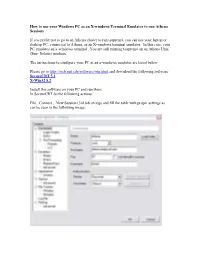
How to Use Your Windows PC As an X-Windows Terminal Emulator to Run Athena Sessions
How to use your Windows PC as an X-windows Terminal Emulator to run Athena Sessions If you prefer not to go to an Athena cluster to run tsuprem4, you can use your laptop or desktop PC, connected to Athena, as an X-windows terminal emulator. In this case, your PC emulates an x-windows terminal. You are still running tsuprem4 on an Athena Unix (Sun- Solaris) machine. The instructions to configure your PC as an x-windows emulator are listed below: Please go to http://web.mit.edu/software/win.html and download the following software: SecureCRT 5.1 X-Win32 8.2 Install this software on your PC and run them. In SecureCRT do the following actions: File...Connect....New Session (3rd tab on top) and fill the table with proper settings as can be seen in the following image: Fill the username field with your Kerberos username and press OK to run and insert your password. Run Xwin32 or Exceed if you have it (Exceed is not available on the MIT website but is available for purchase). In order to see images when running tsuprem4, you need to adjust the DISPLAY system variable according to your IP address. A simple way of getting your IP address, is typing the "setenv" command in SecureCRT screen. You will see something similar to this (with different numbers/characters): USER=pouya LOGNAME=pouya HOME=/afs/athena.mit.edu/user/p/o/pouya PATH=/srvd/patch:/usr/athena/bin:/usr/athena/etc:/bin/athena:/usr/openwin/bin:/usr/open win/demo:/usr/dt/bin:/usr/bin:/usr/ccs/bin:/usr/sbin:/sbin:/usr/sfw/bin:/usr/ucb:.:/mit/avant i/arch/sun4x_510/bin:/mit/matlab/arch/sun4x_510/bin:/mit/maple/arch/sun4x_59/bin MAIL=/var/mail//pouya SHELL=/bin/athena/tcsh TZ=US/Eastern SSH_CLIENT=18.62.30.76 2304 22 SSH_CONNECTION=18.62.30.76 2304 18.7.18.74 22 SSH_TTY=/dev/pts/59 ..... -

PATHWORKS for DOS Microsoft Windows Support Guide
PATHWORKS for DOS ' Microsoft Windows Support Guide PATHWORKS for DOS Microsoft Windows Support Guide Order Number: AA-MF87D-TH August 1991 Revision/Update Information: This document supersedes Microsoft Windows Support Guide, order number AA-MF87C-TH. Software Version: PATHWORKS for DOS Version 4.1 Digital Equipment Corporation Maynard, Massachusetts First Published, October 1988 Revised, April 1989, July 1990, October 1990, January 1991, August 1991 The infonnation in this document is subject to change without notice and should not be construed as a commitment by Digital Equipment Corporation. Digital Equipment Corporation assumes no responsibility for any errors that may appear in this document. The software described in this document is furnished under a license and may be used or copied only in accordance with the terms of such license. No responsibility is assumed for the use or reliability of software on equipment that is not supplied by Digital Equipment Corporation or its affiliated companies. Restricted Rights: Use, duplication, or disclosure by the U.S. Government is subject to restrictions as set forth in subparagraph (c)(l)(ii) of the Rights in Technical Data and Computer Software clause at DFARS 252.227-7013. © Digital Equipment Corporation 1988, 1989, 1990, 1991. All Rights Reserved. Printed in U.S.A. The postpaid Reader's Comments fonn at the end of this document requests your critical evaluation to assist in preparing future documentation. The following are trademarks of Digital Equipment Corporation: ALL-IN-I, DDCMP, DDIF, DEC, DECconnect, DEClaser, DE Cmate , DECnet, DECnet-DOS, DECpc, DECrouter, DECSA, DE C server, DECstation, DECwindows, DECwrite, DELNI, DEMPR, DEPCA, DESTA, Digital, DNA, EtherWORKS, LA50, LA75 Companion, LAT, LN03, LN03 PLUS, LN03 ScriptPrinter, METROWAVE, MicroVAX, PATHWORKS, PrintServer, ReGIS, RMS-ll, RSX, RSX-ll, RT, RT-ll, RX33, ThinWire, TK, ULTRIX, VAX, VAX Notes, VAXcluster, VAXmate, VAXmail, VAXserver, VAXshare, VMS, VT, WPS, WPS.PLUS, and the DIGITAL logo. -

U3-1033 Ovation Netdde Server
Ovation NetDDE Server User Guide Section Title Page Summary of Changes Section 1. Introduction 1-1. Overview. 1-1 1-2. NetDDE Server Features. 1-1 1-3. DDE Overview . 1-2 1-3.1. Application or Service Name. 1-2 1-3.2. Topic . 1-2 1-3.3. Item . 1-3 1-3.4. Network DDE . 1-4 1-4. Limitations . 1-5 Section 2. Getting Started 2-1. Section Overview . 2-1 2-2. Requirements . 2-1 2-2.1. System . 2-1 2-2.2. Hardware . 2-1 2-2.3. Software . 2-2 2-2.4. License Server . 2-2 2-3. Setup . 2-4 2-3.1. Environment Variables Required for Setup. 2-5 2-3.2. Linked Libraries. 2-6 2-3.3. Files Installed During Setup. 2-7 2-3.4. Registry Entries . 2-8 2-3.5. Security . 2-10 2-4. Setup Procedure . 2-10 2-5. Configuration . 2-11 2-5.1. Permissions . 2-11 2-6. Un-installation. 2-11 Section 3. Using NetDDE 3-1. Section Overview . 3-1 3-2. Syntax for Calls. 3-1 Glossary Index 12/00 i U3-1033 (Rev 1) Westinghouse Process Control, Inc. Proprietary Class 2C Summary of Changes This revision of “Ovation NetDDE Server User Guide” (U3-1033) reflects the following changes: • System topic has now been changed to wwwdde_system. • DataCreate and DataOriginate topics are removed from the WDPF NetDDE Server. • The machine name must appear when the point information (or Item) link is created on the WDPF NetDDE Server machine or accessed remotely in Excel or any other DDE supported application. -

Managing the Control Panel Functions
System i and System p Managing the control panel functions System i and System p Managing the control panel functions Note Before using this information and the product it supports, read the information in “Notices” on page 51 and the IBM Systems Safety Information manual, G229-9054. Seventh Edition (September 2007) © Copyright International Business Machines Corporation 2004, 2007. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Safety and environmental notices ........................v About this topic ................................ix Managing the control panel functions .......................1 What’s new for Capacity on Demand ...........................1 PDF file for Managing the control panel functions .......................1 Control panel concepts ................................1 Physical control panel ...............................2 Remote control panel ...............................5 Planning for the remote control panel .........................6 Virtual control panel................................7 Differences between the virtual control panel and remote control panel...............9 Control panel function codes .............................9 Control panel function codes on the HMC ........................10 Control panel function codes on the 7037-A50 and 7047-185 models ...............12 Control panel function code comparison for the RCP, VCP, and HMC ...............13 Values for IPL types, system operating modes, and speeds ..................15 -

Systems Management Logical Partitions Version 6 Release 1
IBM System i Systems management Logical partitions Version 6 Release 1 IBM System i Systems management Logical partitions Version 6 Release 1 Note Before using this information and the product it supports, read the information in “Notices,” on page 135. This edition applies to version 6, release 1, modification 0 of and IBM i5/OS (product number 5761–SS1) to all subsequent releases and modifications until otherwise indicated in new editions. This version does not run on all reduced instruction set computer (RISC) models nor does it run on CISC models. © Copyright IBM Corporation 1999, 2008. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Logical partitions........... 1 Ordering a new server or upgrading an PDF file for Logical partitions ........ 1 existing server with logical partitions .... 45 Partitioning with a System i ......... 1 Providing hardware placement information Logical partition concepts ......... 1 to service providers......... 45 How logical partitioning works ...... 2 Designing your logical partitions ..... 46 How logical partitioning can work for you .. 3 Deciding what runs in the primary and Hardware for logical partitions ...... 4 secondary partition ......... 46 Bus .............. 5 Capacity planning for logical partitions .. 47 Bus-level and IOP-level I/O partitions ... 7 Using the System Planning Tool .... 47 Dynamically switching IOPs between Examples: Logical partitioning ...... 47 partitions ............ 7 Creating logical partitions ........ 48 IOP .............. 9 Managing logical partitions ........ 49 SPD and PCI ........... 11 Managing logical partitions by using System i Processor ............ 11 Navigator, DST, and SST ........ 50 Memory ............ 14 Starting System i Navigator ...... 53 Disk units ............ 15 Starting SST and DST for logical partitions 53 Removable media device and alternate Logical partition authority .....